2020 Qianxin autumn recruitment Java direction test paper 3
1, Q: access to a file is often limited by ()
A: User access rights and file properties
2, Q: the following description of TCP and UDP is correct ().
A: TCP is connection oriented and UDP is connectionless
3, Q: under what circumstances is the node newly inserted into the linked list both the first node and the last node
A: When the linked list is empty
4, Q: does a directed acyclic graph have topological ordering?
A: Exist
5, Q: which of the following descriptions about hash table is correct?
A: The time complexity of hash table query is O(1)
6, Q: there is a sequence composed of numbers [a1,a2,...,aN]. If you want to count the number of occurrences of all numbers, which of the following data structures is more suitable?
A: Hash table
7, Q: there are several strings. To find a string with the same prefix, which of the following data structures is more suitable
A: Trie tree
8, Q: which of the following algorithms is used to solve the maximum common divisor of two positive integers?
A: Rolling Division
9, Q: problems related to epoll two modes
1.What is? epoll
epoll yes Linux The kernel has made improvements to deal with a large number of file descriptors poll,yes Linux Down multiplexing IO Interface select/poll It can significantly improve the system performance when the program is only a small number of active in a large number of concurrent connections CPU Utilization.
2.epoll Two modes of
LT(level trigger)Mode and ET(edge trigger)Mode, where LT Is the default mode
LT: epoll_wait When a descriptor event is detected and the application is notified of this event, the application may not process it immediately and call it the next time epoll_wait Respond to the application again and notify the event again.
ET: epoll_wait When a descriptor event is detected and notified to the application, the application must handle the event, otherwise it will be called next time epoll_wait Does not respond to the application and notify this event. stay ET Mode, non blocking sockets are required( non-blocking IO).
10, Q: umask related issues
1.umask Can be used to set[Permission mask]. [Permission mask]It is composed of three octal digits. After subtracting the permission mask from the existing access permission, the default permission when creating a file can be generated. 2.333 in this question means-wx-wx-wx,rwxrwxrwx filter-wx-wx-wx The result is r--r--r--
11, Q: during DNS system test, assuming that the named process number is 53, how to inform the process to reread the configuration file

12, Q: views are available for
A: Restrict access to data in specific rows or columns in a table
13, Q: one reason to add an index is
A: Improve the performance of SELECT statements
14, Q: you need to delete the view named EmployeeView from your database. Which statement should be used
A: DROP VIEW EmployeeView
15, Q: what's wrong with NAT?
A: IPv6 does not require NAT at all
16, Q: those are not IPv6 Transition technologies
A: Application Recognition Technology
17, The aggregation layer does not belong to the OSI seven layer model
OSI seven layer model: physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer
TCP/IP four layer structure: application layer, transmission layer, network layer and data link layer
18, final modified methods cannot be overloaded
19, String s = new String("xyz"); Created several stringobjecs
1)If String Constant pool, created"xyz",The creation will not continue, and only one object is created at this time new String("xyz"),This is a Obeject Object;
2.If String Constant pool, not created"xyz",Two objects are created, one with a value of"xyz",An object new String("xyz"),There are two Obeject Object;
20, Under the premise of the following four statements:
Integer i01 = -128;
int i02 = -128;
Integer i03 =Integer.valueOf(-128);
Integer i04 = new Integer(-128);
The following output results are false:
i03 == i04 i03 Is a value from the cache, i04 Is new new The two are not the same object, so false. i02 == i04 because i02 Is a basic type, so at this time i04 The box will be opened automatically for value comparison, so the result is true.
21, Which of the following commands can shut down without restarting?
halt and netstat
22, Which of the following is part of the Linux boot process?
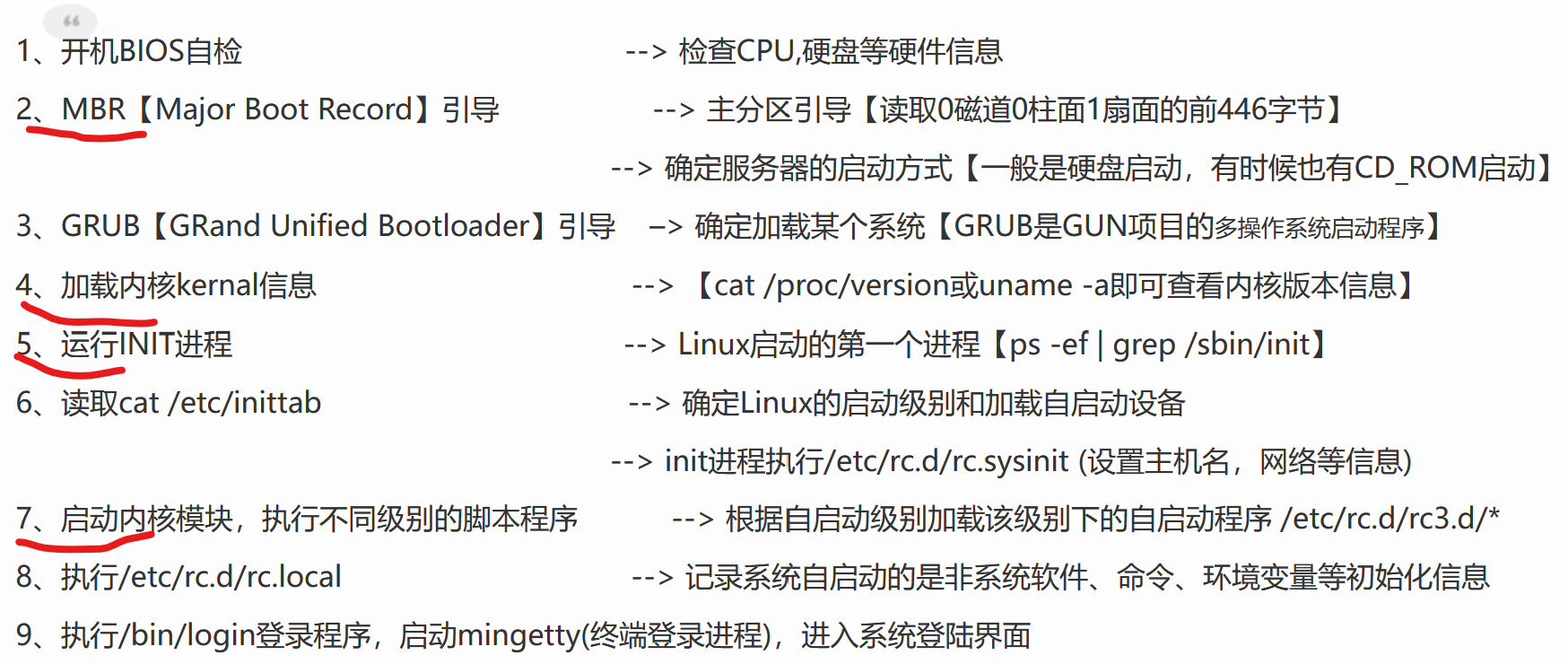
23, inode related knowledge
1.The area where file meta information is stored is called inode(Index node) 2.inode Contains the meta information of the file (all file information except the file name) 3.The file name contains special characters, which can be deleted directly inode,It can delete files 4.each inode The size of is generally 128 bytes or 256 bytes.
24, Which of the following symbols in bash are correct
$0 Represents the name of the script $@Represents all position parameters $# Represents the number of location parameters
25, The statements about DELETE and TRUNCATE TABLE are correct
The former can delete records of specified entries, while the latter cannot Delete the data of the whole table, truncate than delete More efficient
26, In the following statements, the filter conditions are vend id=1002 or vend id=1003
select * from products where vend_id=1002 or vend_ id=1003 select * from products where vend id in(1002, 1003)
27, Which of the following are TCP protocol runtime phases
Connection creation data transfer connection termination
28, Both asymmetric encryption and symmetric encryption are used in hypertext transmission security protocol
29, The following descriptions of daemon threads are correct:
If any non daemon thread does not end, the daemon thread will work all the time When the last non daemon thread ends, the daemon thread follows JVM Finish work together GC Is a daemon thread The new thread generated by the daemon thread is also the daemon thread
30, Modifiers for Java interfaces include
public final