1. Introduction to ingress service
A global load balancing Service set to proxy different backend services is the Ingress Service in Kubernetes.
Ingress consists of two parts: Ingress controller and ingress service.
The Ingress Controller will provide corresponding proxy capabilities according to the Ingress object you define. Various reverse proxy projects commonly used in the industry, such as Nginx, HAProxy, Envoy, traifik, etc., have specially maintained the corresponding progress controller for Kubernetes.
The use of ingress service can only be realized in the policy network, such as calico network
Ingress is equivalent to a 7-tier load balancer and is k8s an abstraction of reverse proxy. The general working principle is indeed similar to Nginx. It can be understood as establishing mapping rules in ingress. The ingress controller listens to the configuration rules in the API object of ingress and converts them into Nginx configuration (kubernetes declarative API and control loop), and then provides services to the outside. Inress includes: inress controller and inress resources
ingress controller: the core is a deployment. There are many ways to implement it, such as nginx, contour, haproxy, trafik and istio. The yaml s to be written include deployment, service, configmap and serviceaccount (Auth). The type of service can be NodePort or LoadBalancer.
ingress resources: This is an k8s api object of type ingress, and this part is for developers.
2.ingress deployment
mkdir ingress
cd ingress/
Download the required deploy.yaml
 vi deploy.yaml
vi deploy.yaml
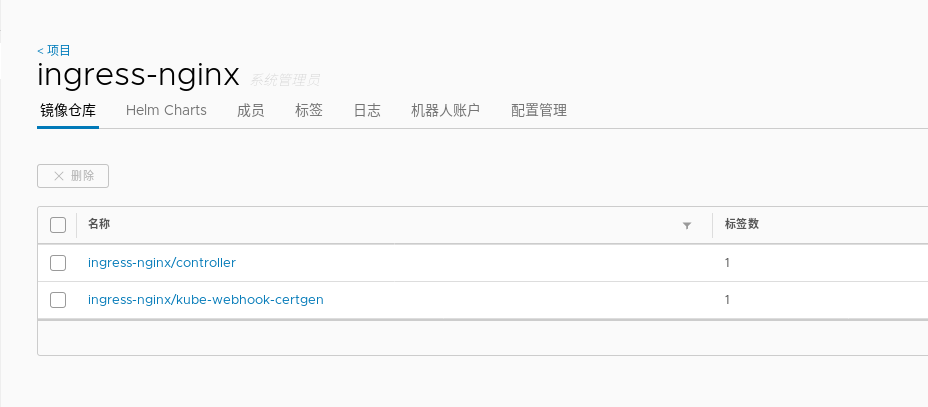
image: ingress-nginx/controller:v1.0.3 image: ingress-nginx/kube-webhook-certgen:v1.5.1
Add a public project, ingress nginx, in your own warehouse to store the relevant images
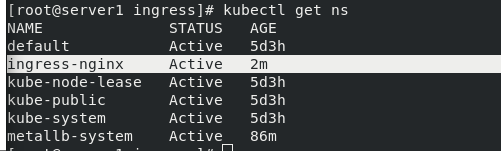
Execute the deploy.yaml list to view the ns status
kubectl apply -f deploy.yaml kubectl get ns
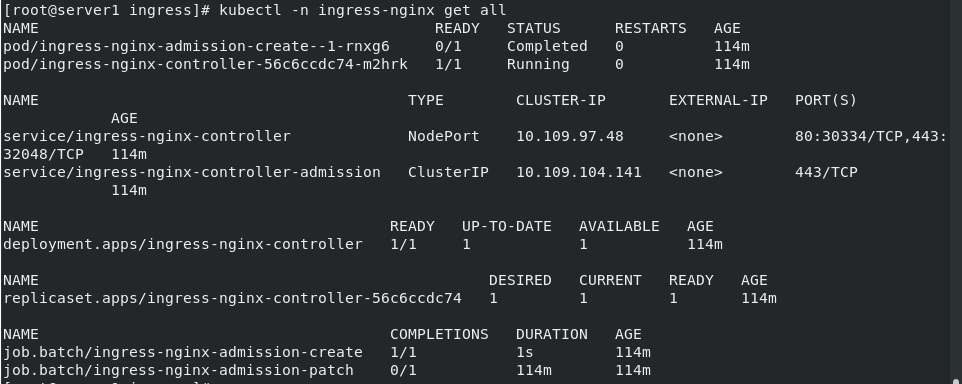
 After viewing all the information of ingress nginx, you can see that the ingress nginx controller has been running
After viewing all the information of ingress nginx, you can see that the ingress nginx controller has been running
kubectl -n ingress-nginx get all
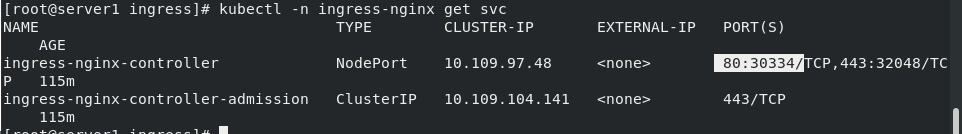
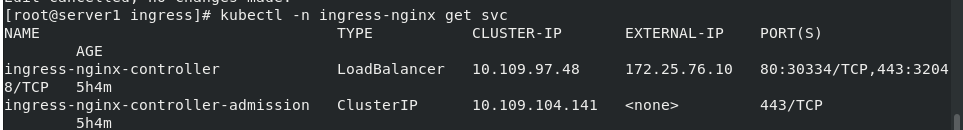
View svc exposed ports
kubectl -n ingress-nginx get svc
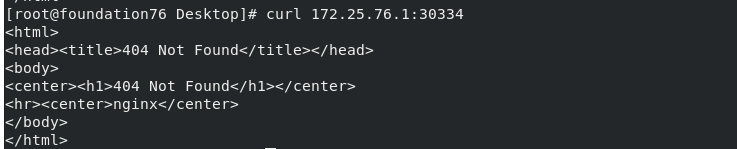
Test: access server1ip address plus port
3. Domain name access + ingress nginx (configure ingress nginx seven layer balance)
3.1 create pod: nginx myapp
vi deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: myapp:v1
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: myapp-deployment
labels:
app: myapp
spec:
replicas: 3
selector:
matchLabels:
app: myapp
template:
metadata:
labels:
app: myapp
spec:
containers:
- name: myapp
image: myapp:v2
Pull up deployment and lock the domain name through the tag

3.2 configuring and adding svc services
vi svc.yaml
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: nginx
---
apiVersion: v1
kind: Service
metadata:
name: myapp-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: myapp
Pull up the service and view the endpoint
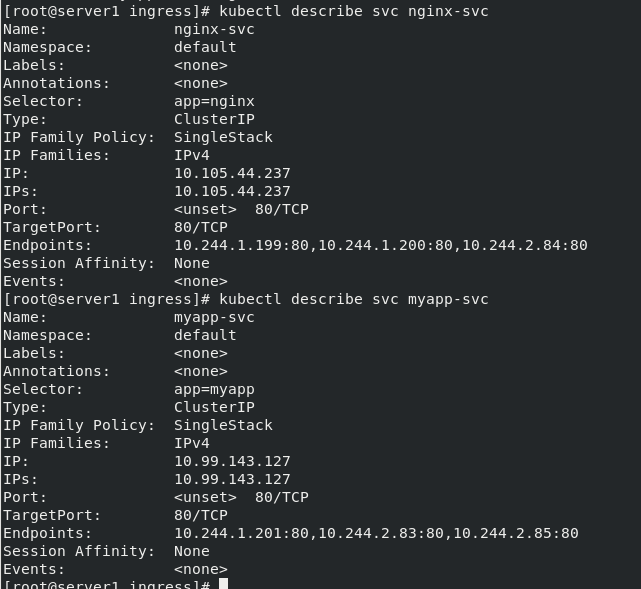 Apply yaml file and create service
Apply yaml file and create service
kubectl apply -f svc.yaml
View service information
kubectl get svc
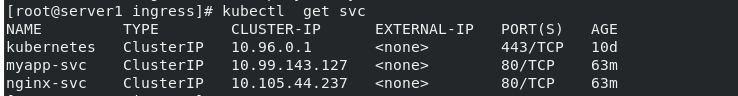
Modify the svc configuration file to load balancing
kubectl -n ingress-nginx edit svc ingress-nginx-controller
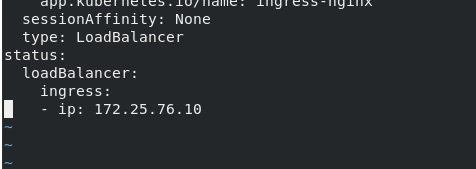
View modifications
kubectl -n ingress-nginx get svc
External IP is 172.25.76.10
 3.3 connect the service to ingress and give the domain name to match the service
3.3 connect the service to ingress and give the domain name to match the service
vi ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-nginx
spec:
rules:
- host: www1.westos.org
http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: nginx-svc
port:
number: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-myapp
spec:
rules:
- host: www2.westos.org
http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: myapp-svc
port:
number: 80
Pull up resource list
kubectl apply -f ingress.yaml
Viewing ingress reverse proxy information
kubectl get ingress
Add the test machine to the service node 172.25.76.10
vi /etc/hosts 172.25.76.10 www1.westos.org www2.westos.org
Access test:
[root@foundation76 ingress]# curl www2.westos.org Hello MyApp | Version: v2 | <a href="hostname.html">Pod Name</a> [root@foundation76 ingress]# curl www1.westos.org Hello MyApp | Version: v1 | <a href="hostname.html">Pod Name</a>
4.Ingress certification
Because authentication requires the authentication function of the system!
Therefore, you need to install the plug-in to generate authentication integers
yum install -y httpd-tools
4.1. Generate certificate
Generate a certificate and enter the authentication password
Create certificate to k8s secret
htpasswd -c auth lcf #Generate a certificate and enter the authentication password kubectl create secret generic basic-auth --from-file=auth # Create certificate to k8s secret kubectl get secrets
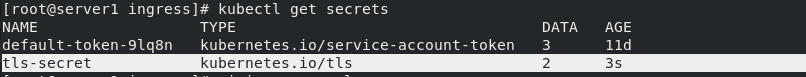 Edit the file ingress.yaml to import the certificate
Edit the file ingress.yaml to import the certificate
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-nginx
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - lcf'
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: nginx-svc
port:
number: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-myapp
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - lcf'
spec:
tls:
- hosts:
- www2.westos.org
secretName: tls-secret
rules:
- host: www2.westos.org
http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: myapp-svc
port:
number: 80
Execute the ingress.yaml file
kubectl apply -f ingress.yaml
Access test
curl -k https://www1.westos.org -u lcf:westos Hello MyApp | Version: v1 | <a href="hostname.html">Pod Name</a>
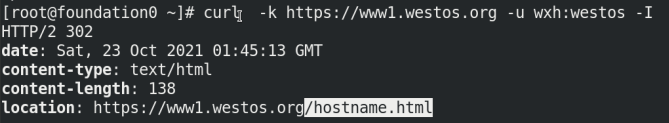
5. Redirection
5.1. Redirect to / hostname.html
Modify the file ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-nginx
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - lcf'
nginx.ingress.kubernetes.io/app-root: /hostname.html
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: nginx-svc
port:
number: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-myapp
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - lcf'
nginx.ingress.kubernetes.io/app-root: /hostname.html
spec:
tls:
- hosts:
- www2.westos.org
secretName: tls-secret
rules:
- host: www2.westos.org
http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: myapp-svc
port:
number: 80
Execute the file ingress.yaml again to view the information:
kubectl apply -f ingress.yaml kubectl describe ingress

Visit www1.westos.org and find that it is automatically redirected to www1.westos.org/hostname.html