13, Configure and protect SSH services
This section describes how to configure and protect SSH services. As a service that must be understood in the foundation, it needs to be well mastered both in principle and operation. SSH is basically used for remote management in work.
This column will cover the entire RHCSA certification: Address of operation and maintenance basic skills column
13.1 ssh service introduction
ssh: secure shell, protocol, 22/tcp, secure remote login, encrypted communication, replacing the traditional telnet protocol
Specific software implementation:
- OpenSSH: the open source implementation of ssh protocol. rhel and centos are installed by default
- dropbear: another open source project implementation of ssh protocol
SSH protocol version:
- v1: MAC based on CRC-32 is unsafe; man-in-middle
- v2: the host protocol of both parties selects the secure MAC mode, performs key exchange based on DH algorithm, and realizes identity authentication based on RSA or DSA
13.1.1 public key exchange principle
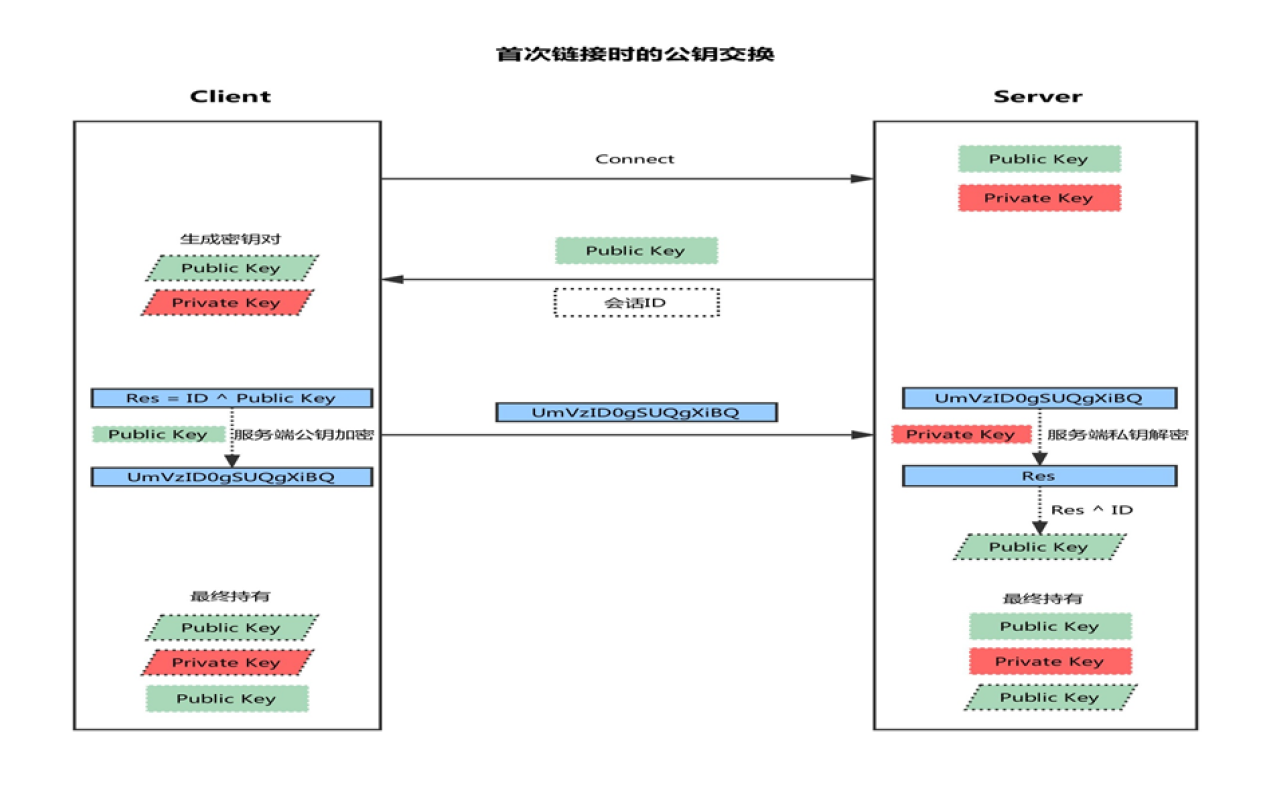
- Client initiated link request
- The server returns its own public key and a session ID (in this step, the client gets the public key of the server)
- Client generated key pair
- The client uses its own public key XOR session ID to calculate a value Res and encrypt it with the public key of the server
- The client sends the encrypted value to the server, and the server decrypts it with the private key to obtain Res
- The server uses the decrypted value Res XOR session ID to calculate the public key of the client (in this step, the server obtains the public key of the client)
- Finally: each party holds three secret keys, namely its own pair of public and private keys, and the other party's public key. All subsequent communications are secure
Will be encrypted
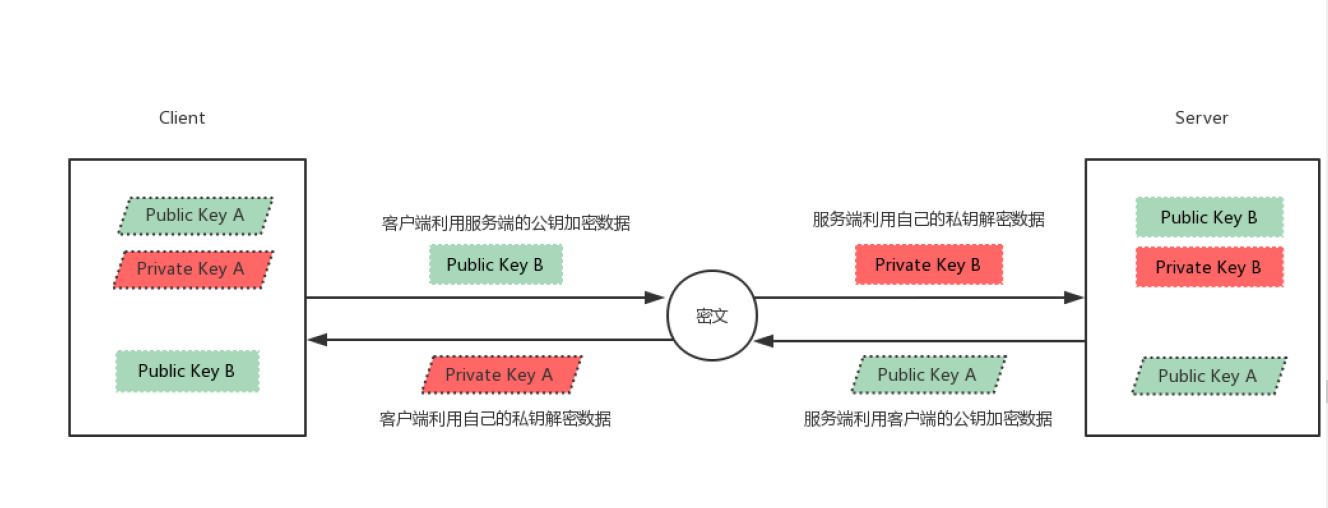
13.1.2 ssh encrypted communication principle
13.2 openssh service
OpenSSH is a free and open source implementation of SSH (Secure SHell) protocol. It is generally installed by default in various Linux versions and is based on C/S structure
Openssh software related packages:
- openssh
- openssh-clients
- openssh-server
Server: / usr/sbin/sshd
Unit file: / usr / lib / SYSTEMd / system / sshd service
client:
- Linux Client: ssh, scp, sftp,slogin
- Windows Client: xshell, MobaXterm,putty, securecrt, sshsecureshellclient
13.2.1 client ssh command
ssh commands are ssh clients that allow authenticated encrypted secure access to remote systems
When the user connects to the ssh server remotely, the ssh server / etc / SSH / SSH will be copied_ host*key. The public key in the pub file to the client
~/. ssh/know_hosts. The next time you connect, the corresponding private key will be automatically matched. If it cannot be matched, the connection will be rejected
Format:
ssh [user@]host [COMMAND] ssh [-l user] host [COMMAND]
Common options
-p port: Port monitored by remote server -b Specify the source of the connection IP -v Debug mode -C Compression mode -X support x11 forward -t Forced pseudo tty Allocation, such as: ssh -t remoteserver1 ssh -t remoteserver2 ssh remoteserver3 -o option For example:-o StrictHostKeyChecking=no -i <file> Specify the path of the private key file to achieve key Validation, default file: ~/.ssh/id_dsa, ~/.ssh/id_ecdsa, ~/.ssh/id_ed25519,~/.ssh/id_rsa etc.
Example: remote command execution
[root@servera .ssh]# ssh 192.168.137.129 ls -l root@192.168.137.129's password: total 4 -rw-------. 1 root root 1624 Apr 2 13:51 anaconda-ks.cfg
13.2.2 ssh login verification
13.2.2.1 introduction to SSH login authentication method
Common authentication methods for ssh service login
- User / password
- Key based
Login authentication based on user and password
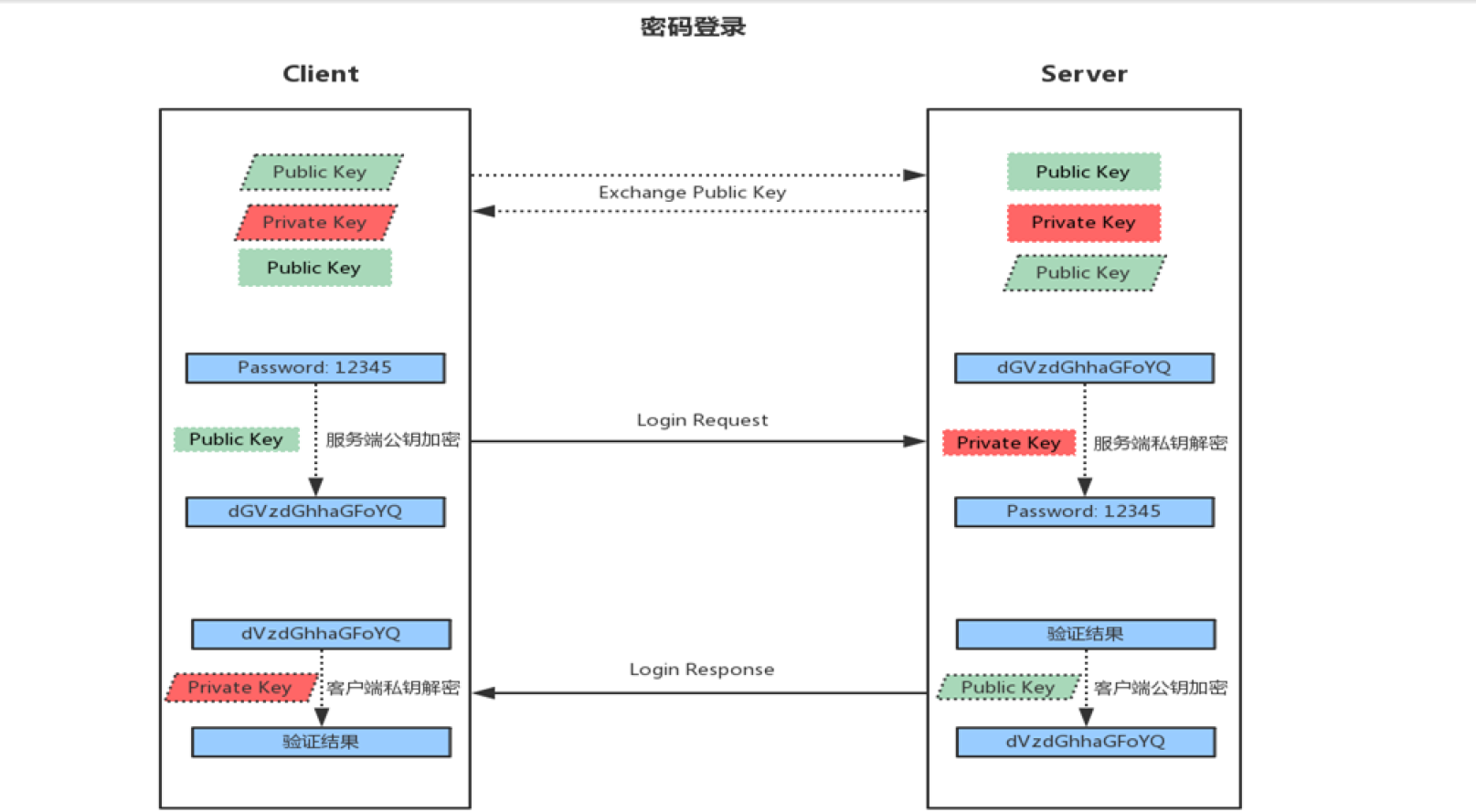
- When the client initiates an ssh request, the server will send its public key to the user
- The user will encrypt the password according to the public key sent by the server
- The encrypted information is sent back to the server, which decrypts it with its own private key. If the password is correct, the user logs in successfully
Key based login method
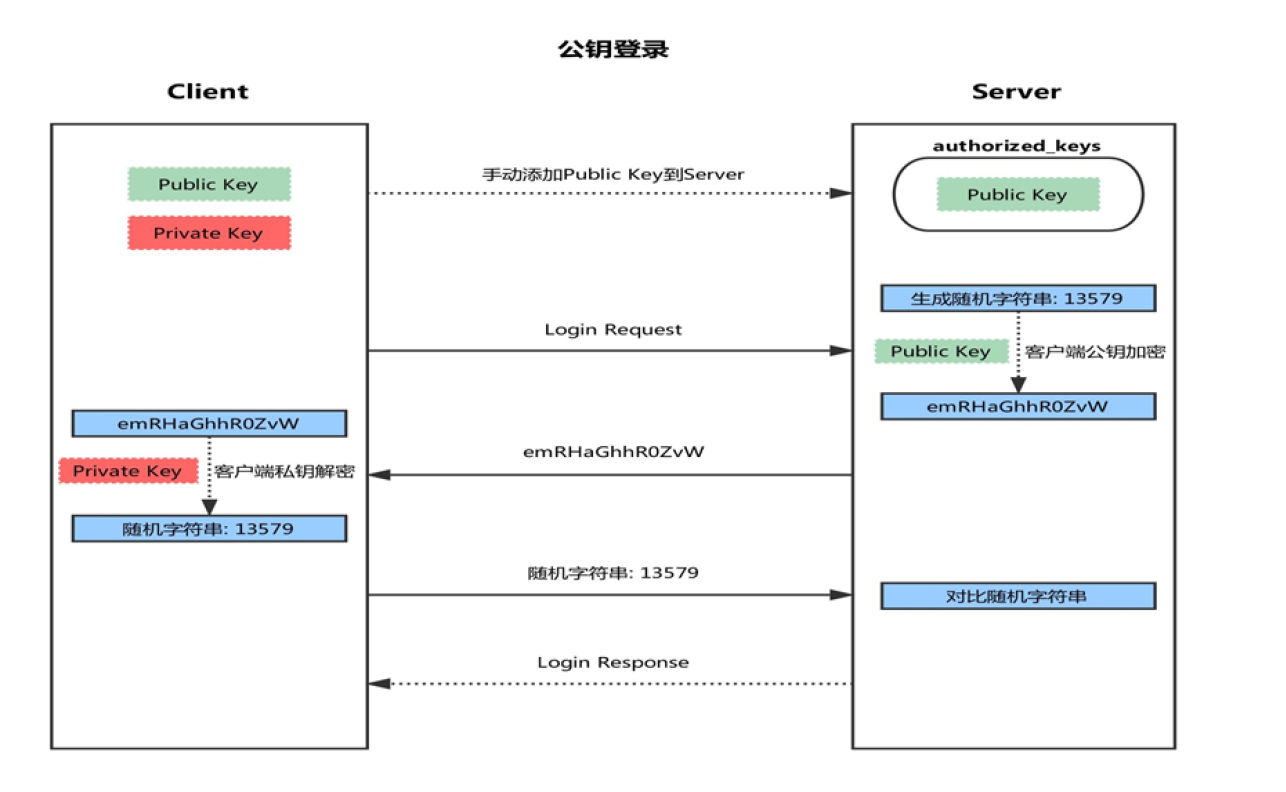
- First, a pair of keys (SSH keygen) is generated on the client
- And copy the client's public key SSH copy ID to the server
- When the client sends a connection request again, including ip and user name
- After receiving the request from the client, the server will go to authorized_keys. If there are responding IP addresses and users, they will be generated randomly
Into a string - The server will use the public key copied from the client for encryption, and then send it to the client
- After receiving the message from the server, the client will decrypt it with the private key, and then send the decrypted string to the server
- After receiving the string sent by the client, the server compares it with the previous string. If it is consistent, it is allowed to log in without password
3.2.3.2 realize key based login
Generate key pair on client
ssh-keygen -t rsa [-P 'password'] [-f "~/.ssh/id_rsa"]
Transfer the public key file to the home directory of the corresponding user of the remote server
ssh-copy-id [-i [identity_file]] [user@]host
Reset private key password:
ssh-keygen -p
13.3.4 ssh server configuration
Server side: sshd
Server side configuration file: / etc/ssh/sshd_config
Server side profile help: man 5 sshd_config
Common parameters:
Port #Before changing the port, turn off selinux and setenforce0 ListenAddress ip LoginGraceTime 2m PermitRootLogin yes #The default ubuntu does not allow root remote ssh login StrictModes yes #Check ssh / owner of the file, permissions, etc MaxAuthTries 6 MaxSessions 10 #Maximum sessions of the same connection PubkeyAuthentication yes #key based authentication PermitEmptyPasswords no #Empty password connection PasswordAuthentication yes #Connect based on user name and password GatewayPorts no ClientAliveInterval 10 #Unit: Second ClientAliveCountMax 3 #Default 3 UseDNS yes #Increase speed can be changed to no GSSAPIAuthentication yes #Increase speed can be changed to no MaxStartups #Maximum unauthenticated connection, default 10 Banner /path/file #Here are some ways to limit users who can log in: AllowUsers user1 user2 user3 DenyUsers AllowGroups DenyGroups
Example: set ssh idle for 60s to automatically log off
Vim /etc/ssh/sshd_config ClientAliveInterval 60 ClientAliveCountMax 0 Service sshd restart #Note: a new connection is valid
Example: solve the problem of slow ssh login
vim /etc/ssh/sshd_config UseDNS no GSSAPIAuthentication no systemctl restart sshd
Example: enable / disable root remote ssh login
#Modify sshd service configuration file vim /etc/ssh/sshd_config #Permitrotlogin exhibit password comment out this line PermitRootLogin yes/no Change to the following form( yes Enable/no (disabled) systemctl restart sshd
Best practices for ssh services
Non default ports are recommended No use protocol version 1 Restrict users who can log in Set idle session timeout length Use firewall settings ssh Access policy Listen only for specific IP address When authenticating based on password, use strong password policy, such as: tr -dc A-Za-z0-9_ < /dev/urandom | head -c 12|xargs Use key based authentication Do not use empty passwords prohibit root User login directly limit ssh Access frequency and concurrent online number Analyze logs frequently
summary
The above is the brief introduction and explanation of SSH by [brother goldfish]. I hope it can be helpful to the little friends who see this article.
If this [article] is helpful to you, I hope I can praise [brother goldfish] 👍, It is not easy to create. Compared with the official statement, I prefer to explain every knowledge point in [easy to understand] style. If you are interested in [operation and maintenance technology], you are also welcome to pay attention ❤️❤️❤️ [brother goldfish] ❤️❤️❤️, I will bring you great [harvest and surprise] 💕💕!
