preface
Today, I will share five data structures of Redis and their use scenarios in actual combat
1, Redis data structure?
We all know that redis is an indispensable middleware tool in large-scale systems. It can support high concurrency scenarios or distributed locks. This is inseparable from his design architecture and underlying data structure. Redis is a non relational database with K and V structure. There are five data types. They are string, hash, list, set and zset. The data types we mentioned are only different from values, and key s are of string type. Here I drew a picture.
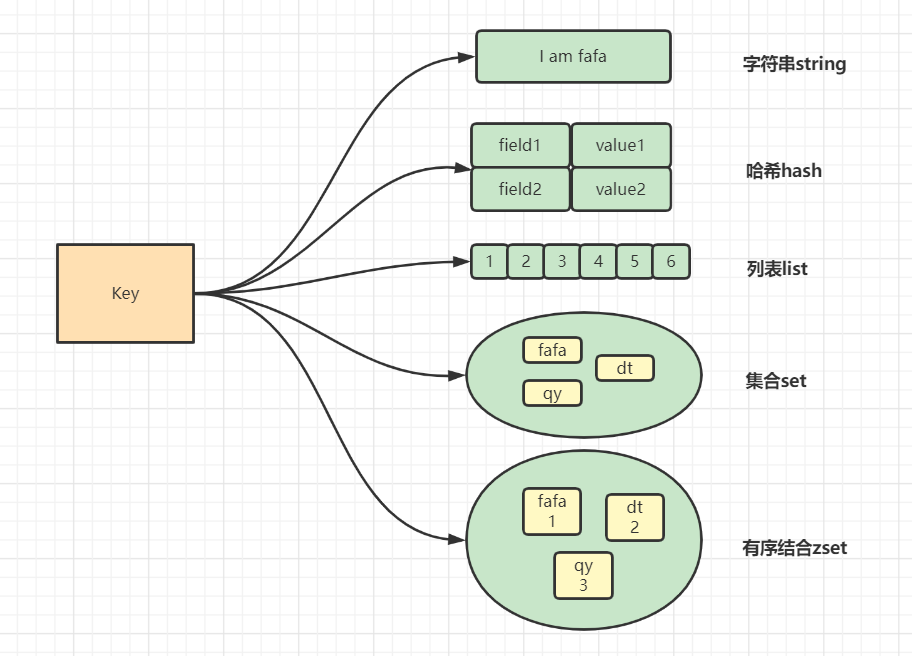
2, string common methods and usage scenarios
1. Introduction to common methods
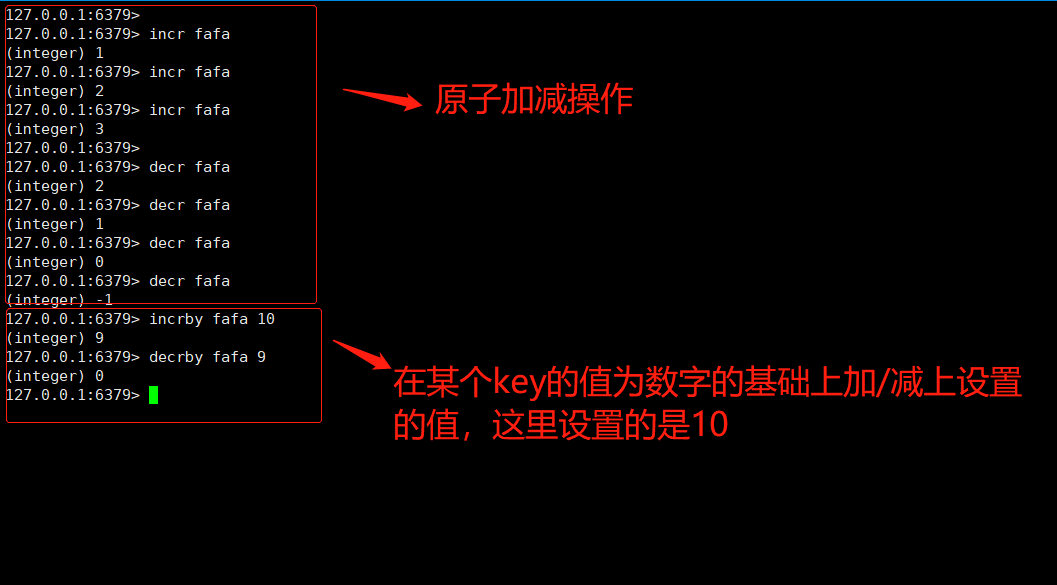
#String common operations set key value //Store key value pairs of strings mset key value [key value ...] //Batch store key value pairs of strings setnx key value //Stores a key value pair of a nonexistent string get key //Get a value according to the key mget key [key ...] //Get value in batch del key [key ...] //Delete key expire key seconds //Set the expiration time of a key #Atomic addition and subtraction incr key //Add 1 to the numeric value stored in the key decr key //J subtract 1 from the digital value stored in the key incrby key increment //Add increment to the value stored in the key decrby key decrement //decrement the value stored in the key
Briefly demonstrate:
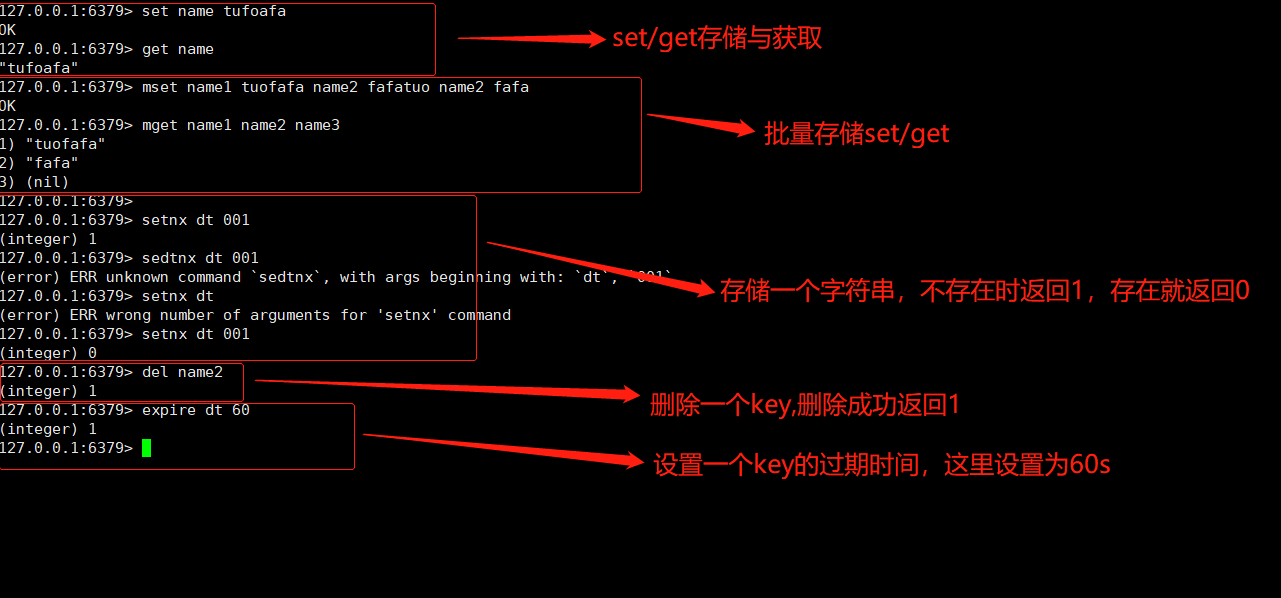
2. Introduction to string usage scenario
- Ordinary single value cache (generally stores the user's token)
set key value
get key
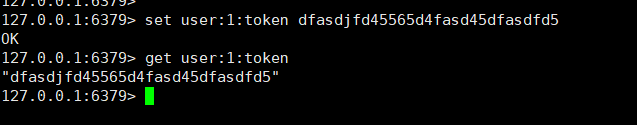
- Object cache (storing user information)
set user:110:info value(json data format)
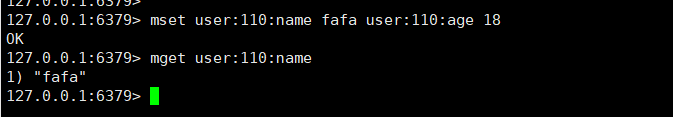
mset user:110:name fafa user:110:age 18
- Distributed lock
setnx product:10010 true
del product:10010
set product:10010 true ex 10 nx
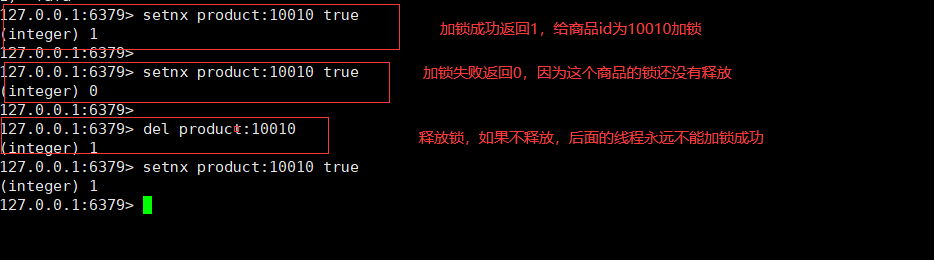
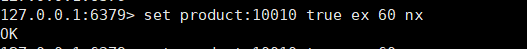
Set the maximum duration of locking to 60s. If the business logic processing has not been completed within 60s, the lock will be released. Of course, in the actual production process, we have many means to prevent the lock from being released before the business logic is processed (the lock continues its life, and reisson has been implemented). Our command is mainly to prevent the deadlock caused by the accidental termination of the program. - Counter
incr
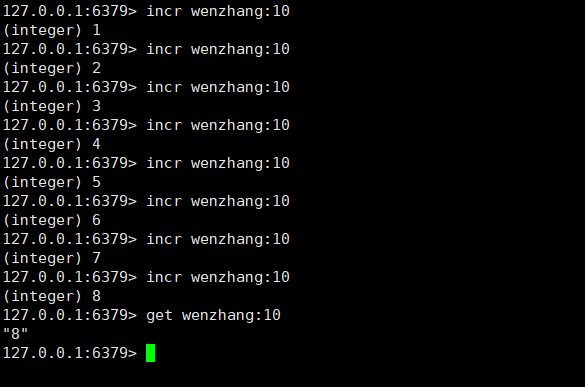
For example, the number of people viewing my csdn blog posts. Check the following number once and add 1. The data structure can be designed like this. incr wenzhang:10
- Global serial number of distributed system
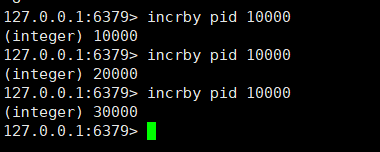
incrby pid 10000 / / batch generation of serial numbers can improve performance
3, Common hash methods and usage scenarios
1. Common hash methods
HSET key field value //Store the key value of a hash table key HSETNX key field value //Store the key value of a non-existent hash table key HMSET key field value [field value ...] //Store multiple key value pairs in a hash table key HGET key field //Get the field key value corresponding to the hash table key HMGET key field [field ...] //Batch obtain multiple field key values in hash table key HDEL key field [field ...] //Delete the field key value in the hash table key HLEN key //Returns the number of field s in the hash table key HGETALL key //Returns all key values in the hash table key HINCRBY key field increment //Add increment to the value of the field key in the hash table key
2.hash usage scenario
- Object cache (if multiple fields of the cache object are frequently modified, the hash structure has higher performance than the string structure)
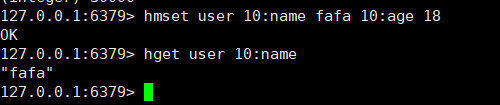
hmset user {userId}:name fafa {userId}:age 18
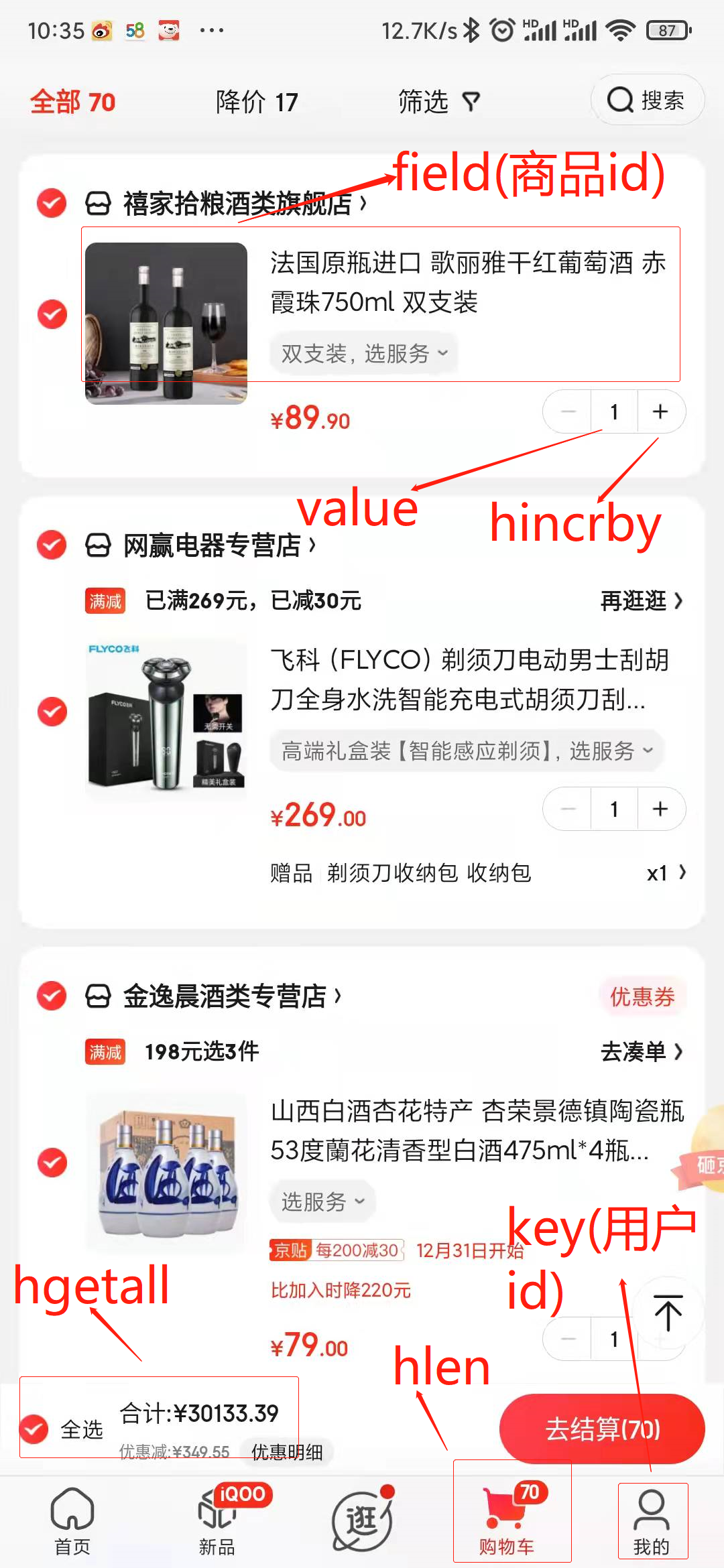
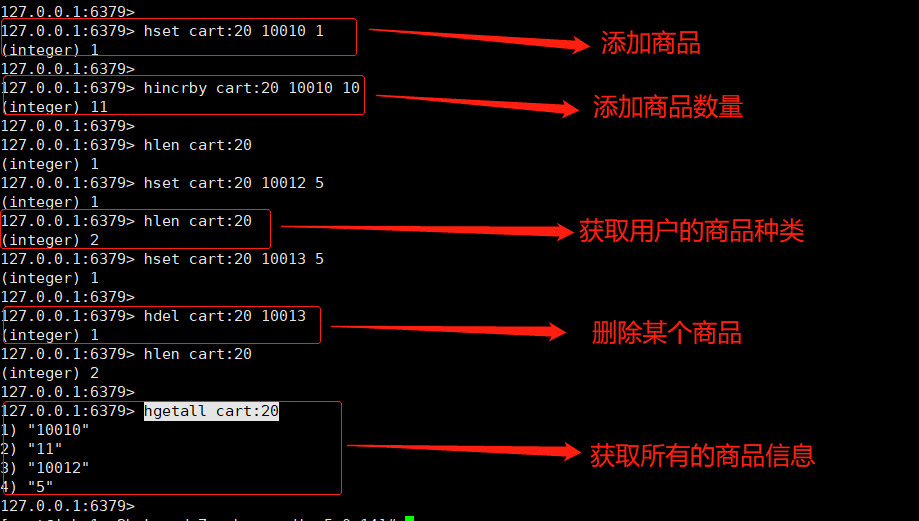
- Shopping cart scene
1. The user id is key
2. The commodity id is field
3 commodity quantity value
Shopping cart operation:
Add item: hset cart:20 10010 1
Added quantity: hincrby Cart: 20 10010
Total number of goods: Helen Cart: 20
Deleted item: hdel cart:20 10013
Get all items in the shopping cart: hgetall cart:20
Command operation:
4, list common methods and usage scenarios
1. Common methods
List Common operation LPUSH key value [value ...] //Insert one or more values value into the header (leftmost) of the key list RPUSH key value [value ...] //Insert one or more values value at the end of the key list (rightmost) LPOP key //Removes and returns the header element of the key list RPOP key //Removes and returns the last element of the key list LRANGE key start stop //Returns the elements within the specified interval in the list key. The interval is specified by offset start and stop BLPOP key [key ...] timeout //Pop up an element from the header of the key list. If there is no element in the list, block and wait Timeout seconds. If timeout=0, it will block and wait all the time BRPOP key [key ...] timeout //Pop up an element from the end of the key list. If there is no element in the list, block and wait Timeout seconds. If timeout=0, it will block and wait all the time
2.list usage scenario
- Common data structures
Stack: lpush + lpop or rpush + rpop
Queue: lpush + rpop or rpush + lpop
Blocking MQ (blocking queue): lpush +brpop or rpush + blpop
Stack:
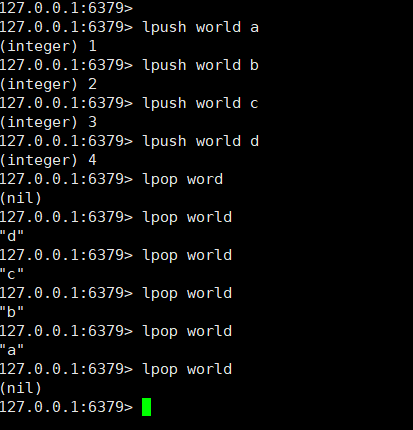
Queue:
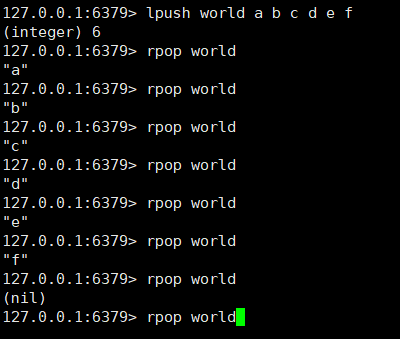
Blocking queue:
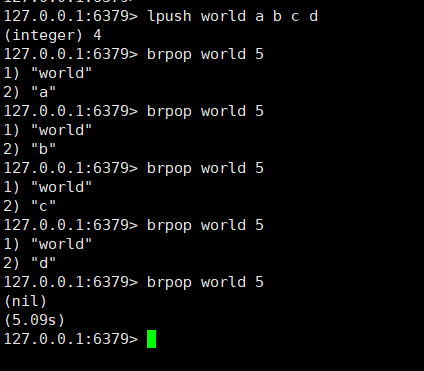
- Micro-blog and WeChat official account message flow
Let's look at a picture first
Wechat subscription number, I believe everyone should be familiar with it! Here I subscribe to the programmer column and the java technology Jianghu. As long as I subscribe to people, they add their article id to my list every time they post an article. In this way, they can get it from this list every time they enter my wechat. This is the use scenario of list. For example:
The programmer column has posted an article with id 111
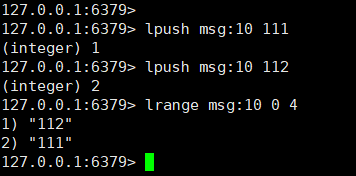
lpush msg:{tuofafaId} 111
java technology Jianghu has published an article with the article id of 112
lpush msg:{tuofafaId} 112
Finally, get the latest news or the previous messages: lrange msg:10 0 4
The operation is shown in the figure below:
5, Common methods and usage scenarios of set
1. Common methods
Set Common operation SADD key member [member ...] //Store elements into the set key, and ignore them if they exist, if key New if none exists SREM key member [member ...] //Delete element from set key SMEMBERS key //Get all elements in the set key SCARD key //Gets the number of elements of the set key SISMEMBER key member //Judge whether the member element exists in the set key SRANDMEMBER key [count] //Select count elements from the set key, and the elements will not be deleted from the key SPOP key [count] //Select count elements from the set key, and delete the elements from the key Set Arithmetic operation SINTER key [key ...] //Intersection operation SINTERSTORE destination key [key ..] //Store the intersection results in the new set destination SUNION key [key ..] //Union operation SUNIONSTORE destination key [key ...] //Store the union result in the new set destination SDIFF key [key ...] //Difference set operation SDIFFSTORE destination key [key ...] //Save the difference set result into the new set destination
2.set usage scenario
-
Lottery scene
We must have participated in the lottery in our daily life. The process will not be described in detail here. In general, we must first let users join the lottery collection, that is to participate. You should also view all users participating in the lottery, and then the lottery.
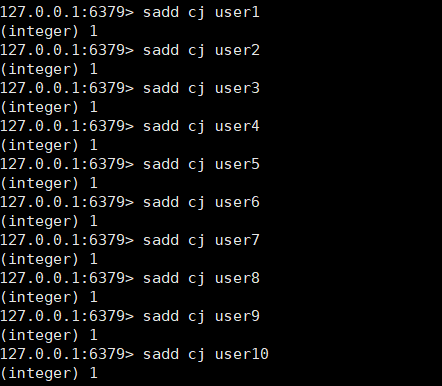
Join the raffle: sadd cj user
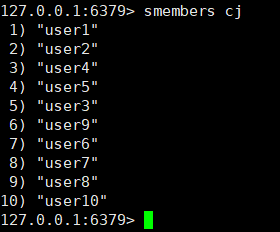
View participants in the raffle: smembers cj
Lucky draw: srandmember cj 3 or spop cj 3. The difference between the two is that the former remains in the collection after drawing the prize (you can continue to draw other prizes), and the latter has been deleted from the collection (you can't participate in other prizes)Join the raffle:
View all users participating in the raffle:
luck draw:
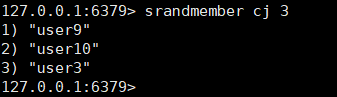
-
Praise and collection of wechat microblog
Look at a picture first

This must be familiar to everyone. Circle of friends often praise others.
Like: sadd like: {message id} {user id}
Cancel likes: srem like: {message id} {user id}
Check whether the user likes: sismember like: {message id} {user id}
List of users who get likes: smembers like: {message id}
Number of users getting likes: scar like: {message id}
The command operation is as follows:
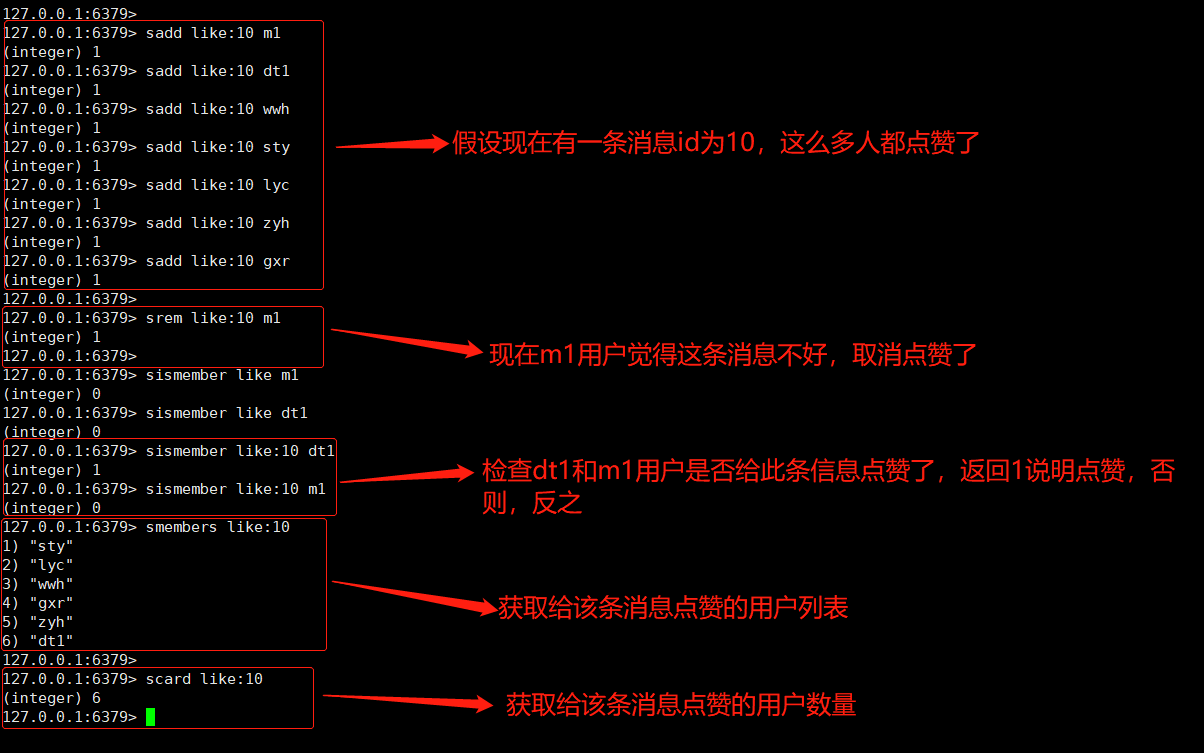
-
Collection operation
In addition, set can also complete the set operation in mathematics. Find some intersection, union and difference sets
We design such an environment, assuming that there are three sets A, B and C. There are a,b,c in set A. b,c,d in set B. There are c,d,e in set C.
Find the intersection of sets a, B and C: sinter a, B and C
Find the union of sets A,B,C: Sunion A,B,C
Find the difference set of sets A, B and C: sdiff A, B and C (return the elements of set A that do not exist in sets B and C)
The command operation is as follows:
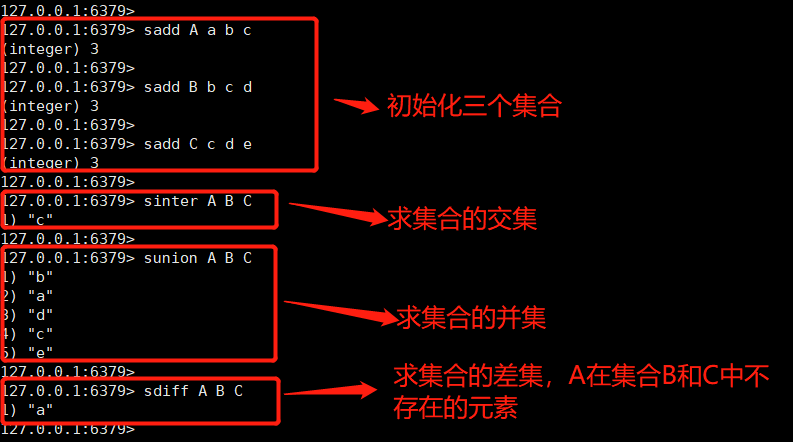
-
Collection operation to realize microblog and wechat attention model
The previous figure illustrates the focus model
This scene is also very common. This is what we call the attention model. Who I pay attention to, who pays attention to me, who I pay attention to, and who we may know, are all application scenarios of set. For example:
fafa People concerned: fafaSet-->{dt,gxr}
suosuo People concerned: suoSet-->{dt,gxr,lmm,fafa}
People concerned by Peng Yuan: pySet-->{dt,suosuo,lmm,fafa,nn}
Me and suosuo People of common concern: sinter fafaSet suoSet --->{dt,gxr}
The people I care about also pay attention to him( suosuo):
sismember dtSet suosuo
sismember gxrSet suosuo
This item may be a little windy. Careful analysis is OK. The people I care about are also concerned suosuo,Then check whether there are people in my collection suosuo. If there is, it means attention, otherwise there will be no attention.
People I may know:
sdiff pySet fafaSet --->{suosuo,lmm,fafa,nn}
6, Common methods and usage scenarios of zset
1. Common methods of Zset
ZADD key score member [[score member]...] //Add elements with scores to the ordered set key ZREM key member [member ...] //Delete element from ordered set key ZSCORE key member //Returns the score of the element member in the ordered set key ZINCRBY key increment member //Add increment to the score of the element member in the ordered set key ZCARD key //Returns the number of elements in the ordered set key ZRANGE key start stop [WITHSCORES] //Obtain the elements of the ordered set key from the start subscript to the stop subscript in positive order ZREVRANGE key start stop [WITHSCORES] //Get the elements of the ordered set key from the start subscript to the stop subscript in reverse order Zset Collection operation ZUNIONSTORE destkey numkeys key [key ...]//Union calculation ZINTERSTORE destkey numkeys key [key ...] //Intersection calculation
2.zset usage scenario
- zset set operation to implement Leaderboard
Use a diagram to illustrate the usage scenario:
Click news: zincrby hotNews:20211228 1 squint
Top 10 on display day: zrevrenge hotnews: 20211228 0 9 WithCores
Seven day list search calculation: ZUNIONSTORE hotNews:20211222-20211228 7
hotNews:20211222 hotNews:20211223... hotNews:20211228
Top ten in seven days:
ZREVRANGE hotNews:20211222-20211228 0 9 WITHSCORES
6, Summary
The usage scenarios of Redis are very rich. To sum up, caching, computing, and distributed locking. Because this article focuses on the common methods and actual combat scenarios of Redis data structure, a separate article will be written later for distributed locks.