Configure https authentication for Tomcat server (use keytool to generate certificate)
1, Certificate generation
1. Generate server certificate
(1) Open the command console and enter the bin directory of the jdk
(2)keytool generates a certificate for Tomcat ("- validity 36500" certificate validity, 36500 indicates 100 years, and the default value is 90 days)
keytool -genkey -v -alias tomcat -keyalg RSA -keystore C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\tomcat.keystore -validity 36500
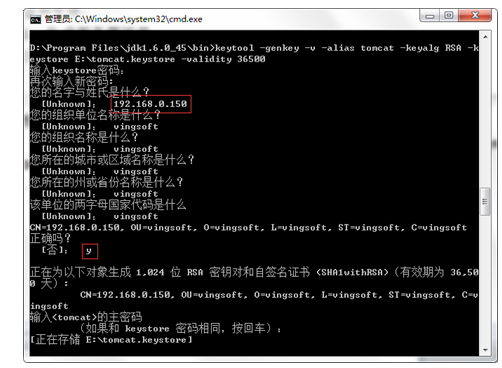
Note: first name and last name, unknown: the things filled in may be related to the domain name accessed during tomcat startup,
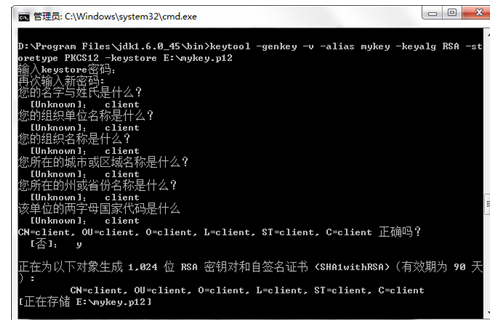
2. Generate client certificate
keytool -genkey -v -alias mykey -keyalg RSA -storetype PKCS12 -keystore C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\mykey.p12
3. Let the server trust the client certificate
(1) Since the certificate Library in PKCS12 format cannot be imported directly, you must first export the client certificate as a separate CER file, using the following command:
keytool -export -alias mykey -keystore C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\mykey.p12 -storetype PKCS12 -storepass 111111 -rfc -file C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\mykey.cer
(2) Import the file into the certificate Library of the server and add it as a trust certificate. The command is as follows:
keytool -import -v -file C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\mykey.cer –keystore C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\tomcat.keystore
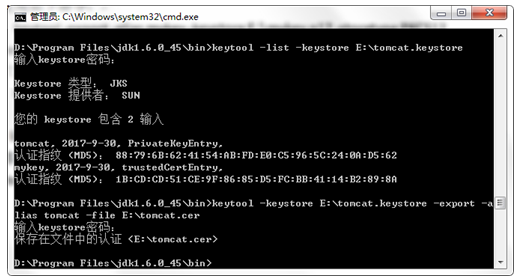
(3) View the server's certificate library through the list command. You can see two certificates, one is the server certificate and the other is the trusted client certificate:
keytool -list -keystore C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\tomcat.keystore
4. Let the client trust the server certificate
Export the server certificate as a separate CER file and provide it to the client. Use the following command:
keytool -keystore C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\tomcat.keystore -export -alias tomcat -file C:\MyFile\work_tools\apache-tomcat-8.5.55\apache-tomcat-8.5.55\tomcat.cer
5. After the above operations, the following certificates are generated:
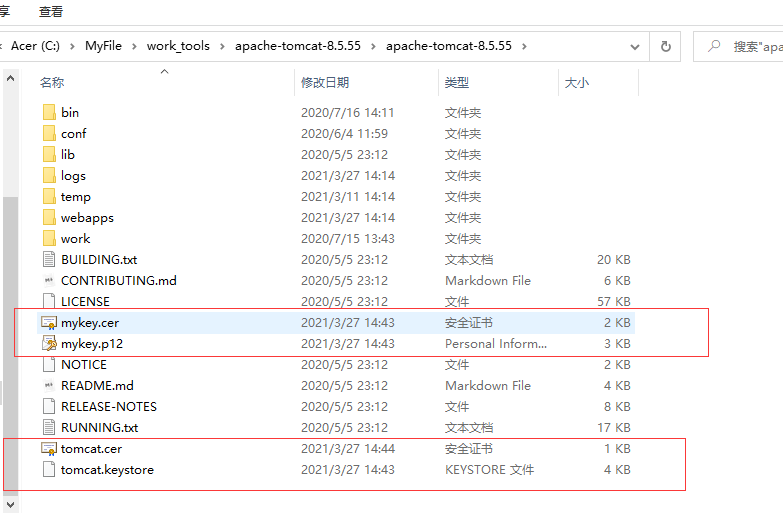
Including Tomcat CER is provided to the client, Tomcat Keystore is used by the server
2, Certificate use
1. Configuration of server tomcat
(1) Open / conf / server.com under the Tomcat root directory XML, find the Connector port="8443" configuration section and modify it as follows:
Comment out
(2) Test the server and enter the access address in IE browser
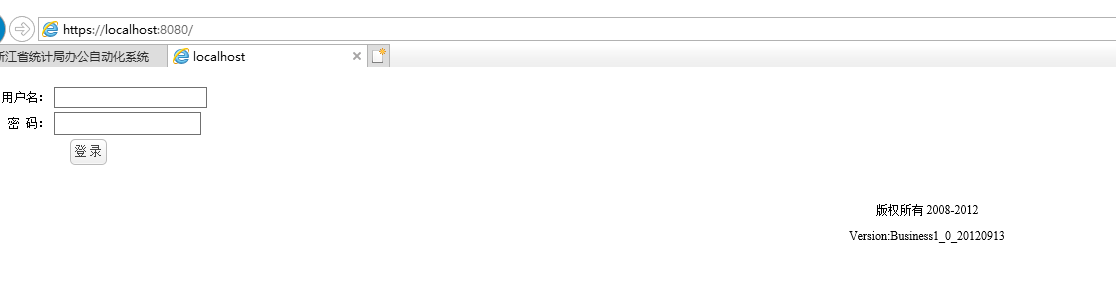
However, because it is a self signed certificate, the browser will warn us that it is unsafe and choose to continue:
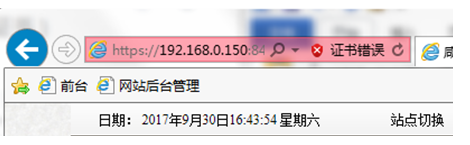
You can see that the access is successful (address bar "certificate error", at this time, the data has been transmitted using HTTPS)
2. Import server public key certificate (tomcat.cer)
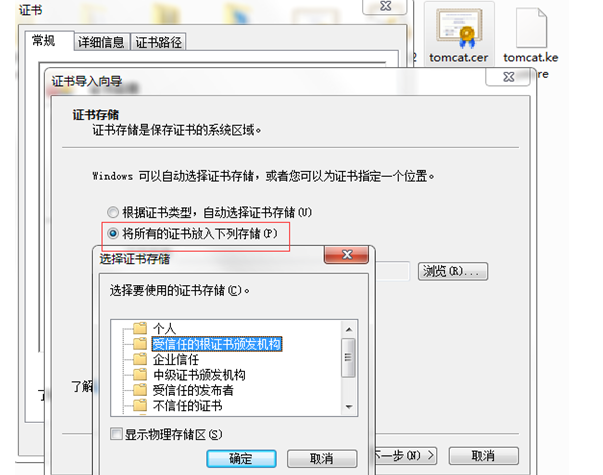
Since it is a self signed certificate, in order to avoid prompting unsafe every time. Here, double-click Tomcat CER installs the server certificate.
Note: fill in the certificate to the trusted root certification authority
If you visit the server again, you will find that there is no unsafe prompt, and there is also a "lock" icon on the browser address bar.
This completes the configuration.
Note: the signature generated by the jdk's built-in keytool belongs to the weak signature algorithm (SHA-1), but SHA-1 is outdated and is no longer recommended. The new certificate uses a stronger signature algorithm (such as SHA-256). SHA-1 certificate will no longer be regarded as safe by mainstream browser manufacturers from 2017.
Finally, use cmd to convert the signature file from * * [* * *. keystore] file to [* * *. p12] file, and then to [*. jks]:
First switch Lu Jin to the bin folder under jre, and then query through the command. The command is as follows:
keytool -importkeystore -srckeystore [absolute path + *. keystore] - srcstoretype JKS -deststoretype PKCS12 -destkeystore [*. p12]
keytool -v -importkeystore -srckeystore [absolute path + *. p12] - srcstoretype PKCS12 -destkeystore [absolute path + *. jks] - deststoretype JKS
p12 extract pem certificate and private key
openssl pkcs12 -in server.p12 -clcerts -nokeys -password pass:111111 -out server.crt openssl pkcs12 -in server.p12 -nocerts -password pass:111111 -passout pass:111111 -out server.key
penssl pkcs12 -in server.p12 -nocerts -password pass:111111 -passout pass:111111 -out server.key