introduce
linux is a multi-user system, which arranges corresponding permissions for each user, so as to better manage files. For example, a user assigns a class of files, so that this class of files can only allow specific users to carry out sensitive operations, so as to prevent other files from being affected and the system from running down due to misoperation
Here I will first introduce some simple terms of user groups
- Uid: user identifier. Each user has a specific value. This is to make it easier for the kernel to call information about your user during execution. Different users generally have different UIDs. For example, the uid of root is 0 by default, and the uid of ordinary users is 500-6000, but some linux starts from 1000, such as kali, Then between the two users is the pseudo user's uid
- gid: the meaning of group indicator is the same as that of user indicator, which can be understood by analogy
- Landing shell: This is discussed in detail in another article. It is an application that connects the system kernel to the user
linux users:
linux user types
-
Super user: root, uid=0, the highest authority management user. You can modify the permissions of other users. By default, it is the highest authority for all files, that is, read-write execution
root Is all classes Unix The administrator of the system has the highest authority, so it will be very convenient in our daily use. There will be no problem of insufficient authority above, but the relative security risk is also greater. Sometimes it is because root A wrong command executed by the user leads to an irreversible crash of the system. In a word, it has great ability and greater responsibility -pysnow,Everyone is using it root Users must be careful when, especially when operating some system files
-
Ordinary user: has limited permissions of the operating system, and the UID value is 500 – 6000
There can be multiple ordinary users. The permissions of ordinary users are limited. For example, some files in the root directory only have read permissions, and some sensitive files only have execution but no read permissions. Then, this ordinary user is different from the pseudo user. He has a password, which is commonly known as the login password. It is also used shell And each ordinary user has his own home directory, which is generally located in/home A folder with the same name as your user in the directory. For example, my ordinary user name is kali,Then my home directory is/home/kali,This home directory can be used~Instead, of course, this home directory does not have to be consistent with your user name. You can modify it. Why should we have this ordinary user? Firstly, it must be to ensure safety and prevent misoperation. Secondly, it is convenient for management. For example, if you hand over your system to multiple people, you can't directly use it root Give it permission. You must give it a user with relatively low permission, so that it can not only enjoy some services brought by the system, but also prevent them from damaging their own system. Take several practical examples, such as the administrator account, teacher account and student account of the campus network. They have different permissions, super control in the live broadcasting room, ordinary bullet screen users, etc
-
Pseudo user: a permanent user specially created to meet the needs of the system process. Since there is no shell assigned to him, it cannot be used for login operation. The uid is 1-499
It is also called system or service users. Generally speaking, the role of these users is to meet the permission needs when executing a system process. Some system files ordinary users do not have permission. Therefore, in order to execute this command, higher permission needs to be allocated, but it can not be too high, as high as root Users do that, so they will execute it for different users according to different functions *Generally speaking, a command or service corresponds to a pseudo user *Pseudo users are not only used to execute system related processes, but also enable some third-party service functions, such as website services. Some of them may need higher permissions than ordinary users. Therefore, when installing this service, a pseudo user will be added to your system by default to make the service run normally *When you execute an operation command, it will be executed in the name of a specific user. When you log in with an ordinary user, you want to execute it reboot The command to restart the system is not allowed, but why is it allowed when operating? It is because you execute the command as one of the pseudo users of the system Common system pseudo users are as follows: bin Have executable user command files sys Own system files adm Own account file uucp UUCP use lp lp or lpd Subsystem usage nobody NFS use
You can use the cat /etc/passwd command to view the details of all users of the current system
linux user management
Add user
useradd [option] User name
option Options: -c comment Specify an annotative description. -d Directory specifies the user's home directory. If this directory does not exist, it will be used at the same time-m Option to create a home directory. -g User group specifies the user group to which the user belongs. -G User group. User group specifies the additional group to which the user belongs. -s Shell File specifies the user's login Shell. -u User number specifies the user number of the user, if both exist-o Option, you can reuse the identification numbers of other users.example
-
useradd -c Blog specific example users pysnow
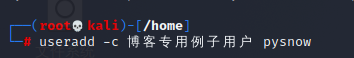

You can see that this comment is a string of descriptions added to the user. In fact, it has no effect except to facilitate the understanding of the user's functions, so as to prevent you from not knowing which user is used for what when you create more users
-
xxxxxxxxxx useradd -u 1314 -g 1111 -s /usr/bin/bash -dm /home/example pysnow
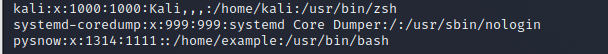
matters needing attention
-
If you do not specify anything except the user name when creating a user, it will default to the following results
comment The information of is empty or* Home directory defaults to/home In the folder with the same name as the currently created user uid It will default to the highest of all current users uid Add 1 on the basis of, for example, the users in my current system uid The largest value is 1314, so I pass useradd example Command to create the user, its uid It should be 1315 gid Default to uid The same unless you actively configure or modify it, and when you pass-g When adding a user group, select gid Must already exist bash Default use/bin/sh
- When two or more users with the same uid are created through the - o option, these users will be regarded as one user, but the functions of these users will not be affected, that is to say, these users are still separated from each other in terms of functions
-
-
delete user
Deleting a user is actually deleting part of the file information, that is, deleting the information about the user in / etc / passwd and / etc / shadow
Command
```bash
userdel [option] username
```
common option Options are-r,That is, delete recursively, and delete the user's home directory together userdel -r user name
Modify user
Modify the user's attributes, that is, the attributes mentioned in useradd above
usermod [option] user name
common option Above
-c comment Specify an annotative description.
-d Directory specifies the user's home directory. If this directory does not exist, it will be used at the same time-m Option to create a home directory.
-g User group specifies the user group to which the user belongs.
-G User group. User group specifies the additional group to which the user belongs.
-s Shell File specifies the user's login Shell.
-u User number specifies the user number of the user, if both exist-o Option, you can reuse the identification numbers of other users.
Manage user passwords
That is to manage the user's login password. By default, the user we created through the useradd command does not have a password, that is, there is no login password. It is locked by another system and cannot log in and use. Therefore, in order to log in and use the new user, we must add a password for it
passwd [option] user name //Modify the passwords of other users. Generally, the root user is used for operation passwd [option] //Modify the default user name, that is, the current user
Common option s are as follows
-l(lock) Lock the password, that is, disable the account. -u(unlock) Password unlock. -d(delete) Make the account no password. -f(force) Force the user to change the password at the next login.
matters needing attention
- When an ordinary user changes his password for himself, he will ask the current user's password, which is similar to qq changing password
- But when you use root to change the password for others, you won't ask. It's similar to qq's recall password function
- When you use the - d option to change the password of a user or your current user to none, the system will not let you log in by default when you try to log in again. You can also use the - l option to achieve the same purpose of not being allowed to log in
linux user properties
user attribute
User name: a string representing the user account. It is usually no longer than 8 characters and consists of upper and lower case letters and/Or numbers. The login name cannot have a colon(:),Because the colon is a separator here. For compatibility, it is best not to include dot characters in the login name(.),And do not use hyphens(-)Plus sign(+)Take the lead. Password: the login password of the user name. In some systems, the encrypted user password is stored Although this field only stores the encrypted string of the user password, not clear text, but because/etc/passwd The file is readable to all users, so this is still a security risk. So now many Linux System (e.g SVR4)All used shadow Technology to store the real encrypted user password in/etc/shadow File, and in/etc/passwd Only one special character is stored in the password field of the file, such as“ x"Or“*" User identifier(uid):Is an integer that is used internally to identify users. Generally, it corresponds to the user name one by one. If the user identification numbers corresponding to several user names are the same, they will be regarded as the same user within the system, but they can have different passwords, different home directories and different logins Shell Wait. Generally, the value range of user ID is 0~65 535. 0 Super user root Identification number of, 1~99 It is reserved by the system. As a management account, the identification number of ordinary users starts from 100 Linux In the system, the limit is 500. Group identifier: similar to the user identifier, it represents the group to which the user belongs, and/etc/passwd Is with/etc/group Corresponding comment(Annotative description):Similar to the comments in programming, it will not run when compiling and running, but it can help others quickly understand the code. The field records some personal situations of users. For example, the user's real name, telephone number, address, etc. this field has no practical use Linux The format of this field is not uniform in many systems Linux In the system, this field stores an arbitrary annotative description text for finger Output of the command. Home directory: the user's starting working directory. It is the directory where the user is located after logging in to the system. In most systems, the home directory of each user is organized in the same specific directory, and the name of the user's home directory is the login name of the user. Each user has read, write and execute (search) permissions on his own home directory, and the access permissions of other users to this directory are set according to the specific situation. land shell: After the user logs in, it is necessary to start a process, which is responsible for transmitting the user's operation to the kernel. This process is the command interpreter or a specific program that the user runs after logging in to the system, that is Shell. Shell Are users and Linux Interface between systems. Linux of Shell There are many kinds, each with different characteristics sh(Bourne Shell), csh(C Shell), ksh(Korn Shell), tcsh(TENEX/TOPS-20 type C Shell), bash(Bourne Again Shell)Wait. The system administrator can specify a user according to the system conditions and user habits Shell. If not specified Shell,Then the system uses sh Is the default login Shell,That is, the value of this field is/bin/sh. User login Shell It can also be specified as a specific program (this program is not a command interpreter). Using this feature, we can limit the user to run only the specified application. After the application runs, the user will automatically exit the system Linux The system requires that only those programs registered in the system can appear in this field. *Pseudo user: These users are/etc/passwd There is also a record in the file, but they cannot log in because they are logged in Shell Empty. Their existence is mainly to facilitate system management and meet the requirements of corresponding system processes for file ownership.
User related documents
-
In the / etc directory of linux, there is a file called passwd, which stores the information of all users of the current system, that is, user attributes
-
Similarly, in the current / etc directory, there is a file called shadow, which is used to encrypt the information after the user password. Generally, ordinary users do not have access
-
Similarly, under the current directory is a file called skel, which is a configuration file used to configure the default attributes when creating users
Next, I will explain the first two documents in detail
-
/etc/passwd file
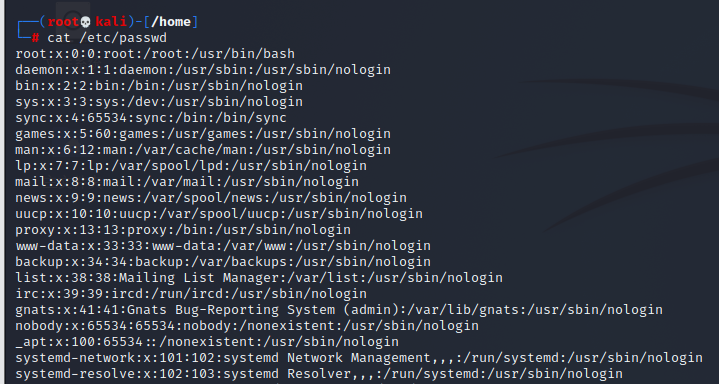
user name:Password:User identification number:Group identification number:Annotative description:home directory:Sign in Shell example: pysnow:x:1314:1111::/home/example:/usr/bin/bash user name: pysnow Password: x User ID: 1314 Group ID: 1111 comment Description: None Home directory:/home/example land bash: /usr/bin/bash

You can see that each line in this file represents the information of a user. The information of each line is separated by semicolons
-
/etc/shadow file
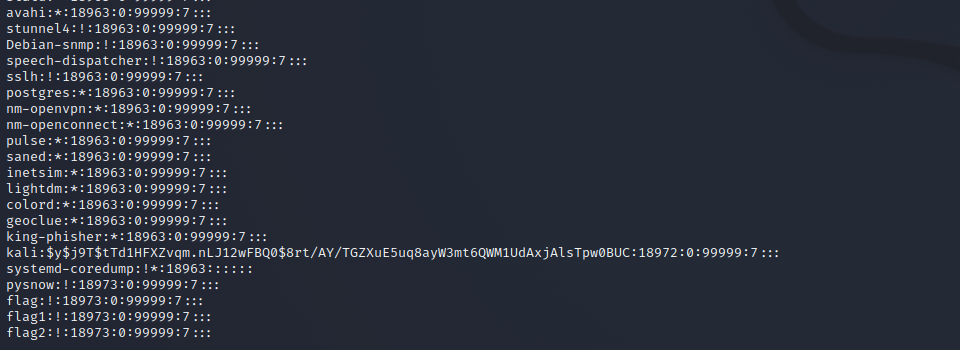
Because the / etc/passwd file is readable by all users, if the user's password is too simple or the law is obvious, an ordinary computer can easily crack it. Therefore, Linux systems with high security requirements separate the encrypted password word and store it separately in a file. This file is the / etc/shadow file. It is only supported by super users Have the permission to read the file, which ensures the security of the user password.
/The record lines in / etc/shadow correspond to those in / etc/passwd one by one. It is automatically generated by pwconv command according to the data in / etc/passwd
Its file format is similar to / etc/passwd
Login name:encrypted password:Last modification time:Minimum time interval:Maximum time interval:Warning time:Inactive time:Failure time:sign example: pysnow:!:18973:0:99999:7::: Login name:"Login name"Is with/etc/passwd User account with the same login name in the file Encrypted password: the password field stores the encrypted user password, with a length of 13 characters. If it is blank, the corresponding user does not have a password and does not need a password when logging in; If it does not belong to the collection { ./0-9A-Za-z }The corresponding user cannot log in. Last modification time: it refers to the number of days from a certain time to the last time the user modifies the password. The time starting point may be different for different systems Minimum time interval: refers to the minimum number of days between two password changes. Maximum time interval: refers to the maximum number of days that the password remains valid. Warning time: the field indicates the number of days between the system warning the user and the official expiration of the user password. Inactive time: refers to the maximum number of days that the user has not logged in but the account can remain valid. Expiration time: the field gives an absolute number of days. If this field is used, the lifetime of the corresponding account will be given. After the expiration, the account will no longer be a legal account and can no longer be used to log in.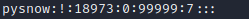
linux user group
Each user has one or more user groups (additional groups) belonging to him. The purpose of this is to facilitate management. For example, when your system has a large number of users, you can't manage them one by one. At this time, you can install your own needs and divide them into different groups. In this way, you can directly manage user information in batches through group operations in the future
In linux, the default is to automatically generate a group when generating users, and the group identifier (gid) is consistent with the user identifier (uid)
linux user group management
Add group:
groupadd [option] User group
Commonly used option Options:
-g GID Specifies the group identification number for the new user group( GID).
-o General and-g Options are used together to represent the name of the new user group GID You can connect with existing user groups in the system GID Same.
Delete group:
groupdel User group
Modify group properties
groupmod [option] User group
Commonly used option Options:
-g GID Specify a new group ID for the user group.
-o And-g Options are used together with the new user group GID You can connect with existing user groups in the system GID Same.
-n New user group changes the name of the user group to a new name
linux user group related files
-
User grouping is a means to manage users and control access rights in Linux system.
-
Each user belongs to a user group; there can be multiple users in a group, and a user can also belong to different groups.
-
When a user is a member of multiple groups at the same time, the main group to which the user belongs is recorded in the / etc/passwd file, that is, the default group to which the user belongs when logging in, while other groups are called additional groups.
-
When a user wants to access a file belonging to an additional group, he must first use the newgrp command to make himself a member of the group to be accessed.
-
All information about user groups is stored in the / etc/group file. The format of this file is also similar to that of the / etc/passwd file. Several fields are separated by colons (:). These fields are:
Group name:Password:Group identification number:List of users in the group Group name: the name of the user group, consisting of letters or numbers/etc/passwd Like the login in, the group name should not be duplicate. Password: the field stores the password word encrypted by the user group. Generally Linux The user groups of the system do not have passwords, that is, this field is generally empty or empty*. Group ID: similar to user ID, it is also an integer, which is used internally to identify groups. Intra group user list: it is a list of all users belonging to this group, with commas between different users(,)Separate. This user group may be the user's primary group or an additional group.
linux user group note
-
As I said earlier, a user can have multiple user groups at the same time. In fact, multiple groups here are multiple additional groups, and there is only one group. How to say, a user can only correspond to one user group, but a user group can correspond to multiple users. In order to realize the operation of corresponding multiple users, the concept of additional groups appears, which means, This is why our virtual machines and ECS can raise permissions and switch root users, because all users in the same user group share permissions with each other
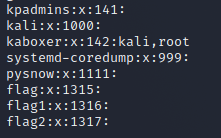
For example, kali in the figure here has an additional group, root
-
Users can switch to other user groups through newgrp. Of course, the premise is that the user group is your additional group
newgrp root //Switch to root group