About file upload vulnerability
Write before the article - avoid stepping on the pit
The upload lads shooting range used in the relevant chapters on file upload vulnerabilities is Docker - 20, and the latest version is 21. And some bypass methods in this paper are only applicable to PHP 5.2 For versions below 4, the Docker installation environment is 5.2 17 version. If you want to pass the customs, you can use PHP study to build a green version of upload lads in the WIN environment. You can bypass some checkpoints by reducing the PHP version!
What is a file upload vulnerability?
When the file upload point does not strictly verify and filter the uploaded files, it is easy to upload any files, including uploading dynamic files (asp,php,jsp), etc
If the uploaded target directory does not restrict the execution permission, resulting in the normal execution of the uploaded dynamic file, it leads to the file upload vulnerability.
Scene: as the name suggests, it is the place where files are uploaded.
WEB APP Software Any operation involving upload be careful:Some uploaded protocols are different,If you go to the upload point of the website agreement, you can use it Upload operation test upload vulnerability;image WEB,APP Even the upload function of some software can be used by using the website protocol, However, some upload points are similar to byte stream protocol,This basically eliminates the need for testing.
Principle: use the file upload function to upload files with back door [pictures, text, files, scripts, etc.] to control the website.
Necessary conditions for upload vulnerability
(1)There are upload points (2)You can upload dynamic files (3)The upload directory has execution permission, and the uploaded files can be executed (4)You can access uploaded dynamic files or scripts
High risk trigger point of file upload vulnerability
album picture upload video Photo sharing Attachment upload (forum post, email) File manager File upload vulnerabilities may exist where file upload function exists, such as photo album, avatar upload, video and photo sharing. The places where attachments can be uploaded, such as forum posts and e-mail, are also high-risk areas for upload vulnerabilities. In addition, functions such as file manager may also be exploited by attackers. It is worth noting that if there are similar operations on the mobile terminal, there is also a risk of file upload vulnerability based on the same principle.
Understand file upload through simple code cases
Think: what information will file upload receive? From the perspective of security, how to filter and use the received information?
The following is a simple file upload function
<html>
<head>
<meta charset="utf-8">
<title>UP_TEST</title>
</head>
<body>
<form action="" method="post" enctype="multipart/form-data">
<label for="file">File name:</label>
<input type="file" name="file" id="file"><br>
<input type="submit" name="submit" value="Submit">
</form>
</body>
</html>
<?php
$name=$_FILES["file"]["name"];
echo "Upload file name: " . $name . "<br>";
$type=$_FILES["file"]["type"];
echo "file type: " . $type . "<br>";
$size=$_FILES["file"]["size"];
echo "file size: " . $size . " kB<br>";
//echo "file size:" ($_FILES["file"]["size"] / 1024) . " kB<br>";
$up_error_info=$_FILES["file"]["error"];
echo "Error:: " . $up_error_info . "<br>";
$temp_name=$_FILES["file"]["tmp_name"];
echo "Location of temporary storage of files: " . $temp_name . "<br>";
?>
From the code, we can see that "$_FILE" contains size, name, type, temporary name and error information.
Now let's look at a packet of real upload operations
Now let's think about where we can make use of when there are security problems and a breakthrough in file upload can be achieved? Or where can we verify that it is an illegal type of attack?
data packet Content-Type: image/jpeg # Verify the file type here [e.g. PHP file type "application / octet stream"] File header information:JPG/PNG/GIF/zip... File name suffix type:jpg/png/gif/zip...
Through the above code demonstration, we analyze the conventional code, and there are many filtered upload content points. The verification of a relatively safe file upload is multifaceted. The opposite side of simple verification may be forged to break through. When all verification points are verified, it shows that such upload points are safe and generally have no security vulnerabilities.
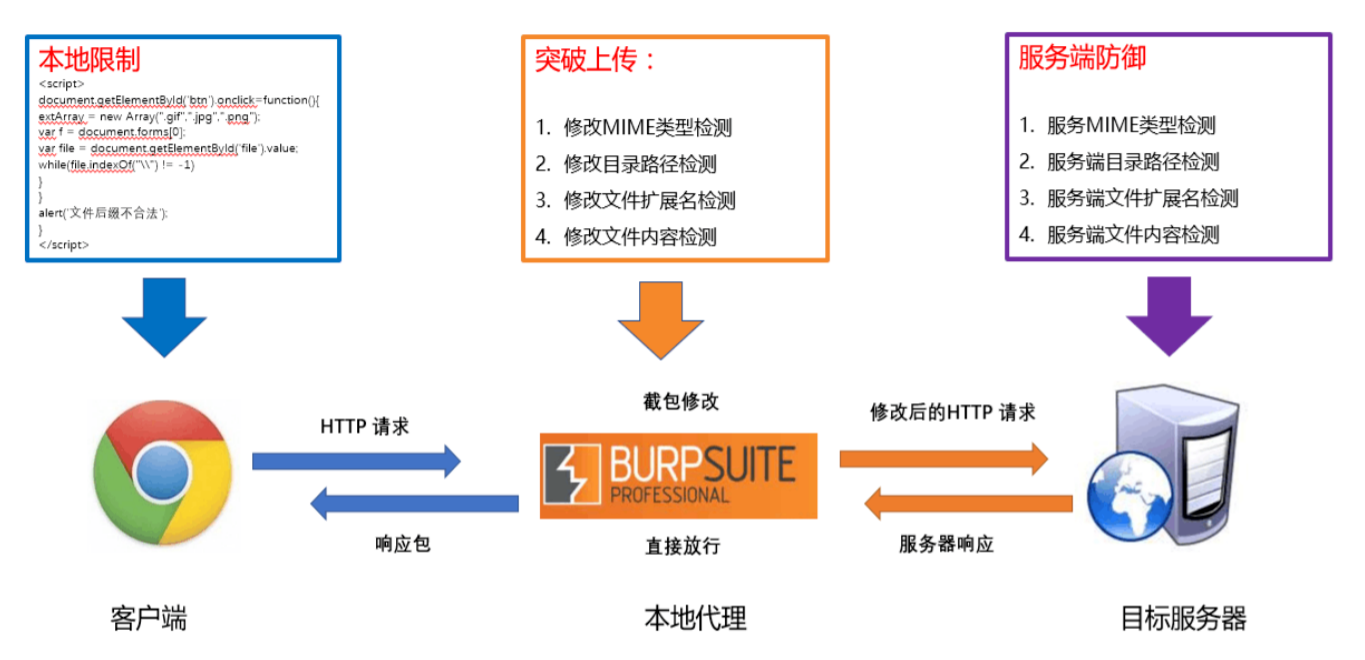
What we need to know about the file upload vulnerability is actually to test what has been verified by the file upload function point? What points can we bypass the verification after modification, so that we can make a breakthrough.
Most file uploads will be done on the data package. Using Burp tool is to intercept the data package and test it on the data package. [there are many kinds of packet capture tools that can intercept, but Burp is relatively simpler, more convenient and faster.]
The back door must be related to the format of the website language