3. Control node Keystone authentication service component
More steps: OpenStack Victoria installation and deployment series tutorials
OpenStack deployment series
Openstack deployment tutorial series
OpenStack Ussuri offline installation and deployment series tutorial (full)
OpenStack Train offline installation and deployment series tutorial (full)
Welcome to leave messages for communication and common progress.
Create keystone database and authorize
1. Log in to the database
Use the root account of mysql database to log in, and the password is the password for initializing mysql data when preparing the control node environment. The password set is root.
mysql -u root -proot
2. Create keystone database and authorize
Create a keystone database, set the password to 111111, grant access to the keystone database, refresh and exit the database
CREATE DATABASE keystone; GRANT ALL PRIVILEGES ON keystone.* TO 'keystone'@'localhost' \ IDENTIFIED BY '111111'; GRANT ALL PRIVILEGES ON keystone.* TO 'keystone'@'%' \ IDENTIFIED BY '111111'; flush privileges; show databases; select user,host from mysql.user; exit
keystone related software installation and configuration
1. Install keystone related software packages
If you want to access using https, you need to install mod_ssl
Install and configure Keystone: For RHEL8/Centos8 and above install package python3-mod_wsgi.
dnf install openstack-keystone httpd python3-mod_wsgi -y
2. Modify / etc / keystone / keystone Conf file
Since there are about 2700 lines of file content and too many comments, the actual effective configuration information is only about 40 lines. In order to facilitate the modification of the file, you can back up the file first and then remove the comment information
cp /etc/keystone/keystone.conf /etc/keystone/keystone.conf.bak egrep -v "^$|^#" /etc/keystone/keystone.conf.bak >/etc/keystone/keystone.conf
vim /etc/keystone/keystone.conf
In order to improve the efficiency of modifying files and reduce the rate of configuration errors, we can use the configuration tool to modify files through commands and install software first
dnf install crudini -y
crudini --set /etc/keystone/keystone.conf database connection mysql+pymysql://keystone:111111@controller/keystone crudini --set /etc/keystone/keystone.conf token provider fernet
Check configuration results
grep '^[a-z]' /etc/keystone/keystone.conf
keystone does not need to be started and is called through the http service
3. Initialize and synchronize keystone database
su -s /bin/sh -c "keystone-manage db_sync" keystone
After synchronization, conduct connection test
mysql -ukeystone -p111111 -e "use keystone;show tables;" mysql -h10.0.0.11 -ukeystone -p111111 -e "use keystone;show tables;"|wc -l
4. Initialize the Fernet token library
Initialize Fernet key repositories,Introduction to Fernet tokens Keystone Fernet tokens
keystone-manage fernet_setup --keystone-user keystone --keystone-group keystone keystone-manage credential_setup --keystone-user keystone --keystone-group keystone
5. Initialize the bootstrap keystone authentication service
keystone-manage bootstrap --bootstrap-password 111111 --bootstrap-admin-url http://controller:5000/v3/ --bootstrap-internal-url http://controller:5000/v3/ --bootstrap-public-url http://controller:5000/v3/ --bootstrap-region-id RegionOne
6. Configure and start Apache Http service
Edit VIM / etc / httpd / conf / httpd Conf file, add the following information
cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf.bak sed -i "s/#ServerName www.example.com:80/ServerName controller/" /etc/httpd/conf/httpd.conf
Create / keystone / keystone Conf file link
ln -s /usr/share/keystone/wsgi-keystone.conf /etc/httpd/conf.d/
Start httpd and configure boot self boot
systemctl start httpd && systemctl enable httpd netstat -anptl|grep httpd systemctl list-unit-files |grep httpd.service
So far, the http service configuration is completed.
7. Create environment variable script
#touch admin-openrc.sh #vim admin-openrc.sh
Create OpenStack client environment scripts, which uses a combination of environment variables and command options to interact with the identity authentication service through the "openstack" client.
In order to improve the efficiency of client operation, OpenStack supports simple client environment variable scripts, namely OpenRC files
cat > /root/admin-openrc.sh <<EOF export OS_PROJECT_DOMAIN_NAME=Default export OS_USER_DOMAIN_NAME=Default export OS_PROJECT_NAME=admin export OS_USERNAME=admin export OS_PASSWORD=111111 export OS_AUTH_URL=http://controller:5000/v3 export OS_IDENTITY_API_VERSION=3 export OS_IMAGE_API_VERSION=2 EOF
Attachment: common openstack management commands need to apply the administrator's environment variables
# View keystone instance related information openstack endpoint list openstack project list openstack user list # Delete endpoint openstack endpoint delete [ID]
8. Create a general instance of keystone
source ./admin-openrc.sh openstack catalog list
(1) [not required] create a field named example
Create a domain. The default domain already exists in the program. This command is only an example of creating a domain. You can not execute it
#openstack domain create --description "An Example Domain" example
(2) [required] create a project named service, also known as tenant, in the default field.
openstack project create --domain default --description "Service Project" service
(3) [not required] create a project named myproject in the default field.
#openstack project create --domain default --description "Demo Project" myproject
(4) [not required] create a myuser user in the default field.
The following commands are displayed in local_ Add myuser user to the user table. Use the – password option to directly configure the plaintext password, and use the – password prompt option to enter the password interactively to directly create the user and password
#openstack user create --domain default --password-prompt myuser # After executing the command, you need to set the user password and enter the same password twice
(5) [not required] create a myrole in the role table.
# openstack role create myrole
(6) * * [not required] * * add myrole role to myproject project and myuser user
#openstack role add --project myproject --user myuser myrole
(7) View keystone instance related information
source admin-openrc.sh openstack role list openstack endpoint list openstack project list openstack user list
Verify whether keystone installation configuration is successful
Verify whether KeyStone service is normal
openstack token issue
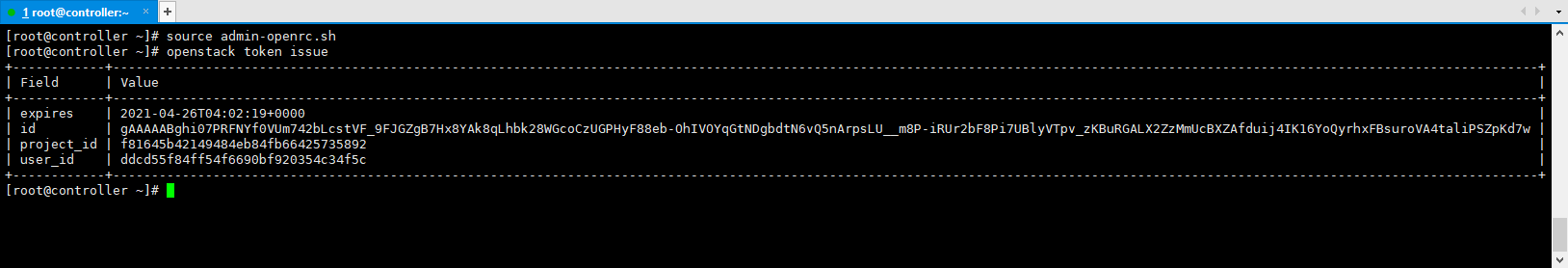
The above information indicates that KeyStone configuration is completed!
1. Remove environmental variables
Close the temporary authentication token mechanism, obtain the token, and verify that the keystone configuration is successful
source admin-openrc.sh unset OS_AUTH_URL OS_PASSWORD env |grep OS_
2. As an administrator, the user requests an authenticated token
Test whether the admin account can be used for login authentication and request authentication token
openstack --os-auth-url http://controller:5000/v3 --os-project-domain-name Default --os-user-domain-name Default --os-project-name admin --os-username admin token issue
#Enter password: 111111
keystone installed
So far, the keystone authentication service component of the control node has been installed and configured. If you use VMware virtual machine, you can now shut down and take a snapshot.
poweroff