1: Three layer switching technology
1.1: General
summary:
Layer 3 switch: 1: layer 3 switch = Layer 3 routing (but it can't be completely used as a router, generally only as a router) vlan Network segment connection) + Layer 2 switch is essentially a layer 2 device 2: The layer 3 routing function can be turned on and off. It can only be turned on manually conf t ip routing Enable layer 3 routing no ip routing Turn off the layer 3 routing function 3: Advantages of layer 3 switch: Compared with single arm Routing: 1: Solved the network bottleneck problem (different vlan Segments share the same"trunk Line",Easy to cause "flow blockage") 2: The single point of failure is solved (the virtual interface no longer depends on any physical interface, one interface will not break, and all network segments cannot communicate) 3: Primary routing, permanent switching 4: Virtual interface (configuration) on layer 3 switch vlan Gateway), the command is as follows: conf t ip routing int vlan 10 ip address 10.1.1.254 255.255.255.0 no shut 5: Upgrade layer 2 port to layer 3 port int f0/x no switchport # If it's not a switch port, it's a layer 3 port (you can understand that) ip address 10.1.1.254 255.255.255.0 no shut
Tips:
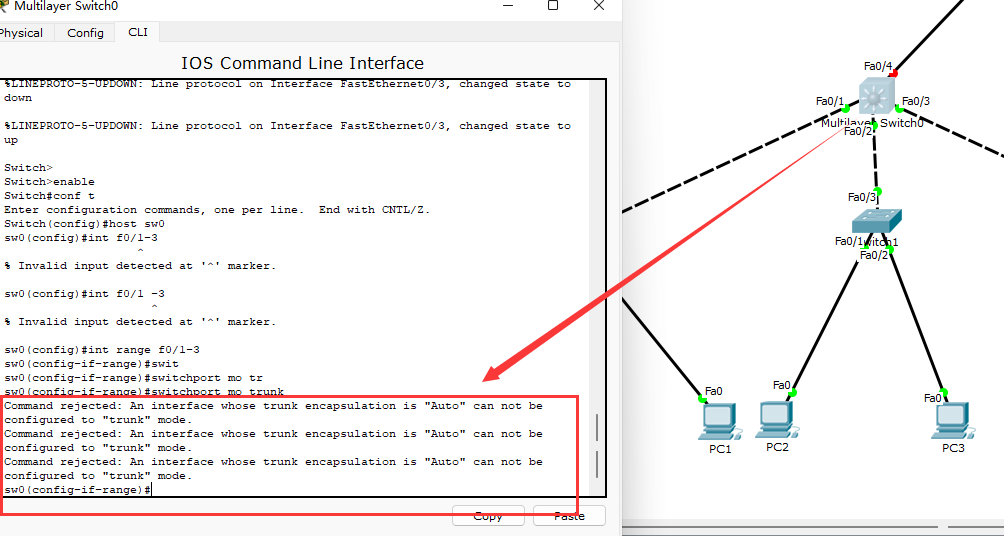
Configuring trunk directly on the layer-3 switch will report an error, but it does not affect it. You can also add a message before the sw m t command to specify the encapsulation protocol, so that an error will not be reported
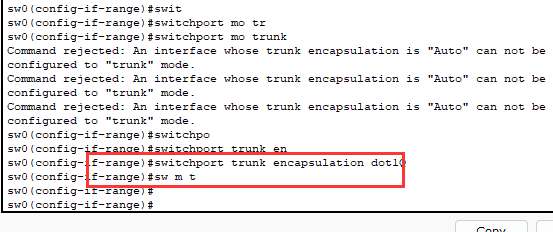
switchport trunk encapsulation dot1Q
As shown in the figure:
After adding:
1.2: small experiment
Experimental topology

As shown in the figure, the layer 3 switch is sw0, and the rest are sw1, sw2 and sw3 from left to right

After configuration:
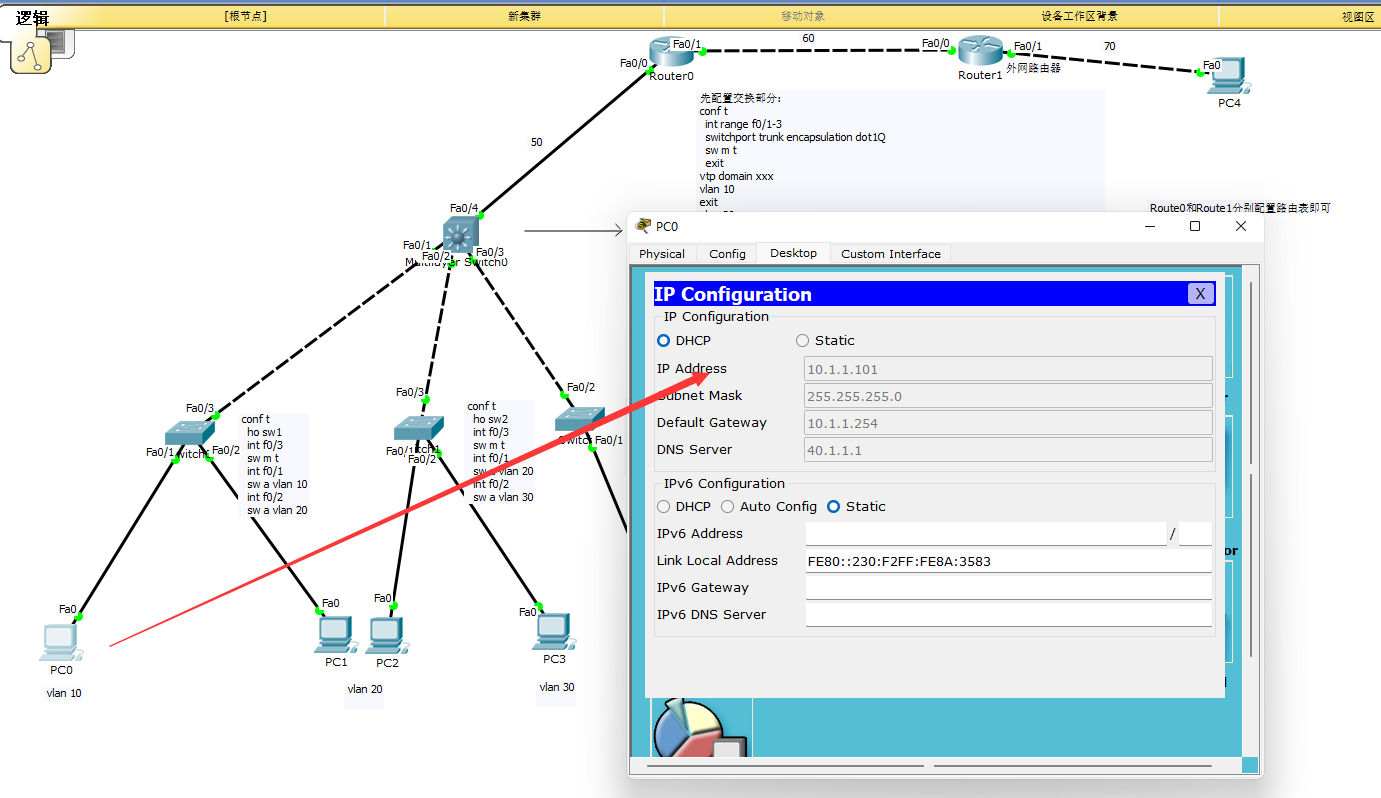
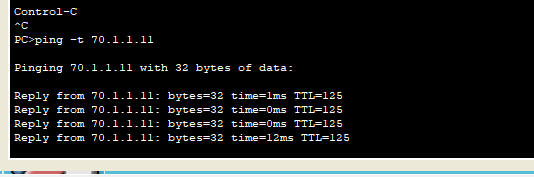
The IP of the external network PC is 70.1 one point one one
2: HSRP
2.1: overview of three-tier network planning
Three layer network planning
Core layer, aggregation layer, access layer
The core layer and aggregation layer are three-layer switches, and the access layer is two-layer switches

2.2: HSRP protocol
HSRP(Hot Standby Routing Protocol)
Hot backup routing protocol) is a private technology of Cisco. It ensures that when the network edge equipment or access link fails, the user communication can be restored quickly and transparently, so as to provide redundancy for the IP network. Through the application of HSRP, the normal operation time of the network can be close to 100%, so as to meet the requirements of users for network reliability
There is another protocol, VRRP, which is public
Hot backup routing protocol: (it is said to be a hot backup routing, but it is actually a hot backup gateway) 1 HSRP Groups: of groups ID Range, 1-255,There is no order of magnitude 2 stay HSRP In the protocol, a virtual router will be created IP Call it virtual IP address 3 HSRP Members of the group: 1)Virtual router (boss) 2)Active router (second) 3)Backup router (third) 4)Other routers (generally not required) 4 HSRP Priority: 1-255,The default is 100. The higher the number, the higher the priority. Virtual routers are not included. Only physical routers have priority 5 HSRP Group members send via scheduled hello Packet to communicate. The default interval is 3 seconds and the persistence time is 10 seconds Persistence time: the backup router will wait for the active router 3 times hello Package (3)*3=9),Then I'll wait another second, so it's 9+1=10,If the active router fails to respond, it will seize the initiative 6 preempt preempt(Active routers can be configured, but backup routers must be configured) Function: when the other party cannot be detected or the other party's priority is lower than yourself, immediately seize the name of the active route 7 Configuration tracking track(Generally, the active router needs to be configured. It doesn't matter whether the backup router is configured or not). It tracks other ports when other ports are configured down If it fails, the priority will be reduced automatically to turn the backup router into an active router, so as to ensure normal communication.
Hot backup commands: these commands are configured in the gateway port, not in the global configuration mode
R1: Active router int f0/0 standby 1 ip 192.168.1.254 # Declare the group name and virtual IP address. This is the virtual IP, not the IP of this port standby 1 priority # Claim priority standby 1 preempt # Declaration preemption (may have) standby 1 track f0/1 # Configuration tracking (required) R2: Backup router int f0/0 standby 1 ip 192.168.1.254 standby 1 priority standby 1 preempt # (required) standby 1 track f0/1 # (yes) see HSRP Status: show standby brief # View configuration show standby # View the configuration (in detail, you can see the value of self downgrade)
2.3: small experiment to verify HSRP protocol
Experimental topology:
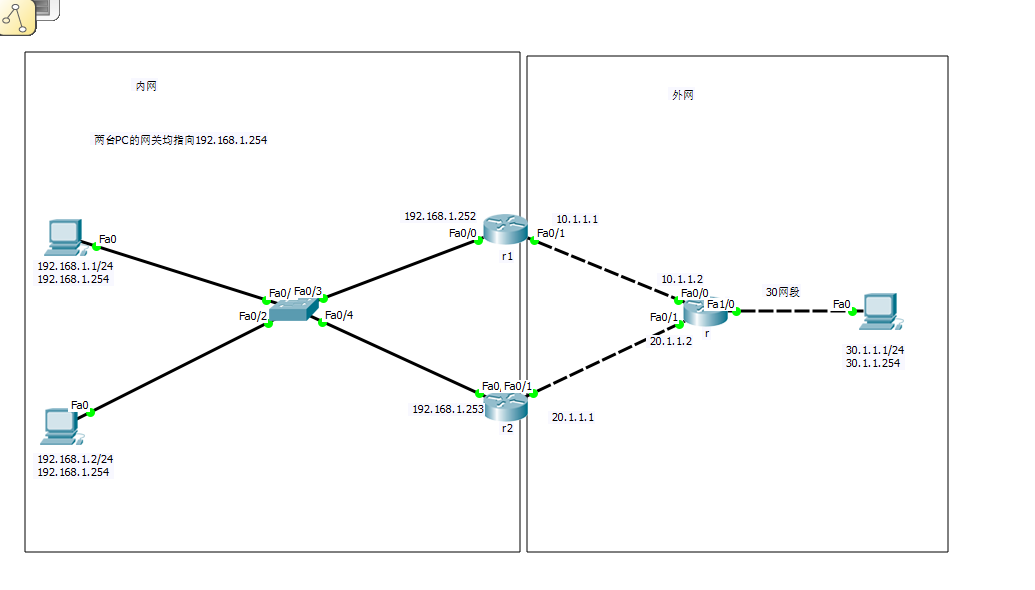
Some experimental processes:
R1:
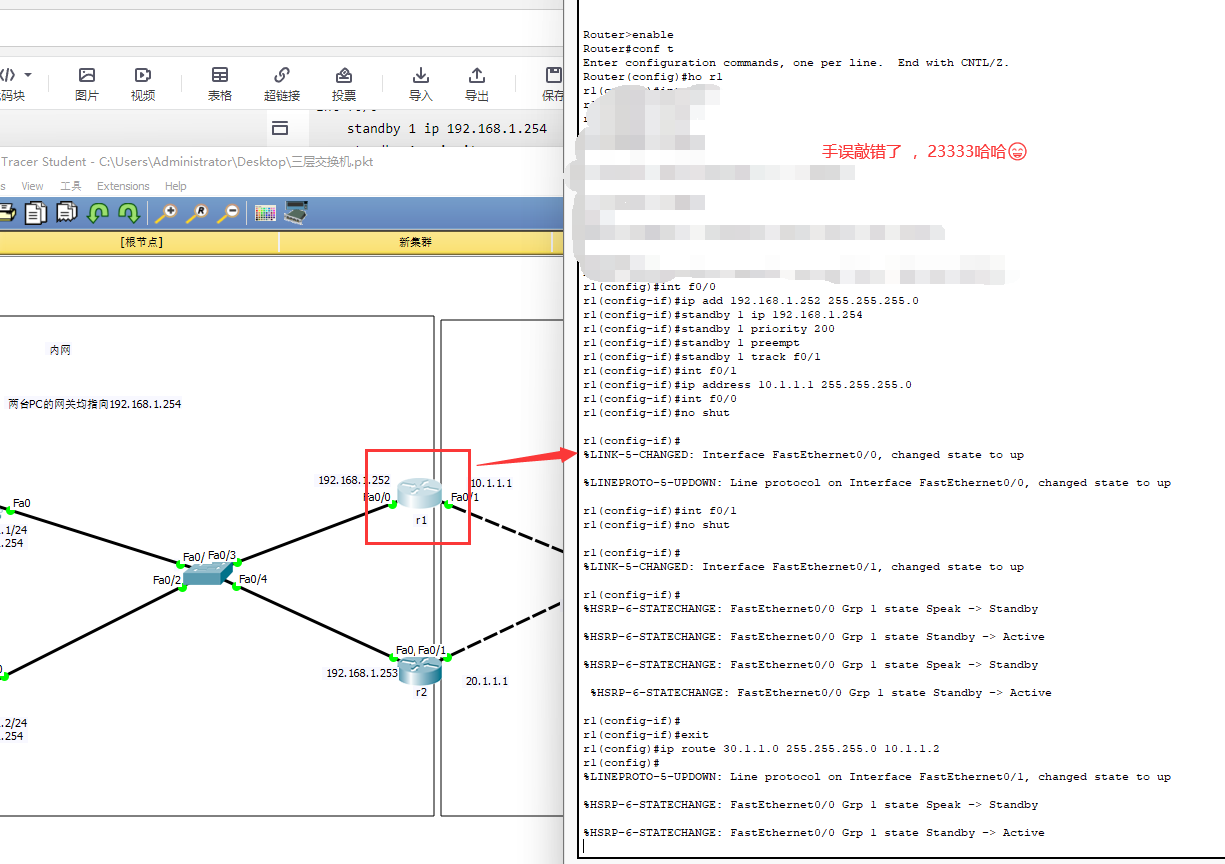
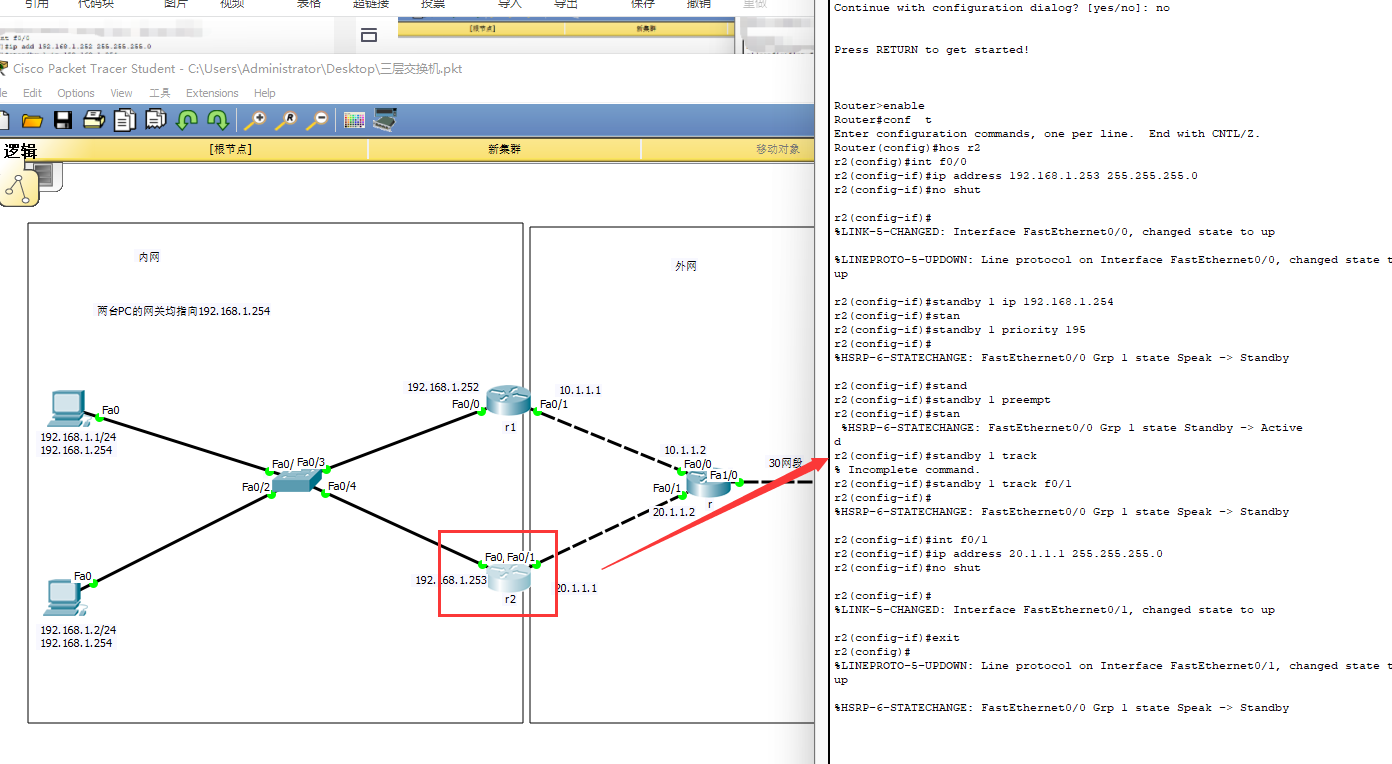
R2:
In the figure, you forgot one step: set the route, IP route 30.1 1.0 255.255. 255.0 20.1. one point two
R:
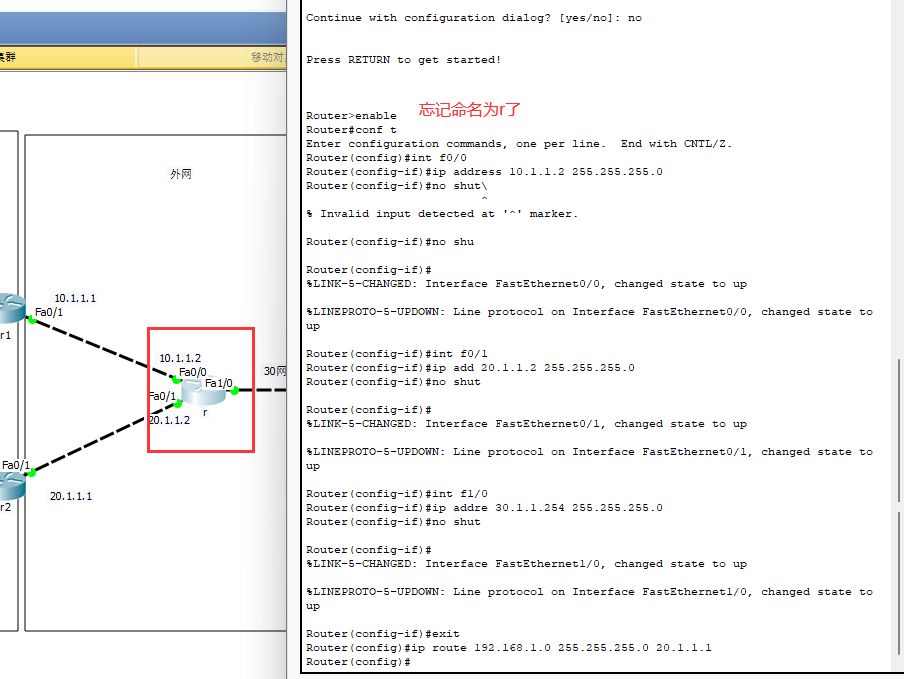
ping command test 1, manual down f0/0:

ping command test 2, manual down f0/1:
The computer has a blue screen. There should be no problem if it is not saved.
Analyze a wave:
When you down the f0/1 interface of r1, because the original r1 is an active route, it will track f0/1. Because it is in the same group, it will automatically degrade and send hello packets to r2. At this time, r2 will preempt and become an active router. This prevents communication interruption.
You can use the show standby command to check how much is degraded. For this software, it should be degraded by 10, that is, from 200 to 190, which is less than 195 of r2. Therefore, r2 preemption is successful and becomes an active router.
Tips:
About self downgrade In command standby 1 track f0/1 number A number can be followed to represent the self drop, but this software doesn't seem to support it
3: Three layer network planning and comprehensive experiment
As shown in the figure:

Then ping the test:
