Generate certificates for WEB servers with openssl (self-signed CA certificates, server certificates)
Source: https://www.cnblogs.com/osnosn/p/10608455.html Come from osnosn's blog
Written in: 2019-03-28.
- Do not want to use self-signed certificate, want to apply for a free server certificate online, see this article: Apply for Freessl Server Certificate at freessl.org
The following content is to use self-signed certificates to generate server certificates for the website.
According to this article“ Use openssl to generate certificates for EAP-TLS (CA certificates, server certificates, user certificates) "Establish all documents.
openssl.cnf adds a few lines as follows. Used to match your server domain name, or IP.
openssl.cnf
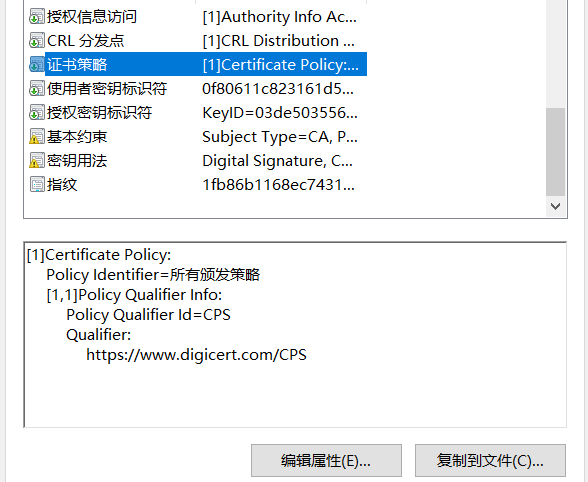
#openssl.cnf [ ca ] default_ca = hostapd [ hostapd ] dir = . serial = $dir/0serial database = $dir/2indexdb.txt new_certs_dir = $dir/3certs_new certificate = $dir/ca_cert.pem private_key = $dir/ca_key.pem RANDFILE = /dev/urandom default_bits = 4096 default_days = 36500 default_crl_days = 36500 default_md = sha512 #unique_subject = no policy = policy_anything [ policy_anything ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = supplied organizationalUnitName = optional commonName = supplied emailAddress = optional [ req ] distinguished_name = req_distinguished_name string_mask = utf8only [ req_distinguished_name ] [ v3_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical,CA:true certificatePolicies=ia5org,@pl_section [ server_cert ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = CA:false extendedKeyUsage = serverAuth,msSGC,nsSGC certificatePolicies=ia5org,@pl_section subjectAltName = @dns_names <---Newly added [ dns_names ] <---Newly added DNS.1 = my.domain.com <---Newly added DNS.2 = your.domain.net <---Newly added IP.1 = 1.2.3.4 <---Newly added IP.2 = 5.6.7.8 <---Newly added [ user_cert ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = CA:false #subjectAltName = email:copy extendedKeyUsage = clientAuth,emailProtection,timeStamping certificatePolicies=ia5org,@pl_section [ pl_section ] policyIdentifier = "X509v3 Any Policy" # Links to the issuer's instructions. In windows, trust is imported before it takes effect. CPS.1 = https://your.web.com/cps/readme.html userNotice.1=@pl_notice [ pl_notice ] # Issuer statment. does not support utf8 Chinese because ia5org. explicitText="Read deail at https://your.web.com/xxx.html"
userNotice.1 can only be written in English, but Chinese can be scrambled.
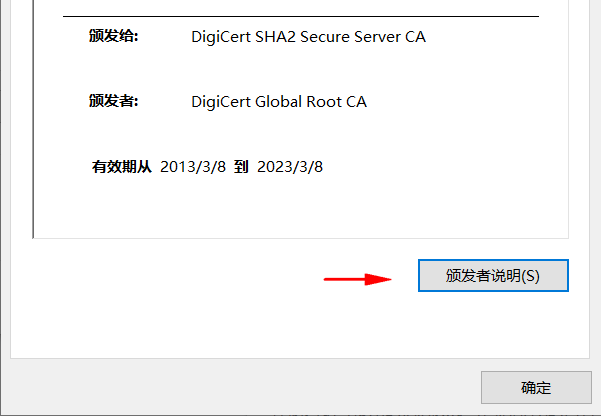
Text description, whether or not the certificate is trusted by the system, will appear in the Issuer Statement when viewing the certificate.
Links to CPS.1. When the system does not trust this certificate, it does not display. Trust will only appear in the Issuer Statement.
CPS.1 = can be either "http://" or "https://".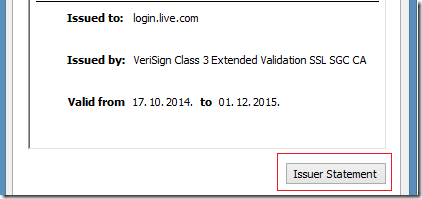
Only one domain name, just write DNS.1=, the rest is not.
There are multiple domain names, DNS.1=, DNS.2=, DNS.3=... DNS.9 is written in the configuration.=
Can write wildcard domain name, DNS.1=*.mydom.org,
All domains with. mydom. org will be matched. For example: abc.mydom.org, www.mydom.org...
But it does not match mydom.org
So wildcard domain names generally write two lines DNS.1 = mydom.org, DNS.2=*.mydom.org
Use only these two commands:
new-ca.sh creates a self-signed root certificate.
new-server.sh creates server certificates for the web.
These three files are the certificates needed to configure the web server.
ca_cert.pem , server_cert.pem , server_key.pem
If necessary, refer to the following instructions for certificate format conversion:
Convert pem to der format, (certificate, key)
Openssl x509-outform der-in server_cert.pem-out server.cer server certificate.
Openssl rsa-in server_key.pem-out form der-out server_key.cer server key.
Convert pem to P12 format, (certificate, key)
openssl pkcs12 -export -out ./server.p12 -inkey server_key.pem -in server_cert.pem -certfile ca_cert.pem
Transfer pem to pkcs#7 format, (certificate)
openssl crl2pkcs7 -nocrl -certfile server_cert.pem -out server.p7b
If you don't want to use self-signed certificates, go online and apply for a free server certificate. Apply for Freessl Server Certificate at freessl.org
Please indicate the source for reprinting.
Source: https://www.cnblogs.com/osnosn/p/10608455.html Come from osnosn's blog
--------- end ---------