Article catalog
preface
Why use key authentication
Secret key authentication process
Secret key generation and use
- Interactive creation and distribution of secret keys
a) Generate secret key
b) Distribute secret keys
c) Login test - Non interactive creation key
summary
preface
We discussed the basic introduction and configuration files of ssh before. If you haven't explored the basic knowledge of ssh, please click the link:
[Linux] step by step learning operation and maintenance - Services - Introduction to ssh services
[Linux] step by step operation and maintenance - Services - detailed explanation of ssh configuration file
Today, let's talk about secret key authentication.
Why use key authentication
The user name and password are entered every time for remote login. One is very troublesome, and the other is not particularly secure. The password needs to be changed from time to time.
Generally in the company, we change the password once a week; Of course, there are companies that do not change their passwords once a few years. Two years after I left my last company, I once demonstrated to students that I could log in even after logging in. How much I felt. Of course, we strictly abide by our duty and don't do damage to them, but it's hard to guarantee that one day when employees leave, they will be unhappy and log in and delete roots for revenge.
Secret key authentication process
Public key login is to solve the problem of entering a password every time you log in to the server. RSA encryption scheme is popular. The main process includes:
1. The client generates RSA public key and private key
2. The client stores its public key in the server
3. The client requests to connect to the server, and the server sends a random string to the client
4. The client encrypts the random string according to its private key and then sends it to the server
5. After receiving the encrypted string, the server decrypts it with the public key. If it is correct, let the client log in, otherwise it will be rejected. So you don't have to use a password.
This method requires users to provide their own public key. If there is no ready-made one, you can directly use SSH keygen to generate one
Secret key generation and use
1. Create and distribute secret keys interactively
a) Generate secret key
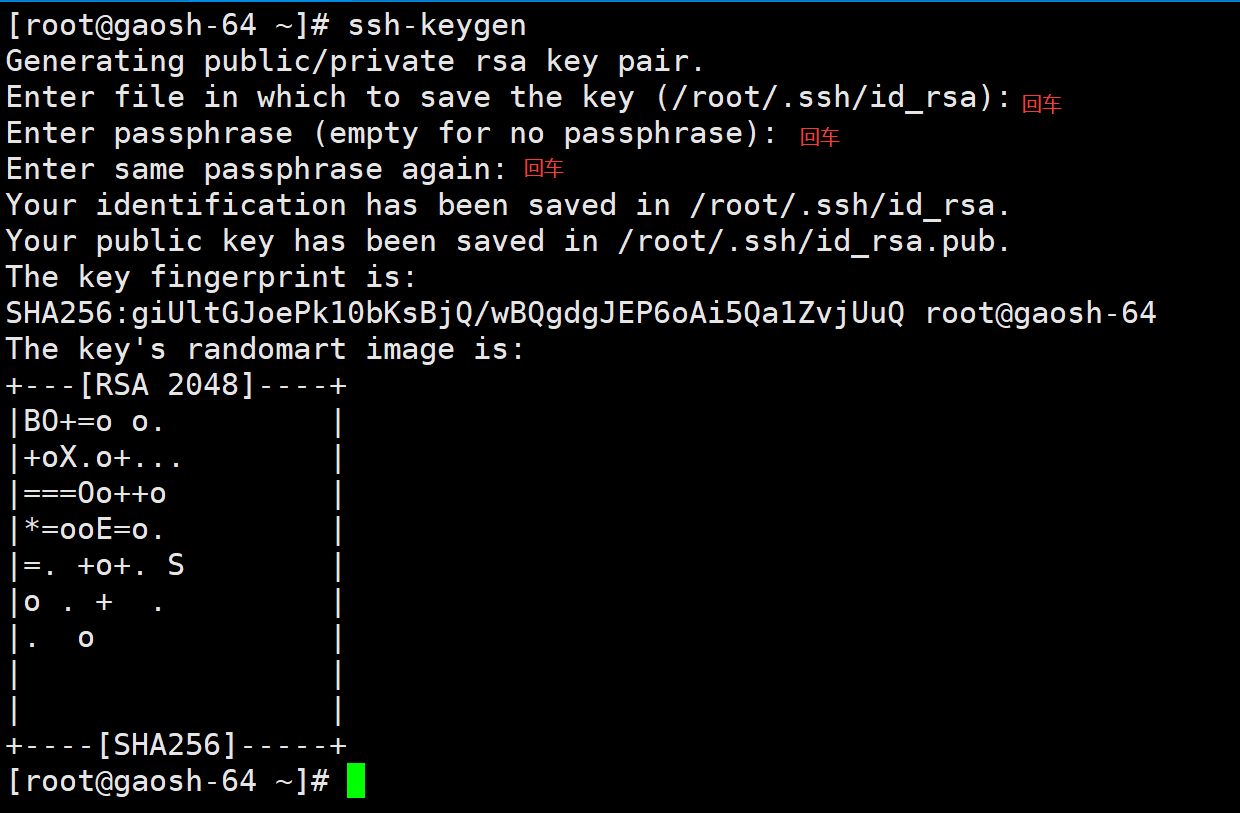
Enter all the way with lightning. The password of the private key can be set or not.
After running, it will be in $home / In SSH / directory, two new files will be generated: id_rsa.pub and id_rsa. The former is your public key and the latter is your private key.
b) Distribute secret keys
[root@gaosh-64 ~]# ssh-copy-id root@192.168.1.22 ### Distribute secret keys /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub" /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@192.168.1.22's password: ##Enter 22 the password for this server Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'root@192.168.1.22'" and check to make sure that only the key(s) you wanted were added.
c) Login test
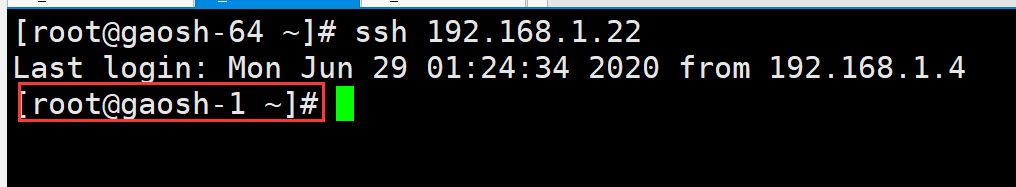
You can see that you do not need to enter a password
2. Non interactive creation of secret keys
ssh-keygen -t dsa -f ~/.ssh/id_dsa -P ""
| parameter | effect |
|---|---|
| ssh-keygen | Generate key pair command |
| t | Specify the password encryption type of the key pair (rsa and dsa) |
| f | Specifies that the generation path of the key pair file contains the file name |
| P | Specifies the password for the key pair |
[root@gaosh-1 ~]# ssh-keygen -t dsa -f ~/.ssh/id_dsa -P "" Generating public/private dsa key pair. Your identification has been saved in /root/.ssh/id_dsa. Your public key has been saved in /root/.ssh/id_dsa.pub. The key fingerprint is: 48:ee:69:98:53:3e:63:2e:00:14:27:f3:ad:5c:5f:58 root@gaosh-1 The key's randomart image is: +--[ DSA 1024]----+ | +.. E | | .= . o | |. . o.. . | |. . oo... | | . o +.S | | . * . | | .+ O | | .= o | | .. | +-----------------+ [root@gaosh-1 ~]#
summary
In the later study, especially when writing shell scripts, secret key authentication involves the combination of two servers, which is particularly convenient. When using, as long as the secret key can be created interactively.
This article is from ID: Internet old Xin more content is concerned about the official account of the "geek operation and maintenance home".
