preface
The simulated Login operation of station B is realized by selenium. No more nonsense. Let's start happily~
Effect demonstration
development tool
Python version: 3.6 four
Related modules:
selenium module;
And some python built-in modules.
Chromedriver:
Download the driver matching the Google browser version on your computer in the following link:
http://npm.taobao.org/mirrors/chromedriver/
Environment construction
Install python and add it to the environment variable. pip can install the relevant modules required.
Principle introduction
First, let's instantiate a webdriver Chrome object, which is used to automate the operation of Google browser in our computer:
browser = webdriver.Chrome(executable_path=chromedriverpath, options=chrome_opts)
Next, we use it to automatically access the login interface of station B:
browser.get('https://passport.bilibili.com/login')
And automatically fill in the following user name and password:
driver_wait = WebDriverWait(browser, 30) username_sender = driver_wait.until(EC.presence_of_element_located((By.XPATH, '//*[@id="login-username"]'))) username_sender.send_keys(username) password_sender = driver_wait.until(EC.presence_of_element_located((By.XPATH, '//*[@id="login-passwd"]'))) password_sender.send_keys(password)
The input boxes of user name and password are directly located by xpath
Then simulate clicking the login button to enter our Slider verification code cracking link, in which time is added Sleep (3) is to ensure that the slider verification code pops up smoothly:
button = driver_wait.until(EC.presence_of_element_located((By.XPATH, '//a[@class="btn btn-login"]'))) button.click() time.sleep(3)
The slider verification code of station B is about this long:
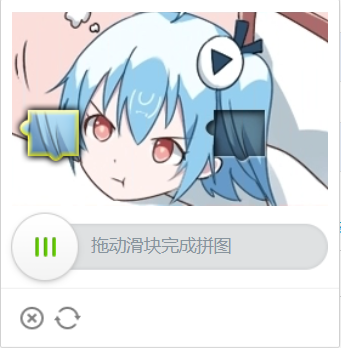
You just need to drag the slider to the corresponding notch position. The difficulty of the problem is how to determine the notch position. The simplest, crude and effective way is naturally to directly compare the original picture of the verification code with the picture with the notch, so as to obtain the notch position. For station B, you can realize this way. First, obtain the original diagram of verification code:
image_ori = browser.execute_script('return document.getElementsByClassName("geetest_canvas_fullbg")[0].toDataURL("image/png");')
image_ori = image_ori.split(',')[1]
image_ori = base64.b64decode(image_ori)
image_ori = Image.open(io.BytesIO(image_ori))
Similarly, obtain the diagram of verification code with notch:
image_gap = browser.execute_script('return document.getElementsByClassName("geetest_canvas_bg")[0].toDataURL("image/png");')
image_gap = image_gap.split(',')[1]
image_gap = base64.b64decode(image_gap)
image_gap = Image.open(io.BytesIO(image_gap))
The pixel matrices of the two images are then compared to obtain the notch coordinates:
gap_pos = []
for i in range(image_ori.size[0]):
if gap_pos:
break
for j in range(image_ori.size[1]):
pixel_ori = image_ori.getpixel((i, j))
pixel_gap = image_gap.getpixel((i, j))
if abs(pixel_ori[0] - pixel_gap[0]) > 10 and abs(pixel_ori[1] - pixel_gap[1]) > 10 and abs(pixel_ori[2] - pixel_gap[2]) > 10:
gap_pos = [i, j]
break
After obtaining the notch coordinates, we only need to use the browser to control the slider to move to the position of the notch:
slider = driver_wait.until(EC.presence_of_element_located((By.XPATH, '/html/body/div[2]/div[2]/div[6]/div/div[1]/div[2]/div[2]')))
ActionChains(browser).click_and_hold(on_element=slider).perform()
tracks = TrackGenerator.getTracksByExpfunc(distance * 0.93)
for delta_dis in tracks:
ActionChains(browser).move_by_offset(xoffset=delta_dis, yoffset=0).perform()
ActionChains(browser).pause(0.5).release().perform()
The motion trajectory of the slider can be simulated by an exponential function:
def getTracksByExpfunc(distance, delay=5):
tracks = []
offset = 0
for i in np.arange(0.1, delay, 0.1):
delta_dis = round((1 - pow(2, -10 * i / delay)) * distance) - offset
tracks.append(delta_dis)
offset += delta_dis
tracks[-1] += (distance - offset)
return tracks
This is the end of the article. Thank you for watching the 24 game series of Python. The next article shares Python+Selenium decoding the slider verification code of station B
In order to thank readers, I would like to share some of my recent collection of programming dry goods with you and give back to every reader. I hope I can help you.
Dry goods mainly include:
① More than 2000 Python e-books (both mainstream and classic books should be available)
② Python standard library materials (the most complete Chinese version)
③ Project source code (forty or fifty interesting and classic hand training projects and source code)
④ Videos on basic introduction to Python, crawler, web development and big data analysis (suitable for Xiaobai)
⑤ Python learning roadmap (bid farewell to non stream learning)
All done ~ get the complete source code by private letter..
Previous review