First of all, the project was not successful when writing this article. It just summarized the research process and ideas.
A method based on hook and decryption
This is the idea I came up with without consulting any data. If I want to audit the chat content, I must first obtain the chat content. Then I can intercept the message sending and receiving of these instant messaging software to obtain the chat content, but the security personnel of these large factories must not give it in vain, and the intercepted information will be encrypted, The following is the contest between cryptography.
After a simple review, it is found that this road is different. qq has applied the anti hook technology seven or eight years ago, and even if the real hook arrives, it is not realistic to crack the password protection set up by their security team by themselves.
II. Cracking of local database
There are some materials on the Internet,
Wechat reverse
qq reverse
Nail research
It can be said that it basically includes all the current mainstream communication software. Generally, the idea can not escape through the dynamic debugging of ollydbg. After entering the function with db file as parameter, check whether the relevant string is the database password, and then write code to decrypt the database according to the password, but the password is generated dynamically. If it changes, you need to find it again next time, The password changes, but the base address of the stored password will not change, so you can use CE to locate the address of the currently found password for dynamic acquisition, so as to ensure the long-term availability of the password.
Some tests have been carried out, which can be used for reference. It is still reliable, but it is not completely reliable. It may be that a completely direct and feasible scheme has not been found for the time being because of a little time or other problems.
However, if this scheme is successful, it will be the most complete way to obtain chat content.
Three screenshots OCR
It is to extract the text from the screenshots and then the captured pictures. This method can be said to be the most stupid, inefficient and troublesome for the time being, but it is the most feasible. The first two have great technical problems. If you study them by yourself, it seems that you are afraid of the whole Tencent / Ali security team by yourself.
The scheme captures information through uninterrupted screenshots, and then extracts the text through the existing ocr software. If it is improved later, the extracted text can be processed, such as de duplication.
But no matter how stupid you are, you can't take a screenshot of the screen no matter what the user is doing. At this moment, the computer hard disk space is not enough. Who can't see it? It's best to take a screenshot when and only when the user uses communication software. This operation can be realized through some windows API s to detect the process currently used by the user. If it is qq, wechat or nailing, capture the window size, screenshot and report an error. The example code is as follows:
#You need to install pypiwin32 library and pilot pillow library PIP install pypiwin32 / pilot
import win32gui as w
import win32process,logging
import wmi,uuid,os,filecmp
import time
from PIL import ImageGrab
import ctypes
from ctypes.wintypes import *
#import mypyutils
g_allNeedCaptureSoft = ';QQ.EXE;DINGTALK.EXE;WECHAT.EXE;'
c = wmi.WMI()
def get_window_rect(hwnd):#Get window size
try:
f = ctypes.windll.dwmapi.DwmGetWindowAttribute
except WindowsError:
f = None
if f:
rect = ctypes.wintypes.RECT()
DWMWA_EXTENDED_FRAME_BOUNDS = 9
f(ctypes.wintypes.HWND(hwnd),
ctypes.wintypes.DWORD(DWMWA_EXTENDED_FRAME_BOUNDS),
ctypes.byref(rect),
ctypes.sizeof(rect)
)
return rect.left, rect.top, rect.right, rect.bottom
def get_app_path(hwnd):
try:
_, pid = win32process.GetWindowThreadProcessId(hwnd)
for p in c.query('SELECT ExecutablePath FROM Win32_Process WHERE ProcessId = %s' % str(pid)):
exe = p.ExecutablePath
break
except:
return None
else:
return exe
def get_app_name(hwnd):
exe = None;
try:
_, pid = win32process.GetWindowThreadProcessId(hwnd)
for p in c.query('SELECT Name FROM Win32_Process WHERE ProcessId = %s' % str(pid)):
exe = p.Name
break
except:
return None
else:
return exe
if __name__ == "__main__":
#mypyutils.initLog('capturewindows.log')
lastJpgName = None;
lastTitle = None;
while True:
try:
activeWnd = w.GetForegroundWindow();
appName = get_app_name(activeWnd)
if appName is None:
print('Unable to get the active window process name...');
time.sleep(0.1);
continue;
else:
print('The window process name is%s'%appName);
appName = str.upper(appName)
if g_allNeedCaptureSoft.__contains__(appName) is False:#If the window application is not communication software, continue
time.sleep(1);
continue;
title = w.GetWindowText (activeWnd)
wndRect = get_window_rect(activeWnd);#Gets the current window size
title ='----window title = %s,rect=%d,%d,%d,%d -----'%(title,wndRect[0],wndRect[1],wndRect[2],wndRect[3]);
print("title:",title)
if lastTitle is not None and str(title).__eq__(lastTitle) is False:#What's this for?
print(title)
lastTitle = title
#newWndRect = ( wndRect[0]+10, wndRect[1]+10, wndRect[2]-10,wndRect[3]-10);
fileName = appName + '-'+ time.strftime("%H-%M-%S", time.localtime()) + str(uuid.uuid4().__str__())[5:10] +'.png'
img=ImageGrab.grab(wndRect)
img.save(fileName, "PNG")
print("Saved successfully")
if lastJpgName is None:
lastJpgName = fileName
continue
lastPngMd5 = mypyutils.get_file_md5(lastJpgName);
newPngMd5 = mypyutils.get_file_md5(fileName);
logging.info(f'last file ={lastJpgName},md5={lastPngMd5},new file = {fileName},md5={newPngMd5}');
if lastPngMd5.__eq__(newPngMd5):
os.remove(lastJpgName);
logging.info(f'{lastJpgName},{fileName},The two pictures are the same. They don't need to be stored and have been deleted{lastJpgName}file')
lastJpgName = fileName;
except Exception as e:
lastJpgName = None;
logging.error('Exception occurred during loop processing, but continue processing.....');
logging.exception(e);
time.sleep(1)
PS: for form size, you can actually use win32gui Getwindowrect() api directly obtains the position and size of the window, but in actual operation, it is found that the acquisition effect is not ideal. The size is too small and the position is too left. Some articles say that it is because the system after vista comes with frosted glass effect, which is not calculated in the api, but now Win10 has frosted glass effect, which is not very clear, but get_window_rec function is really useful, so we don't have to worry about these details.
Text extraction and image recognition is popular because of artificial intelligence. If you identify in batches in Baidu search days, you can find resources to download. The software can generate one or more word documents containing image text.
At this point, you can get all the chat content of the communication software. The accuracy of the chat content depends on the third-party image recognition software, and the specific audit depends on manual work. At present, it can only be counted and cannot be reviewed, and the generated pictures should be uploaded to a special server and the cleaning traces should be deleted, which is not done. However, as a demo that simply realizes the acquisition of communication content, it still meets the minimum requirements.
Four tools
At present, ping 32, a mature commercial product for communication content audit, has strong functions. It can instantly obtain qq, wechat and nailing chat records, including time, expression, etc., alarm according to sensitive words, analyze the user's computer usage, even including file operation and pasteboard content, and shut down and restart the computer at the same time, Lock the mouse, keyboard and other operations. It can be said that the computer with the client has no secrets at all, and completely exposes its every move to the server. Some functions and interfaces are shown as follows:
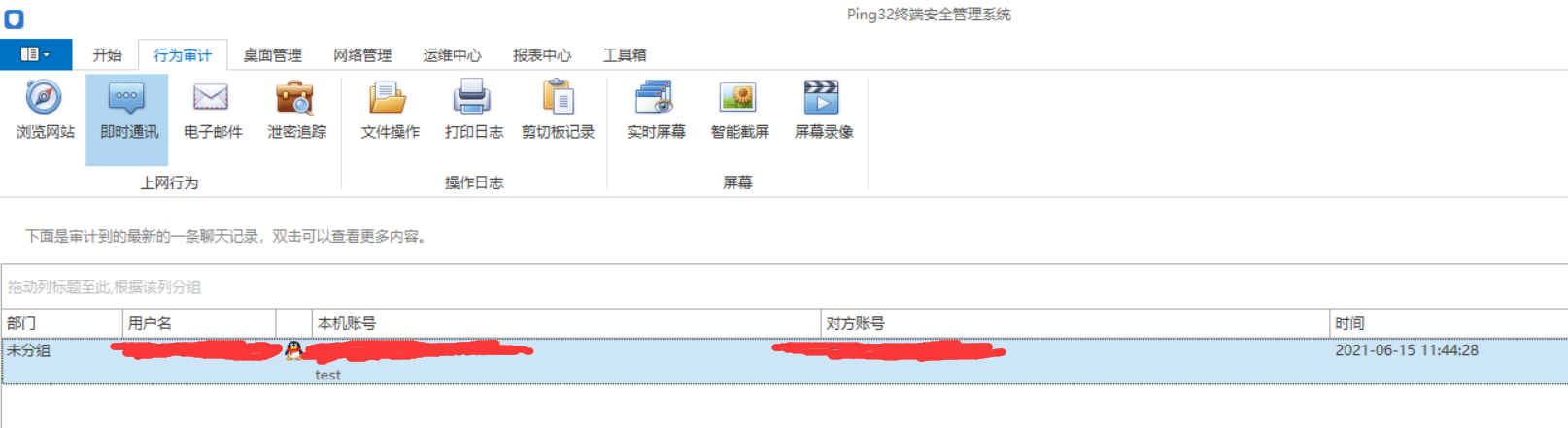
It should be noted that the client of the trial version does not provide an uninstall interface. At present, it has been searched in all directions such as application, background process and service, but it is not found. The original intention is to prevent malicious uninstall, but is the trial version a little rogue. And the software monitors too many projects, which really makes people feel like running naked. Anyway, I won't work for the company that installs this system for me.