Learn from Mr. Tang zuolin
refine:
You can jump between code segments (privilege level switching) without using the call gate (jump from low privilege level to high privilege level) and TSS task status segment (jump from high privilege level to low privilege level). What you use is the basis for privilege level protection of code segments in the protection mode, that is, the rules of consistent code segments and inconsistent code segments.
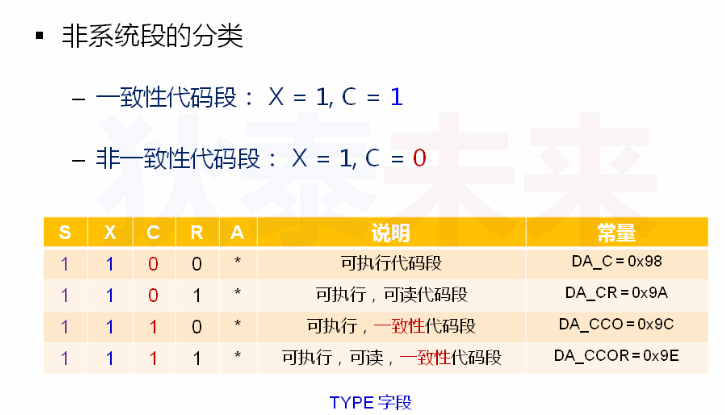
1 for non-conforming code segments, you can only transfer at the same level
Other code snippets of the same privilege level (not limited to consistent or inconsistent) -- jump to - > current inconsistent code snippet
2 for consistent code segments, the transfer from low privilege level to high privilege level consistent code segments is supported, but!!! But the CPL remains unchanged after the transfer!!!
Jump to the high privilege level through the call gate normally, and the code segment CPL will be assigned as the DPL of the current memory segment, but this is not applicable to the consistent code segment!!!
Other low (same) privilege level code segments ---- jump to - > current high privilege level consistency code segment
3 when the privilege level is reduced and transferred, that is, when the retf instruction is executed, it will trigger the processor to check the privilege level of the stack segment directly through the RPL in the selector. Specifically, the privilege level RPL of the selector request of SS should be equal to the privilege level RPL of the selector request of the code segment
4. The consistent code segment can jump directly to other non consistent code segments at the same level for execution
There is no essential difference between the code in the consistent code segment and the code in the non consistent code segment. These two code segments only use different legitimacy judgment rules when jumping. Therefore, the direct peer jump from the consistent code segment to the non consistent code segment is legal
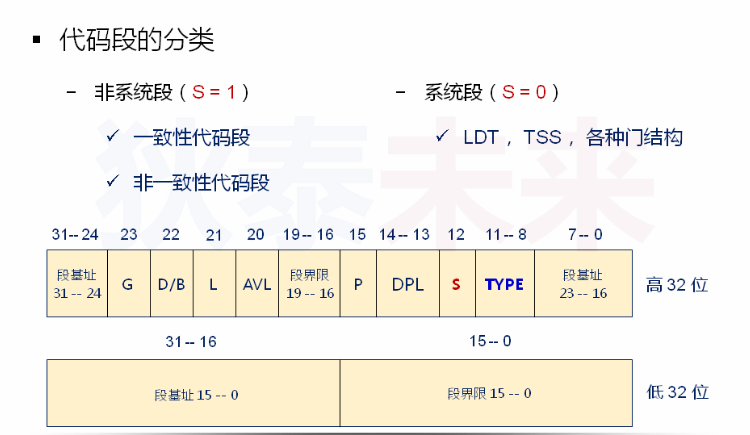
The distinction between system segment and non system segment is to look at the 12th bit of the high 32 bits in the memory structure of segment descriptor. Note that the system segment and non system end mentioned here refer not to the operating system, but to the processor itself. For example, the specific point of system segment is local segment description schedule, TSS task status segment, etc. the feature is that the processor needs them to complete some key functions, For example, LDT and TSS are the basis of multi task implementation, so they are system segments
Non system segment refers to the commonly defined code segment and data segment. For code segment, it is divided into consistent code segment and non consistent code segment
The Type field in the memory structure of segment descriptor: the 8th - 11th bits of the upper 32 bits to judge whether the consistency code segment is the value of C bit
The jump here does not need to call the gate descriptor!!!
The difference between consistent code segments and inconsistent code segments is mainly reflected in the jump between code segments
If you want to jump to a non-conforming code segment, you must meet the following two conditions:
CPL == DPL current code segment executable privilege level = = target memory segment privilege level
RPL < = DPL target memory selection sub request privilege level is higher than target memory privilege level
Horizontal jump
If you want to jump to the consistent code segment, you only support the transfer from the low (same) privilege level code to the high privilege level consistent code segment. That is, the condition for successful jump is CPL > = DPL, that is, the executable privilege level of the current code segment is lower than or equal to the privilege level of the target memory segment. On the surface, this is very powerful. Without the help of the call gate descriptor, Jump directly from the low privilege level to the high privilege level. Although you can jump directly, the CPL privilege level will not change after the jump. For example, if you want to jump from a code segment with privilege level 1 to a consistent code segment with privilege level 0, then after we jump, CPL will not automatically equal the privilege level 0 of the current memory segment, but will still be 1 and will not change!!!

Experiment: direct jump rule of code segment
%include "inc.asm"
org 0x9000
jmp ENTRY_SEGMENT
[section .gdt]
; GDT definition
; Section base address, Segment boundaries, Segment properties
GDT_ENTRY : Descriptor 0, 0, 0
CODE32_DESC : Descriptor 0, Code32SegLen - 1, DA_C + DA_32 + DA_DPL1
VIDEO_DESC : Descriptor 0xB8000, 0x07FFF, DA_DRWA + DA_32 + DA_DPL2
DATA32_DESC : Descriptor 0, Data32SegLen - 1, DA_DR + DA_32 + DA_DPL2
STACK32_DESC : Descriptor 0, TopOfStack32, DA_DRW + DA_32 + DA_DPL1
;Inconsistent snippet properties DA_C
FUNCTION_DESC : Descriptor 0, FunctionSegLen - 1, DA_C + DA_32 + DA_DPL1
;Consistent snippet properties DA_CCO Privilege level 0
NEW_DESC : Descriptor 0, NewSegLen - 1, DA_CCO + DA_32 + DA_DPL0
; GDT end
GdtLen equ $ - GDT_ENTRY
GdtPtr:
dw GdtLen - 1
dd 0
; GDT Selector
Code32Selector equ (0x0001 << 3) + SA_TIG + SA_RPL1
VideoSelector equ (0x0002 << 3) + SA_TIG + SA_RPL2
Data32Selector equ (0x0003 << 3) + SA_TIG + SA_RPL2
Stack32Selector equ (0x0004 << 3) + SA_TIG + SA_RPL1
;Inconsistent snippet selector
FunctionSelector equ (0x0005 << 3) + SA_TIG + SA_RPL1
;Consistency snippet selector
NewSelector equ (0x0006 << 3) + SA_TIG + SA_RPL0
; end of [section .gdt]
TopOfStack16 equ 0x7c00
[section .s16]
[bits 16]
ENTRY_SEGMENT:
mov ax, cs
mov ds, ax
mov es, ax
mov ss, ax
mov sp, TopOfStack16
; initialize GDT for 32 bits code segment
mov esi, CODE32_SEGMENT
mov edi, CODE32_DESC
call InitDescItem
mov esi, DATA32_SEGMENT
mov edi, DATA32_DESC
call InitDescItem
mov esi, STACK32_SEGMENT
mov edi, STACK32_DESC
call InitDescItem
;Inconsistent code segment initialization segment descriptor
mov esi, FUNCTION_SEGMENT
mov edi, FUNCTION_DESC
call InitDescItem
;Consistency code segment initialization segment descriptor
mov esi, NEW_SEGMENT
mov edi, NEW_DESC
call InitDescItem
; initialize GDT pointer struct
mov eax, 0
mov ax, ds
shl eax, 4
add eax, GDT_ENTRY
mov dword [GdtPtr + 2], eax
; 1. load GDT
lgdt [GdtPtr]
; 2. close interrupt
cli
; 3. open A20
in al, 0x92
or al, 00000010b
out 0x92, al
; 4. enter protect mode
mov eax, cr0
or eax, 0x01
mov cr0, eax
; 5. jump to 32 bits code
push Stack32Selector ; Target stack segment selector
push TopOfStack32 ; Stack top pointer position
push Code32Selector ; Object snippet selector
push 0 ; Target code segment offset
;When the privilege level is reduced and transferred, it is executed retf The instruction will trigger the processor to check the privilege level of the stack segment directly through selection
;In the child RPL Check, specifically SS Select subrequest privilege level RPL To be equal to the selected subrequest privilege level of the code segment RPL
retf
; esi --> code segment label
; edi --> descriptor label
InitDescItem:
push eax
mov eax, 0
mov ax, cs
shl eax, 4
add eax, esi
mov word [edi + 2], ax
shr eax, 16
mov byte [edi + 4], al
mov byte [edi + 7], ah
pop eax
ret
[section .dat]
[bits 32]
DATA32_SEGMENT:
DTOS db "D.T.OS!", 0
DTOS_OFFSET equ DTOS - $$
Data32SegLen equ $ - DATA32_SEGMENT
[section .s32]
[bits 32]
CODE32_SEGMENT:
mov ax, VideoSelector
mov gs, ax
mov ax, Data32Selector
mov ds, ax
mov ax, Stack32Selector
mov ss, ax
mov eax, TopOfStack32
mov esp, eax
;Jump to non persistent snippet
; mov ebp, DTOS_OFFSET
; mov bx, 0x0C
; mov dh, 12
; mov dl, 33
;Jump to inconsistent code segment execution at the same privilege level
; call FunctionSelector : PrintString
;Jump to high privilege level consistent snippet
;Jump directly from non-conforming code snippets of low privilege level to consistent code snippets of high privilege level
;use jmp Jump directly from the non-conforming code segment with privilege level 1 to the code segment with privilege level 0!!!
;Therefore, for consistent code segments, you can jump directly from low privilege code segments!!!
jmp NewSelector : 0
Code32SegLen equ $ - CODE32_SEGMENT
;Consistent code snippets must be from low privilege code(Or code snippets of the same privilege level)Segment jump over
[section .new]
[bits 32]
NEW_SEGMENT:
;characteristic:
;Feature 1: continue to jump in the consistency code with privilege level 0(Function call),Jump to the non-conforming code segment with privilege level 1 for execution
;Feature 2: The current code segment is a consistent code segment with privilege level 0, and the stack segment privilege level used is 1
;That is to say, directly descend the privilege level and jump(Not used retf),And unequal stack segments are used
;So, although it can be from low privilege level code(Or code snippets of the same privilege level)Segment jump to high privilege level, or 1, so you can jump directly
;Execute in the non-conforming code segment with privilege level 1 and use the stack segment with privilege level 1
mov ebp, DTOS_OFFSET
mov bx, 0x0C
mov dh, 12
mov dl, 33
call FunctionSelector : PrintString
jmp $
NewSegLen equ $ - NEW_SEGMENT
;Non consistent code segments can only jump horizontally
[section .func]
[bits 32]
FUNCTION_SEGMENT:
; ds:ebp --> string address
; bx --> attribute
; dx --> dh : row, dl : col
PrintStringFunc:
push ebp
push eax
push edi
push cx
push dx
print:
mov cl, [ds:ebp]
cmp cl, 0
je end
mov eax, 80
mul dh
add al, dl
shl eax, 1
mov edi, eax
mov ah, bl
mov al, cl
mov [gs:edi], ax
inc ebp
inc dl
jmp print
end:
pop dx
pop cx
pop edi
pop eax
pop ebp
retf
PrintString equ PrintStringFunc - $$
FunctionSegLen equ $ - FUNCTION_SEGMENT
[section .gs]
[bits 32]
STACK32_SEGMENT:
times 1024 * 4 db 0
Stack32SegLen equ $ - STACK32_SEGMENT
TopOfStack32 equ Stack32SegLen - 1
It is proved that for consistent code segments, the transfer from low privilege level to high privilege level consistent code segments is supported, but!!! But the CPL remains unchanged after the transfer!!!
Decompile: ndisasm -b 32 -o 0x9000 loader > loader.txt address 00009115 EA000000003000 jmp dword 0x30:0x0 bochs 6 break 0x9115 info break c Stop to command: jmp NewSelector : 0 place sreg ;View key register values cs:0x0009, That is, the lowest two digits of 1001 are 01, which proves the privilege level of the current executable code segment CPL Is 1, which is the privilege level we define s ;Single step execution call FunctionSelector : PrintString place cs:0x0031 The lowest two digits are still 01, which indicates the privilege level of the current executable code segment CPL Is 1, indicating that at this time CPL Privilege level has not changed!!!
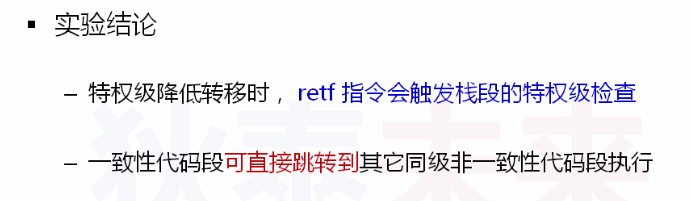
1 when the privilege level is reduced and transferred, that is, when the retf instruction is executed, it will trigger the processor to check the privilege level of the stack segment directly through the RPL in the selector. Specifically, the privilege level RPL of the selector request of SS should be equal to the privilege level RPL of the selector request of the code segment
2. The consistent code segment can jump directly to other non consistent code segments at the same level for execution
There is no essential difference between the code in the consistent code segment and the code in the non consistent code segment. These two code segments only use different legitimacy judgment rules when jumping. Therefore, the direct peer jump from the consistent code segment to the non consistent code segment is legal
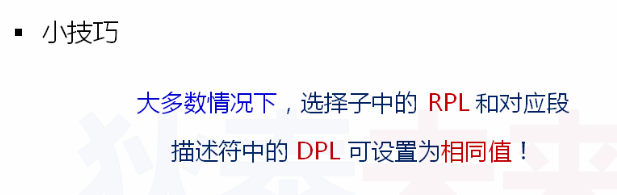
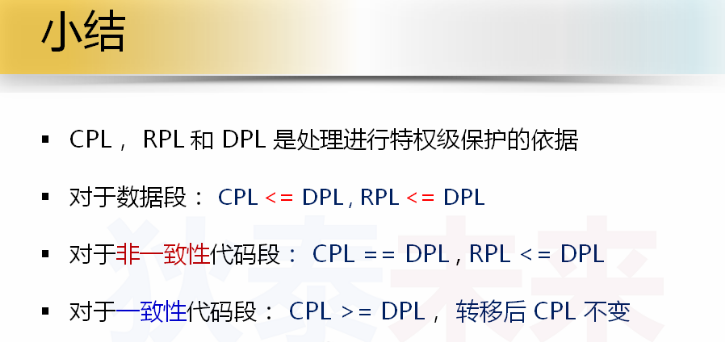
Rules that CPL, DPL and RPL should follow when checking the protection mode
For data segments, it is described in the previous section
For non-conforming snippets, only siblings can be transferred
For consistent code segments, the transfer from low privilege level to high privilege level consistent code segments is supported, but!!! But the CPL remains unchanged after the transfer!!!
Jump to the high privilege level through the call gate normally, and the code segment CPL will be assigned as the DPL of the current memory segment, but this is not applicable to the consistent code segment!!!