Direct decompression of "flag.rar" found that there was a password, and the 4-6-bit password exploded unsuccessfully, indicating that the password was obtained from two other PNG pictures.
Directly take all pictures out of binwalk and break them down (binwalk-e 1.png), (binwalk-e 2.png)
Get a "password.xls" file and a "hint.txt" file, respectively
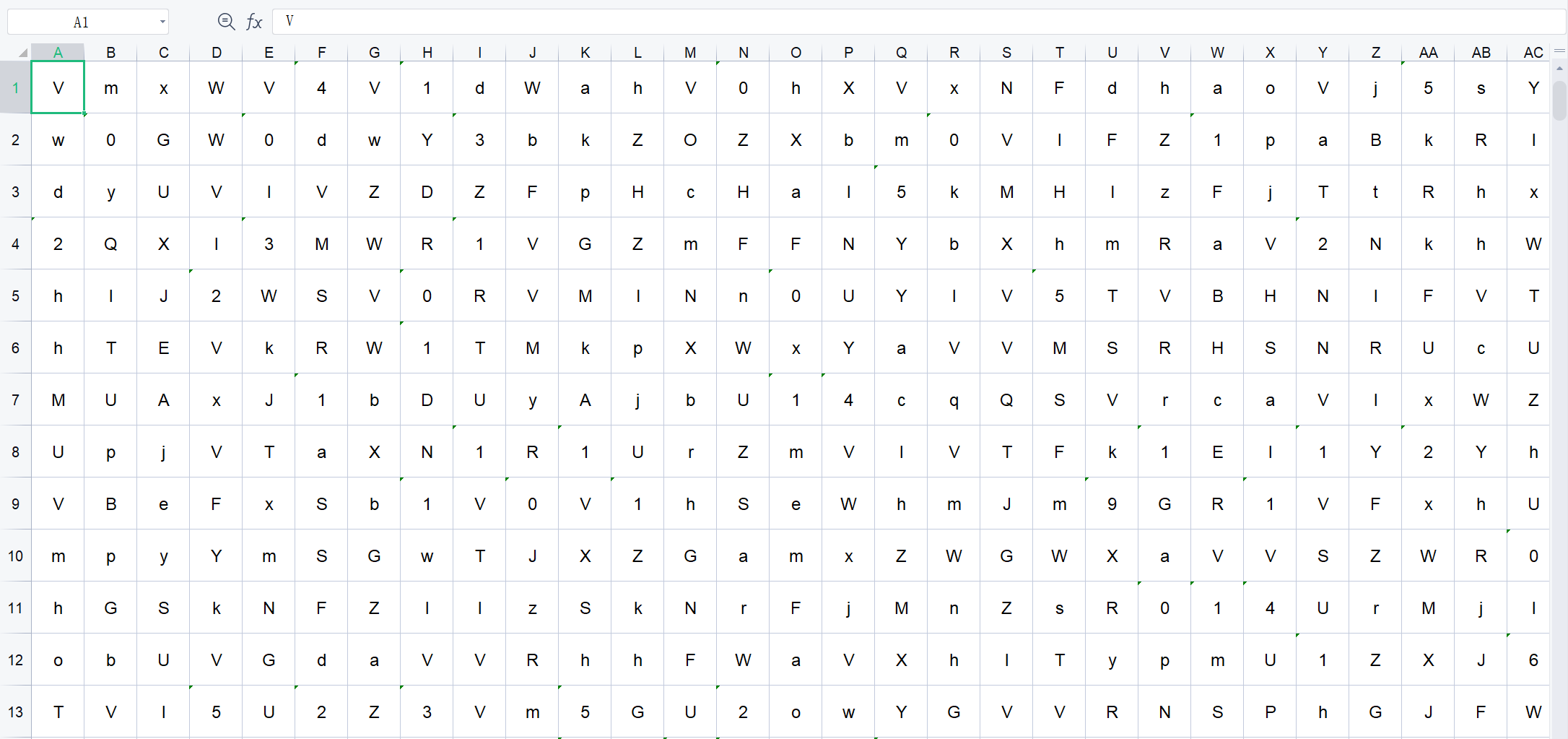
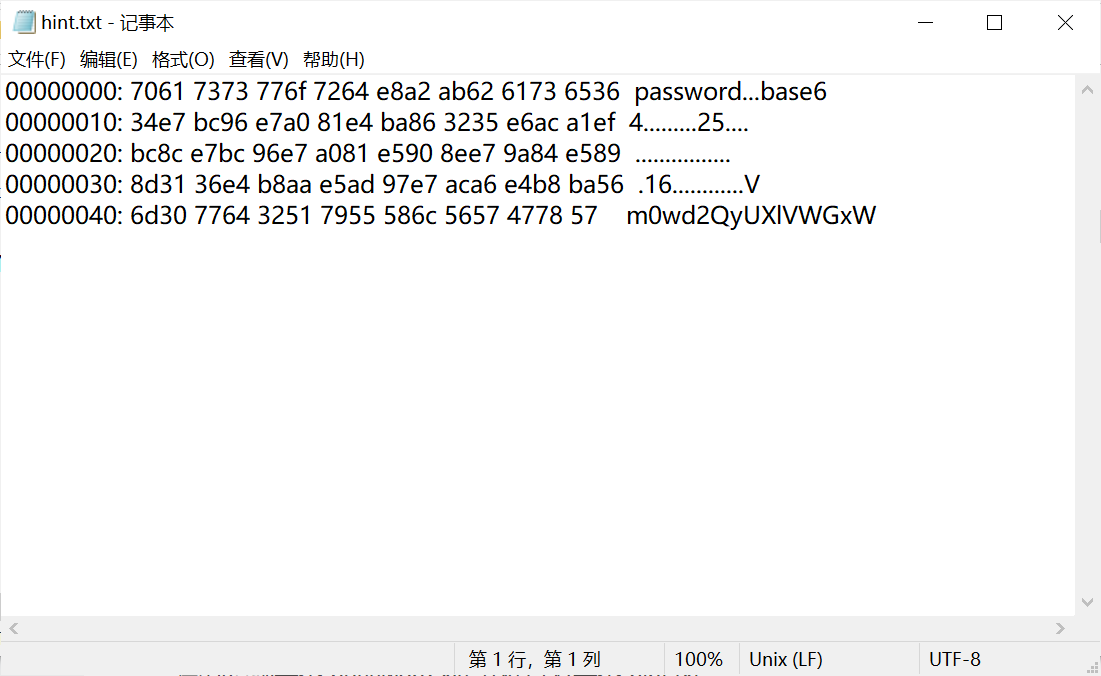
You can't read password.xls alone, but hint.txt is more obvious. There is base64 decoding, and there is information like encrypted "Vm0wd2QyUXlVWGxW". But you can't get any useful information by directly removing the decoding, so you should combine password.xls to get information.
Looking at it in general, we find that the message "Vm0wd2QyUXlVWGxW" is probably from password.xls, because password.xls contains most uppercase and lowercase letters and "=".
Looking closely, guess that the information "Vm0wd2QyUXlVWGxW" should not be complete, so find out how this information is portrayed in password.xls.
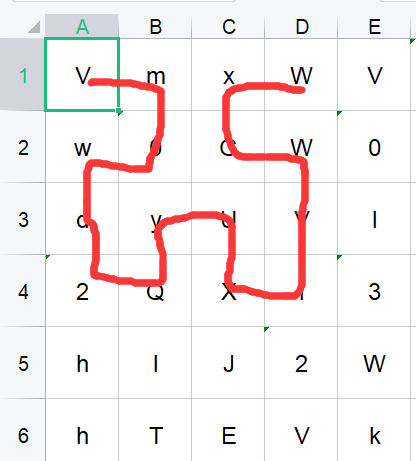
The discovery is a Hilbert curve, directly up the code:
import xlrd
from hilbertcurve.hilbertcurve import HilbertCurve
data=xlrd.open_workbook('./password.xls')
table=data.sheets()[0]
rows=table.nrows
cols=table.ncols
hilbert_curve = HilbertCurve(17, 2)
str1=''
for k in range(rows*cols):
[i,j]=hilbert_curve.point_from_distance(k)
str1+=table.cell_value(i,j)
#print(str1)
#Discovering too much data may cause the program to crash
#So writing files is more feasible.
file=open('base.txt','wb')
file.write(str1.encode())
file.close()
After writing the file, we get a large list of base64 codes, but we find a lot of'='at the end, so we need to manually adjust the data to remove only two or one equals sign.
Finally, decode with the program:
import base64
file=open('base.txt','r')
string=file.read()
while True:
string=base64.b64decode(string)
print(string)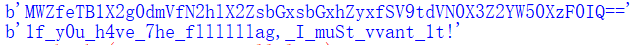
This "1f_y0u_h4ve_7he_fllllag, _I_muSt_vvant_1t!" is our unzip secret.
After successful decompression, you get a flag.php file and open it directly.
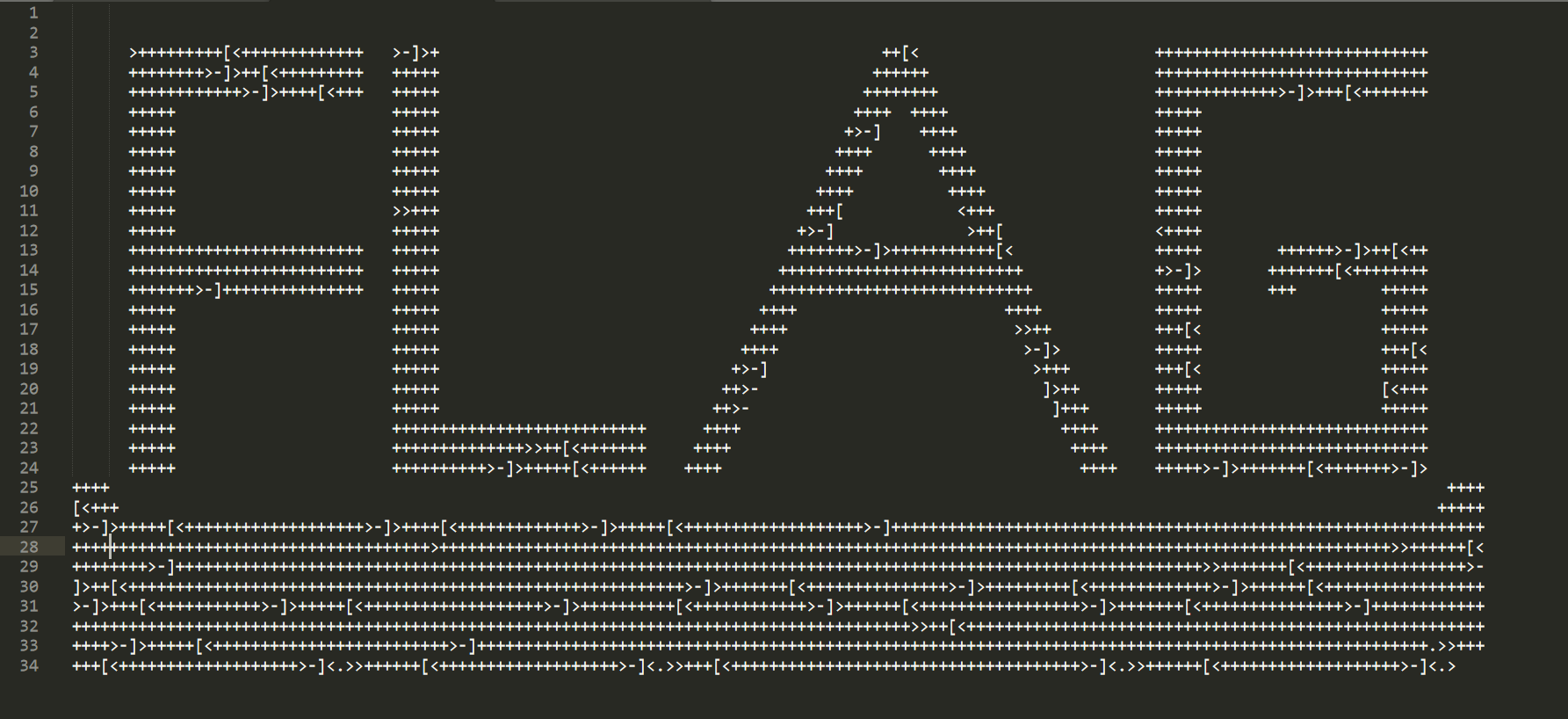
The obvious brainfuck(BF) password.
Directly take the decryption, found a mistake, and then refer to the practice of the big man is to take and see the stack of BF execution.
Directly CV all BF codes up,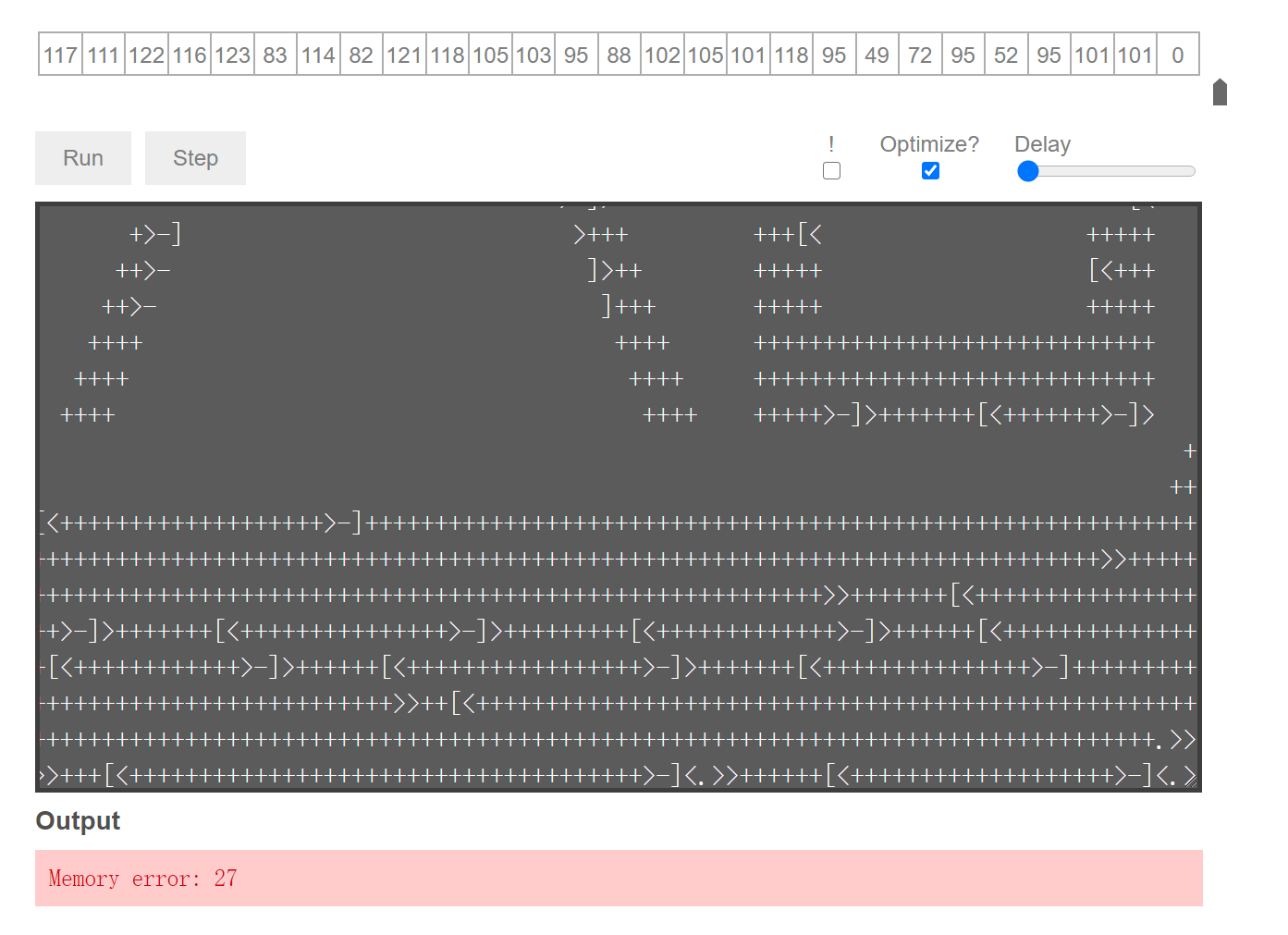
Found that the website is not long enough to report an error
This requires us to adjust it manually and link up the results in sections.
I started here
Because errors will be reported directly from line 27, you can refer to the BF principle. BF analysis

Simply stitch together to get:
117,111,122,116,123,83,114,82,114,82,121,118,105,103,95,88,102,105,101,118,95,49,72,95,49,72,95,52,95,101,101,48,109,119,118,105,117,102,33,95,120,102,105,101,118,125,101,114,114,111,114
Since none of them exceed 128, which are all printable characters, the guess is ASCII code.
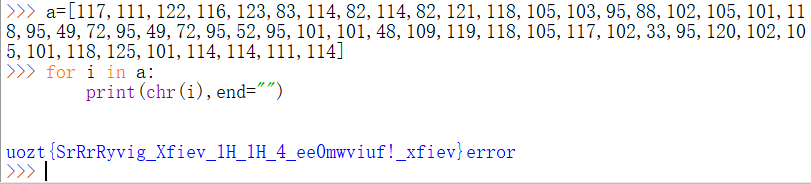
Compare the flag {xxxxxxx} form
=>'f'=>'u' , 'l'=>'o','a'=>'z','g'=>'t'
Obvious atbash password
list2=['a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z']
list3=['A','B','C','D','E','F','G','H','I','J','K','L','M','N','O','P','Q','R','S','T','U','V','W','X','Y','Z']
tmp=0
string=input("Input:")
output=''
for i in string:
if(i in list2):
tmp=list2.index(i) #Get Index
output+=list2[len(list2)-tmp-1]
elif(i in list3):
tmp=list3.index(i) #Get Index
output+=list3[len(list3)-tmp-1]
else:
output+=i
print(output)
Result: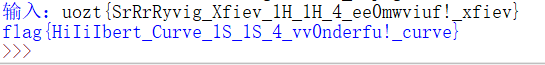
Reference Mumuzi Big Guys Blog The first Great Wall Cup Part WP_is Mumuzi's blog-CSDN blog