Having a more secure channel is the best way to transmit user information across the network
cryptography
Most of the problems on the network are related to security issues and the storage and transmission of sensitive data in the network. So we must provide a secure system on it. The most popular and practical way to establish a secure connection in the network is encryption technology. Encryption technology is the process of encrypting and decrypting data to ensure data security. For example, in the following figure, Bob wants to send data to Alice. This data is called the message and input parameters of the encryption process. Then add a specific key with encryption function to this message and generate a ciphertext, that is, our encrypted message. Therefore, this message passes through the network, and the hacker is waiting to steal this data.
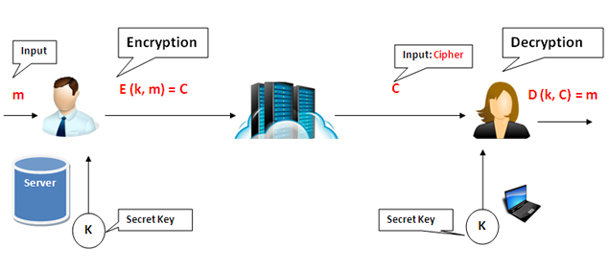
In another stage, Alice waits to receive Bob's message. On this side, there is a decryption function that decrypts the message with the same key. This secret key is exactly like Bob's. Therefore, the decryption function with the same key and ciphertext (encryption key) will generate a decryption message for Alice, and finally Alice will receive Bob's message. This process is called symmetric encryption.
The biggest problem in this process is to provide a powerful and complex key. Because encryption and decryption algorithms are available on the Internet and use almost similar steps and functions to encrypt data and change these algorithms, it is useless because hackers can easily find them. Therefore, we must focus on making power keys to ensure the security of confidential data.
- Cryptography is a great tool for any security problem.
- However, cryptography is not suitable for naive users to make actions that harm themselves, especially for social attackers.
- Cryptography needs to innovate new methods, because using the old encryption system is as bad as not using it.
- If the implementation of cryptography is not correct, it can only correctly meet your requirements.
Some secure communication solutions
- Web traffic: HTTPS - > secure sockets layer (SSL/TLS)
- Wireless traffic: GSM: 802.11 or WPA2: Bluetooth
- Encrypted files on disk
Advanced Encryption Standard (AES)
AES is one of the encryption technologies using the same key and based on Rijndael cryptographic algorithm. AES is based on substitution and permutation functions and uses complex methods to generate powerful and almost unbreakable keys, which is our goal to transmit our sensitive data over the network.
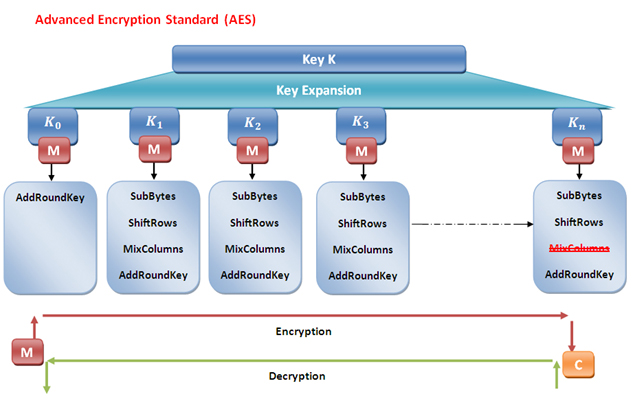
In the first step, AES expands the key with a length of 128 bits to more than ten keys, in which the length of each key is 128 bits, that is, the number of key construction cycles generated. Messages as input parameters are mixed with these keys. AES only uses the "" function in K # 0, SubBytes, Shiftrows and AddRoundKey in K # n, and all four functions "AddRoundKey", "SubBytes", "Shiftrows" and "AddRoundKey" in AES from K # 2 to K # n-1. Finally, the message or plaintext will be converted into encrypted message or ciphertext through these complex functions.
AES reverse uses this mode to generate the same message from encrypted messages. AES converts the message text and key into a four by four matrix because it is easier to work in matrix form than in the original form. Look at the figure below to have a clearer imagination of what happens inside the AES algorithm.
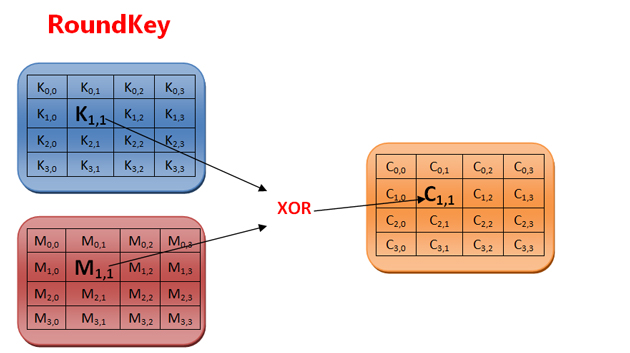
Add wheel key
This function mixes K ^ i,j and M ^ i,j through the XOR function. This means that AES extracts row i and column j from the message and key, applies the XOR function to these coincident rows and columns, and generates C ^ i,j. In the following figure, XOR is applied between the blue key and the red message to generate an orange password.
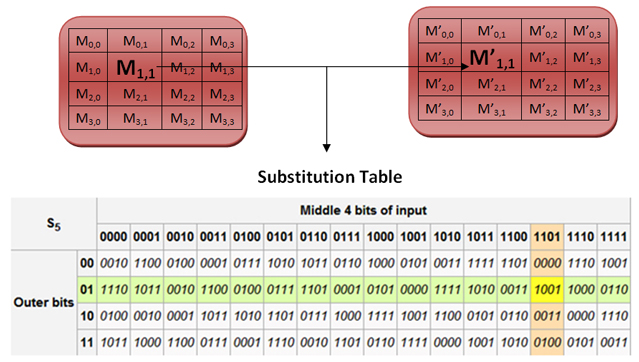
Sub byte
This function finds the replacement of M i,j from the replacement table with specific patterns and steps, and replaces the new with m ~ i,j. This means that AES extracts row i and column j from the message, applies the substitution function to each row and column of the message matrix, and generates the cryptographic matrix C ^ i,j.
Mixed column
There is a fixed matrix C, which will affect the message matrix. In the first step, it does not change the first row, but moves the second row to the left and the third row to the left, and applies the XOR function for this.
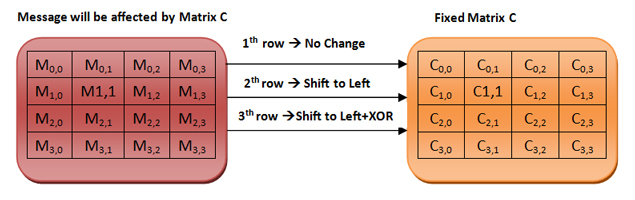
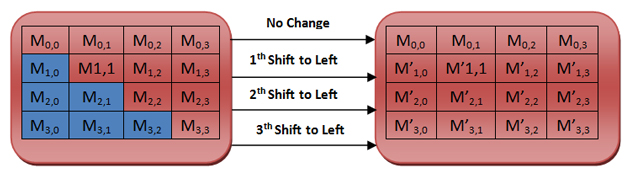
Migration
This function selects the message matrix and does not change the first row of the matrix. Then, for the second row, move a cell to replace M # 1,0 with M # 1,3. Move two for the second row and three for the third row.
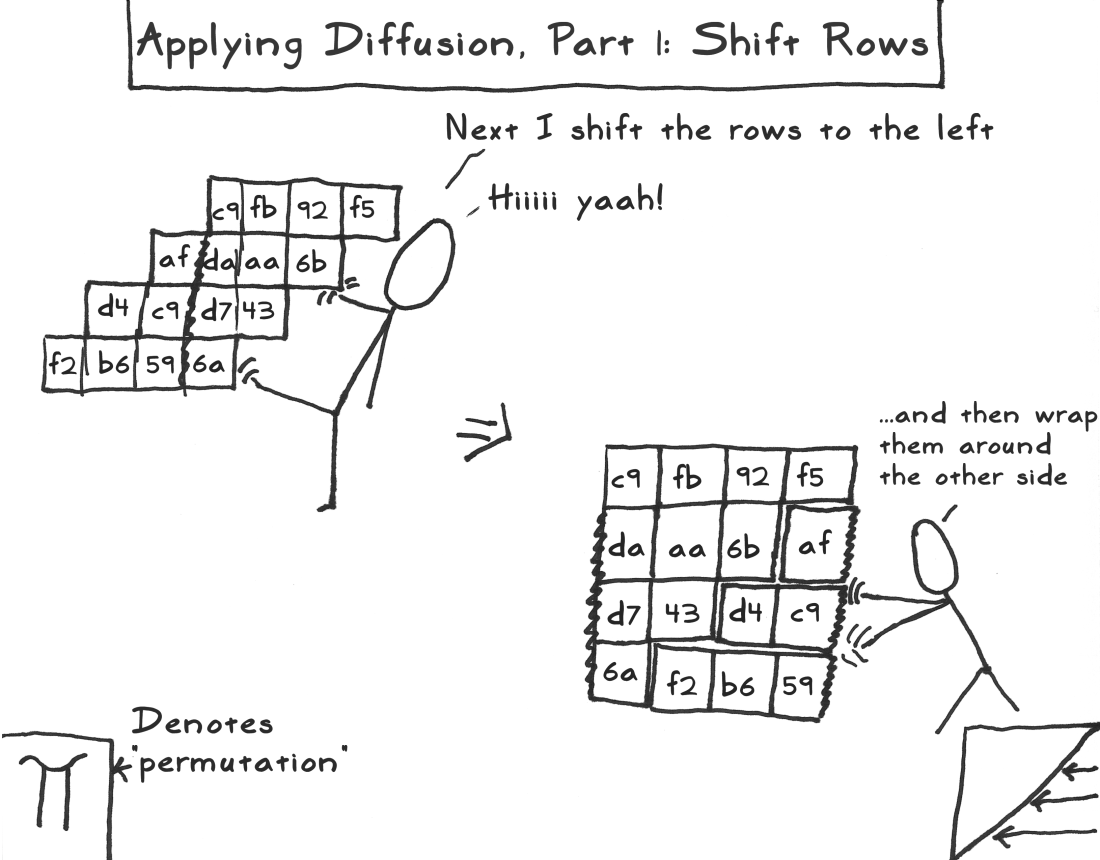
I have explained the following figure as a deeper operation within AES. DES and 3DES algorithms are almost similar to AES, except that 3DES is 168 bits, which is a bit more than AES, but it only uses permutation functions to generate keys, while AES uses permutation and substitution functions, and takes less time than 3DES.

My network security solutions
I want to publish a solution with authentication and authorization to identify users. Authentication allows us to know whether the user's declaration is correct by obtaining the user name and password. One solution is to use this part as a two-step authentication, first by obtaining a password, and then by biometrics. In this state, if someone steals the user's password, the hacker will not be able to access the user's personal data.
The next part is authorization, which is related to permission management to determine whether a specific role has access to and view a specific part. For example, here (in an electronic healthcare system), doctors have access to their patients' health information and read or write EHR.
The third part is encryption technology (AES). As I mentioned above, AES uses different functions to encrypt data from hackers. Therefore, the data in the database can be saved as encrypted text instead of plain text to increase security problems.
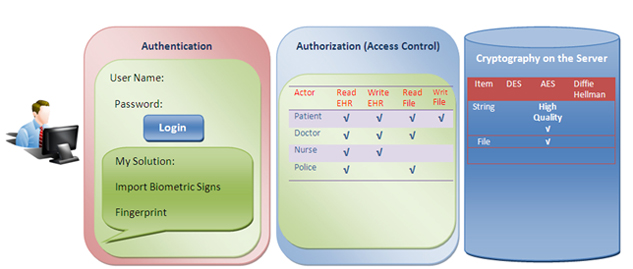
More description of my solution
My solution is to use biometrics and mix this key with the key to generate a more powerful and secure key in AES. The biometric key can be extracted from fingerprints or corneal markers. Today, fingerprints can be captured by mobile phones (such as iPhones), and these data can be converted into a second key matrix and mixed with the secret key of the strong key we have. These marks are always available, we will not forget them, and hackers can't get them, so this is a good solution to maintain data confidentiality.
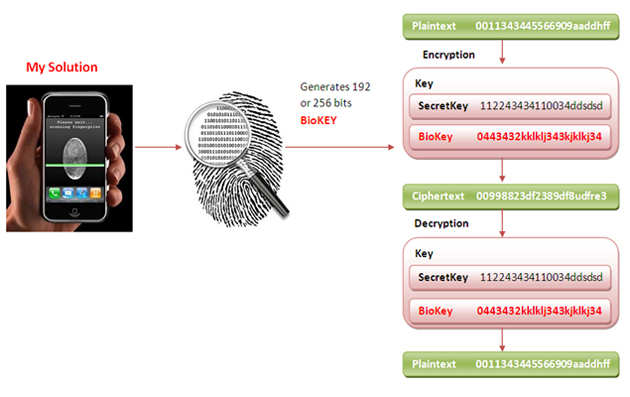
How to use and implement code
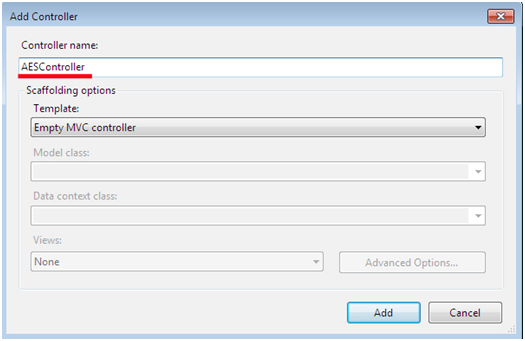
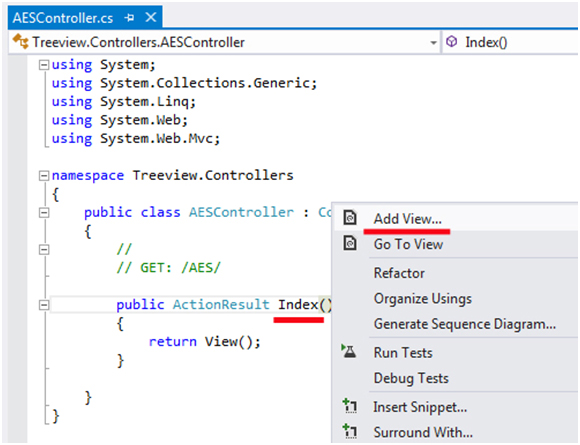
First, open visual studio 2013 - > file (menu) - > new project - > ASP NET MVC -> Empty Controller -> Add New Controller
using System;
using System.Collections.Generic;
using System.IO;
using System.Linq;
using System.Security.Cryptography;
using System.Text;
using System.Web;
using System.Web.Mvc;
namespace WebSecurity.Controllers
{
public class AESController : Controller
{
//
// GET: /AES/
public ActionResult Index()
{
ViewData["Encrypted"] = TempData["TEncrypted"];
ViewData["Decrypted"] = TempData["TDecrypted"];
return View();
}
//txtforEN is PlainText
//Key is Public Secret Key
[HttpPost]
public ActionResult Encryption(string Text, string Key)
{
// Convert String to Byte
byte[] MsgBytes = Encoding.UTF8.GetBytes(Text);
byte[] KeyBytes = Encoding.UTF8.GetBytes(Key);
// Hash the password with SHA256
//Secure Hash Algorithm
//Operation And, Xor, Rot,Add (mod 232),Or, Shr
//block size 1024
//Rounds 80
//rotation operator , rotates point1 to point2 by theta1=> p2=rot(t1)p1
//SHR shift to right
KeyBytes = SHA256.Create().ComputeHash(KeyBytes);
byte[] bytesEncrypted = AES_Encryption(MsgBytes, KeyBytes);
string encryptionText = Convert.ToBase64String(bytesEncrypted);
TempData["TEncrypted"] = encryptionText;
return RedirectToAction("Index");
}
public byte[] AES_Encryption(byte[] Msg, byte[] Key)
{
byte[] encryptedBytes = null;
//salt is generated randomly as an additional number to
//hash password or message in order o dictionary attack
//against pre computed rainbow table
//dictionary attack is a systematic way to test
//all of possibilities words in dictionary weather or not is true?
//to find decryption key
//rainbow table is precomputed key for cracking password
// Set your salt here, change it to meet your flavor:
// The salt bytes must be at least 8 bytes. == 16 bits
byte[] saltBytes = new byte[] { 1, 2, 3, 4, 5, 6, 7, 8 };
using (MemoryStream ms = new MemoryStream())
{
using (RijndaelManaged AES = new RijndaelManaged())
{
AES.KeySize = 256;
AES.BlockSize = 128;
var key = new Rfc2898DeriveBytes(Key, saltBytes, 1000);
AES.Key = key.GetBytes(AES.KeySize / 8);
AES.IV = key.GetBytes(AES.BlockSize / 8);
AES.Mode = CipherMode.CBC;
using (var cs = new CryptoStream
(ms, AES.CreateEncryptor(), CryptoStreamMode.Write))
{
cs.Write(Msg, 0, Msg.Length);
cs.Close();
}
encryptedBytes = ms.ToArray();
}
}
return encryptedBytes;
}
[HttpPost]
public ActionResult Decryption(string Text2, string Key2)
{
// Convert String to Byte
byte[] MsgBytes = Convert.FromBase64String(Text2);
byte[] KeyBytes = Encoding.UTF8.GetBytes(Key2);
KeyBytes = SHA256.Create().ComputeHash(KeyBytes);
byte[] bytesDecrypted = AES_Decryption(MsgBytes, KeyBytes);
string decryptionText = Encoding.UTF8.GetString(bytesDecrypted);
TempData["TDecrypted"] = decryptionText;
return RedirectToAction("Index");
}
public byte[] AES_Decryption(byte[] Msg, byte[] Key)
{
byte[] decryptedBytes = null;
// Set your salt here, change it to meet your flavor:
// The salt bytes must be at least 8 bytes.
byte[] saltBytes = new byte[] { 1, 2, 3, 4, 5, 6, 7, 8 };
using (MemoryStream ms = new MemoryStream())
{
using (RijndaelManaged AES = new RijndaelManaged())
{
AES.KeySize = 256;
AES.BlockSize = 128;
var key = new Rfc2898DeriveBytes(Key, saltBytes, 1000);
AES.Key = key.GetBytes(AES.KeySize / 8);
AES.IV = key.GetBytes(AES.BlockSize / 8);
AES.Mode = CipherMode.CBC;
using (var cs = new CryptoStream
(ms, AES.CreateDecryptor(), CryptoStreamMode.Write))
{
cs.Write(Msg, 0, Msg.Length);
cs.Close();
}
decryptedBytes = ms.ToArray();
}
}
return decryptedBytes;
}
}
}Right click actions (add view) - > select Add Index.
@{
ViewBag.Title = "Index";
Layout = "~/Views/Shared/_Layout.cshtml";
}
<h2>Encryption And Decryption</h2>
<div style="color:red;" id="EncryptedText"
>Encrypted Message: @ViewData["Encrypted"]</div>
<div style="color:red;" id="DecryptedText"
>Decrypted Message: @ViewData["Decrypted"]</div>
<pre>
@using(Html.BeginForm("Encryption", "AES", FormMethod.Post))
{
<label id="lbk1">Key:</label>
<input name="Key" id="Key" type="text" />
<br />
<br />
<label id="lbk2">Message:</label>
<input name="Text" id="Text" type="text" />
<br />
<br />
<input id="btnEncryption" type="submit" value="Encryption" />
<br />
<br />
}
How to test an application
For encryption:
- Enter a Key, such as Key=122
- Input message: Message = Mahsa
- Press the encrypt button
- You will see the password text -- > encrypted message: 7gkI7SpPzsOiJ8O2OO2jOQ==
For decryption:
- Enter the same key = "122"
- Enter encrypted message -- > 7gkI7SpPzsOiJ8O2OO2jOQ==
- Press the decrypt button
- You will see the decrypted message: Mahsa
Security Assertion Markup Language (SAML)
SAML is an open standard based on XML. It formats data, which should transmit user information as encrypted data between identity providers and service providers. It includes a specific label that contains this encrypted data.
<saml:Assertion ..> "includes important message from identity provider to service provider "Who is this user (Attribute Identity) "Is he/she allowed to consume service? </saml:Assertion>
When a service provider invokes a direct query to an identity provider through a secure channel, the SAML protocol is requested. A popular use in SAML is single sign on (SSO) for Web browsers. In this problem, the following problems occur when using SAML:
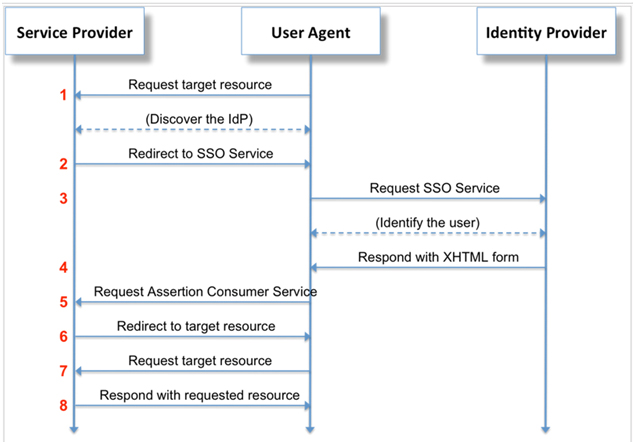
- Request target resource
Users can enter in the address bar through web browsers such as Chrome or Mozila www.sample.com For example: http : //www.stackoverflow.com/, And send a request to use a specific service from stack overflow as a service provider. This user can use stack authentication to enter their user name and password directly, or select one of the authentication options from the login page.
- Redirect to SSO service
Assuming that the user selects the Google option for the authentication process, stack overflow will remove him / her from the http://www.stackoverflow.com/ Redirect to https://accounts.google.com.
- Request SSO service
In this example, stack overflow is a service provider that provides users with the required services, while Google COM is an identity provider that performs single sign on for users. Google identifies users by requesting some information belonging to users (such as user name and password) and checks whether these credentials are valid. The identity provider uses directory services such as LDAP, Radius, and Active Directory for authentication.
- Respond with XHTML form
At this stage, the user should press Google.com as an identity provider Com to allow some of his / her information (such as user name and email) to be delivered and transmitted to the service provider. When he / she does so, the identity provider responds to the service provider in XHTML (the following code).
<form method="post" action="https://sp.example.com/SAML2/SSO/POST" ...> <input type="hidden" name="SAMLResponse" value="response" /> <input type="submit" value="Submit" /> </form> - Request assertion consumer service
If in the above XHTML, the identity provider allows the user to use the service from the service provider, so the user redirects to the service provider, and he / she is a valid user of the site and can use the required service. (although at this stage, the service provider performs an authorization process to check his / her access rights to each service).
- Redirect to target resource
At this stage, the service provider performs an authorization process to check his / her access rights to each service, and then the user will be redirected to the target resource.
- Request target resource
The user requests a specific resource from the service provider. As I mentioned above, if the service provider confirms the license, the user can use it. as http://astronomy.stackexchange.com/
- Response to resource request
If the user has access to the service, the service provider redirects the user to the resource.
Dictionaries
In this section, I have explained some specific words that need more description. This part can solve misunderstandings and show my intention to use these words in my writing style.
XML
Extensible markup language is a markup language that contains specific rules for encoding and formatting documents so that they are readable by people and machines. XML can be used to process Web applications and services to organize different types of data structures and human languages.
XML has rules to define how to arrange our content. It includes "< div > < / div >" tag, class attribute in "". Finally, our data is located in the tag, such as "", and its declaration starts with ""< div class=”class1”></div>Hello“<div class=”class1”>Hello</div>”<? xml version="1.0" encoding="UTF-8"?>
Security Token
A security token is a device that generates a key for the authentication process. It is an additional tool that can improve security to detect whether users really claim who they are. It is a key generator, USB connector and Bluetooth wireless devices. It stores a key for cryptography problems (encryption and decryption functions), which can be a biometric, such as a fingerprint or a digital signature. The key with specific password function can generate a new digital number. The user enters the digital number after the user name and password. This key proves whether the user's claim is what he / she really claims. In the figure, the user enters the user name and password, then presses the key on the device, enters the number "54392971" as the password, and then clicks "login".

Service provider
Service providers are called companies and provide their customers with a list of services. These services are divided into telecommunications, applications, storage sites and the Internet.
identity provider
The identity provider is a third party. In addition to two parts (the authentication situation includes the consumer as the user and the supplier as the service provider), it detects whether the user is an authorized user and provides some important information of the user to the service provider, and finally authorizes the user to obtain the licensed consumer service.
For example, stackoverflow COM is a supplier (service provider), you can ask your questions in the relevant section. If users want to log in to this site, it has some options to do so, such as using Google, Facebook, Yahoo, LiveJournal, WordPress, Blogger, Verisign and AOL, or logging in through stackoverflow. If the user chooses stack overflow, he / she should create a user name and password for this site and enter all duplicate information here again. Whenever a user selects other options for the identity provider, he will redirect from stackoverflow to these websites, enter them with a specific user name and password, and then these websites will decide whether the user is valid or not? If the user is valid, the user's e-mail address and other information will be passed to the stack overflow site.

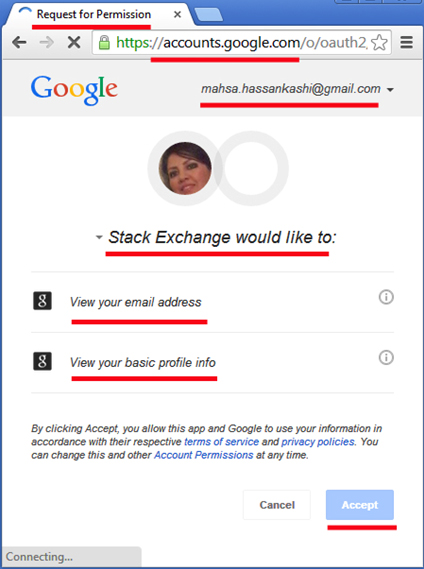
Redirect to Google for authentication (log in to Stackoverflow.com with a Google account).
LDAP
Lightweight Directory Access Protocol (LDAP) is an Internet protocol. LDAP finds information by creating an index for each data and filtering only the specific items needed.
Active Directory
Active Directory is a windows domain based directory service with authentication and authorization services. When a user logs in to a computer in a windows domain, Active Directory checks the password submitted by LDAP. If the user name and password have access to Active Directory, they are allowed to use the required services.
Window domain
A Windows domain is a network in which all users and computers and their peripherals are registered on a central computer.
Federated identity provider
Federated identity is a technology to establish a connection between user identity (user name and password) and other identity management, so as to authenticate the user and notify the source node that the user is valid. This means that you can have only one user name and password and are valid on multiple websites. Single sign on is a subset of Federated identities.
U-Prove
U-Prove is an encryption technology that reveals the minimum information of users who want to browse multiple websites, especially when users interact with identity providers. U-Prove is difficult to track what users want to do. The U-Prove token encrypts information through two functions. First, the encrypted "wrapping" of information without related handles leads to avoiding tracking users. Secondly, users disclose the least information in the process of verifier policy, such as "age", but do not explicitly disclose "date of birth".
Open ID
OpenID is a protocol that allows users to continue their authentication process. Other websites called "relying parties" are called third parties, such as Google, Microsoft, Facebook, AOL, etc.
Stateless and stateful
Stateless is a communication protocol that establishes independent requests and responses between the client and the server. In contrast, Stateful does not require the server to save information about the communication between requesters and responders, but Stateful requires the server to save information about its state. The internet protocol, the IP foundation and hypertext transmission} protocol of the Internet, HTTP and the foundation of network data communication are all examples of statelessness. Transmission control protocol TCP is an example of Stateful, which provides reliable and error checked communication between client and server.
conclusion
I used one of the most popular encryption techniques in my application as AES. AES is a symmetric encryption function. The sender and receiver use the same key. AES generates a strong key, which can not be cracked by hackers. Therefore, AES is a good method to maintain data confidentiality and integrity.