Python wechat ordering applet course video
https://edu.csdn.net/course/detail/36074
Python practical quantitative transaction financial management system
https://edu.csdn.net/course/detail/35475
1, Introduction
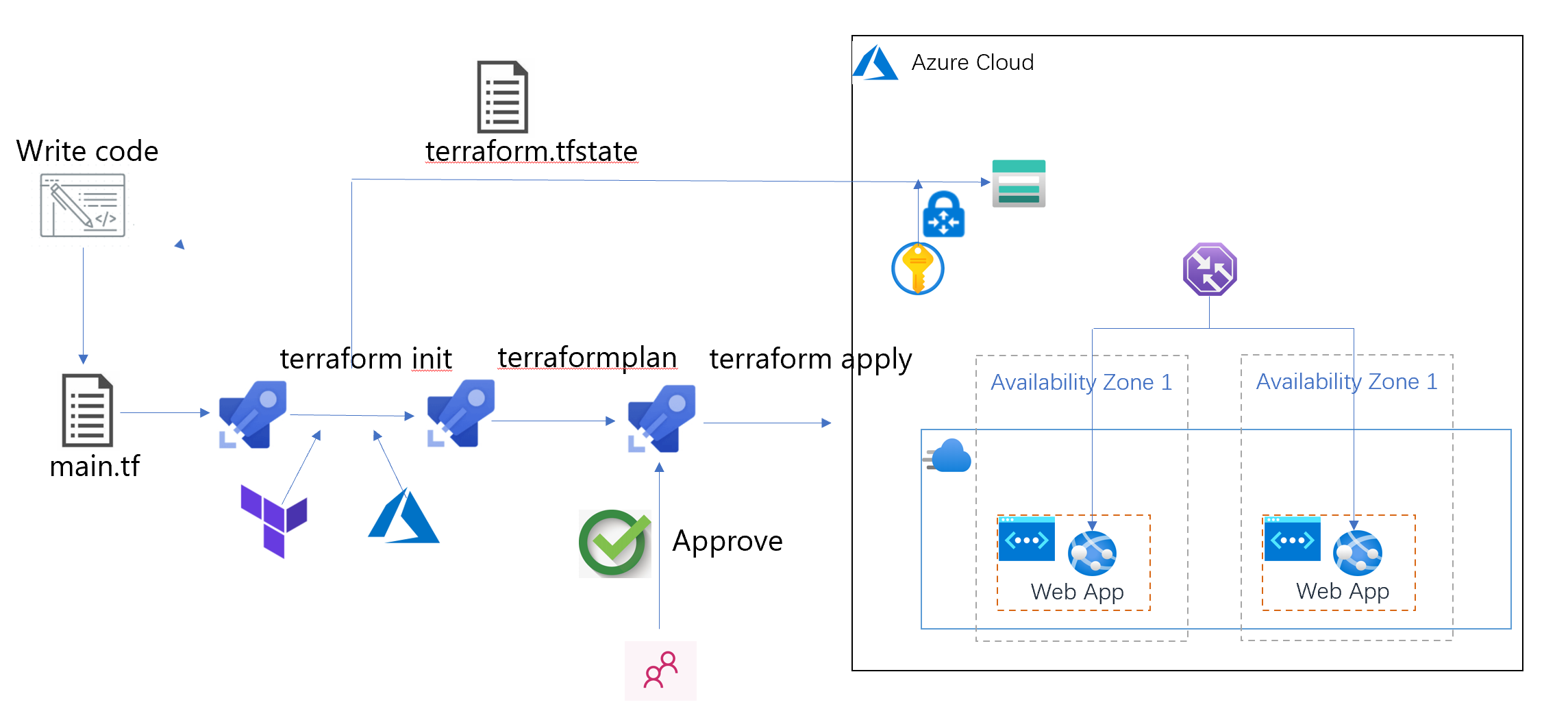
Azure Pipeline is an automated process; However, for some reason, we often need to obtain approval before proceeding to the next process, so we can add approval to the Azure Pipeline pipeline! The approval process can help us further control our pipeline; We can control the start of the Step at a specific stage in the pipeline, pass the approval, and decide when the Azure Pipeline will be completed.
As for why the approval process should be added, it is because the deployment of infrastructure resources needs to be evaluated and operated carefully. With approval, you can check the previous stage to confirm whether the configuration code is correct.
--------------------Azure terrain series--------------------
1. Introduction to azure terrain (I)
2. Detailed explanation of azure terrain (II) syntax
3. Azure Terraform (III) deploying Web applications
4. Azure terrain (IV) status file storage
5. Azure terrain (V) realize automatic deployment of basic resources by using Azure DevOps
6. Azure terrain (VI) Common Module
7. Azure terrain (VII) realize automatic deployment of basic resources by using Azure DevOps (supplementary)
8. Azure Terraform (VIII) uses Azure DevOps to realize Infra resources and NET CORE Web application continuous integration and deployment
9. Azure terrain (IX) uses the approval of Azure DevOps Pipeline to control the process release
2, Text
1. Create a new project with Azure DevOps
Address to log in to Azure DevOps: https://www.dev.azure.com , click "+ New project" to create a New project
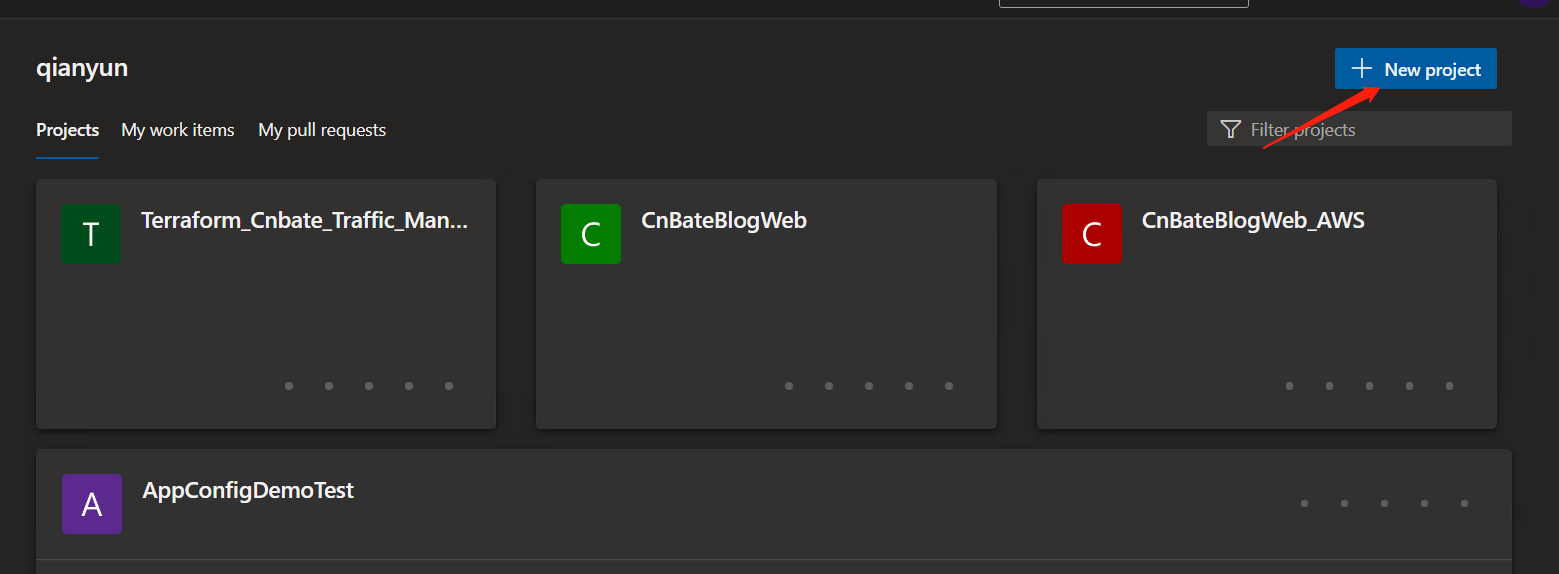
Enter information such as project description
Project name: "Terraform_CnBateBlogWeb_AutoDeploy"
Visibility selection: "Private" ---- (set according to existing projects)
Version control select Git
Work item process: "Agile"
After confirming the above information, click "Create" to Create it.
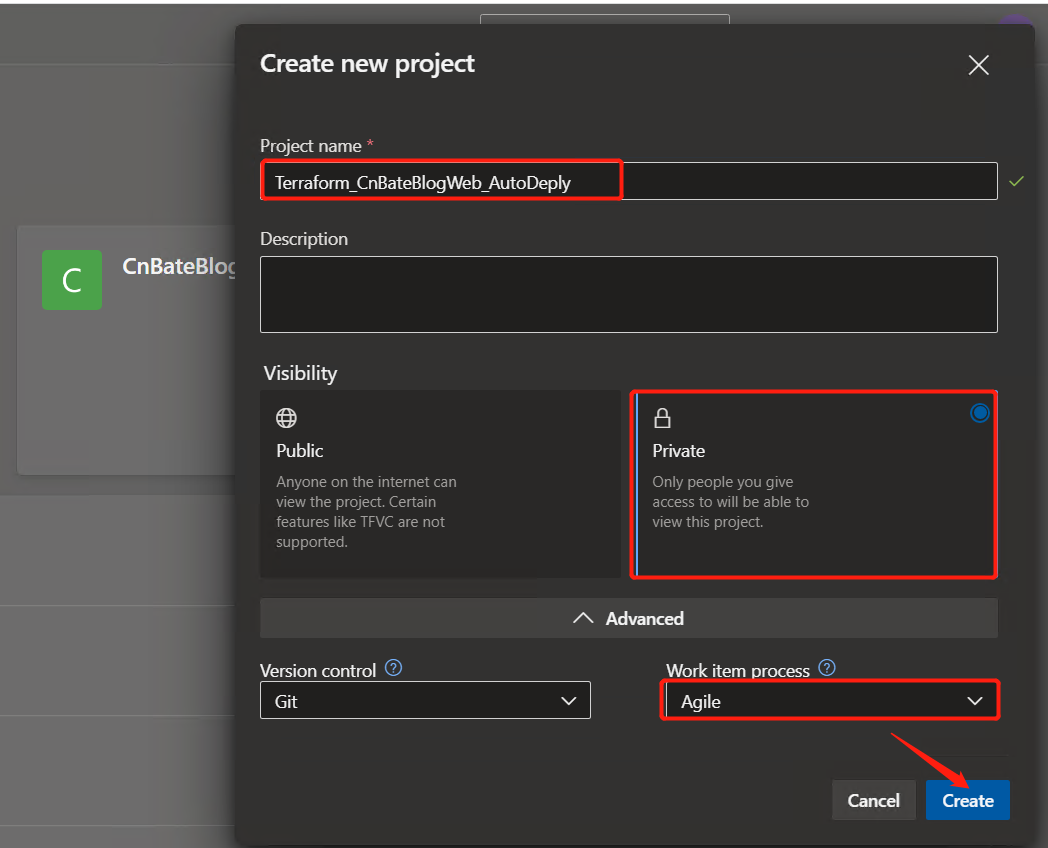
2. Configure Azure DevOps approval
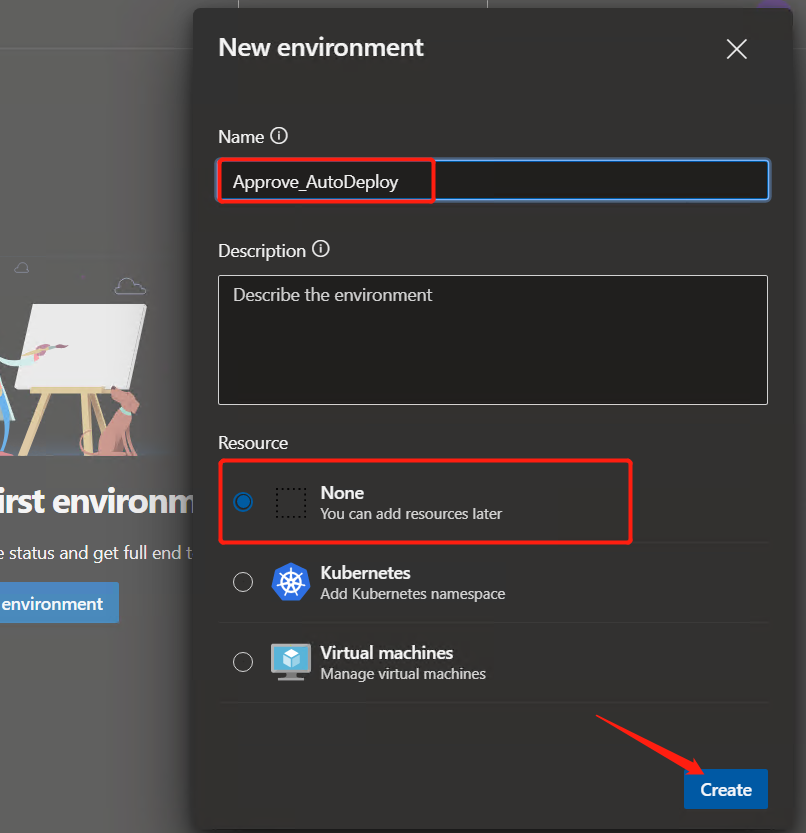
Select "Pipelines =" Environments "in the left menu and click" Create environment "to create an environment
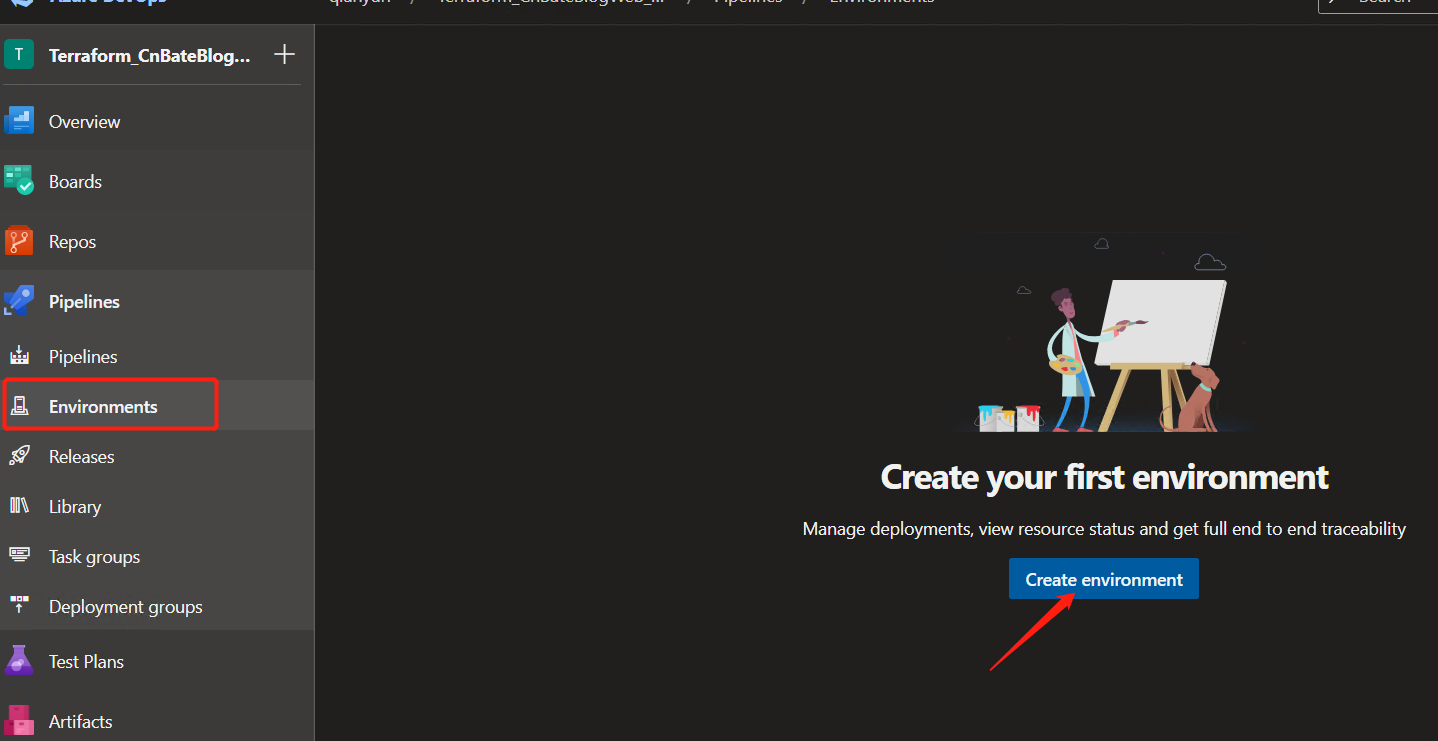
Enter the following parameters for configuration
Name: "Approve_AutoDeploy"
Resource selection: "None" (default)
Click "Create" to Create the environment
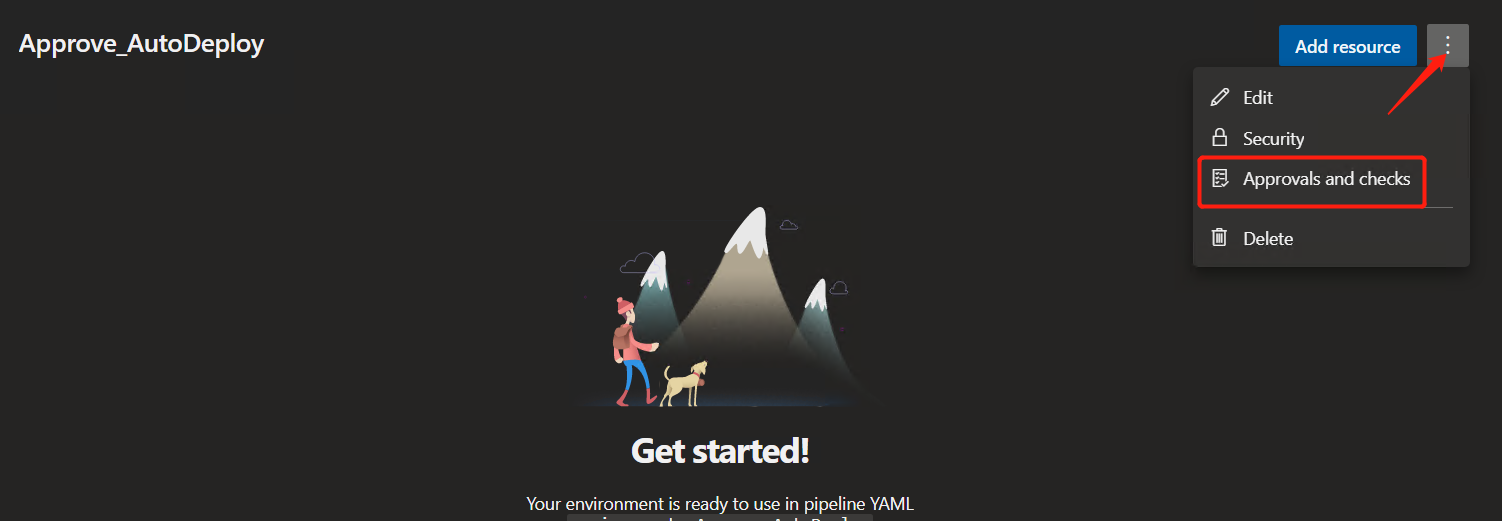
Next, create an approval for the current Approve_AutoDeploy environment
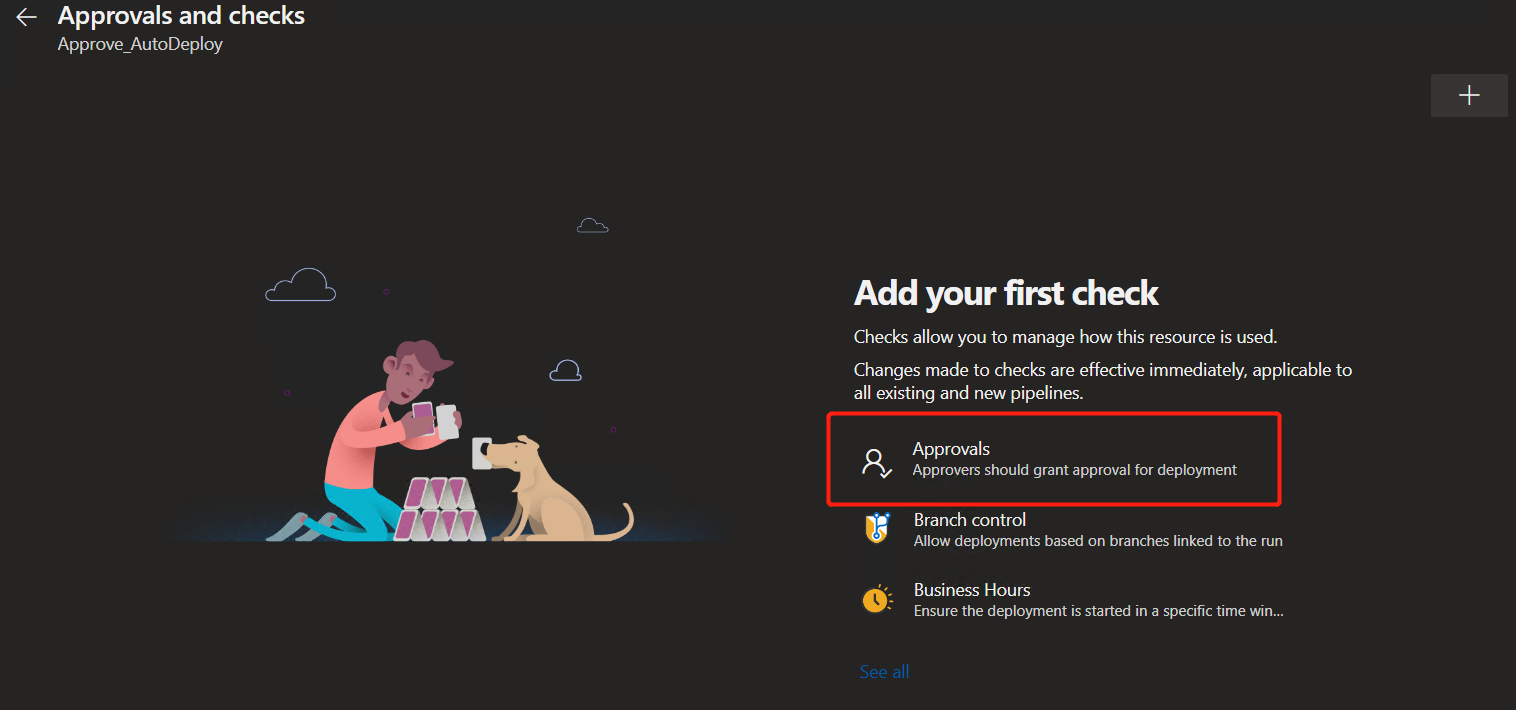
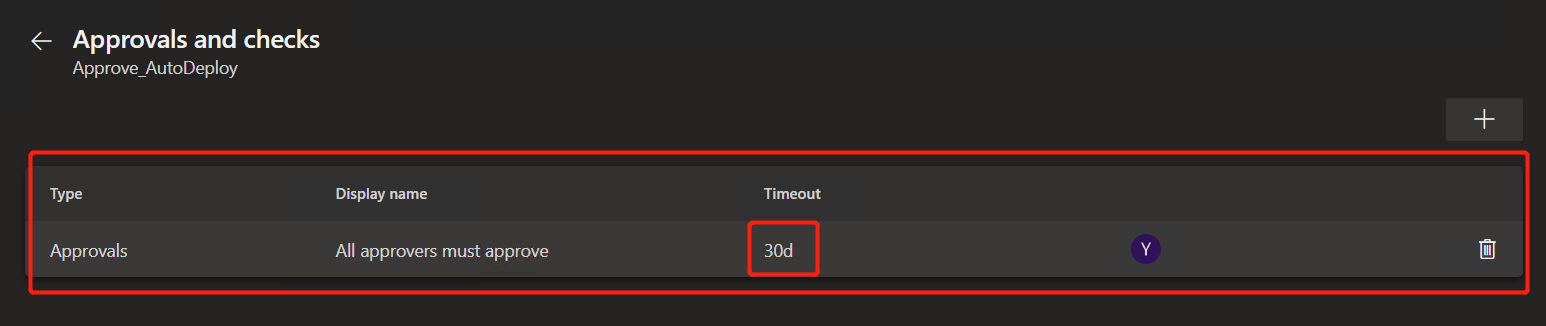
Click the red arrow and select "Approve and checks" to add the approval request
Select "Approvals" and set yourself as the applicant
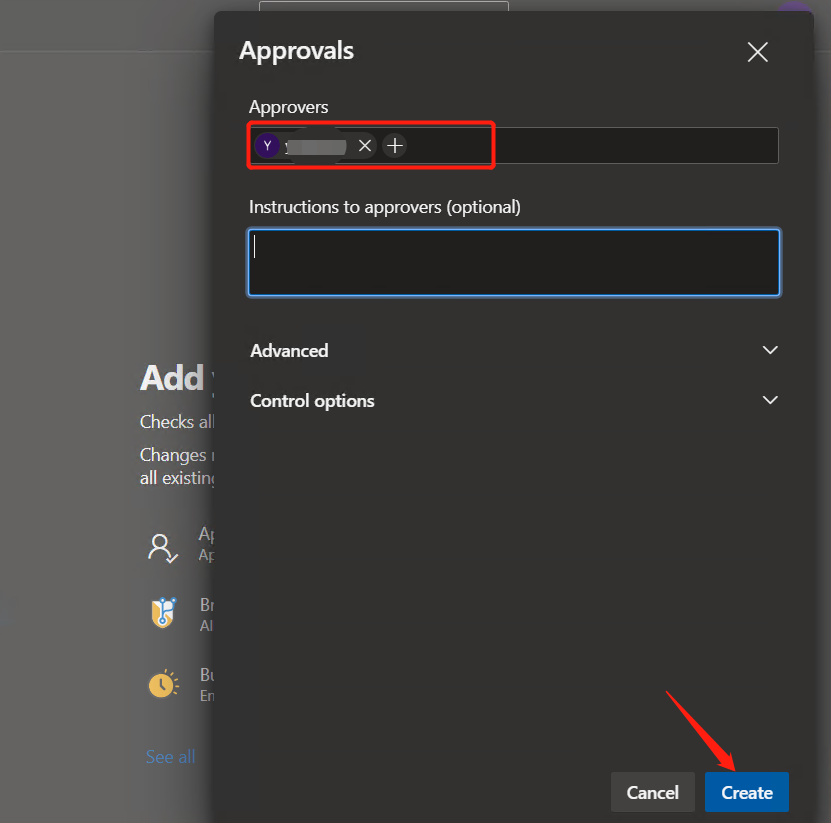
After adding, you can see the records with the type of "Approvals". You should note that the expiration time of approval is "30 days" by default, which can be changed according to the actual situation.
3. Configure Azure DevOps Pipeline
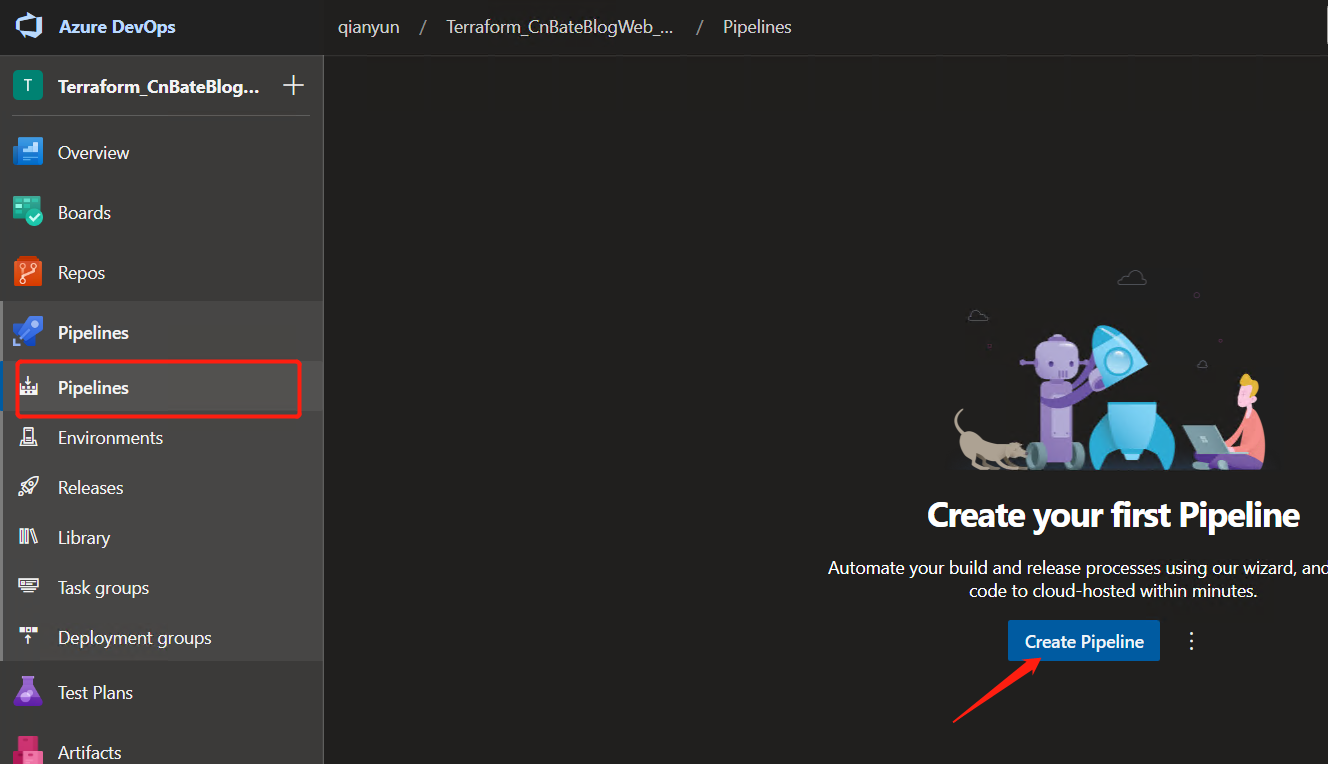
Select "Pipelines" in the left menu and click "Create Pipeline" to create} pipeline job
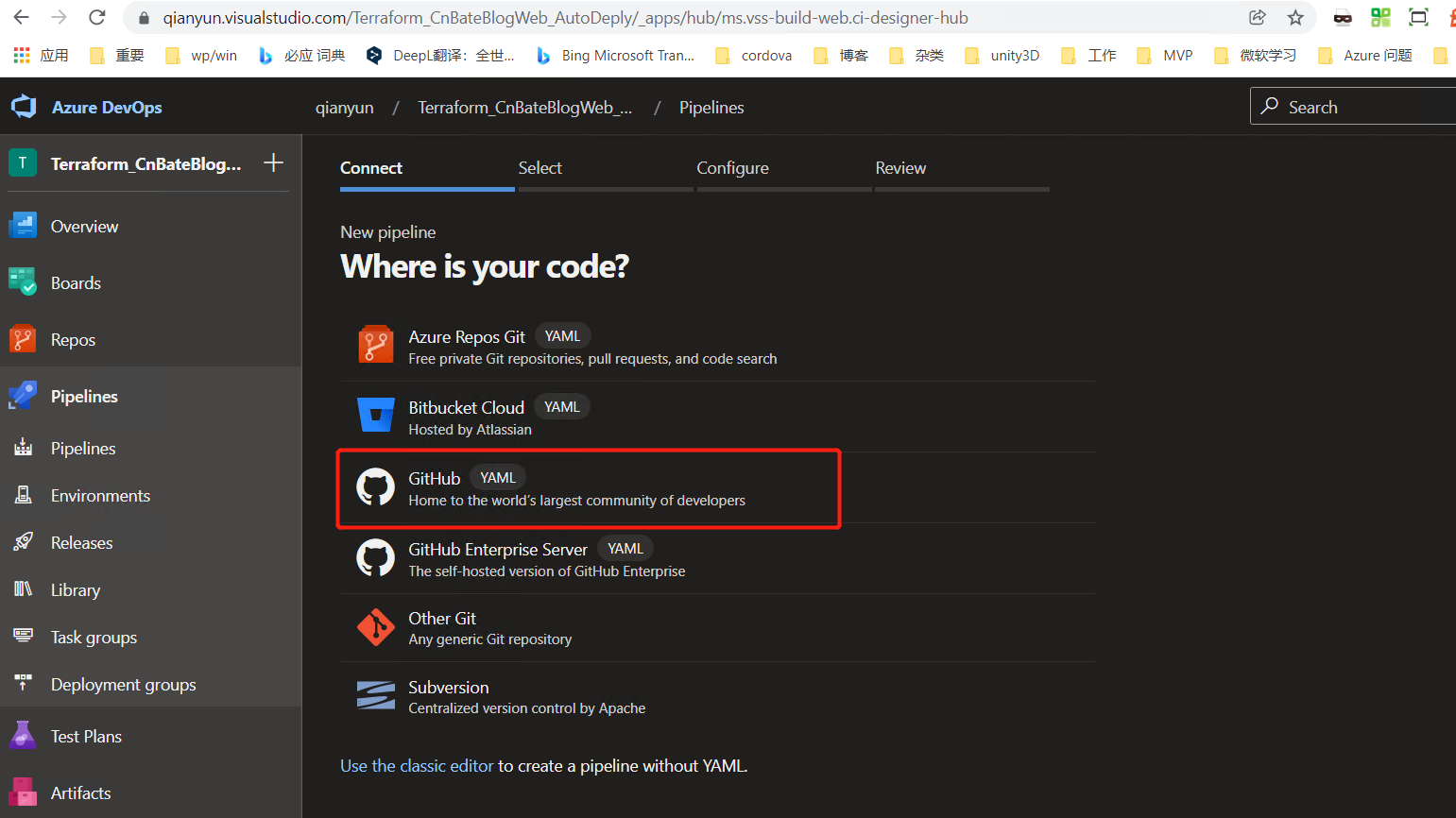
Instead of using the classic Editor Mode today, choose GitHub (yaml)
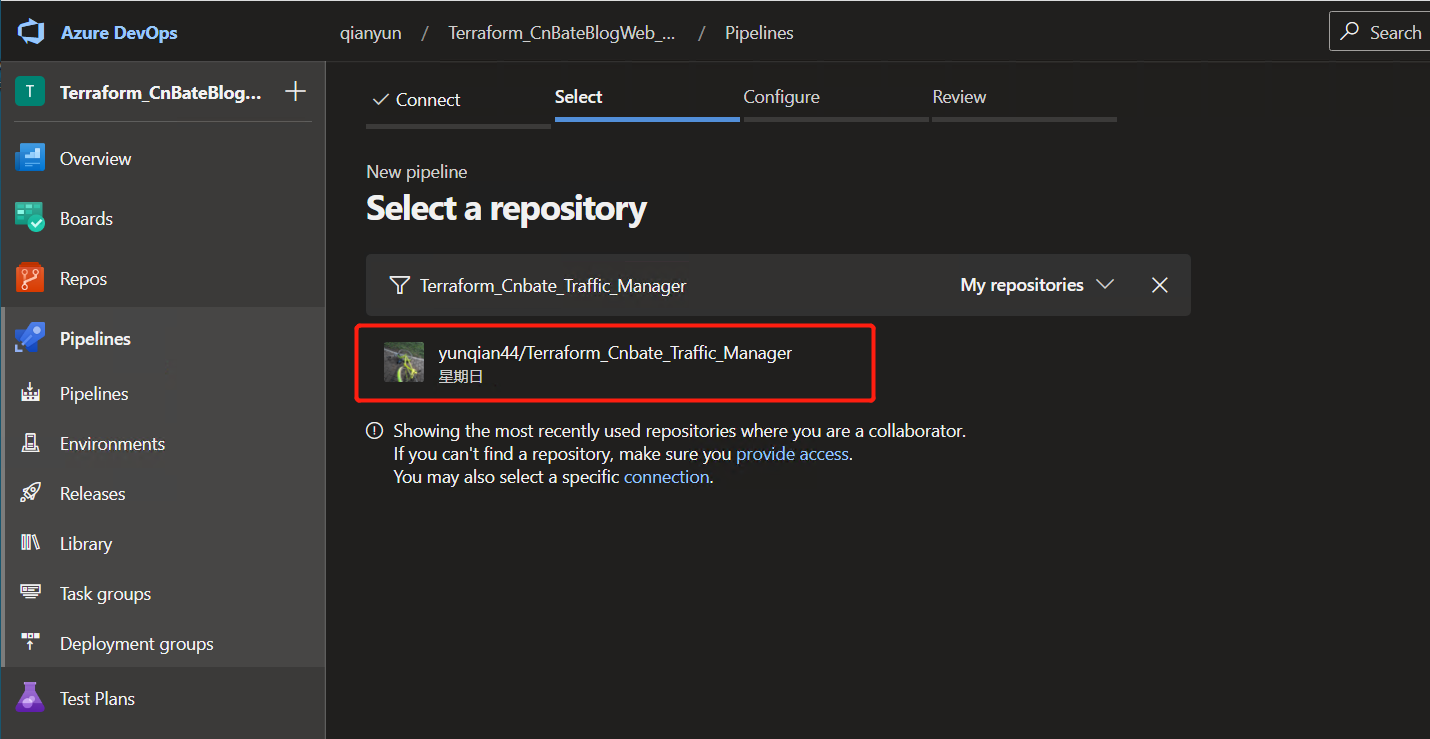
Select the code warehouse of the corresponding TF Code
Select "Start Pipeline" to open a new pipeline build deployment code
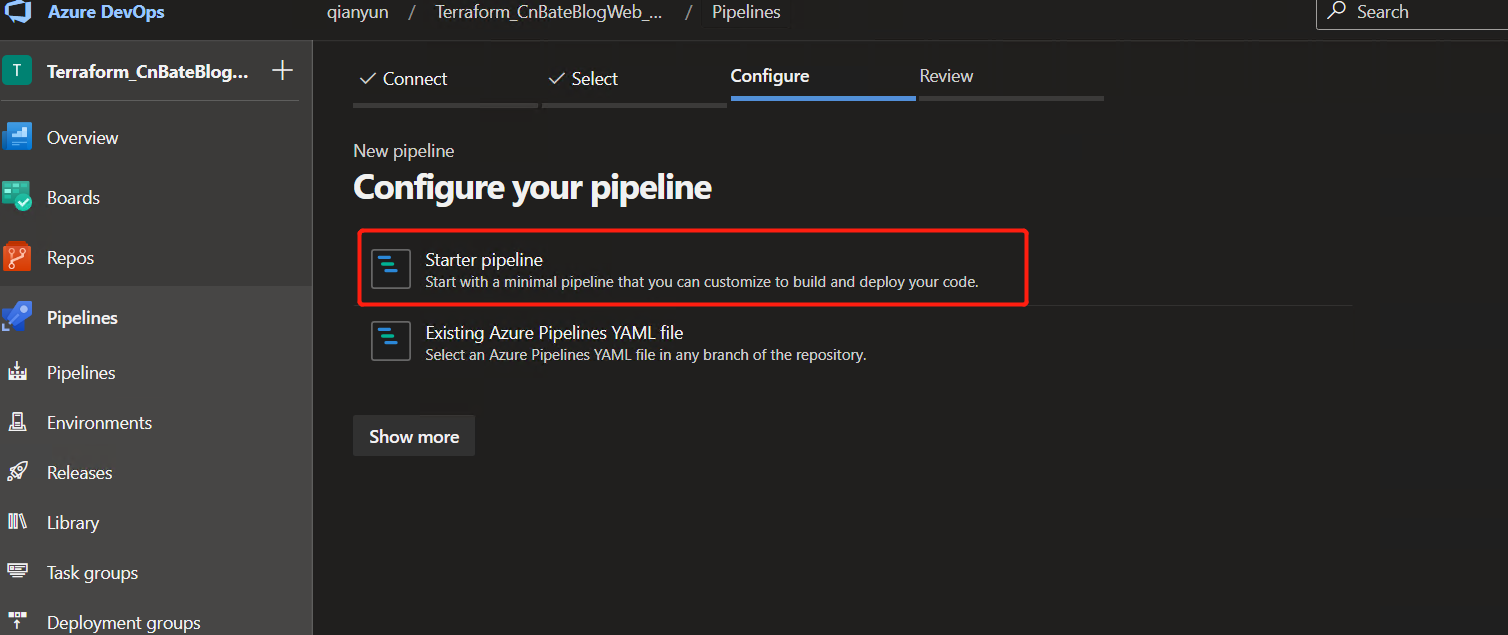
Azure DevOps will automatically generate a file named "azure pipelines. Yaml" in the project root directory for us, and we will add the defined pipeline steps to the file
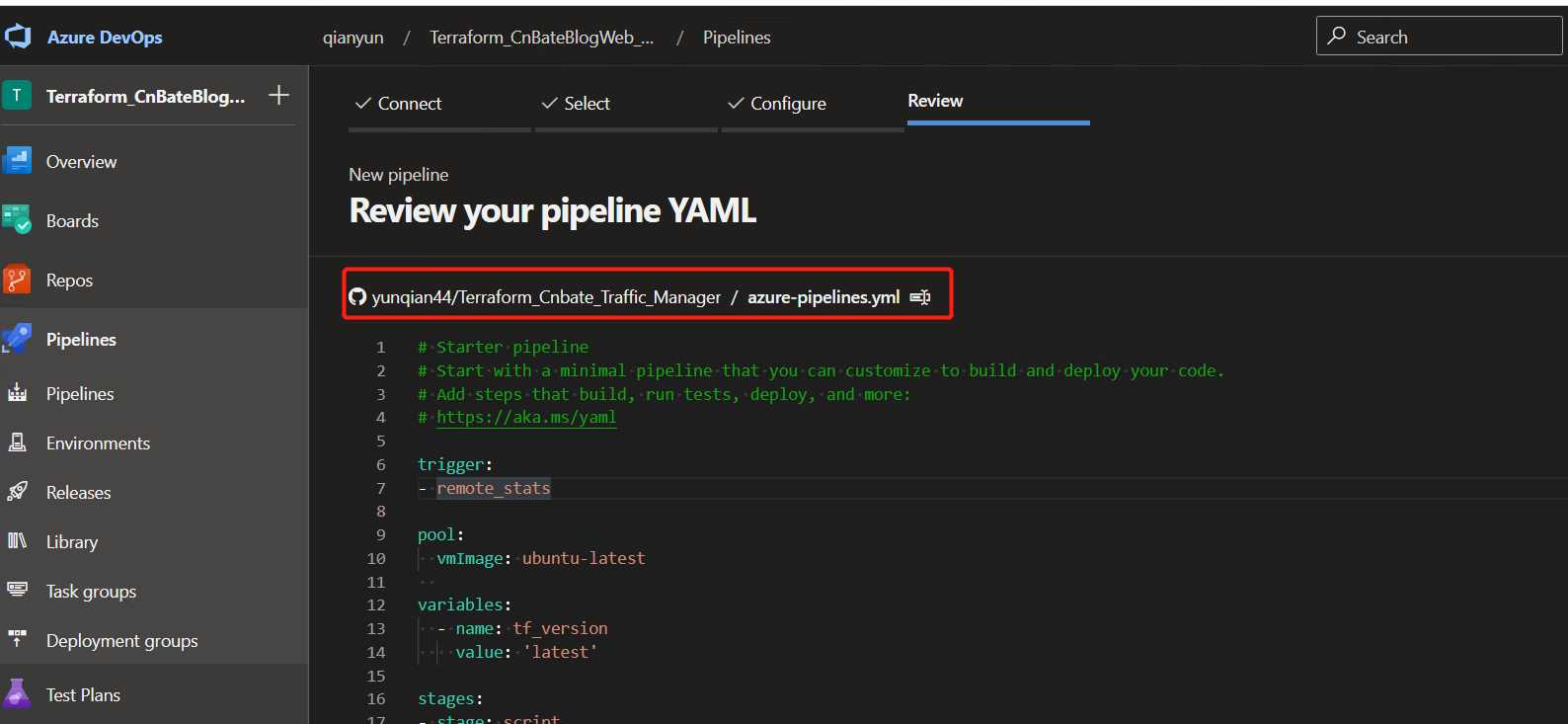
Pipe step approval yaml sample code
jobs: - deployment: terraform\_apply continueOnError: false environment: 'Approve\_Production' timeoutInMinutes: 120 strategy: runOnce: deploy: steps:
Note: I'll be in the} terrain_ Add an application request before the apply} phase
The red mark is the subscription that needs to be changed to your own Azure,
The orange flag is the variable to be added:
**1. Pipeline variable: * * tf_version
**2. Secret variable: * * * * terrain_ rg,**storage_account,storage_account_container,container_key,keyvault,keyvault_sc
1 # Starter pipeline
2 # Start with a minimal pipeline that you can customize to build and deploy your code.
3 # Add steps that build, run tests, deploy, and more:
4 # https://aka.ms/yaml
5
6 trigger:
7 - remote\_stats
8
9 pool:
10 vmImage: ubuntu-latest
11
12 **variables**:
13 - name: **tf\_version** 14 value: '**latest**'
15
16 stages:
17 - stage: script
18 jobs:
19 - job: azure\_cli\_script
20 steps:
21 - task: AzureCLI@2
22 displayName: 'Azure CLI :Create Storage Account,Key Vault And Set KeyVault Secret'
23 inputs:
24 azureSubscription: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
25 scriptType: 'bash'
26 scriptLocation: 'inlineScript'
27 inlineScript: |
28 # create azure resource group
29 az group create --location eastasia --name **$(terraform\_rg)** 30
31 # create azure storage account
32 az storage account create --name **$(storage\_account)** --resource-group **$(terraform\_rg)** --location eastasia --sku Standard\_LRS
33
34 # create storage account container for tf state
35 az storage container create --name **$(storage\_account\_container)** --account-name **$(storage\_account)** 36
37 # query storage key and set variable
38 ACCOUNT\_KEY=$(az storage account keys list --resource-group **$(terraform\_rg)** --account-name **$(storage\_account)** --query "[?keyName == 'key1'][value]" --output tsv)
39
40 # create azure keyvault
41 az keyvault create --name **$(keyvault)** --resource-group **$(terraform\_rg)** --location eastasia --enable-soft-delete false
42
43 # set keyvault secret,secret value is ACCOUNT\_KEY
44 az keyvault secret set --name **$(keyvault\_sc)** --vault-name **$(keyvault)** --value $ACCOUNT\_KEY
45
46 - task: AzureKeyVault@2
47 displayName: 'Azure Key Vault :Get Storage Access Secret'
48 inputs:
49 azureSubscription: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
50 KeyVaultName: '$(keyvault)'
51 SecretsFilter: 'terraform-stste-storage-key'
52 RunAsPreJob: false
53
54 - stage: terraform\_validate
55 jobs:
56 - job: terraform\_validate
57 steps:
58 - task: TerraformInstaller@0
59 inputs:
60 terraformVersion: ${{variables.tf\_version}}
61 - task: TerraformTaskV2@2
62 displayName: 'terraform init'
63 inputs:
64 provider: 'azurerm'
65 command: 'init'
66 # commandOptions: '-backend-config="access\_key=$(terraform-stste-storage-key)"'
67 backendServiceArm: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
68 backendAzureRmResourceGroupName: $(terraform\_rg)
69 backendAzureRmStorageAccountName: $(storage\_account)
70 backendAzureRmContainerName: $(storage\_account\_container)
71 backendAzureRmKey: $(container\_key)
72 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
73 - task: TerraformTaskV2@2
74 inputs:
75 provider: 'azurerm'
76 command: 'validate'
77 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
78
79 - stage: terraform\_plan
80 dependsOn: [terraform\_validate]
81 condition: succeeded('terraform\_validate')
82 jobs:
83 - job: terraform\_plan
84 steps:
85 - task: TerraformInstaller@0
86 inputs:
87 terraformVersion: ${{ variables.tf\_version }}
88 - task: TerraformTaskV2@2
89 displayName: 'terraform init'
90 inputs:
91 provider: 'azurerm'
92 command: 'init'
93 # commandOptions: '-backend-config="access\_key=$(terraform-stste-storage-key)"'
94 backendServiceArm: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
95 backendAzureRmResourceGroupName: $(terraform\_rg)
96 backendAzureRmStorageAccountName: $(storage\_account)
97 backendAzureRmContainerName: $(storage\_account\_container)
98 backendAzureRmKey: $(container\_key)
99 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
100 - task: TerraformTaskV2@2
101 inputs:
102 provider: 'azurerm'
103 command: 'plan'
104 environmentServiceNameAzureRM: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
105 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
106
107 - stage: terraform\_apply
108 dependsOn: [terraform\_plan]
109 condition: succeeded('terraform\_plan')
110 jobs:
111 - deployment: terraform\_apply
112 continueOnError: false
113 environment: 'Approve\_Production'
114 timeoutInMinutes: 120
115 strategy:
116 runOnce:
117 deploy:
118 steps:
119 - checkout: self
120 - task: TerraformInstaller@0
121 inputs:
122 terraformVersion: ${{ variables.tf\_version }}
123 - task: TerraformTaskV2@2
124 displayName: 'terraform init'
125 inputs:
126 provider: 'azurerm'
127 command: 'init'
128 # commandOptions: '-backend-config="access\_key=$(terraform-stste-storage-key)"'
129 backendServiceArm: '**Microsoft Azure Subscrription(XXXX-XXX-XX-XX-XXX)**'
130 backendAzureRmResourceGroupName: $(terraform\_rg)
131 backendAzureRmStorageAccountName: $(storage\_account)
132 backendAzureRmContainerName: $(storage\_account\_container)
133 backendAzureRmKey: $(container\_key)
134 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
135 - task: TerraformTaskV2@2
136 inputs:
137 provider: 'azurerm'
138 command: 'plan'
139 environmentServiceNameAzureRM: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
140 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
141 - task: TerraformTaskV2@2
142 inputs:
143 provider: 'azurerm'
144 command: 'apply'
145 commandOptions: '-auto-approve'
146 environmentServiceNameAzureRM: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
147 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
148
149 # - stage: terraform\_apply
150 # dependsOn: [terraform\_plan]
151 # condition: succeeded('terraform\_plan')
152 # jobs:
153 # - job: terraform\_apply
154 # steps:
155 # - task: TerraformInstaller@0
156 # inputs:
157 # terraformVersion: ${{ variables.tf\_version }}
158 # - task: TerraformTaskV2@2
159 # displayName: 'terraform init'
160 # inputs:
161 # provider: 'azurerm'
162 # command: 'init'
163 # # commandOptions: '-backend-config="access\_key=$(terraform-stste-storage-key)"'
164 # backendServiceArm: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
165 # backendAzureRmResourceGroupName: $(terraform\_rg)
166 # backendAzureRmStorageAccountName: $(storage\_account)
167 # backendAzureRmContainerName: $(storage\_account\_container)
168 # backendAzureRmKey: $(container\_key)
169 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
170 # - task: TerraformTaskV2@2
171 # inputs:
172 # provider: 'azurerm'
173 # command: 'plan'
174 # environmentServiceNameAzureRM: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
175 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
176 # - task: TerraformTaskV2@2
177 # inputs:
178 # provider: 'azurerm'
179 # command: 'apply'
180 # commandOptions: '-auto-approve'
181 # environmentServiceNameAzureRM: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
182 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
183
184 - stage: terraform\_destroy
185 dependsOn: [terraform\_apply]
186 condition: succeeded('terraform\_apply')
187 jobs:
188 - job: terraform\_destroy
189 steps:
190 - task: TerraformInstaller@0
191 inputs:
192 terraformVersion: ${{ variables.tf\_version }}
193 - task: TerraformTaskV2@2
194 displayName: 'terraform init'
195 inputs:
196 provider: 'azurerm'
197 command: 'init'
198 # commandOptions: '-backend-config="access\_key=$(terraform-stste-storage-key)"'
199 backendServiceArm: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
200 backendAzureRmResourceGroupName: $(terraform\_rg)
201 backendAzureRmStorageAccountName: $(storage\_account)
202 backendAzureRmContainerName: $(storage\_account\_container)
203 backendAzureRmKey: $(container\_key)
204 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
205 - task: TerraformTaskV2@2
206 inputs:
207 provider: 'azurerm'
208 command: 'plan'
209 environmentServiceNameAzureRM: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
210 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
211 - task: TerraformTaskV2@2
212 inputs:
213 provider: 'azurerm'
214 command: 'destroy'
215 commandOptions: '-auto-approve'
216 environmentServiceNameAzureRM: '**Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)**'
217 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
Add a secret variable and click "Variables =" New variable "
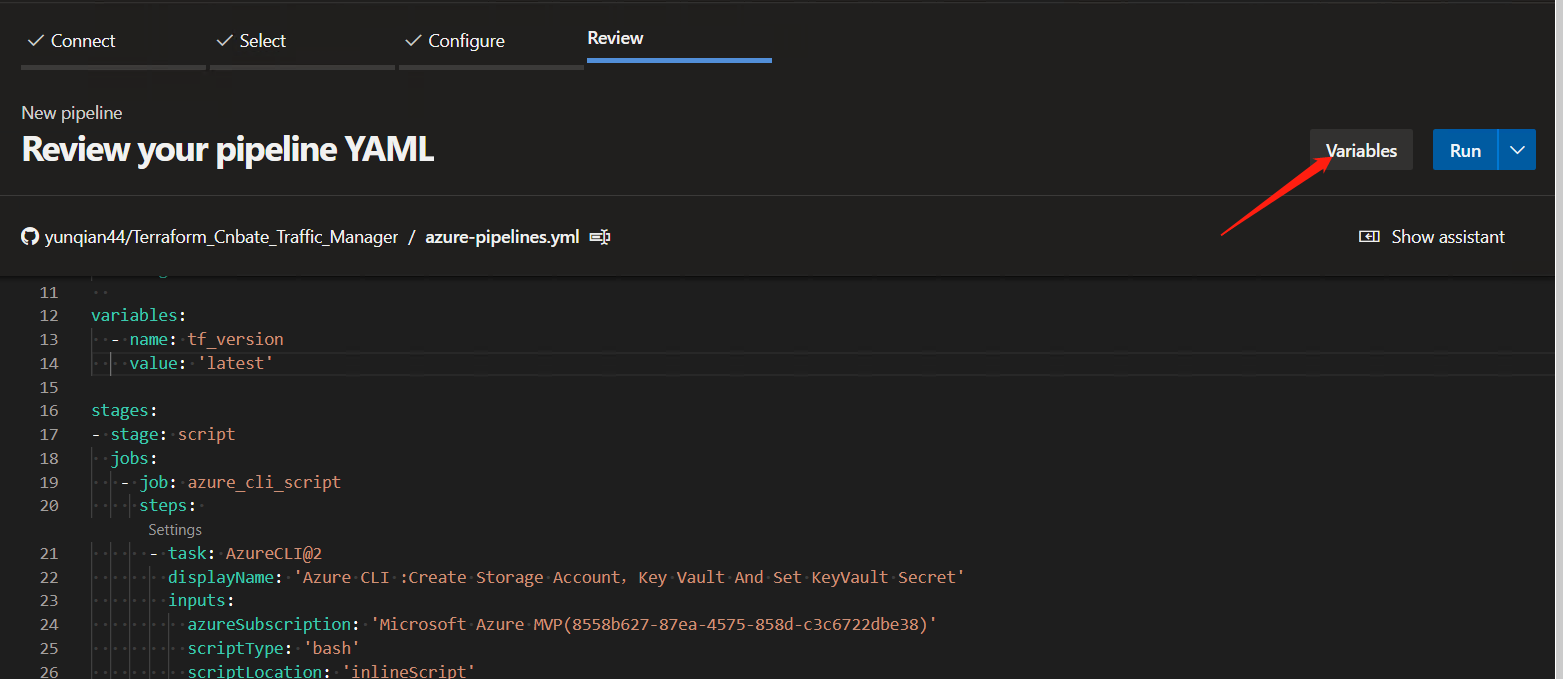
Enter the name and value of the secret
Name: "terraform_rg"
Value: "Web_Test_TF_RG"
Click "OK" to confirm the addition
Add the following confidential information at one time as above
terraform_rg: "Web_Test_TF_RG"
storage_account: "cnbatetfstorage"
storage_account_container: "tf-state001"
container_key: "cnbate.tf.stats"
keyvault: "cnbate-terraform-kv001"
keyvault_sc: "terraform-stste-storage-key"
After completing the above information, click "Run" to manually trigger the current Pipeline
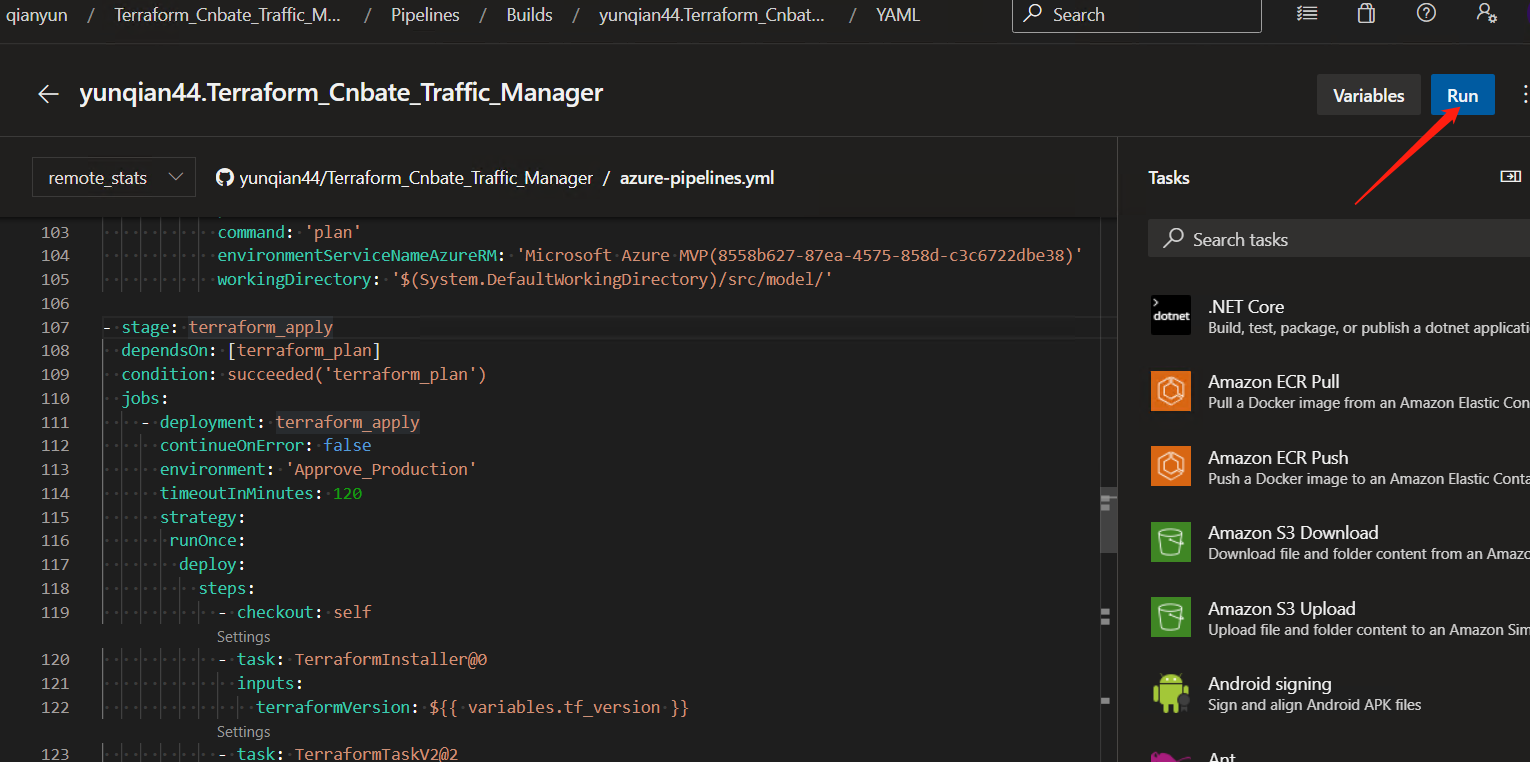
Select the branch "remote_stats" and click "Run"
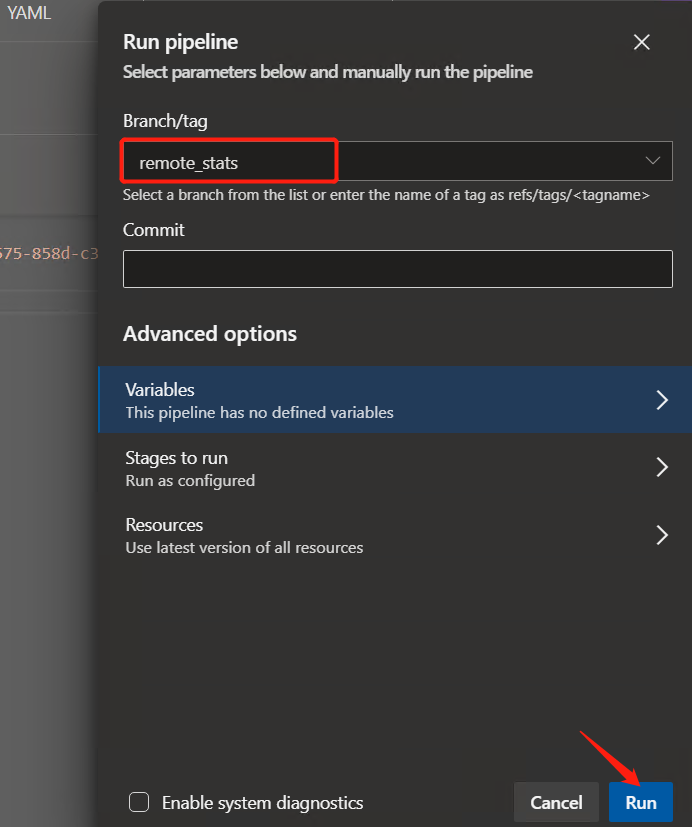
Next, we will see the whole process steps and the currently running steps. If approval is required, the process will be suspended and subsequent operations will be performed after the approval is completed
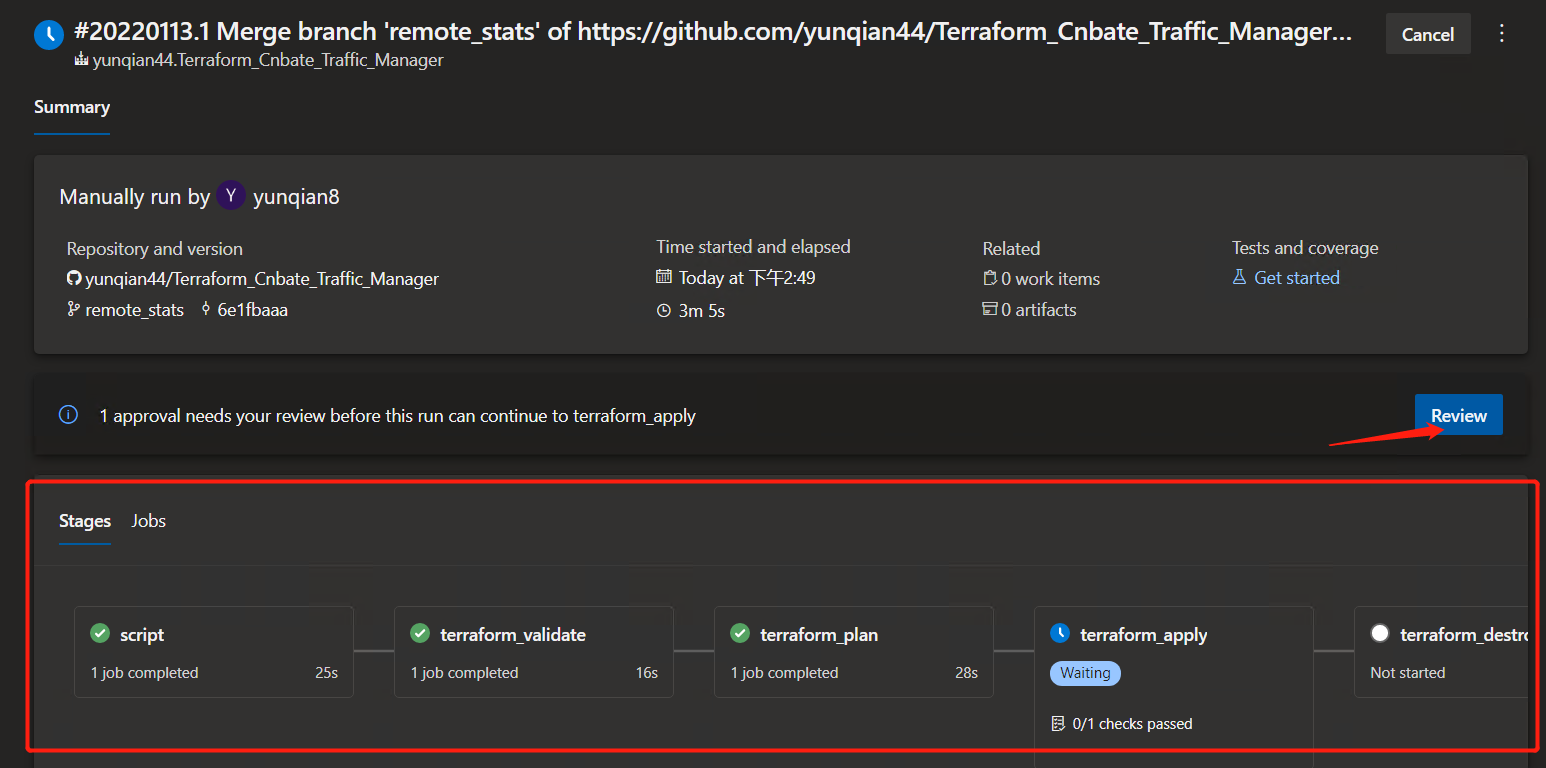
Click "Approve" to Approve and proceed to the next step to execute the deployment plan
OK, success!!! Deployment complete. yes ✨😁 ヾ(≧▽≦*)o
3, End
For the operation of today's experiment, you can practice more and refer to the author's github warehouse. Today's content needs to be operated on Azure DevOps. We should practice more. As for the Terraform code, there is not much explanation, mainly because we have a certain understanding of Terraform in combination with the previous deployment of Azure resources. So you can download, analyze and modify by yourself.
reference material: Terraform official,Azure Pipeline document
Terraform_Cnbate_Traffic_Manager github Address: https://github.com/yunqian44/Terraform_Cnbate_Traffic_Manager
Welcome to the blogger's blog: https://allenmasters.com/
Author: Allen
Copyright: please indicate the author and source in the obvious position of the article. If mistakes are found, criticism and correction are welcome.