See Essentials Through Phenomena - docker's four network modes, configuring docker's custom network while troubleshooting
Preface
The last article described resource control for docker, mainly in three areas: CPU, memory, and IO.This article describes the network mode in docker 4.
1. Brief description of three network modes in VMware
Perhaps, for many friends who are exposed to the Linux operating system, the first step is to learn in depth through virtual machine software.For one of these software, the network connection of VMware software may be a difficult problem for beginners.The principles and significance of the three network modes provided may not have been understood at all.This subsection then briefly describes the three network modes of VMware: Bridged, NAT, and Host-Only.These three types correspond to VMnet0, VMnet1 (or newly created later), VMnet8 (NAT network card can only have one)
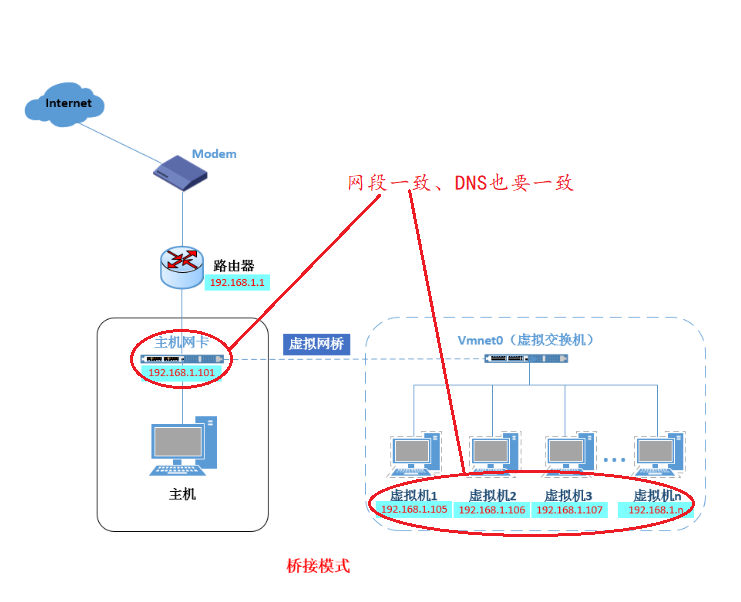
1.1 Bridge Mode
Concept: Bridge mode is the use of a virtual bridge to communicate between the network card of the host (like on your notebook) and the network card of the virtual machine.
Principle Understanding: The understanding of this mode can be thought of as a virtual switch in which all bridged virtual machines are connected to one interface of the switch. Of course, the physical machines also need to be connected to this switch, that is, all network cards in bridged mode are switching mode, accessible to each other and do not interfere with each other.
Typical features: The IP address of the virtual machine needs to be on the same network segment as the host, and if networking is required, the gateway and DNS need to be consistent with the host network card.
This can be explained in the following illustrations:
1.2 Network Address Translation Mode
NAT mode should be relatively familiar.Network address translation, since there is address translation, must have changed.NAT mode is better suited for situations where IP resources are scarce and virtual machines are expected to be networked.
NAT mode relies on virtual NAT devices and virtual DHCP servers, enabling virtual machines to connect to the network.As shown in the following figure:

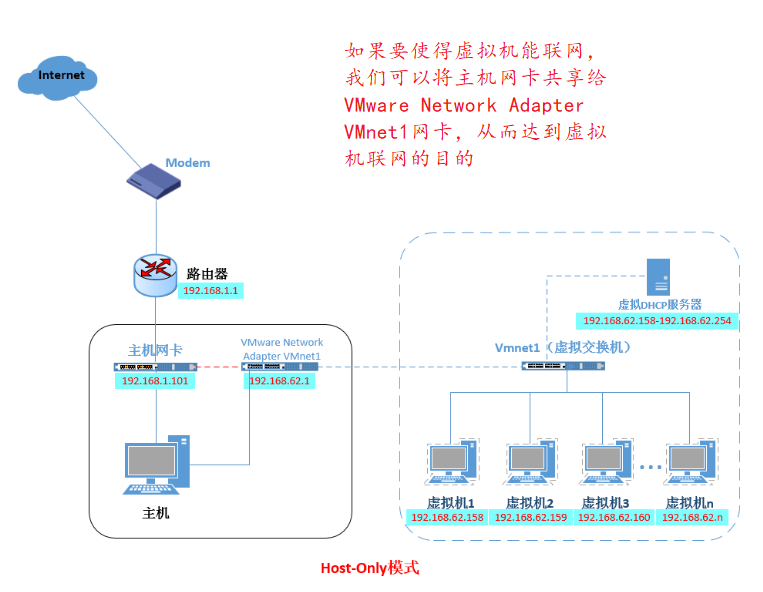
1.3 Host only mode
Host-only mode, in fact, is a network mode without NAT devices. It only uses VMnet1 virtual network card to connect with virtual switches to communicate with virtual machines. This mode achieves the isolation of virtual machines from external networks, that is, a single server that communicates with each other only.As shown in the following figure:
Okay, now you have a general idea of the three network modes in VMware. Now let's continue to talk about the network modes in docker.
2. Network mode of docker
2.1 docker network implementation principle
Doker uses Linux bridging, which means that the host machine virtual a docker container bridge (docker0), and when the docker starts a container, it assigns the container an IP address based on the segment of the docker bridge, which is the container ip, and the docker is the default gateway for each container.Therefore, containers within the same host can communicate directly through the container IP address.
Normally, after installing and starting the docker service, we can use the ifconfig command to view the virtual bridge device for this docker0:
[root@localhost ~]# ifconfig | head -7
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:58:71:c9:ba txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
From the results shown above, the default container gateway address is 172.17.0.1/16ha!Of course, loopback network cards are loopback network cards, test validation (TCP/IP connections), and virtual bridges are virtual bridges (think KVM [Native Cloud]
(Of course, docker bridges are virtual hosts, not real network devices. External networks cannot be directly addressed through IP addresses. This means that we need to make the external network accessible to the container in other ways, typically by accessing the ports of the host ip-bound container (and ports are typically mapped, which will be described later).Access to row containers.
4 network modes of 2.2 docker
The following table directly distinguishes the four docker network modes
| docker network mode | To configure | Explain |
|---|---|---|
| host | Container and host share Network namespace | |
| container mode | Container shares Network namespace with another container | |
| none mode | Containers have separate network namespaces but do not have any network settings for them, such as assigning Veth pairs and bridge connections, configuring IP, etc. | |
| bridge mode | Default mode |
Actually, after starting the docker service, you can use the docker network related commands to control the management network. Here's a list of the networks: (there are three by default). Here's a step-by-step description (combining the contents of the first section to understand the network principles in docker).
[root@localhost ~]# docker network ls NETWORK ID NAME DRIVER SCOPE 3763f78eb404 bridge bridge local 3bb2f50eb211 host host local e12cd7b98c54 none null local
2.2.1 host mode
The host mode is understood in conjunction with host-only mode in VMware, as illustrated in the following diagram:

From the diagram above, you can see that if the host mode is used after starting the container, the container will not get a separate Network Namespace (network namespace), but will share a Network Namespace with the host system.And that means the container will not dummy out its own network card, configure its own ip, etc. but will use the host's IP and port.However, it is isolated from other aspects, such as the file system.
The biggest advantage of this method is that the network performance is good, but the disadvantage is also obvious - the network isolation is weak.
2.2.2 container mode
This pattern, as described in the table above, means that a Network Namespace is shared between the specified newly created container and an existing container.This also means that the new container will not create its own network card and other related operations, but will share these resources with the specified container.
This mode is also similar to the host s described above, except for the network, its file system, process list, and so on are all isolated.
Refer to the following figure:

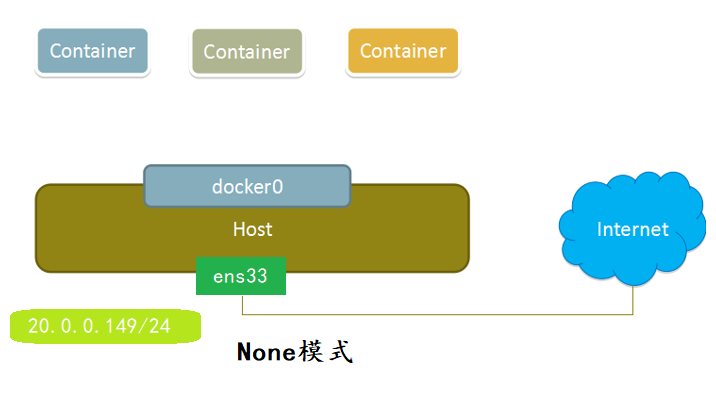
2.2.3none mode
With none mode, the Docker container has its own Network Namespace, but no network configuration will be made to the Docker container.This means that this Docker container does not have network card, IP, routing, etc.We need to add network cards, configure IP, etc. for the Docker container ourselves.This way the network is most completely isolated, meaning that the network functionality of the container is turned off and that the container is inaccessible.
The diagram is as follows:
2.2.4 bridge mode
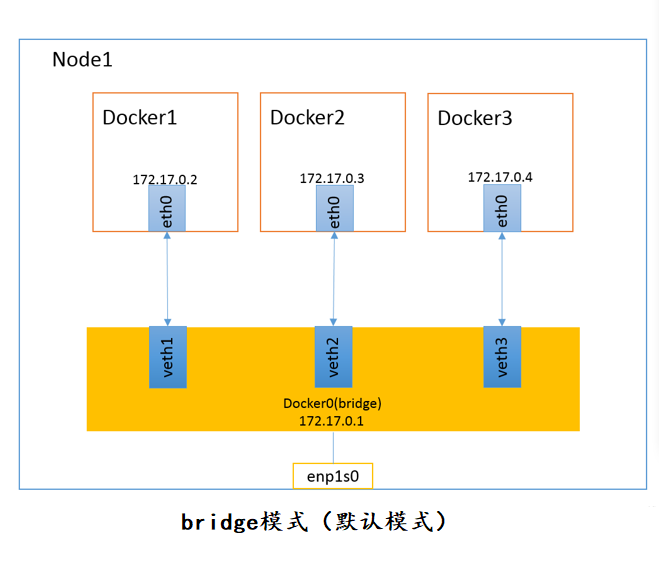
This mode is the default docker network mode after we start the docker service. It creates a virtual network bridge named docker0 on the host, and all the boot containers on this host are connected to this virtual network bridge.Combining the principle of bridge mode in VMware, it is easy to understand the principle of physical switch.
Assign an IP from the docker0 subnet to the container and set the IP address of the docker0 as the default gateway for the container.Create a pair of virtual network card veth pair devices on the host, Docker will VethThe pair device is placed in a newly created container (veth has seen us in OpenStack, and I think it can be understood as a bridge, a virtual device that establishes the relationship between the two sides of the bridge), named eth0 (the container's network card), and on the host, named vethxxx after something similar, and added this network device to docker0In the bridge.
When using the docker run-p command, docker actually makes DNA T rules in the firewall to implement port forwarding.
The following is an understanding of the server structure of a node:
Of course, none of these four modes need to be manually configured. What you really need to configure is a custom network.
3. Configuration of commands related to docker network control
The docker network command corresponding to the docker network control is given above. Here is a detailed description of the command:
docker network Command usage of: Usage: docker network COMMAND Manage networks Commands: connect Connect a container to a network create Create a network disconnect Disconnect a container from a network inspect Display detailed information on one or more networks ls List networks prune Remove all unused networks rm Remove one or more networks
3.1 Bridge Command Settings
We configure the docker network by experimenting, troubleshooting, and validating.
The firewall needs to be turned on because NAT address translation is required, but the core protection is off.
[root@localhost ~]# systemctl start firewalld.service
[root@localhost ~]# systemctl status firewalld.service
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled)
Active: active (running) since 2020-04-06 10:18:40 CST; 2s ago
Docs: man:firewalld(1)
Main PID: 65611 (firewalld)
...Initialize the environment: (returns to this environment state later)
[root@localhost ~]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE [root@localhost ~]# docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
Let's try to set an ip address (custom) to a container by docker bridge (bridging). Here's a look at the results of the command execution:
[root@localhost ~]# docker run -itd --name test --network bridge --ip 172.17.0.10 centos:7 /bin/bash Unable to find image 'centos:7' locally 7: Pulling from library/centos ab5ef0e58194: Pull complete Digest: sha256:4a701376d03f6b39b8c2a8f4a8e499441b0d567f9ab9d58e4991de4472fb813c Status: Downloaded newer image for centos:7 29f9e9cbb398085d7c89bed2982d626bfb7e564371a76a6cb693cffa68b917af docker: Error response from daemon: user specified IP address is supported on user defined networks only.
First, since the mirror is not altered, the container is pulled out, created, and attempted to run, but an error is encountered because the user's own ip address is only appropriate for the network they define.However, this does not affect the acquisition and creation of the mirror. Let's try running to see the results:
[root@localhost ~]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE centos 7 5e35e350aded 4 months ago 203MB [root@localhost ~]# docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 29f9e9cbb398 centos:7 "/bin/bash" About a minute ago Created test [root@localhost ~]# docker start 29f9e9cbb398 Error response from daemon: user specified IP address is supported on user defined networks only Error: failed to start containers: 29f9e9cbb398
Obviously, the result tells us that this is still the cause of the problem, so you can only delete this container.Let's just revert to the initialization environment (actually, you can remove it--the network bridge won't make a mistake, but the set ip address won't work, so try it yourself). We won't specify an ip address to try, we'll check that we don't add this parameter, and we'll set the ip address in a custom way after reverting to the initialization state.
[root@localhost ~]# docker run -itd --name demo centos:7 /bin/bash 984545df8ebf2c30f4ccf3f5f4699ed67bd2a93cbc068f2ace4865a828b4a4d1 [root@localhost ~]# docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 984545df8ebf centos:7 "/bin/bash" 8 seconds ago Up 6 seconds demo
Enter the container to view the ip address
[root@localhost ~]# docker exec -it 984545df8ebf /bin/bash
[root@984545df8ebf /]# yum install -y net-tools
Loaded plugins: fastestmirror, ovl
Determining fastest mirrors
[root@984545df8ebf /]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.2 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:ac:11:00:02 txqueuelen 0 (Ethernet)
RX packets 2201 bytes 15042254 (14.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1999 bytes 111171 (108.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
First, we need to create a custom subnet segment and give it a name by which to set a fixed ip address for the corresponding container.
[root@localhost ~]# docker network create --subnet=172.18.0.0/24 mynetwork Error response from daemon: Failed to Setup IP tables: Unable to enable SKIP DNAT rule: (iptables failed: iptables --wait -t nat -I DOCKER -i br-4cd28c051bec -j RETURN: iptables: No chain/target/match by that name. (exit status 1))
Unfortunately, error again, don't panic. Let's see what caused this error. It seems that the root cause of this error is the firewall, which means we can't skip the DNA T (Target Network Address Translation) rule. In fact, the cause of this problem is that we just opened the firewall, but did not restart the docker service, which is similar to changing the configuration file and not restarting the service.
[root@localhost ~]# systemctl restart docker [root@localhost ~]# docker network create --subnet=172.18.0.0/24 mynetwork 723d0fd514eb219d57667f72c3eb75fc4864af0cd94c21b6c70e868fb8d520a1
[root@localhost ~]# docker network ls NETWORK ID NAME DRIVER SCOPE 00008a1e778b bridge bridge local 3bb2f50eb211 host host local 723d0fd514eb mynetwork bridge local e12cd7b98c54 none null local [root@localhost ~]#
A test to verify custom settings for a container's fixed IP address is performed at this time:
[root@localhost ~]# docker run -itd --name test2 --network mynetwork --ip 172.18.0.10 centos:7 /bin/bash Unable to find image 'centos:7' locally 7: Pulling from library/centos ab5ef0e58194: Pull complete Digest: sha256:4a701376d03f6b39b8c2a8f4a8e499441b0d567f9ab9d58e4991de4472fb813c Status: Downloaded newer image for centos:7 683ad76f7789b5c16f251577047a288a3a4a00777128a216adfee15985b94c04
View the status of the container, enter the container to view the ip address
[root@localhost ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
683ad76f7789 centos:7 "/bin/bash" 23 seconds ago Up 22 seconds test2
[root@localhost ~]# docker exec -it 683ad76f7789 /bin/bash
[root@683ad76f7789 /]# yum install -y net-tools
Loaded plugins: fastestmirror, ovl
...
[root@683ad76f7789 /]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.18.0.10 netmask 255.255.255.0 broadcast 172.18.0.255
ether 02:42:ac:12:00:0a txqueuelen 0 (Ethernet)
RX packets 2302 bytes 15050471 (14.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2049 bytes 113777 (111.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 62 bytes 7019 (6.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 62 bytes 7019 (6.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
The custom network settings container ip address was found to be successful.
4. Summary
In this paper, the working principle of three network modes in VMware software is explained, docker's various network modes are explained step by step, and how docker bridge mode configures container ip address, default mode and customized mode are described in detail through a case combined with troubleshooting ideas.
Finally, it is important to note whether the commands need to be remembered, typed and practiced. Thank you for reading!