- get data
get key
- Delete data
del key
- Set expiration time (default unit is seconds)
expire key second
- Append information after initial value
append key value
- Add / modify multiple data
mset key1 value1 key2 value2...
- Get multiple data
mget key1 key2 ...
- Get string length
strlen key
- Set the lifecycle control lifecycle of the key
setex key seconds value (second) psetex key millisexxonds value (MS)
-
key setting Convention
It corresponds to the table - primary key - field in the database one by one
Table name Primary key name Primary key value Field name eg1 order id 443523454 name eg2 equire id 435432543 type eg3 news id 45435454 title
Basic data type: Hash
- Storage requirements: arrange a series of stored data to facilitate management. Typical applications store object information
- Storage structure: one storage space stores multiple key value pair data
- Hash type: the bottom layer uses hash table structure to realize data storage
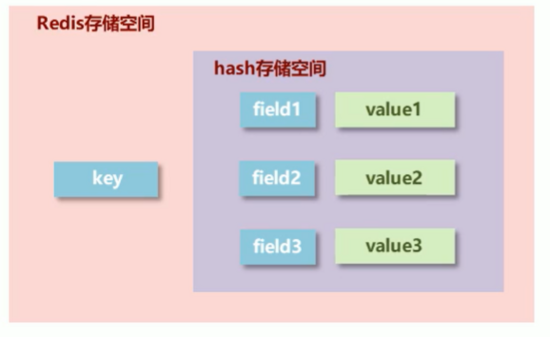
hash storage structure optimization
- If the number of field s is small, the storage structure is optimized to class array structure
- If the number of field s is large, the storage structure uses the HashMap structure
Basic operation of hash type
- Add / modify data
hset key field value
- get data
hget key field hgetall key
- Delete data
hdel key field [field2 ...]
- Add or delete multiple data
hmset key field1 value1 field2 value2 ...
- Get multiple data
hmget key field1 field2 ...
- Gets the number of fields in the hash table
hlen key
- Gets whether the specified field exists in the hash table
hexists key field
- Gets the field name or field value used in the hash table
hkeys key hvalues key
- Sets the numeric data of the specified field and increases the value of the specified range
hincrby key field increment hincrbyfloat key field increment
- If the field under the key value exists, no operation will be performed, and if it does not exist, it will be added
hsetnx key field value
Precautions for hash type data operation
-
The value under the hash type can only store strings. It is not allowed to store other data types. There is no nesting. If the data is not obtained, the corresponding value is (nil)
-
The upper limit of key value pairs stored in each hash is
$$
2^{32}-1
$$
Key value pairs
-
Hash type is very close to the storage form of objects, and object attributes can be deleted flexibly. However, hash is not designed to store a large number of objects. Remember not to abuse it, let alone use hash as an object list
-
hgetall operation can obtain all attributes. If there are too many internal field s, the overall data traversal efficiency will be very low, which may become a data access bottleneck
Application scenario
- Design and implementation of shopping cart on e-commerce website
Basic data type: list
- Data storage requirements: store multiple data and distinguish the key sequence of data entering the storage Jon
- Required storage structure: one storage space stores multiple data, and the data can reflect the entry order
- List type: save multiple data, and the bottom layer is realized by using the two-way linked list storage structure
The list type is stored in a two-way linked list
list basic operation
- Add / modify data
lpush key value1 value2 [value3] ... //Add from the left side of the list rpush key value1 value2 [value3] ... //Add from the right side of the list
- get data
lrange key start stop //Specify the value in the start and end position of the linked list //When obtaining a list type of unknown length, if you want to view all value s, you can use - 1 to represent the penultimate lrange key start -1 lindex key index //Gets the value of the specified position in the linked list llen key //Get the length of the linked list
- Get and remove data
lpop key rpop key
- Acquire and remove data within a specified time (blocking data acquisition)
blpop key1 [key2] timeout //Take out and remove the value corresponding to the key value within the specified time. If the timeout is not taken out, a null value (nil) will be returned. If no other client added the value of the key while waiting, the operation task queue will be performed brpop key1 [key2] timeout
- Remove specified data
lrem key count value
Precautions for list type data operation
- The data saved in the list is of string type, and the total data capacity is limited, with a maximum of 2 ^ 32-1 elements
- list has the concept of index, but when operating data, it usually performs queue in and out operations in the form of queue, or stack in and out operations in the form of stack
- The index to get all operation end data is set to - 1
- List can perform paging operation on data. Usually, the information on the first page comes from list, and the second page and more data information are queried and loaded through the database
Basic data type: set
- Storage requirements: store a large amount of data to provide higher efficiency in query
- Storage structure: it can save a large amount of data and has an efficient internal storage mechanism to facilitate query
- set type: exactly the same as the hash storage structure. Only keys are stored, no value (nil) is stored, and the value cannot be empty
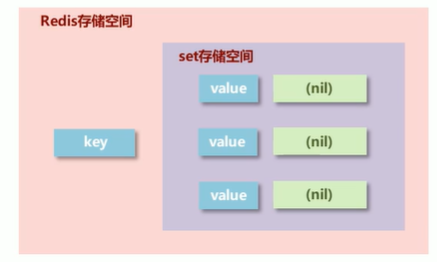
Set storage structure is an unordered set of string type. Internal storage is a hash storage structure, so the complexity of adding, searching and deleting is O(1)
set basic operation
- Add non duplicate data
sadd key value
- Get all stored data
smembers key ### How to get free architecture learning materials?      > Due to space constraints, pdf The detailed information of the document is too comprehensive, and there are too many details, so only the screenshots of some knowledge points are roughly introduced. There are more detailed contents in each small node!**[If you need a program, you can poke it here and get it for free](https://gitee.com/vip204888/java-p7)** 0YW-1628417841538)] [External chain picture transfer...(img-TYRcplte-1628417841538)] > Due to space constraints, pdf The detailed information of the document is too comprehensive, and there are too many details, so only the screenshots of some knowledge points are roughly introduced. There are more detailed contents in each small node!**[If you need a program, you can poke it here and get it for free](https://gitee.com/vip204888/java-p7)**