1. Environmental preparation
- 1 Alibaba cloud server
- centos7.9
- docker latest version
2. Installation steps of docker
Set up warehouse
- Install the required packages. Yum utils provides Yum config manager, and the device mapper storage driver requires device mapper persistent data and lvm2.
sudo yum install -y yum-utils device-mapper-persistent-data lvm2
- Set alicloud source
sudo yum-config-manager \
--add-repo \
http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repoInstall the latest version of docker engine community and containerd
sudo yum install docker-ce docker-ce-cli containerd.io
Start Docker
sudo systemctl start docker
Configure Docker image acceleration
curl -sSL https://get.daocloud.io/daotools/set_mirror.sh | sh -s http://f1361db2.m.daocloud.io
Restart Docker
sudo systemctl daemon-reload sudo systemctl restart docker
3. Configure certificate
Create a directory for storing certificates
mkdir -p /usr/local/ca cd /usr/local/ca
Create a one click certificate generation script
vi ca.sh
Press key A to switch to input mode, and then paste the following code
#!/bin/bash SERVER="Server extranet ip" PASSWORD="yinfeng" COUNTRY="CN" STATE="shanghai" CITY="shanghai" ORGANIZATION="yinfeng" ORGANIZATIONAL_UNIT="dev" EMAIL="yinfeng@qq.com" echo "starting..." cd /usr/local/ca openssl genrsa -aes256 -passout pass:$PASSWORD -out ca-key.pem 4096 openssl req -new -x509 -passin "pass:$PASSWORD" -days 3650 -key ca-key.pem -sha256 -out ca.pem -subj "/C=$COUNTRY/ST=$STATE/L=$CITY/O=$ORGANIZATION/OU=$ORGANIZATIONAL_UNIT/CN=$SERVER/emailAddress=$EMAIL" openssl genrsa -out server-key.pem 4096 openssl req -subj "/CN=$SERVER" -new -key server-key.pem -out server.csr sh -c 'echo "subjectAltName = IP:'$SERVER',IP:0.0.0.0" >> extfile.cnf' sh -c 'echo "extendedKeyUsage = serverAuth" >> extfile.cn' sh -c 'echo "extendedKeyUsage = serverAuth" >> extfile.cnf' openssl x509 -req -days 3650 -in server.csr -CA ca.pem -CAkey ca-key.pem -passin "pass:$PASSWORD" -CAcreateserial -out server-cert.pem -extfile extfile.cnf openssl genrsa -out key.pem 4096 openssl req -subj "/CN=client" -new -key key.pem -out client.csr sh -c 'echo extendedKeyUsage=clientAuth >> extfile-client.cnf' openssl x509 -req -days 3650 -sha256 -in client.csr -CA ca.pem -CAkey ca-key.pem -passin "pass:$PASSWORD" -CAcreateserial -out cert.pem -extfile extfile-client.cnf rm client.csr server.csr cp server-*.pem /etc/docker/ cp ca.pem /etc/docker/ echo "========end========"
Execute after saving the script
sh ca.sh
After execution, the following files will be generated. After searching for a long time, I summarized the only available script in the whole network. Hey hey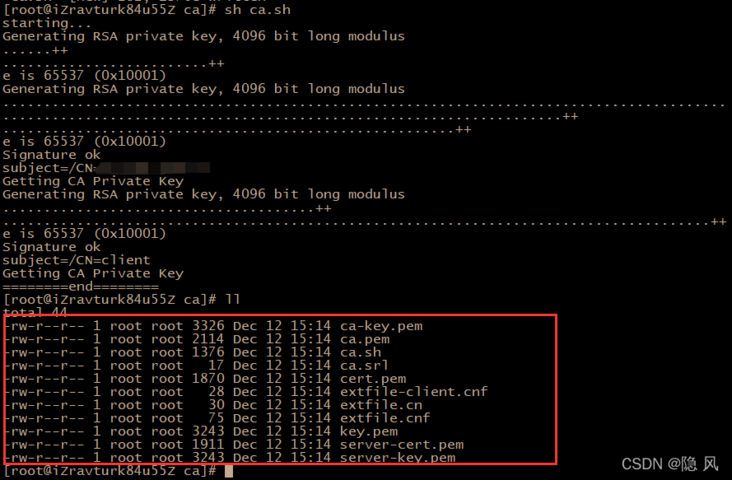
Modify Docker configuration
- Make the Docker daemon only receive links from clients that provide CA trusted certificates
vim /lib/systemd/system/docker.service
- Replace the ExecStart property value
ExecStart=/usr/bin/dockerd --tlsverify --tlscacert=/usr/local/ca/ca.pem --tlscert=/usr/local/ca/server-cert.pem --tlskey=/usr/local/ca/server-key.pem -H tcp://0.0.0.0:2375 -H unix:///var/run/docker.sock
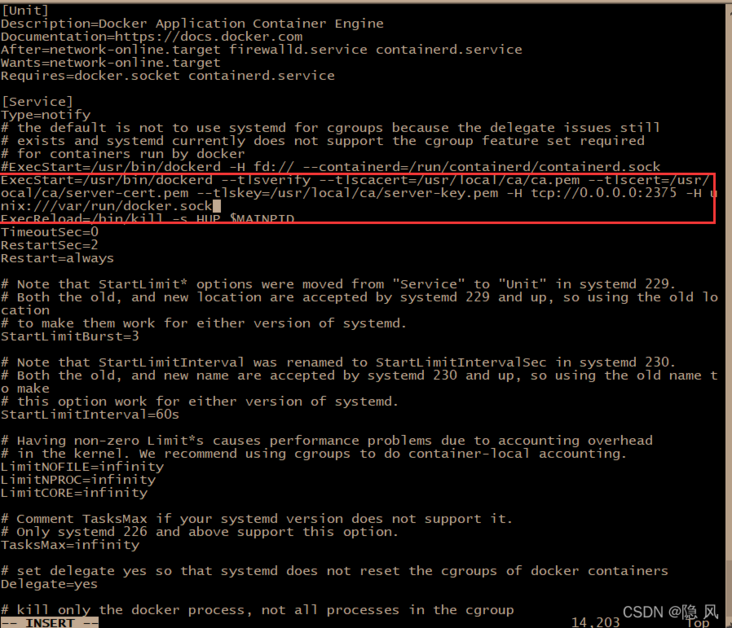
Reload the service and restart docker
systemctl daemon-reload && systemctl restart docker
Save the certificate client file locally
I use sz. If not, I need to install it first
yum -y install lrzsz
Execute after successful installation
sz ca.pem cert.pem key.pem
I save them directly on the desktop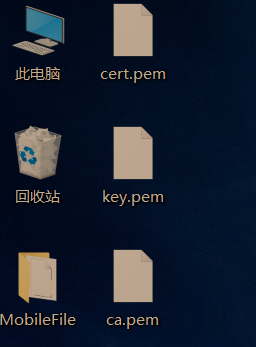
Test whether the certificate is successfully configured. If it is successful, the certificate related information will be output. If it fail s, please check the certificate generation process
docker --tlsverify --tlscacert=ca.pem --tlscert=cert.pem --tlskey=key.pem -H=Server extranet ip:2375 version

Finally, test it on idea
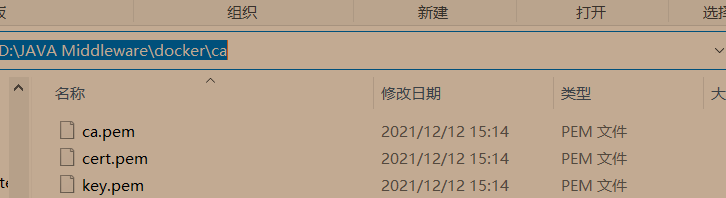
- Move the certificate just downloaded to the certificate directory of our computer
- Before linking, you need to open alicloud's 2375 port, otherwise it will be blocked by alicloud

- Through the docker plug-in of idea, you can see that the link has been successful

- Let's test whether the previous link through tcp can be successful

4. Summary
Finally, to sum up, when configuring docker extranet links, you must take good encryption measures, otherwise it is easy to hang up. At present, the online steps are generally tcp secret free links, which is very unsafe. I tried yesterday and was scanned and hung up in less than half an hour. Therefore, I decided to write a note to record my deployment process. I hope you can learn from it.
This is the alarm information of Alibaba cloud
I'll write another one later when I have time Deploy springboot to docker container with idea one click encryption The liver is not easy, please let the old fellow thank you for your support.