preface
It's also an interview experience shared by a fan
During the summer internship of his junior year, he went ashore with Tencent through three technical aspects and one hr. The questions asked by the interviewer are also quite representative. They compare the test principles and thinking logic, and sort them out for everyone to see. The students interviewed recently suggested collecting them, which is very helpful.

Interview process

- After 3 skills + 1hr, 4 rounds of interviews
- Technical side ----- 6.16
- Technical aspects ----- 6.18
- Three aspects of technology ----- 6.23
- Hrface ------6.30
- oc-------7.1
- offer----7.2
Interview questions
All the questions in this article must be endless. Here we'll pick some classic topics to talk to you.
For the complete interview questions, you can see this one I sorted out Real interview questions of Tencent Java post in 2021,
Of course, if you don't catch cold with Tencent, I'll sort out the real questions of other Internet top companies. I'll pay attention to the official account number: Java.
All right, stop talking nonsense and start the text.
As usual, I post the questions first and then put forward the answers. I can think about them first. If I don't, I can look down at the answers.
- Deep cloning, shallow cloning, and implementation method
- Java Object Access
- The method to solve Hash conflict, Hash conflict digitization
- Relationship between equals and hashcode
- Why Innodb chooses B + tree
- Thinking problem, balance weighs a small ball, finds a heavy one in a pile of light ones, and summarizes the general formula
- Scenario of topk problem
- Algorithm part:
① Split palindrome string
② Handwritten LRU, and describe the underlying principles, why use a two-way linked list
③ rand5()->rand7()
Interview questions
1. Deep cloning, shallow cloning, and implementation method
Shallow cloning: the reference type variable of an object copies the reference value of the object
Deep clone: copy the memory space of the object pointed to by the reference type variable to the new object
How to clone objects? There are three steps:
- Object class implements clonable interface;
- Override the clone() method of the Object class;
- Calling super. in the clone () method clone();
public class ShallowClone implements Cloneable{
public int id;
public String name;
public ShallowClone(int id, String name){
this.id = id;
this.name = name;
}
public Object clone(){
Object sc = null;
try {
sc = super.clone();
} catch (Exception e) {
System.out.println(e.toString());
}
return sc;
}
public static void main(String[] args) {
// TODO Auto-generated method stub
ShallowClone sc1 = new ShallowClone(1, "sc1Name");
ShallowClone sc2 = (ShallowClone)sc1.clone();
System.out.println("sc1's id: " + sc1.id + "\tsc2's id: " + sc2.id);
System.out.println("sc1's name: " + sc1.name + "\tsc2's name: " + sc2.name);
System.out.println(sc1.name == sc2.name);
System.out.println(sc1.name.equals(sc2.name));
}
}
Output results:
sc1's id: 1 sc2's id: 1 sc1's name: sc1Name sc2's name: sc1Name true true
2. Java Object Access
**Handle access method: * * a piece of memory will be divided in the java heap as the handle pool. The reference stores the handle address of the object, and the handle contains the specific address information of the object instance data and type data.
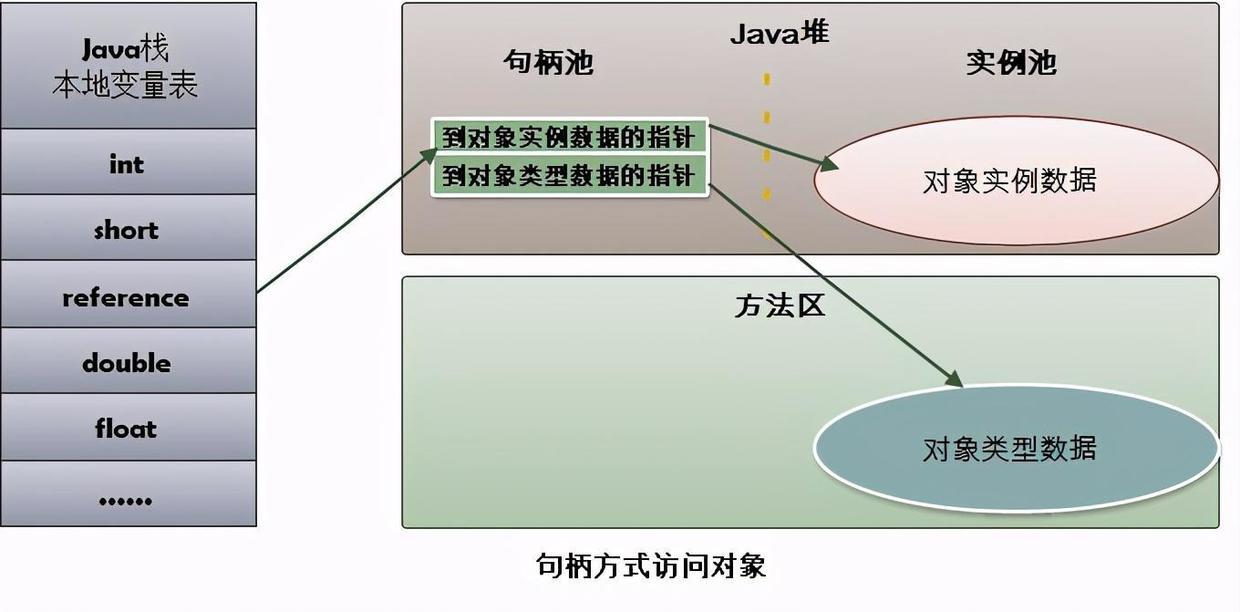
**Pointer access method: * * the address of the object is directly stored in the reference variable, and one part of the java heap object stores object instance data and the other part stores object type data.
[image upload failed... (image-68dcf6-1625474897121)]
These two methods of accessing objects have their own advantages. The biggest advantage of using handle access is that the reference stores a stable handle address. When the object moves, only the instance data pointer in the handle needs to be changed, while the reference does not need to be changed.
The biggest advantage of using pointer access is fast speed. It saves the time cost of pointer positioning. For virtual machines, it uses the second method (direct pointer access)
3. Ways to resolve Hash conflicts
Although we do not want conflict, the possibility of conflict still exists. When the keyword value field is much larger than the length of the hash table, and the specific value of the keyword is not known in advance. Conflict is inevitable.
In addition, when the actual value of the keyword is greater than the length of the hash table and the table is full of records, not only conflict but also overflow will occur if a new record is inserted. There are two common methods to deal with conflict and overflow
- Open addressing
- Zipper method
Don't start to talk about it specifically. You can't finish it in one or two sentences. If you are interested, you can find relevant information and blogs by yourself
4. Relationship between equals and hashcode
- If the two objects equals is true, the hashcode should also be the same
- If equals of the two objects is false, the hashcode should be different, otherwise the efficiency will be affected. The implication is that if equals is rewritten, it is recommended to rewrite hashcode
5. Why Innodb chooses B + tree
If I mention the characteristics of B + tree, it should be easy to understand
B + tree features:
- Each node of the B + tree can contain more nodes for two reasons. One is to reduce the height of the tree. The other is to change the data range into multiple intervals. The more intervals, the faster the data retrieval. The occupied space is very small, so the nodes of each layer can index a wider range of data. In other words, each IO operation can search for more data.
- Each node can store multiple keys instead of just one key.
- Non leaf nodes store keys, while leaf nodes store keys and data.
- The two pointers of leaf nodes are linked to each other, and the sequential query performance is higher. The leaf nodes are connected in pairs, which conforms to the read ahead characteristics of the disk.
6. Thinking problem: balance weighs a small ball, finds a heavy one in a pile of light ones, and summarizes the general formula
This question is also simple. You can get the answer quickly by three points
- Divide the ball into three parts at a time (if you can score equally, score equally).
- Put the same number of two parts on the balance. If the two parts are the same weight, the lighter ball must be in the third part. Next, carry out the same operation on the third part;
- Otherwise, perform the same operation on the lighter one.
So, y < = 3 ^ X
7. Scenario of topk problem
This should also be a common scene question in the interview. There are many online answer blogs. I won't repeat it here
8. Algorithm part:
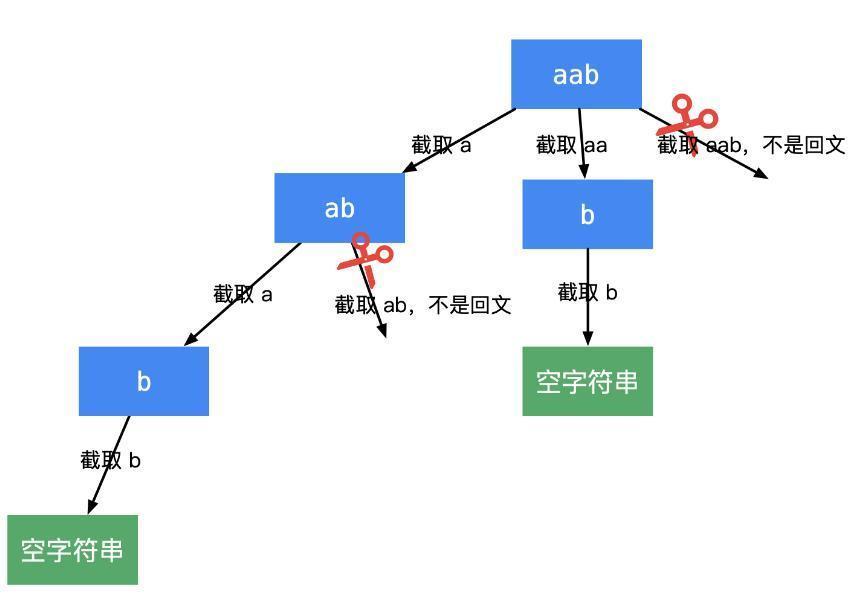
① Split palindrome string
This problem is also a classic one. I'll stick a picture here for you. It should be well understood
② Handwritten LRU
package algorithm.Interview;
import java.util.HashMap;
public class LRUCache {
private Node firstNode;
private Node lastNode;
private int initialCapacity;
private HashMap<String, Node> hashMap;
public LRUCache(int initialCapacity) {
if (initialCapacity <= 0) {
throw new IllegalArgumentException("initialCapacity must > 0");
}
this.initialCapacity = initialCapacity;
hashMap = new HashMap<>();
}
public String get(String key) {
Node node = hashMap.get(key);
if (node == null) {
return null;
}
//If the element is queried, move the element to the end of the linked list
removeNodeToTail(node);
return node.value;
}
public void put(String key, String value) {
Node node = hashMap.get(key);
if (node == null) {
//Larger than the memory capacity, the least commonly used node needs to be deleted
if (hashMap.size() >= initialCapacity) {
// Delete the least commonly used
String oldKey = removeNode(firstNode);
hashMap.remove(oldKey);
}
Node newNode = new Node(key, value);
addNode(newNode);
hashMap.put(key, newNode);
} else {
node.value = value;
//It is assigned again and moved to the end of the linked list
removeNodeToTail(node);
}
}
/**
* Move elements to the end of the linked list
* @param node
*/
private void removeNodeToTail(Node node) {
if (node == lastNode) {
return;
}
//Delete first
removeNode(node);
//Add to tail
addNode(node);
}
/**
* Tail interpolation, the more front the linked list elements, the older
* @param node
*/
private void addNode(Node node) {
if (lastNode != null) {
lastNode.next = node;
node.prev = lastNode;
}
//The tail node points to the newly inserted node
lastNode = node;
//If the linked list is empty, it is the first node at the same time
if (firstNode == null) {
firstNode = node;
}
node.next = null;
}
/**
* Removes the specified element and returns the key of the removed element
* @param node
* @return
*/
private String removeNode(Node node) {
if (node == lastNode) {
lastNode = lastNode.prev;//The tail node points to the precursor node of the original tail node
lastNode.next =null;
} else if (node == firstNode) {
firstNode = firstNode.next;//The first node points to the successor node of the original first node
firstNode.prev = null;
} else {
node.prev.next = node.next;//The successor node of the predecessor node of the current node points to the successor node of the current node
node.next.prev = node.prev;//The predecessor node of the successor node of the current node points to the predecessor node of the current node
}
return node.key;
}
private class Node {
Node prev; //Precursor node
Node next; //Successor node
String key;
String value;
Node(String key, String value) {
this.key = key;
this.value = value;
}
}
@Override
public String toString() {
StringBuilder ret = new StringBuilder();
Node p = firstNode;
while (p!=null){
ret.append("key:").append(p.key).append(",value:").append(p.value).append("; ");
p = p.next;
}
return ret.toString();
}
}
③ rand5()->rand7()
Algorithm code:
public static int random5() {
return (int) (1+Math.random()*5);
}
public static int random7() {
int a=random5();
int b=random5();
int rand=10*a+b;
if(rand<14) {
return 1;//11 12 13
}else if(rand<22) {
return 2;//14 15 21
}else if(rand<25) {
return 3;//22 23 24
}else if(rand<33) {
return 4;//25 31 32
}else if(rand<36) {
return 5;//33 34 35
}else if(rand<44) {
return 6;//41 42 43
}else if(rand<52) {
return 7;//44 45 51
} else
return random7();//52 53 54 55
}
Test code:
public static void main(String[] args) {
HashMap<Integer,Integer> map5=new HashMap<Integer,Integer>();
for(int i=0;i<10000000;i++) {
int key = random5();
if(map5.get(key)==null) {
map5.put(key, 1);
}else
map5.put(key, map5.get(key)+1);
}
System.out.println("random5:");
map5.entrySet().forEach(e->{
System.out.println(e+"\t"+1.0*e.getValue()/10000000);
});
System.out.println();
HashMap<Integer,Integer> map7=new HashMap<Integer,Integer>();
for(int i=0;i<10000000;i++) {
int key = random7();
if(map7.get(key)==null) {
map7.put(key, 1);
}else
map7.put(key, map7.get(key)+1);
}
System.out.println("random7:");
map7.entrySet().forEach(e->{
System.out.println(e+"\t"+1.0*e.getValue()/10000000);
});
}
Well, I'll write this article. In addition to the above questions, there are also some questions about TCP, thread pool and so on. After all, the interview makes rockets. Due to space constraints, I won't post them here.
But don't be disappointed. I've compiled all the questions into one book Real interview questions of Tencent Java post in 2021 PDF, and the latest interview questions will continue to be included later. You can get them by clicking directly
In addition to Tencent, I am also collecting and sorting out the real problems of other major manufacturers, which can be shared with you free of charge,
The students who need attention are concerned about the official account: Java, returning to the interview, and then getting all the interview materials I have arranged, as well as the massive learning materials of Java system.