1, ThreadLocal [resolve shared variables]
1.ThreadLocal is called thread variable, which means that the variable filled in ThreadLocal belongs to the current thread. This variable is isolated from other threads, that is, this variable is unique to the current thread. ThreadLocal creates a copy of the variable in each thread, so each thread can access its own internal copy variable.
2. Make sure that each thread does not access the same object at a certain time, which isolates the data sharing of multiple threads.
3.ThreadLocalMap is the internal static class of ThreadLocal, and its composition mainly uses Entry to save data, and it is also an inherited weak reference. In the Entry, ThreadLocal is used as the key and the value we set is used as the value
Dirty data
Because the Thread pool will reuse the Thread object, the ThreadLocal variable without the static attribute of the class bound to the Thread will also be reused. If the remove() method is not obviously substituted in the ready-made run () method, it may get (important Thread information)
Memory leak
In fact, the key used in ThreadLocalMap is the weak reference of ThreadLocal. The feature of weak reference is that if this object has only weak reference, it will be cleaned up in the next garbage collection.
ThreadLocal has three methods. get set remove and finally remove must be executed. Otherwise, memory leakage will occur, because the prompt indicates static and ThreadLocal modification
Usage scenario
1. Each thread needs to have its own separate instance
2. Instances need to be shared in multiple methods, but do not want to be shared by multiple threads
Store user Session
Database connection, processing database transactions
2, explain sql statement
We can know the following information: the reading order of the table, the type of data reading operation, which indexes can be used, which indexes are actually used, references between tables, how many rows of each table are queried by the optimizer, etc.
Add the explain keyword before the select statement. MySQL will set a flag on the query. When executing the query, the execution plan information will be returned instead of executing the SQL (if the from contains a subquery, the subquery will still be executed and the results will be placed in the temporary table).
mysql> explain select * from actor; +----+-------------+-------+------+---------------+------+---------+------+------+-------+ | id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra | +----+-------------+-------+------+---------------+------+---------+------+------+-------+ | 1 | SIMPLE | actor | ALL | NULL | NULL | NULL | NULL | 2 | NULL | +----+-------------+-------+------+---------------+------+---------+------+------+-------+
1.id column
The number of the id column is the serial number of the select. If there are several selections, there are several IDS, and the order of IDS increases in the order in which the select appears. MySQL divides select query into simple query and complex query. Complex queries are divided into three categories: simple subqueries, derived tables (subqueries in the from statement) and union queries.
1) Simple subquery
mysql> explain select (select 1 from actor limit 1) from film; +----+-------------+-------+-------+---------------+----------+---------+------+------+-------------+ | id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra | +----+-------------+-------+-------+---------------+----------+---------+------+------+-------------+ | 1 | PRIMARY | film | index | NULL | idx_name | 32 | NULL | 1 | Using index | | 2 | SUBQUERY | actor | index | NULL | PRIMARY | 4 | NULL | 2 | Using index | +----+-------------+-------+-------+---------------+----------+---------+------+------+-------------+
2) Subquery in from clause
mysql> explain select id from (select id from film) as der; +----+-------------+------------+-------+---------------+----------+---------+------+------+-------------+ | id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra | +----+-------------+------------+-------+---------------+----------+---------+------+------+-------------+ | 1 | PRIMARY | <derived2> | ALL | NULL | NULL | NULL | NULL | 2 | NULL | | 2 | DERIVED | film | index | NULL | idx_name | 32 | NULL | 1 | Using index | +----+-------------+------------+-------+---------------+----------+---------+------+------+-------------+
2.select_type column
select_type indicates whether the corresponding row is a simple or complex query. If it is a complex query, which of the above three complex queries is it.
1) Simple: simple query. The query does not contain subqueries and union s
mysql> explain select * from film where id = 2; +----+-------------+-------+-------+---------------+---------+---------+-------+------+-------+ | id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra | +----+-------------+-------+-------+---------------+---------+---------+-------+------+-------+ | 1 | SIMPLE | film | const | PRIMARY | PRIMARY | 4 | const | 1 | NULL | +----+-------------+-------+-------+---------------+---------+---------+-------+------+-------+
2) primary: the outermost select in a complex query
3) Subquery: subquery contained in the select (not in the from clause)
4) Derived: the subquery contained in the from clause. MySQL will store the results in a temporary table, also known as a derived table
5) Union: the second and subsequent select in the union
6) union result: select to retrieve the result from the union temporary table
3. table column
This column indicates which table a row of explain is accessing.
4. type column
This column represents the association type or access type, that is, MySQL determines how to find rows in the table.
eq_ref: all parts of the primary key or unique key index are used by connection, and only one qualified record will be returned at most. This is probably the best join type other than const. This type will not appear in simple select queries
5. possible_keys column
This column shows which indexes the query may use to find.
6. key column
This column shows which index mysql actually uses to optimize access to the table.
7. key_len column
This column shows the number of bytes used by mysql in the index. Through this value, you can calculate which columns in the index are used.
8.ref column
This column shows the columns or constants used by the table to find the value in the index of the key column record. The common ones are: const (constant), func, NULL, and field name (for example: film.id)
9.rows column
This column is the number of rows that mysql estimates to read and detect. Note that this is not the number of rows in the result set.
10.Extra column
This column shows additional information.
3, Red black tree? Different from AVL?
Similar to the balanced binary search tree, red black tree maintains its own balance through specific rotation when inserting and deleting element nodes, so as to obtain high new query energy.
1. Node energy application lion red and black
2. The root node must be black
3. All NIL nodes are black. [two virtual nodes hanging under the leaf node]
4. Two adjacent red nodes cannot appear on a path
5. In any subtree, the number of black nodes in all paths from the root node to the leaf node is the same.
difference
1. The balance of red black tree is not as good as AVL, which is roughly balanced. The strict height difference between the left and right subtrees is not guaranteed to be 1, which may be higher, and the average search times avoid AVL more.
2. When inserting, rotate at most twice to restore balance
3. When deleting, the red black tree can be balanced at most three times, and AVL is align times
4. Red black tree is more suitable for frequent insertion and deletion
5.AVL is more suitable for low modification, deletion and large number of queries
4, Strong reference, soft reference, weak reference and virtual reference [Alibaba manual]

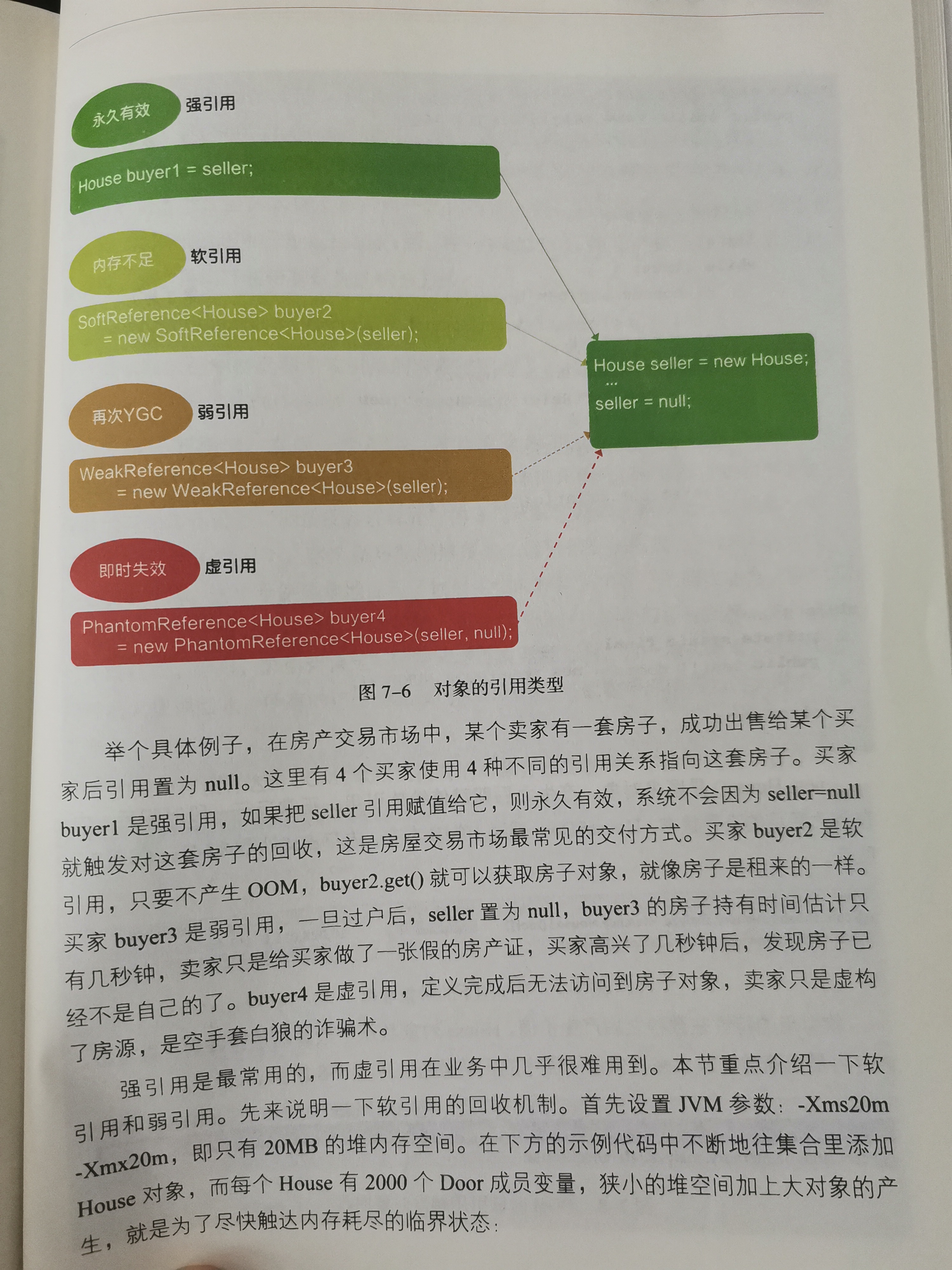
5, The CPU of the program suddenly burst. How to locate it?
1. Use the top command to determine which thread occupies too much memory
2. If it is your own Java program thread, use the thread command: view the details of a thread to determine whether it is a business thread or a GC garbage collection thread
3.jmap -histo process number: print all the objects in the jvm to see which object takes up more space; And check whether the log has OUTOFMEMORY
4. Using jinfo tool, you can modify the parameters, generate a snapshot, that is, dump file, and download it to windows environment
5. Open the visual VM tool for analysis and locate the problematic code block in combination with the object printed by the jmap command
6. Locate the cause of the problem by combining the analysis results and codes
6, Have you done a lot of network packet capturing of data? What is the general process?
nothing
7, LRU algorithm hash table and bidirectional linked list
Idea: in the linked list, insert a new node and put it directly into the header. If the accessed node is not hit in the table, move the node to the header. If the access fails, create a new node and put it in the header. If the chain expression reaches the maximum value, delete the last node, and the last node is the least unused recently.
8, DNS load balancing, long and short connections
The implementation principle of DNS load balancing technology is to configure multiple IP addresses for the same host name in the DNS server. When answering DNS queries, the DNS server will return different resolution results according to the IP addresses recorded in the DNS file for each query, and guide the access of clients to different machines, so that different clients can access different servers, So as to achieve the purpose of load balancing.
Main advantages
The main disadvantages of this technology are as follows
First, the technology is flexible, convenient, simple and low-cost, which is suitable for most TCP/IP applications. Network experts are not required to set it up or maintain it in case of problems.
Second, for Web applications, there is no need to make any changes to the code. In fact, the Web application itself is not aware of the load balancing configuration, even in front of it.
Third, the Web server can be located anywhere on the Internet.
When DNS load balancing technology has the above advantages, its disadvantages are also very obvious, mainly in
First, the load cannot be distributed according to the processing capacity of the Web server.
Second, it does not support high reliability, and DNS load balancing technology does not consider fault tolerance.
Third, it may cause additional network problems.
Fourth, once a server fails, even if the DNS settings are modified in time, it still needs to wait enough time (refresh time) to function. During this period, the client computer that saved the address of the failed server will not be able to access the server normally.