- "hidden dangers are more dangerous than open fire, prevention is better than disaster relief, and the responsibility is heavier than Mount Tai"
preface
This paper introduces the security test process of sending SMS verification code interface in detail, including ideas, some test codes and test results.
This test website - Xiaomi (xiaomi.com)
Xiaomi is an Internet company with mobile phones, smart hardware and IoT platform as the core, with rich products and services such as smart phones, smart TVs and notebooks.

I. find the external SMS interface
It can be found from the registration portal of the website that the registration is also completed by sending SMS verification code.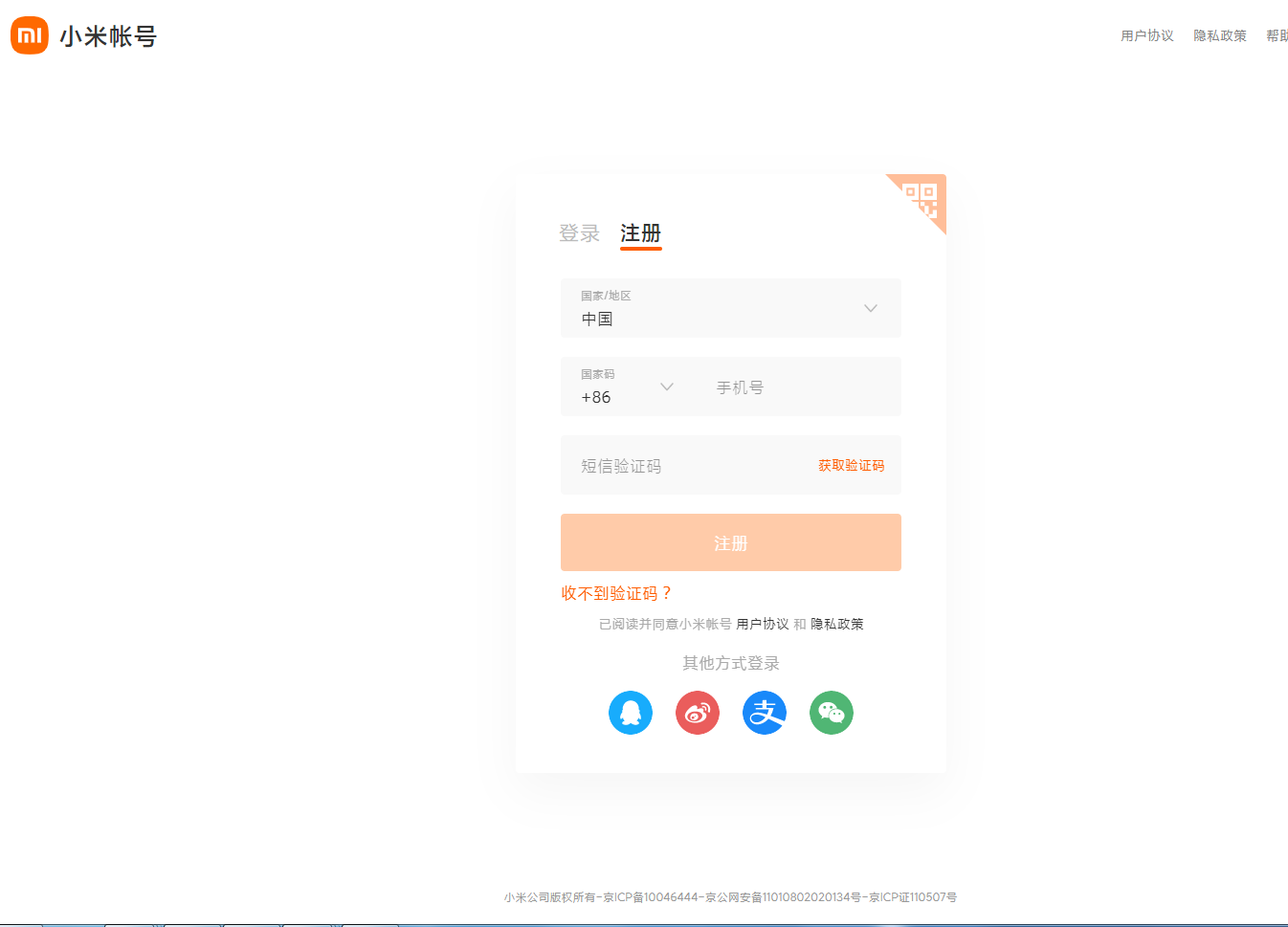
II. Analyze external defense measures
- Enter the phone number and click to get the verification code
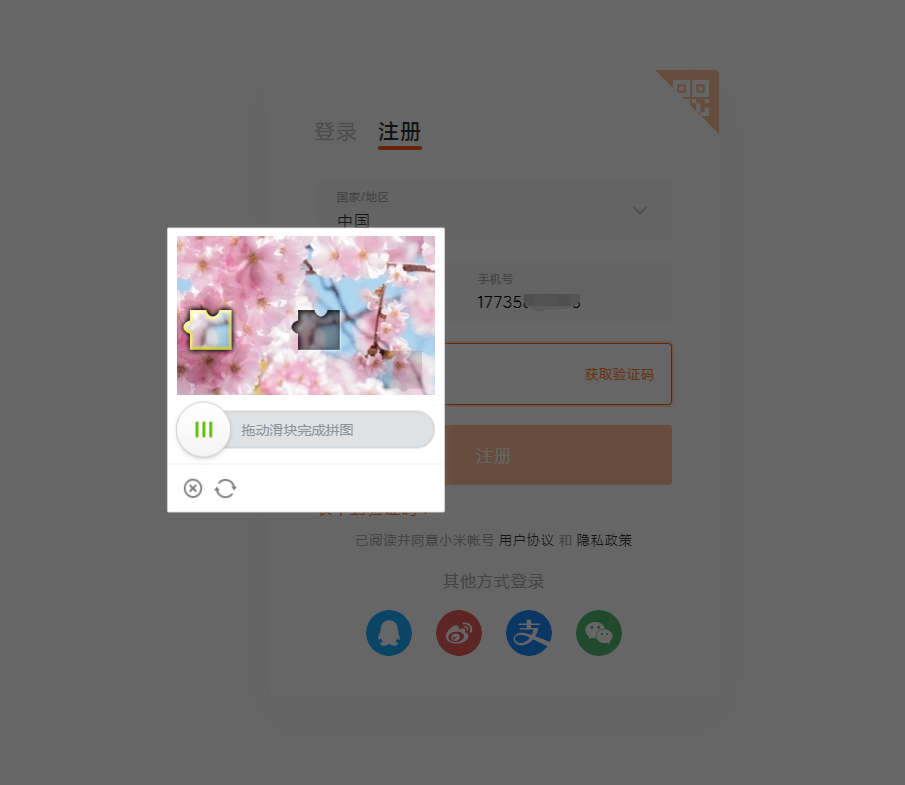
Here, you need to drag the slider to complete the Slide Puzzle verification code before sending it
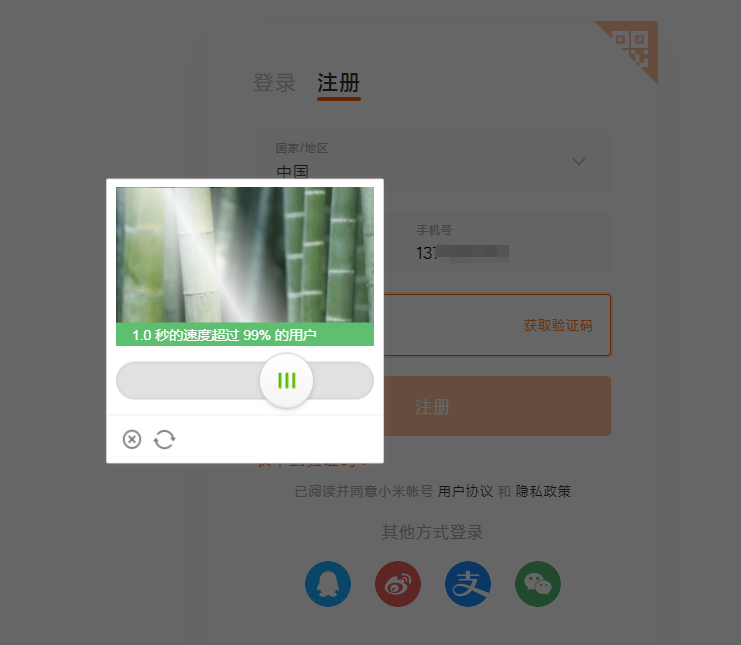
External defense measures: sliding verification code
III. analysis and test
1. Analysis and test points
- Simulate human operation through simulator
- Identification sliding verification code
2. Write code to simulate operation for test
The sliding verification code of the website is polar sliding verification code:
Recognition method: image recognition algorithm to find the shadow position.
General idea:
- The image is processed by noise reduction and binarization
- Find the shadow position through the template matching algorithm.
There is no additional complaint here. If you are interested, you can see the following articles on verification code identification:
Polar sliding puzzle verification code
Then test. Some codes are as follows:
// Enter mobile number
By phoneBy = By.name("phone");
GeetSplitApi.waitForLoad(driver, phoneBy);
WebElement phoneElemet = driver.findElement(phoneBy);
phoneElemet.clear();
for (int i = 0; i < phone.length(); i++) {
char c = phone.charAt(i);
phoneElemet.sendKeys(c + "");
phoneElemet.click();
}
Thread.sleep(1 * 1000);
// Click send
By clickBy = By.className("ant-btn-link");
GeetSplitApi.waitForLoad(driver, clickBy);
WebElement clickElemet = driver.findElement(clickBy);
clickElemet.click();
Thread.sleep(3 * 1000);
// The following js code comes from the canvas document
// Complete background image geetest_canvas_fullbg geetest_fade geetest_absolute
String fullImgJs = "return document.getElementsByClassName(\"geetest_canvas_fullbg geetest_fade geetest_absolute\")[0].toDataURL(\"image/png\");";
String fullImgPath = GeetCanvasApi.getImgByJs(driver, fullImgJs, input);
// Background image with gap geetest_canvas_bg geetest_absolute
String bgImgJs = "return document.getElementsByClassName(\"geetest_canvas_bg geetest_absolute\")[0].toDataURL(\"image/png\");";
String bgImgPath = GeetCanvasApi.getImgByJs(driver, bgImgJs, input);
// Get slide button
By moveBy = By.className("geetest_slider_button");
GeetSplitApi.waitForLoad(driver, moveBy);
WebElement moveElemet = driver.findElement(moveBy);
Start test:

V. result analysis
Test objectives:
Conduct security test on the interface for sending SMS verification code.
Test idea:
1. Find the request interface
2. Analysis of defense mechanism
3. Test method
Test results:
adopt
Test conclusion:
The foreground is limited by sliding verification code, and the background mobile phone number and IP have no frequency limit or frequency limit. When encountering a large number of mobile phone numbers and IP attacks, all defense measures of the website are invalid.
Risk level: medium high
Vi. conclusion
Many people may not think too much about security at the beginning of the construction of SMS service. There are many reasons.
For example: "the demand is so urgent, of course, the function is realized first", "the business volume is very small, and the system is not afraid of being used by so many people", "how can we be targeted? It's impossible" and so on.
There are some reasons, although reasonable, but what should come will always come. The debts owed in the early stage must always be paid off. The earlier you return it, the smaller the problem and the lower the loss.
Therefore, we should pay attention to safety. (bloody chestnuts!) #Secure SMS#
Poke here → Kangkang, how many websites have you registered your mobile phone number!!!
Google's graphics verification code has been in vain in front of AI, so Google announced to withdraw from the verification code service. Then, when all graphics verification codes are cracked, how should we do a good job in defense?
>>Related reading
Tencent waterproof wall sliding puzzle verification code
Baidu rotating picture verification code
Netease shield Slide Puzzle verification code
Verification code for point selection of top image area
Top image sliding puzzle verification code
Polar sliding puzzle verification code
Using deep learning to crack captcha verification code
Verification code Terminator - training deployment kit based on CNN+BLSTM+CTC