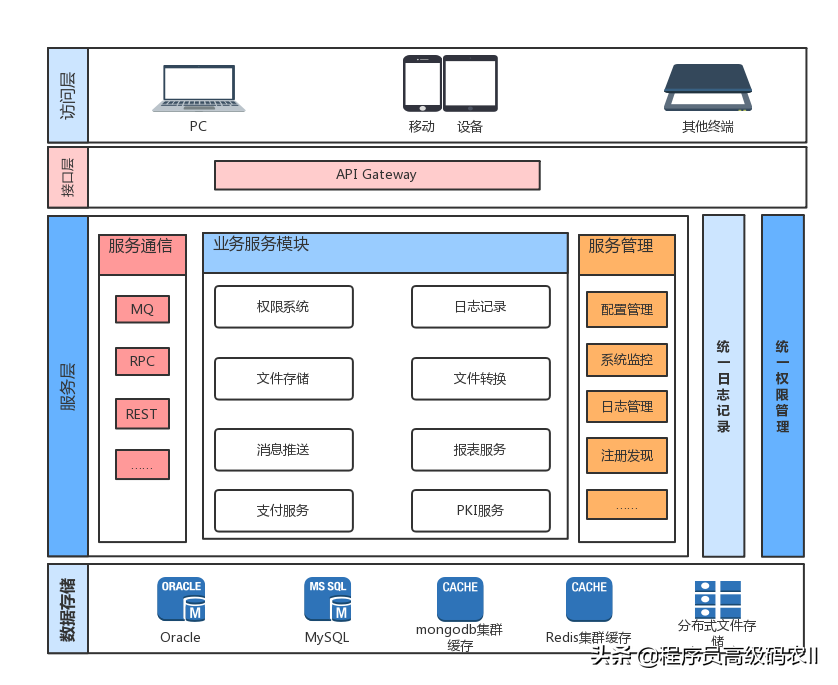
Access control design of platform management background
The access control design here is implemented by spring security, which is not much different from the implementation method of the access control part in Chapter 10 SSO design. The difference is that OAuth 2 is not required here, and a simpler method is used for the design of permission management. Some of the same points will be omitted below, and only the different points will be explained. These designs are implemented in the module manage web.
Using operators in access control
Create a MyUserDetails class to implement the UserDetails of spring security, so as to import the Operators user and its permission management. The code is as follows:
public class MyUserDetails implements UserDetails {
private String username;
private String password;
private Collection<? extends GrantedAuthority> authorities;
private Operators operators;
public MyUserDetails(String username,String password, collection<? extendsGrantedAuthority>authorities,Operators operators) {
this.username = username;
this.password = password;
this.authorities =authorities;this.operators = operators;
this.operators.setPassword(null);
)
...
}Create a MyUserDetailsService service class and reference it in the configuration class SecurityConfiguration. In this way, spring security can use our defined users and their permissions for secure access control authentication. The specific implementation details can refer to the SSO design mentioned above.
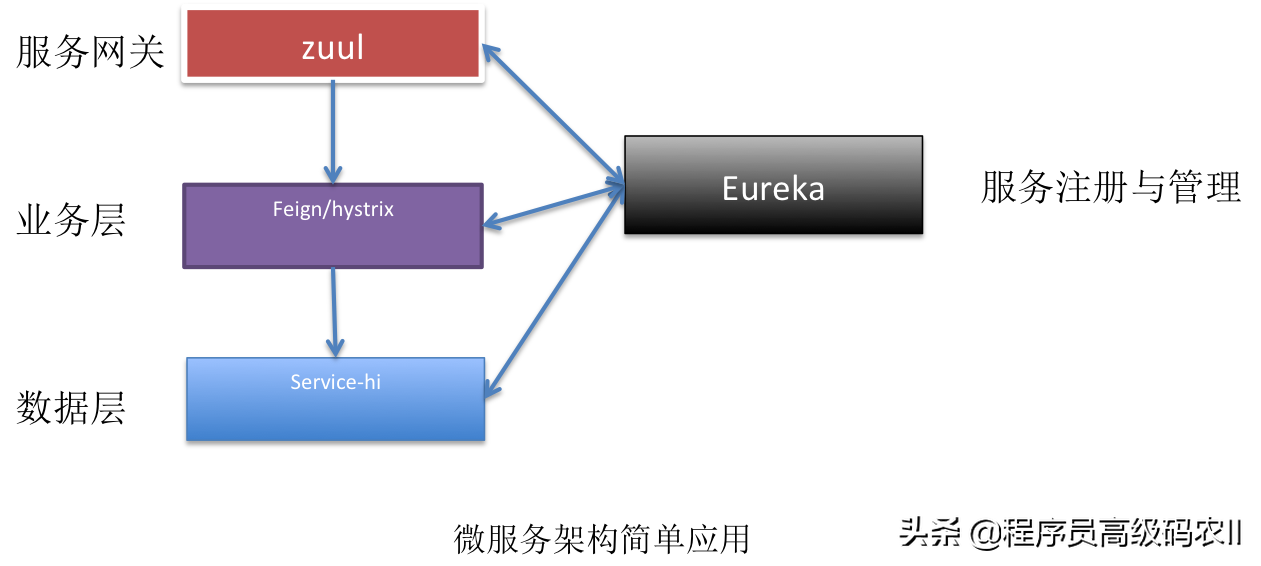
Authority management design of platform management background
The permission management here uses a relatively simple method, that is, the permission management is realized by using configuration parameters. The implementation method is as follows.
First, add the following configuration items to the application configuration of the module:
securityconfig: logoutsuccssurl:/ permitall:-/druid/*★- /bbs** deniedpage:/deny urlroles:/**/new/** =admins; /★*/edit/**=admins, editors;/**/delete/** =admins
These configuration parameters are implemented by a custom configuration class SecuritySettings.
Where urlroles is the configuration parameter of permission management. This configuration parameter sets the user's access rights through the requested URL. Here, only two roles (or user groups) are set, namely admins and editors. In URL resource configuration, combined with the wildcard "*", the keywords new, edit and delete are used to represent new, edit and delete operations respectively.
In the design of the controller, you also need to use these keywords to set the URL, such as some @ RequestMapping designs shown below:
@RequestMapping( "/new")
CRequestMapping(value="/edit/{id] ")
@RequestMapping(value="/update",method = RequestMethod.POST)@RequestMapping(value=" /delete/{id} ")Secondly, metadata management in security resource management
In CustomSecurityMetadataSource, the following design is used:
public CustomsecurityMetadataSource (String urlroles){
super();
this.urlroles =urlroles;
resourceMap = loadResourceMatchAuthority();
private Map<String, Collection<ConfigAttribute>>loadResourceMatchAuthority({
Map<String, Collection<ConfigAttribute>>map = new HashMap<String,
Collection<ConfigAttribute>>(0);
if (urlroles !=null && !urlroles.isEmpty()){
String[] resouces = urlroles.split(";");for(String resource : resouces){
String[]urls = resource.split("=");String[roles = urls[1].split(",");Collection<ConfigAttribute> list = new
ArrayList<ConfigAttribute>();
for(String role :roles){
ConfigAttribute config =new SecurityConfig (role.trim());list.add (config);
//key: url,value: roles
map.put(urls[0].trim(), list);
}else{
logger.error("'securityconfig.urlroles' must be set");
}
logger.info ( "Loaded UrlRoles Resources. ");return map;
}This design indicates that when the system starts, the data of the above permission configuration will be imported as the metadata of security management to provide a basis for subsequent permission inspection.
Finally, in the permission check
In the design of CustomAccessDecisionManager, the following design is used:
public class CustomAccessDecisionManager implements AccessDecisionManager
{
protected Log log = LogFactory.getLog (getClass());
@override
public void decide (Authentication authentication, 0bject object,
Collection<configAttribute>configAttributes)
throws AccessDeniedException,InsufficientAuthenticationException tif(configAttributes == null) {
return;
}
//config urlroles
Iterator<ConfigAttribute>iterator = configAttributes.iterator();
while (iterator.hasNext()){
ConfigAttribute configAttribute = iterator.next();//need role
String needRole = configAttribute.getAttribute();//user roles
for (GrantedAuthority ga : authentication.getAuthorities())I
if (needRole.equals(ga.getAuthority())) {
return;
}
}
log.info("need role is " + needRole);
}
throw new AccessDeniedException ( "Cannot Access!");
}
}When the user's access rights in the list match the metadata contained in the management role, it is used to verify whether the user's access rights match the metadata contained in the list.
This simplified design requires that when we create a role, its name must match the name in the configuration, that is, use admins and editors in the previous configuration.
If you want to control permissions through data management and realize richer permission management functions, you can refer to section 10.4.
After completing all the above designs, you can start testing.
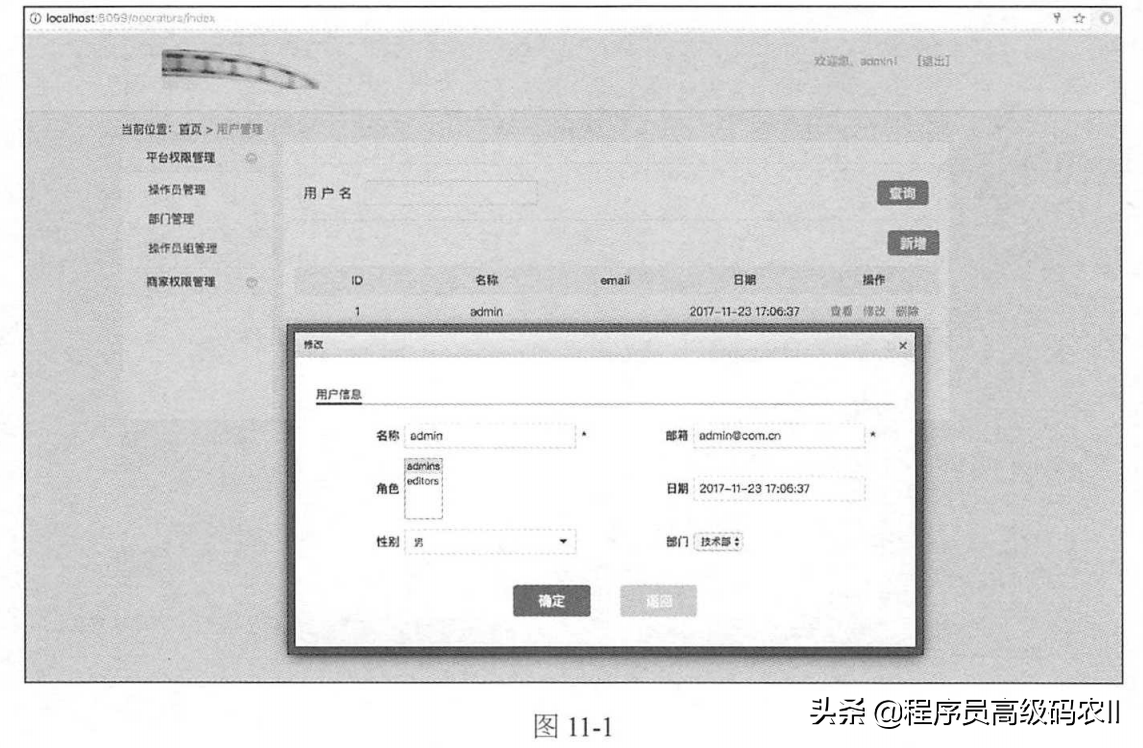
Directly start the manage web application. After successful startup, enter the following link in the browse to log in to the system:
http://localhost:8099
Use the user name admin generated in the previous unit test to log in to the system. After logging into the system, you can manage data such as operators and their roles, as shown in Figure 11-1.
The content of this paper is platform management background and merchant menu resource management: access control design of platform management background
- The next article will explain the platform management background and merchant menu resource management: the design of merchant registration management;
- Friends who think the article is good can forward this article and pay attention to the Xiaobian;
- Thank you for your support!