Named access control list can adjust the policy flexibly, provided that on the basis of standard access list and extended access list, no+ACL number can be used to delete the policy, or ACL number + permit+ip can be used to append the ACL policy.
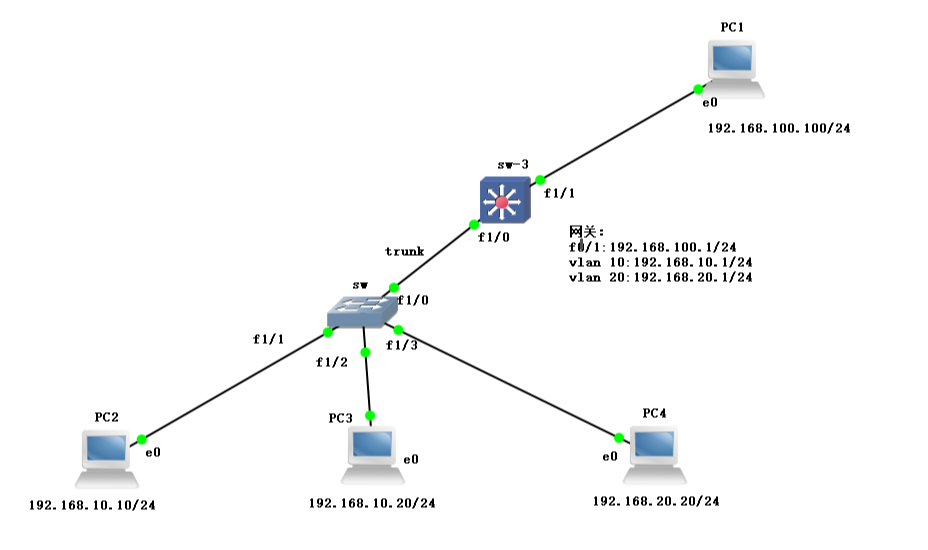
Experimental environment
One two-layer switch A three-layer switch Four PCs
Experimental requirement
Allow pc2 in VLAN 10 to access pc1 Deny other access to pc1 in vlan10 Allow hosts in other network segments to access pc1
Experimental topology
1. Configure sw layer 2 switch
sw#conf t ##Global schema sw(config)#vlan 10,20 ##Creating vlan10, 20 sw(config-vlan)#ex sw(config)#do show vlan-sw b ##View vlan sw(config)#int range fa1/1 -2 ##Enter interfaces f1/1 and f1/2 sw(config-if-range)#sw mo acc ##Create access link sw(config-if-range)#sw acc vlan 10 ##Put the interface in vlan10 sw(config-if-range)#ex sw(config)#int f1/3 ##Enter f1/3 interface, create access link and put it into VLAN 20 sw(config-if)#sw mo acc sw(config-if)#sw acc vlan 20 sw(config-if)#int f1/0 ##Enter f1/0 to create trunk link sw(config-if)#sw mo t sw(config-if)#sw t encapsulation dot1q sw(config-if)#ex sw(config)#no ip routing ##Turn off routing
2. Configure sw-3 three-layer switch
sw3#conf t ##Enter global mode sw3(config)#int f1/1 enters f1/1 interface sw3(config-if)#no switchport ##Close layer 2 interface sw3(config-if)#ip add 192.168.100.1 255.255.255.0 ##Configure interface gateway address sw3(config-if)#no shut on sw3(config-if)#ex sw3(config)#vlan 10,20 ##Creating vlan10, 20 sw3(config-vlan)#ex sw3(config)#int vlan 10 ##Enter vlan10 to configure the gateway address sw3(config-if)#ip add 192.168.10.1 255.255.255.0 sw3(config-if)#no shut sw3(config-if)#ex sw3(config)#int vlan 20 ##Enter vlan20 to configure the gateway address sw3(config-if)#ip add 192.168.20.1 255.255.255.0 sw3(config-if)#no shut sw3(config-if)#ex sw3(config)#do show ip int b ##View interface ip Vlan10 192.168.10.1 YES manual up down Vlan20 192.168.20.1 YES manual up down sw3(config)#int f1/0 ##Enter f1/0 interface to create trunk link sw3(config-if)#sw mo t sw3(config-if)#sw t encapsulation dot1q sw3(config-if)#ex sw3(config)#do show ip route ##View routing table C 192.168.10.0/24 is directly connected, Vlan10 C 192.168.20.0/24 is directly connected, Vlan20 C 192.168.100.0/24 is directly connected, FastEthe
3. Configure the ip address of the pc and test the interoperability of the whole network
pc 1: 192.168.100.100 pc 2: 192.168.10.10 pc 3: 192.168.10.20 pc 4: 192.168.20.20
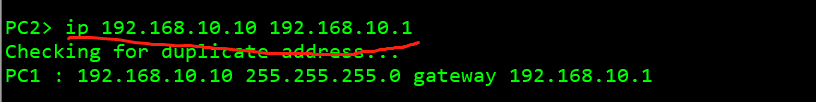
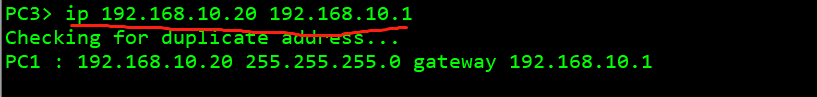
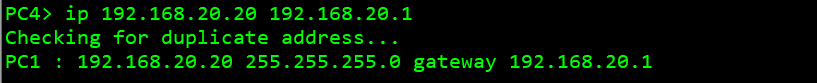
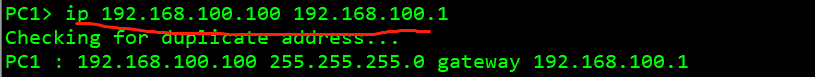
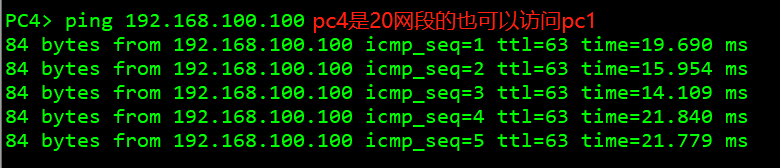
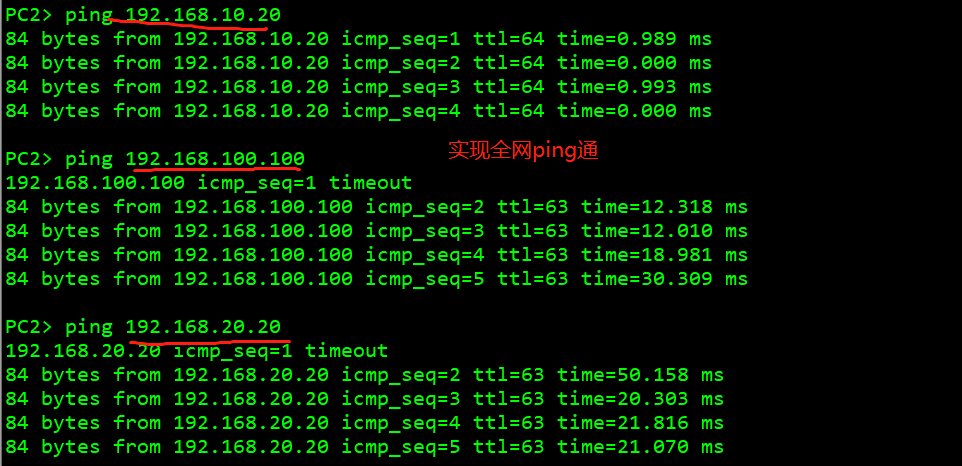
Test whether the whole network interworking
4. Configure ACL named access control list
sw3(config)#ip access-list standard test
##Set the mode and name. Standard is the standard and extended is the extension.
sw3(config-std-nacl)#permit host 192.168.10.10 ##Allow access to host ip
sw3(config-std-nacl)#deny 192.168.10.0 0.0.0.255 ##Deny other 10 segment access
sw3(config-std-nacl)#permit any ##Allow all other hosts access
sw3(config-std-nacl)#ex
sw3(config)#do show access-list ##View access control list
Standard IP access list test
10 permit 192.168.10.10
20 deny 192.168.10.0, wildcard bits 0.0.0.255
30 permit any
sw3(config)#int f1/1 ##Enter f1/1, apply ACL to interface in exit direction
sw3(config-if)#ip access-group test out5. Test ACL access control results
1. Host 2 in VLAN 10 can communicate with host 1.
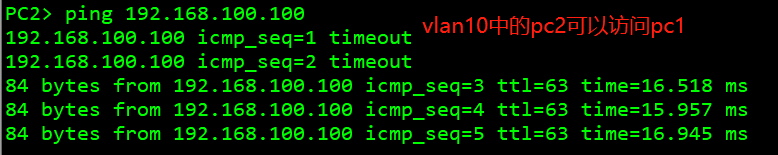
2. Host 3 in vlan10 cannot communicate with host 3
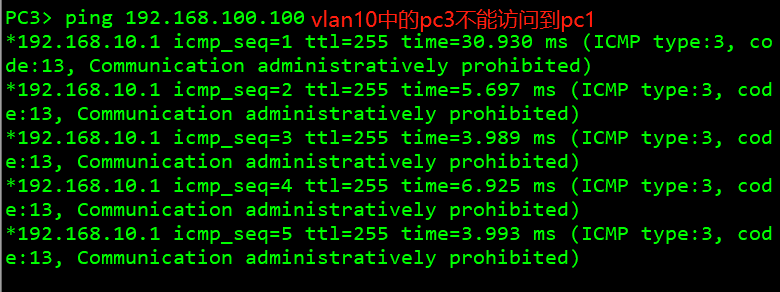
3. Host 4 of other network segments can be connected with host 1.