1.this is flag
Idea: the title description is flag
2.pdf
Attachment: link: https://pan.baidu.com/s/1nyajq1Bjql-scT2FxicOGg
Extraction code: 5zzi
Idea: open the attachment and find a pdf file with a picture
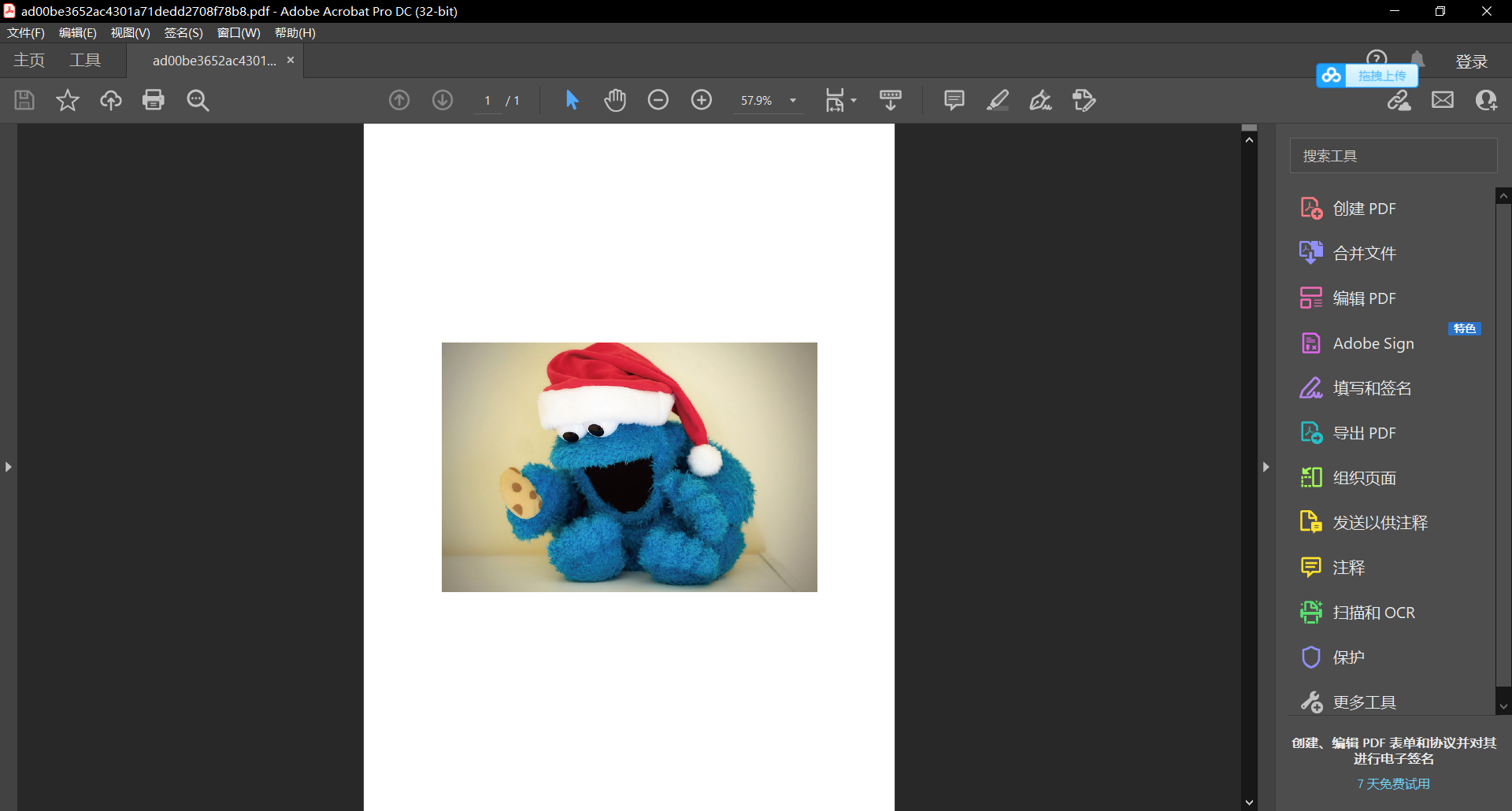
In the title description, "there is nothing below the picture", it is speculated that it is multi-layer or picture occlusion
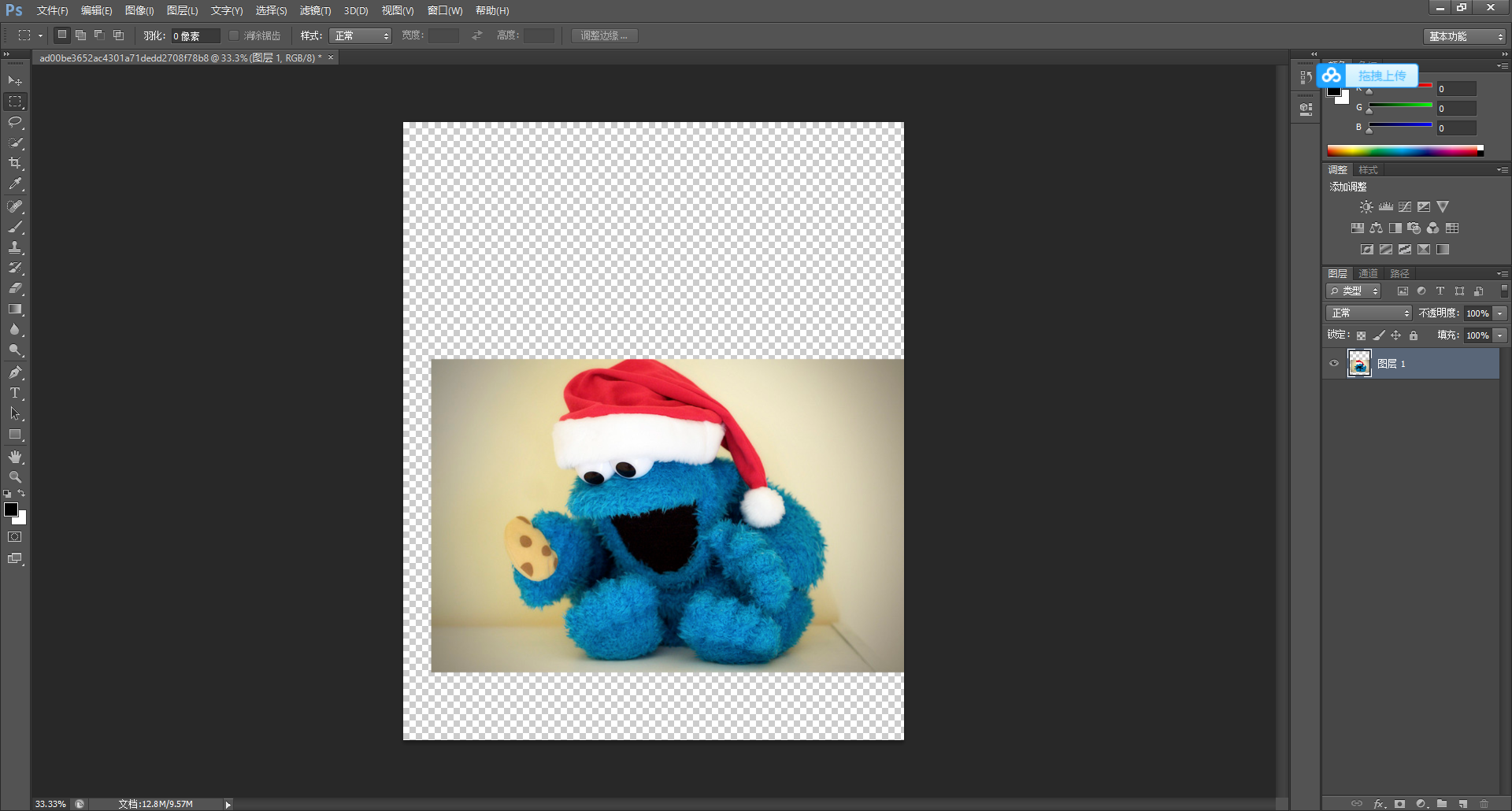
Open with PS and find that there is only one layer
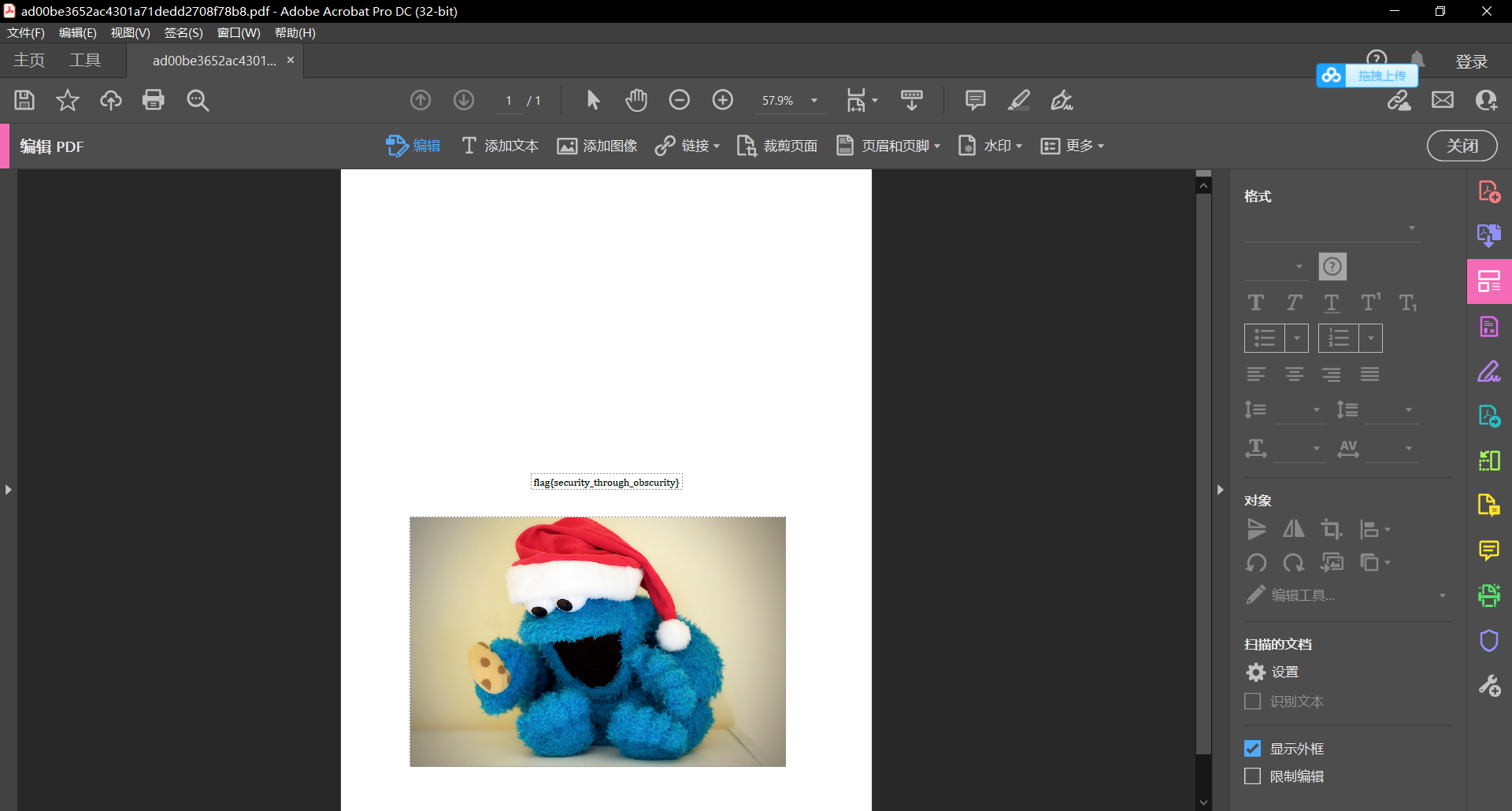
Try to use Adobe Acrobat Pro to edit pdf files, remove the pictures and get the flag
3. Tathagata thirteen palms
Attachment: link: https://pan.baidu.com/s/11YSA14LDDFSW3mkJImooDA
Extraction code: l8wu
Idea: the attachment is a word document
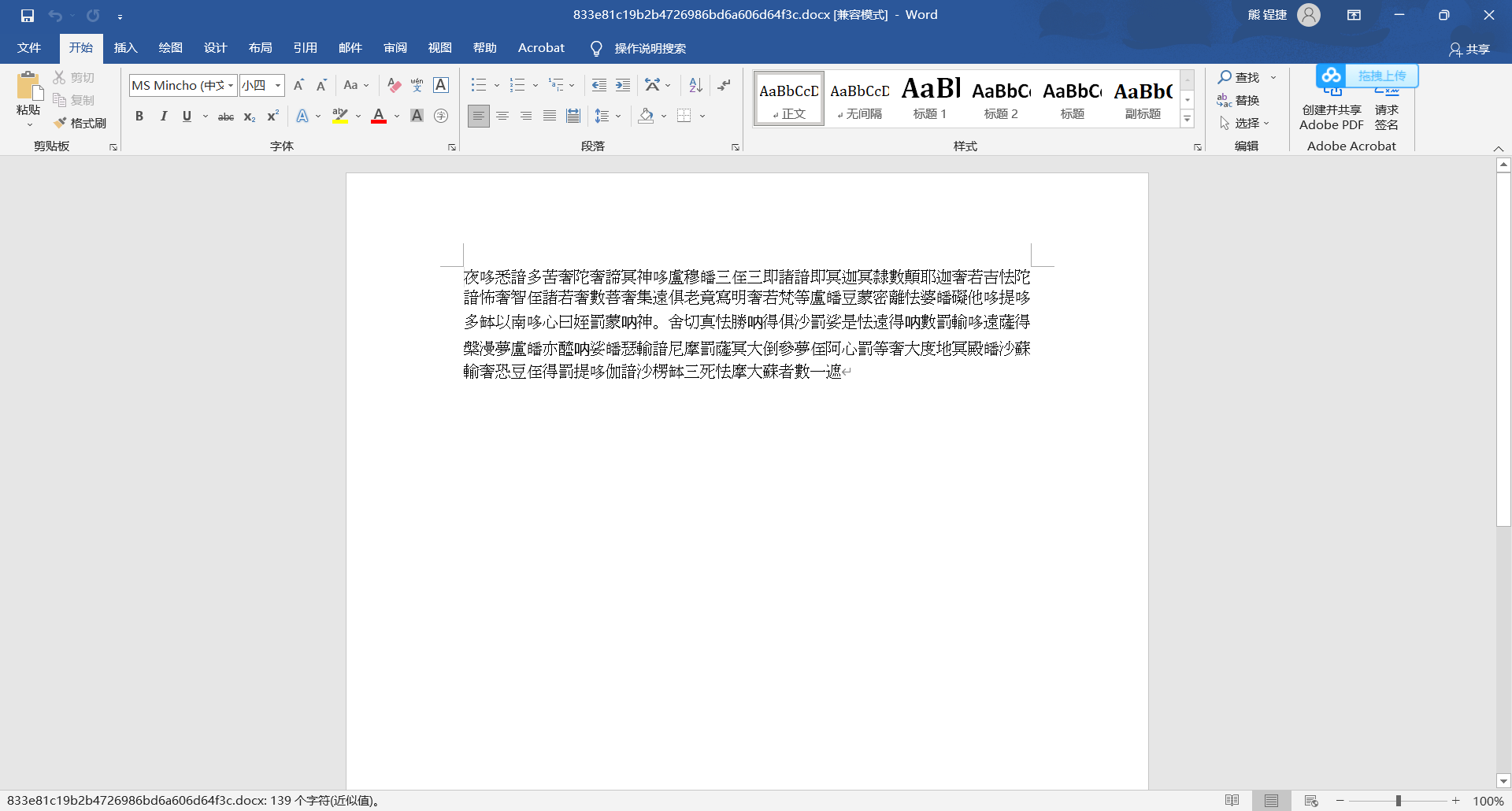
The content is Buddhist scripture text, which is decrypted through the website of Buddhism and Zen
And Buddhism on Zen (keyfc.net)
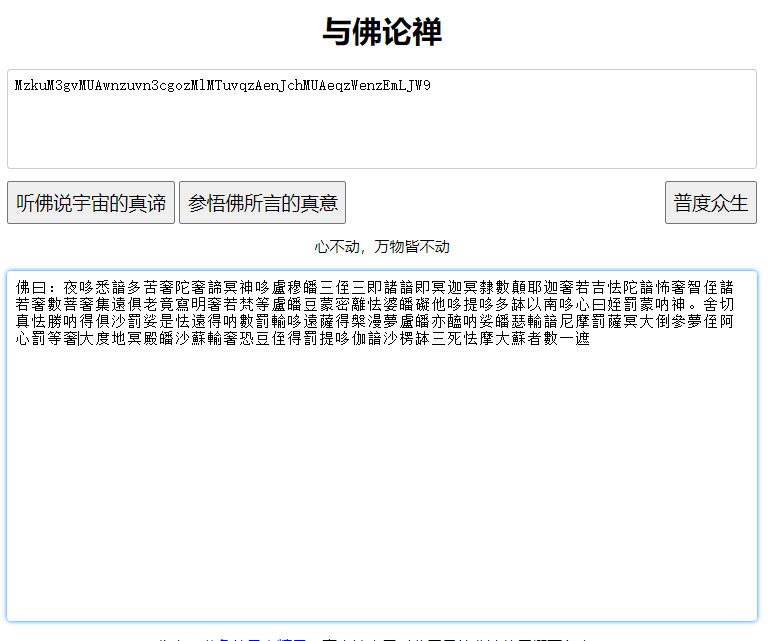
Because it is the thirteen palm of Tathagata, try to decrypt it through rot13
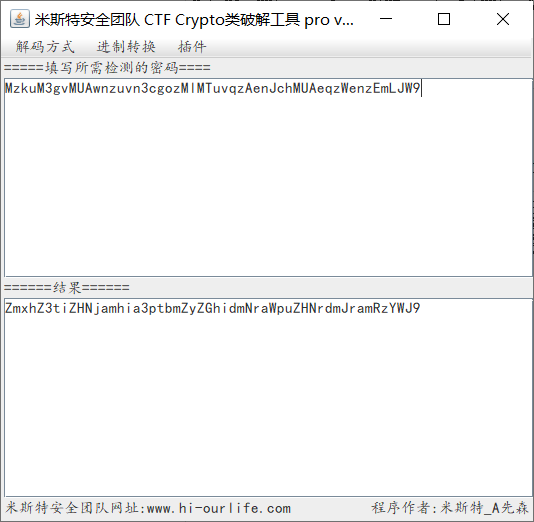
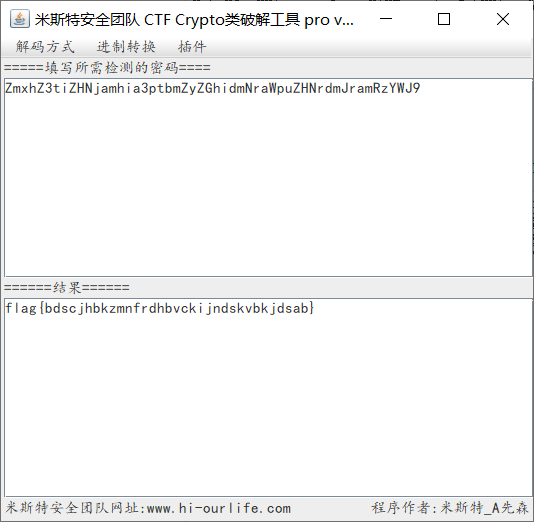
The obtained ciphertext is still ciphertext, which is decoded by base64 to get flag
4.give_you_flag
Attachment: link: https://pan.baidu.com/s/1zJlVW2Rj02V9pPMoXX6-2g
Extraction code: 860r
Idea: the attachment is a moving picture. After playing, it is found that there is a QR code hidden in one frame. After pausing, it is found that the positioning angle is missing

Complete the QR code and scan the code to get the flag

5.stegano
Attachment: link: https://pan.baidu.com/s/1E2l7tAzpreIpCIAMRC4ikQ
Extraction code: yo4n
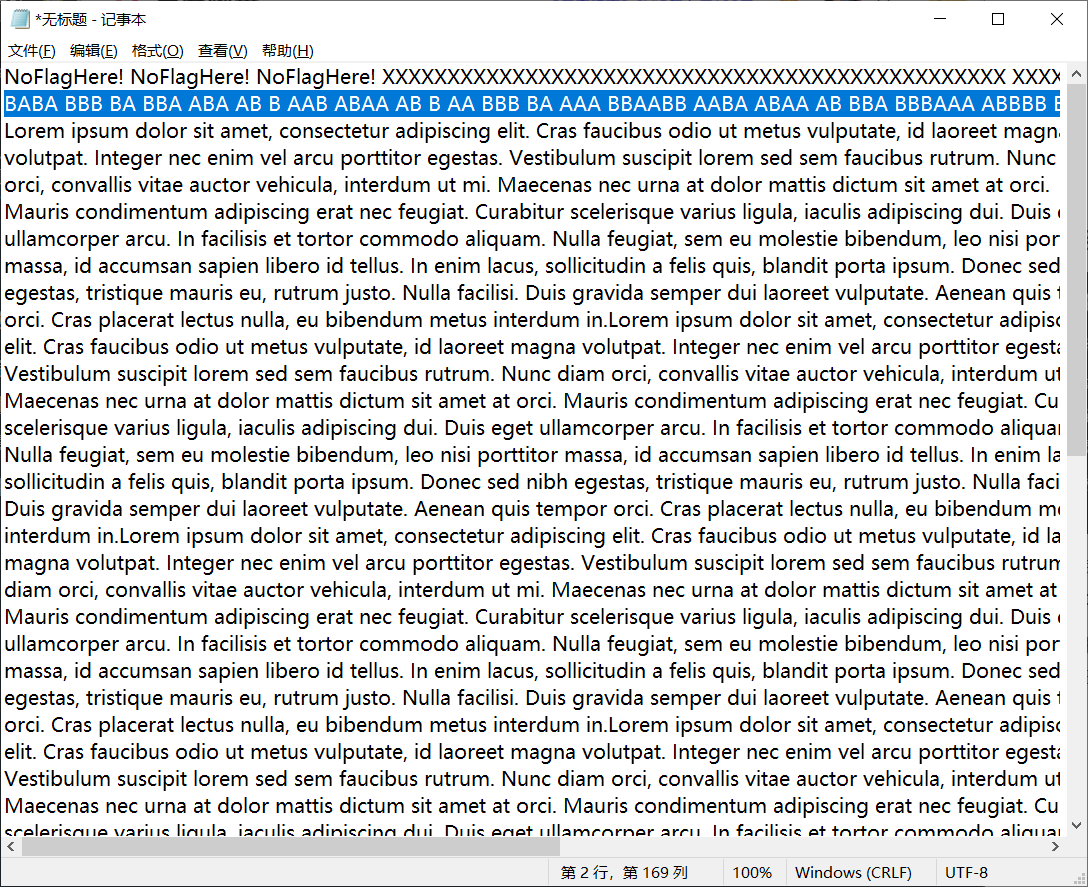
Idea: open the pdf file and find that the content is more than the displayed part. After selecting all, copy and paste it into the Notepad. It is found that there is only AB content in one line. It is speculated that it is encrypted by Morse code
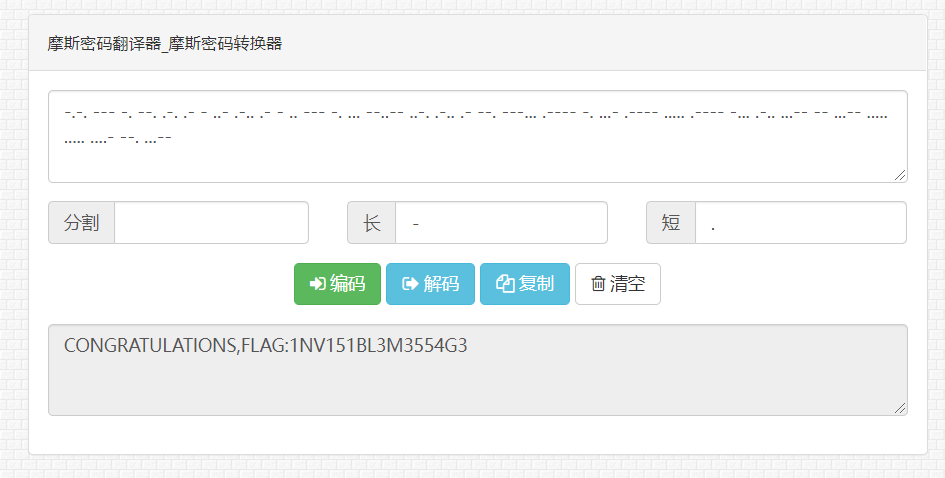
After converting to Morse code, get flag
6. Persist for 60s
Attachment: link: https://pan.baidu.com/s/1nMnj89Iqdiw1Ui6JZA25qQ
Extraction code: j6ft
Idea: the attachment is a java project. After opening, it is a small game. Combined with the title, you can get the encrypted flag after 60s

Obviously, the real flag is obtained after base64 encryption and decryption
Idea 2: since no flag was given at the beginning of 60s, use the java reverse tool luyten to download the link: GitHub - deathmarine/Luyten: An Open Source Java Decompiler Gui for Procyon
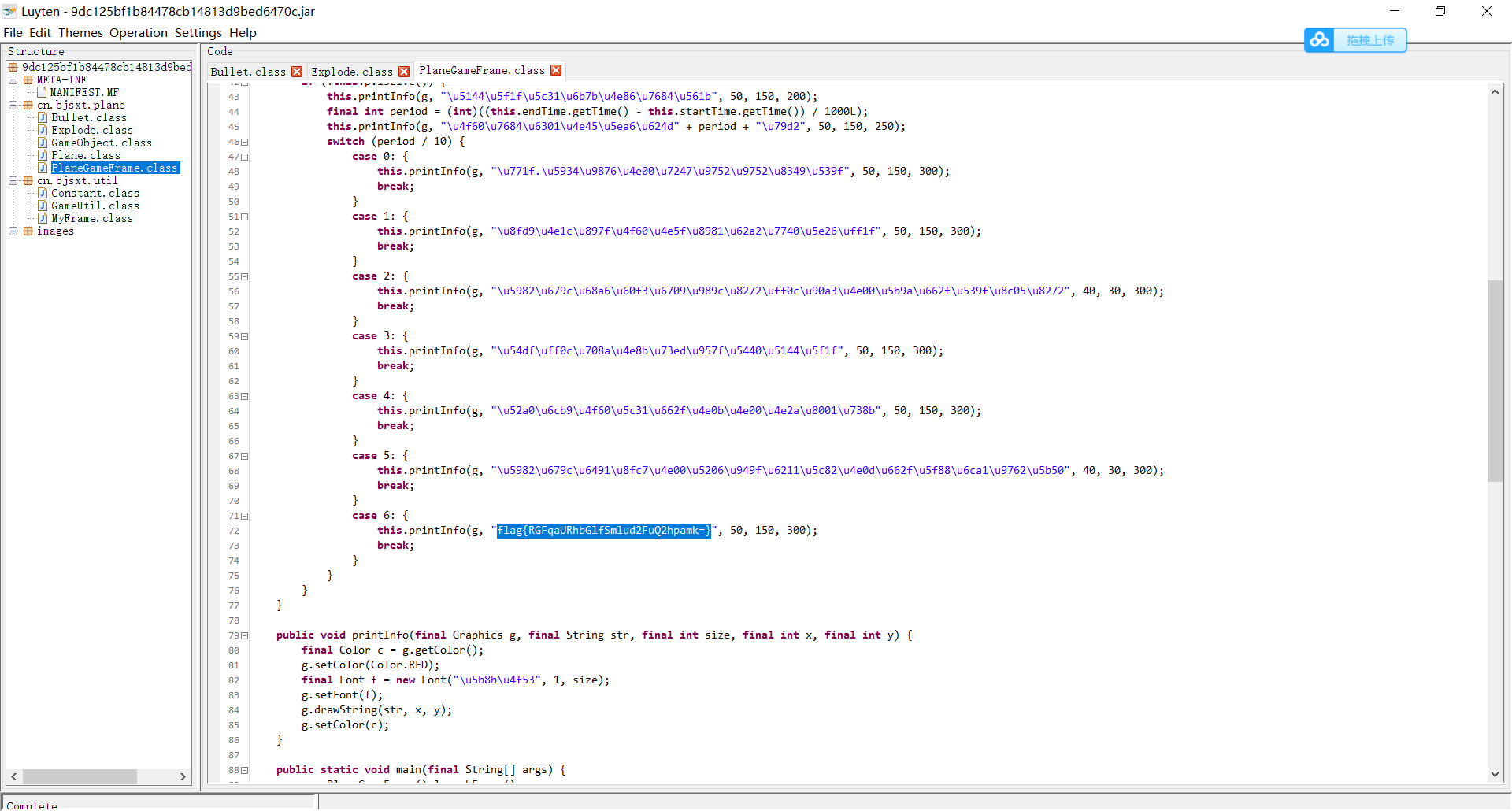
In planegameframe Obviously, the encrypted flag can also be obtained in the class file
7.gif
Attachment: link: https://pan.baidu.com/s/1VGHvgturbdRFd30NqshAlA
Extraction code: 7tz0
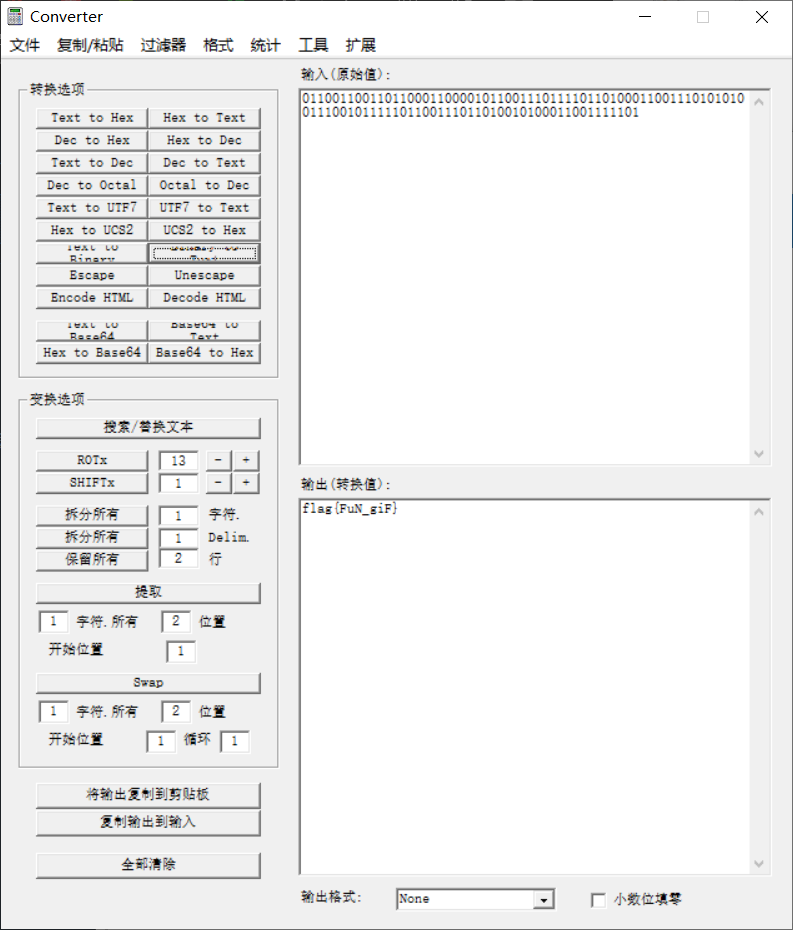
Idea: the attachment is a compressed package. There are 104 pure black and white pictures in the directory gif. It is speculated that it is binary encryption. White is 0 and black is 1. After decoding, it is converted into text to get flag
8. Lift the table
Message: c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e4e4e6f2
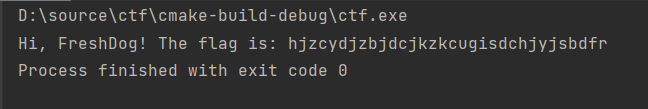
Idea: try base64 decoding first, but it is unsuccessful. Try md5 decoding again, but it is still unsuccessful. It is speculated that the text is converted to two digit hexadecimal, but they are beyond the range of ASCII, so subtract 128 and then convert it to text to get flag
#include <iostream>
using namespace std;
int main()
{
string s1="c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2";
char s2[3];
int ten,single,hex;
//cout<< sizeof(s1)<<endl;
int i=0;
for (i=0;i<118;i++)
{
if(i%2==0)
{
s2[0] = s1[i];
s2[1] = s1[i + 1];
s2[2]='\0';
//cout<<s2;
//cout << '-';
ten=s2[0];
//cout<<ten<<'-';
ten-=95;
ten*=16;
//cout<<ten<<'-';
single=s2[1];
if(single<96)
single-=48;
else
single-=87;
hex=ten+single;
cout<<char(hex);
}
}
}
9.ext3
Attachment: link: https://pan.baidu.com/s/1pbn5EggJFGwWdumsof4xDA
Extraction code: e419
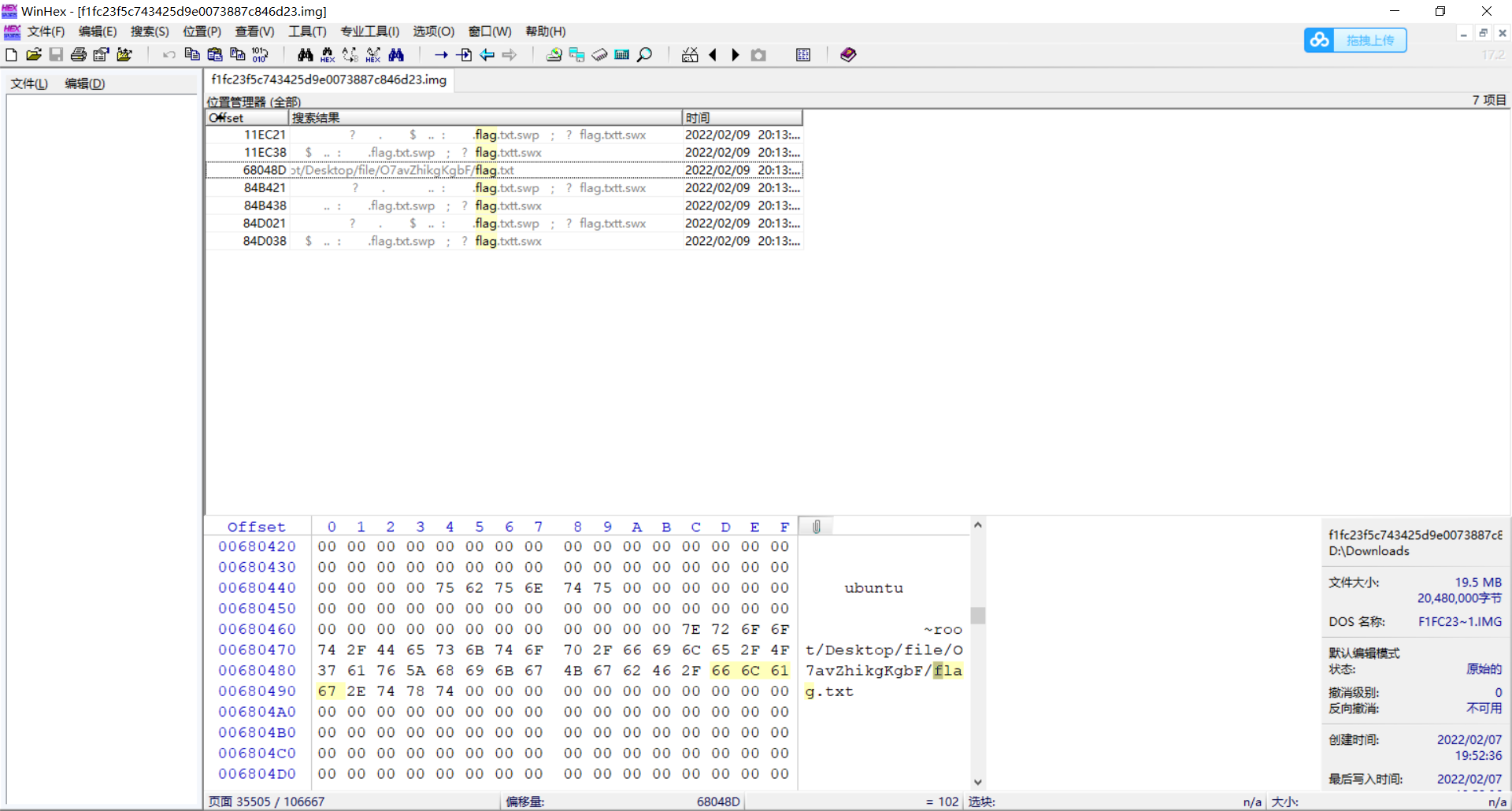
Idea: the attachment is a file without suffix. Search for the title ext3, and you know that it is a file system under linux, but you can open it through explore2fs tool under Windows (explore2fs tool link: chrysocome.net - Explore2fs)
Drag the file into winhex and search the flag information to get the flag Txt path
Get the flag through the path in explore2fs Txt, view after export
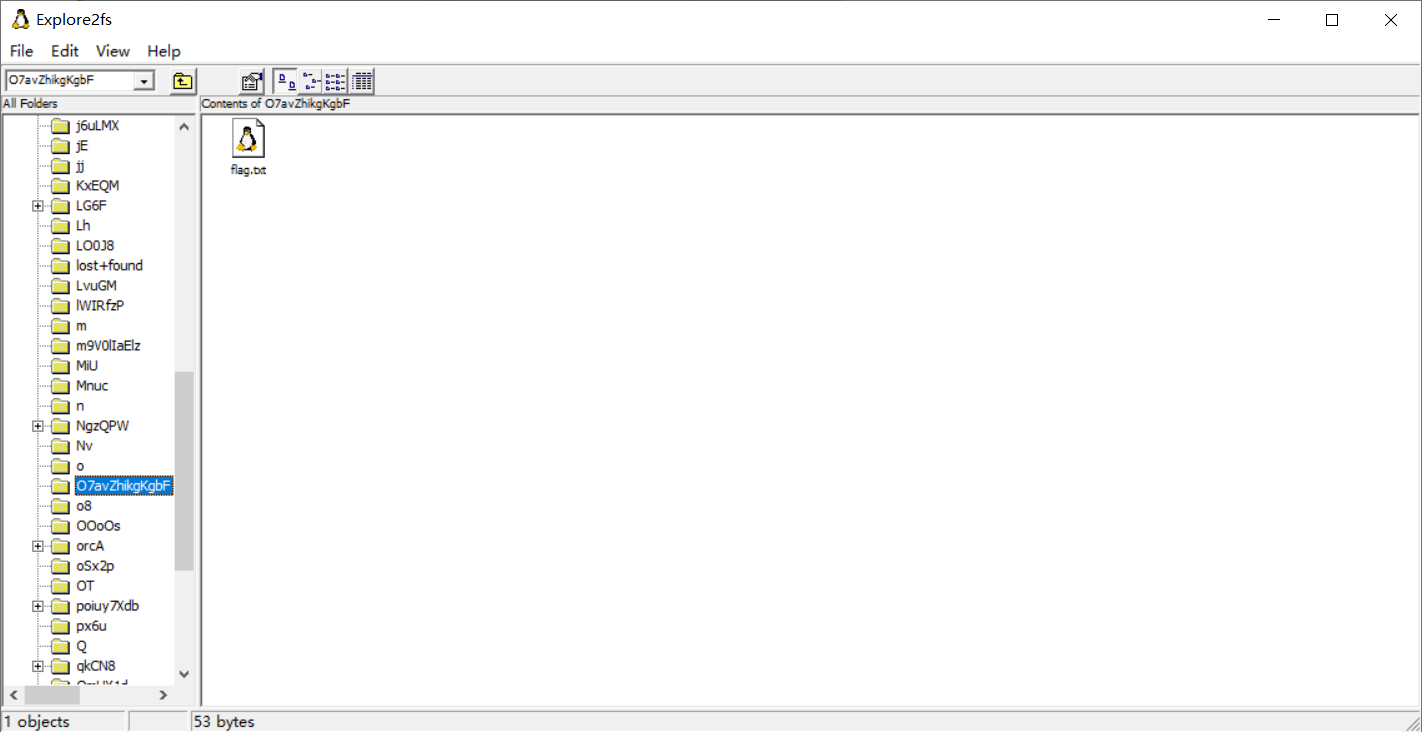
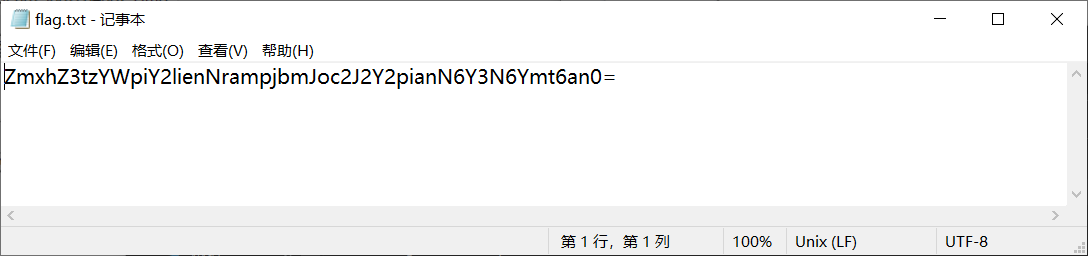
Obviously, it is the ciphertext encrypted by base64, and the flag is obtained after decryption
10.SimpleRAR
Attachment: link: https://pan.baidu.com/s/19RKM2chqJganO6yJM5dZsw
Extraction code: jqkp
Idea: the attachment is a compressed file, and there is only one text document flag in the compressed package Txt, the content is "flag is not here". Open it in winhex and find that there is secret in the compressed package Png, so check the file format.
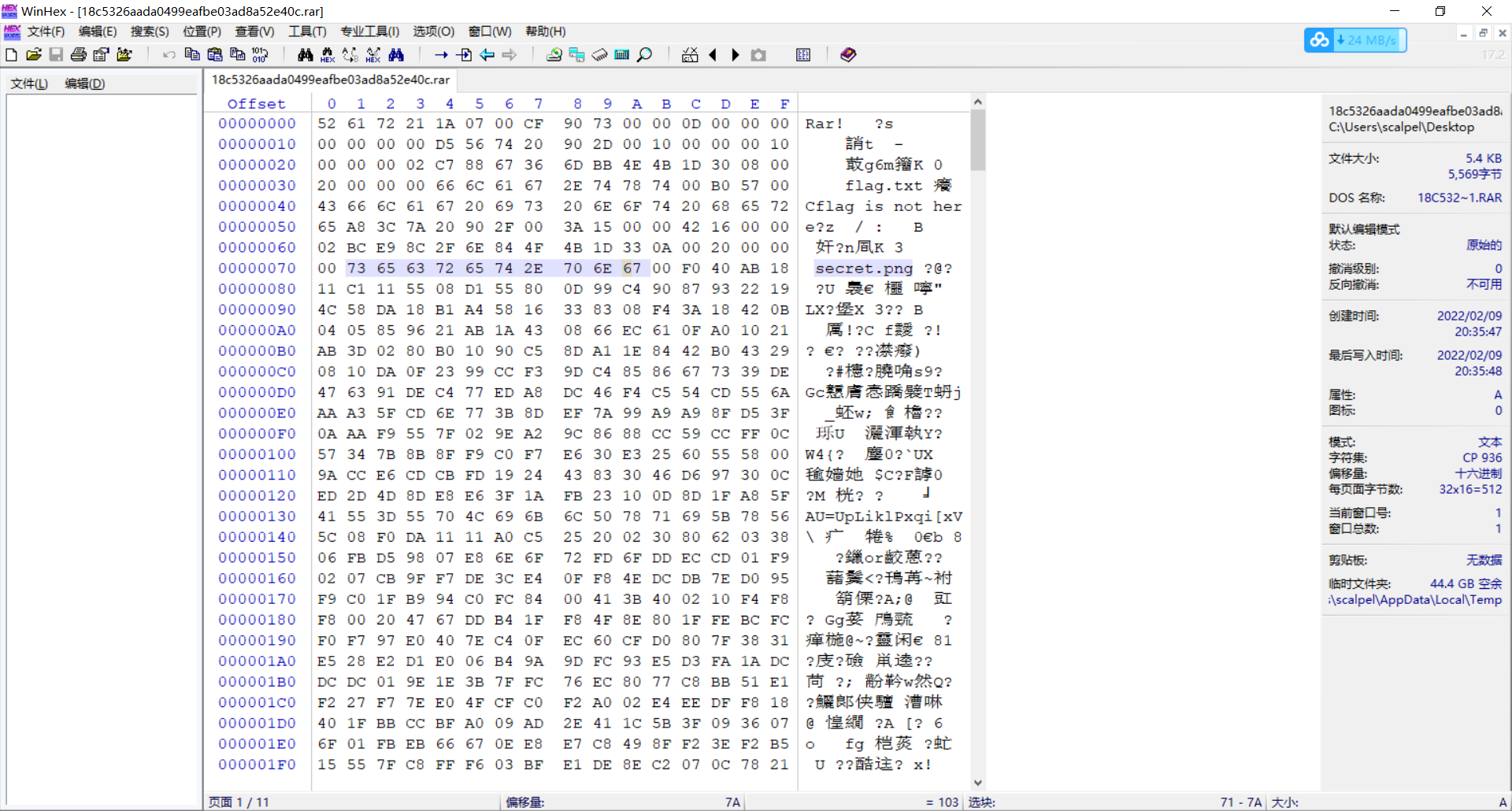
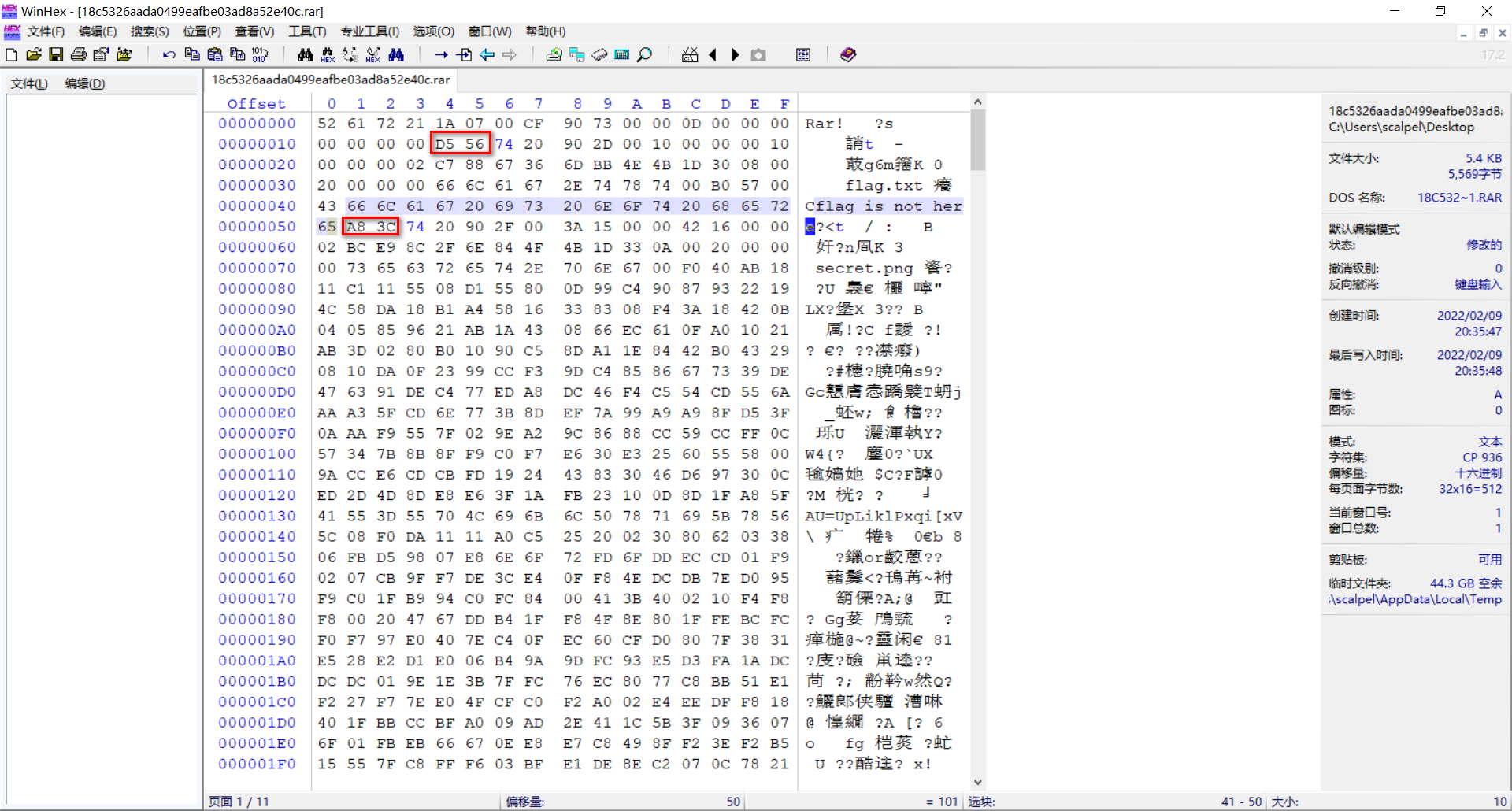
After the two red boxes come out, 74 should be connected to indicate the file header in the compressed file. After modification, extract secret png
For the explanation of rar file, see the blog rar file simple analysis - Angel - Steve - blog Park (cnblogs.com)
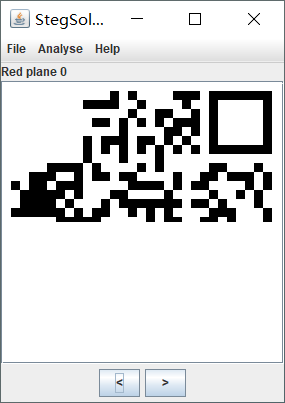
Use stegsolve to open the picture and get the QR code of the lower part
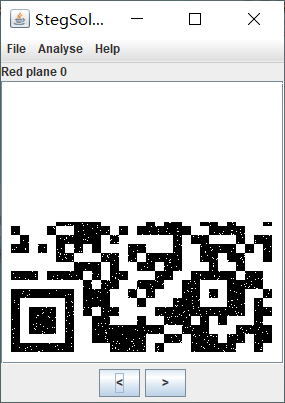
It can be seen from the title description that the file should be multi-layer. Try to open it with ps, but there are the following errors, and then open it with winhex for analysis
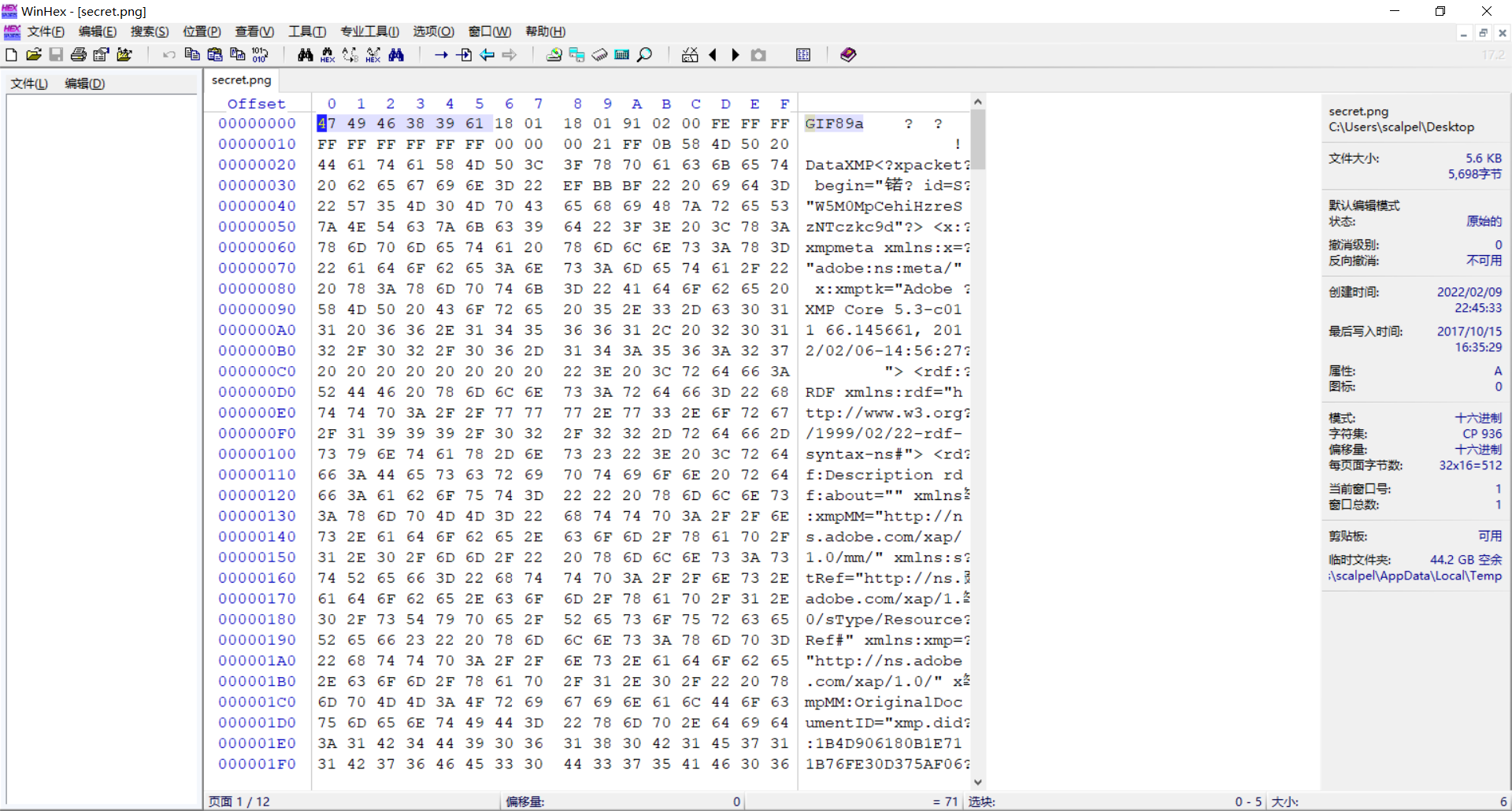 After observing the file header, it is found that the file is actually in gif format. After modifying the suffix, open it with ps, merge the two layers, and then use stegsolve to get the QR code of the upper part. After patching and completing, scan the code to get the flag
After observing the file header, it is found that the file is actually in gif format. After modifying the suffix, open it with ps, merge the two layers, and then use stegsolve to get the QR code of the upper part. After patching and completing, scan the code to get the flag
11.base64stego
Attachment: link: https://pan.baidu.com/s/1Zr4xht-Iu0HlfXESM1z8OA
Extraction code: kmnh
Idea: the attachment is an encrypted compressed package. Since there is no prompt for decompression password, it is judged to be pseudo encryption, and zipcenop.com is used Jar de pseudo encryption
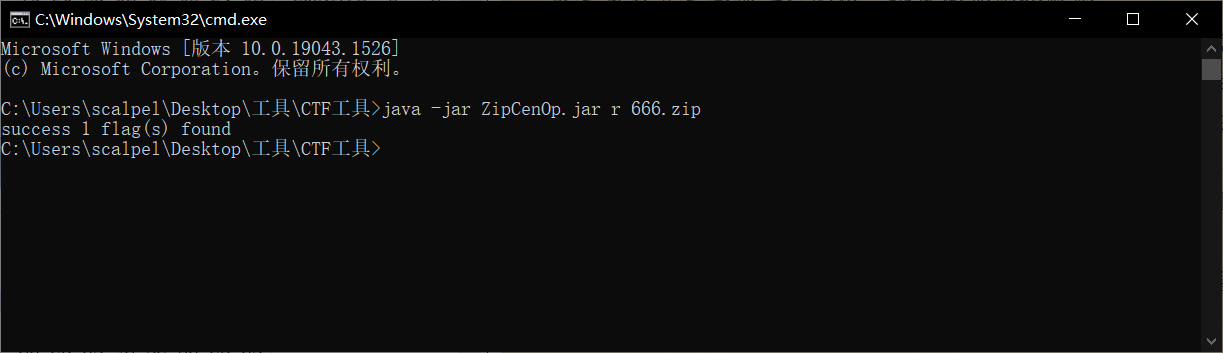
Get stego file
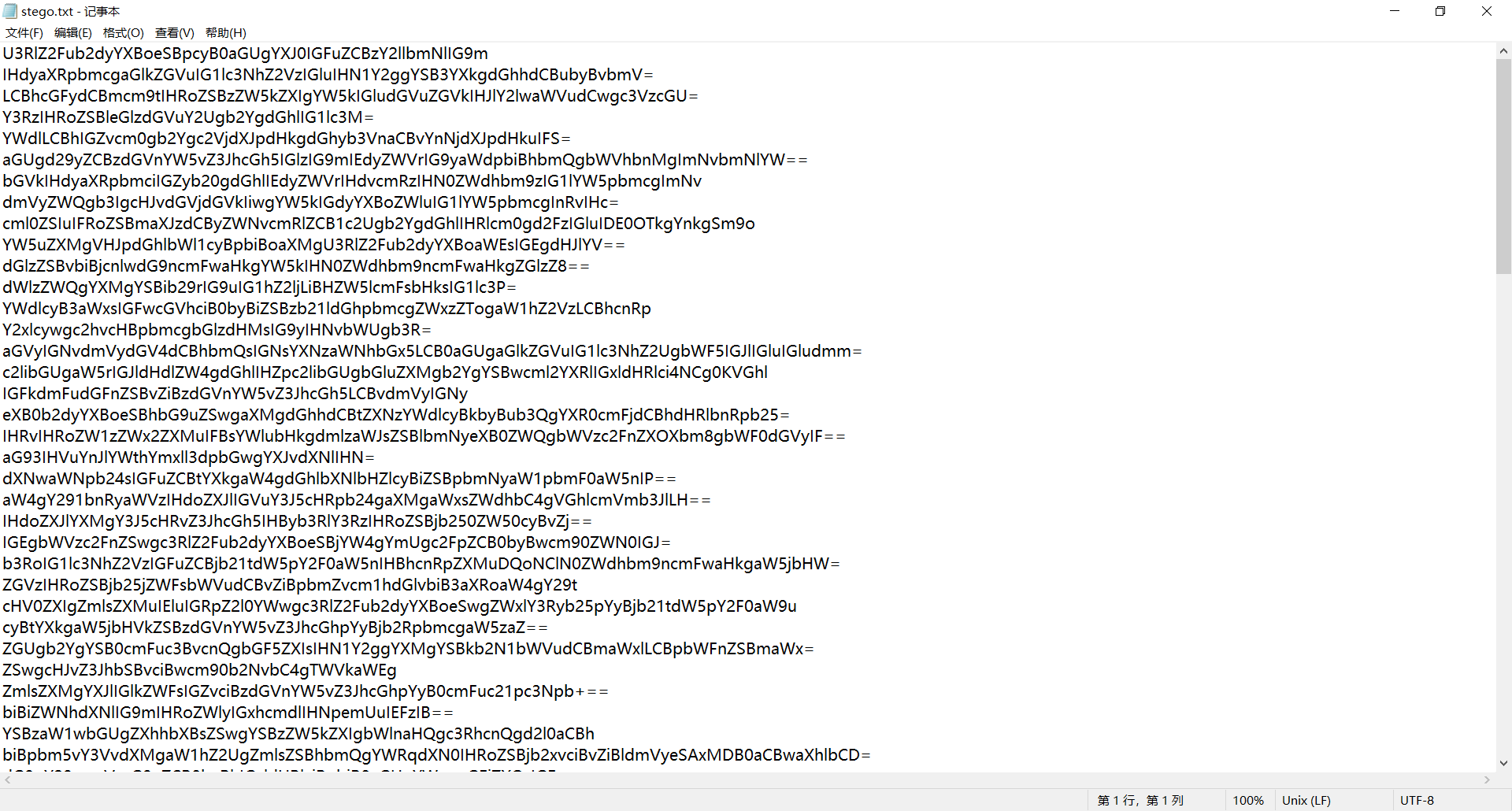
The second method to remove the pseudo encryption is to modify the binary file, open the pseudo encrypted compressed package with winhex, and modify the continuous 4-bit byte to "504b 01 02" (P, K.) The following byte is encrypted when it is odd and not encrypted when it is even (usually at the end of the file, there are multiple places)
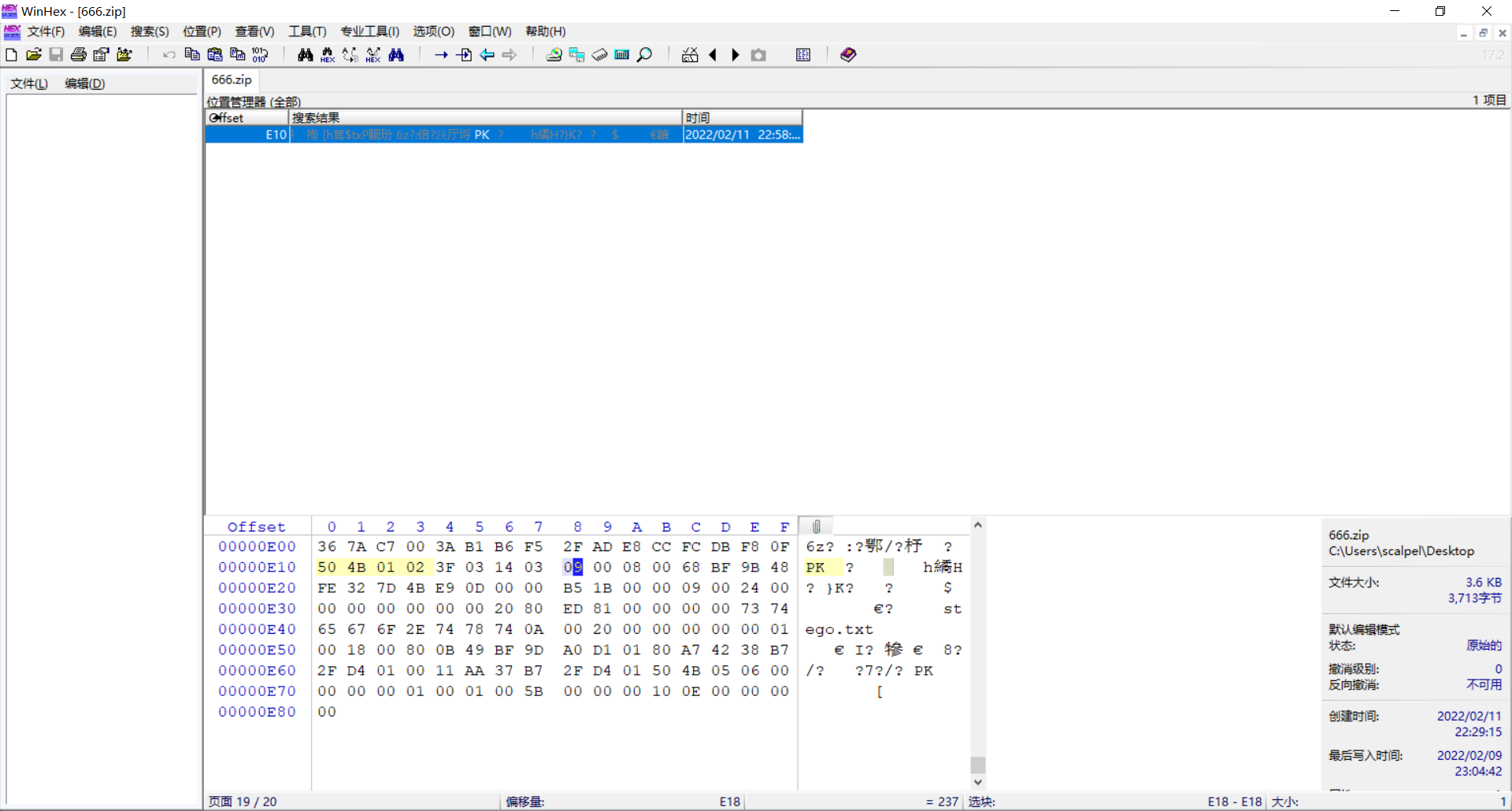
Replace the blue 9 with 0 to remove the pseudo encryption
Put stego Txt ciphertext decryption, get an article about steganography
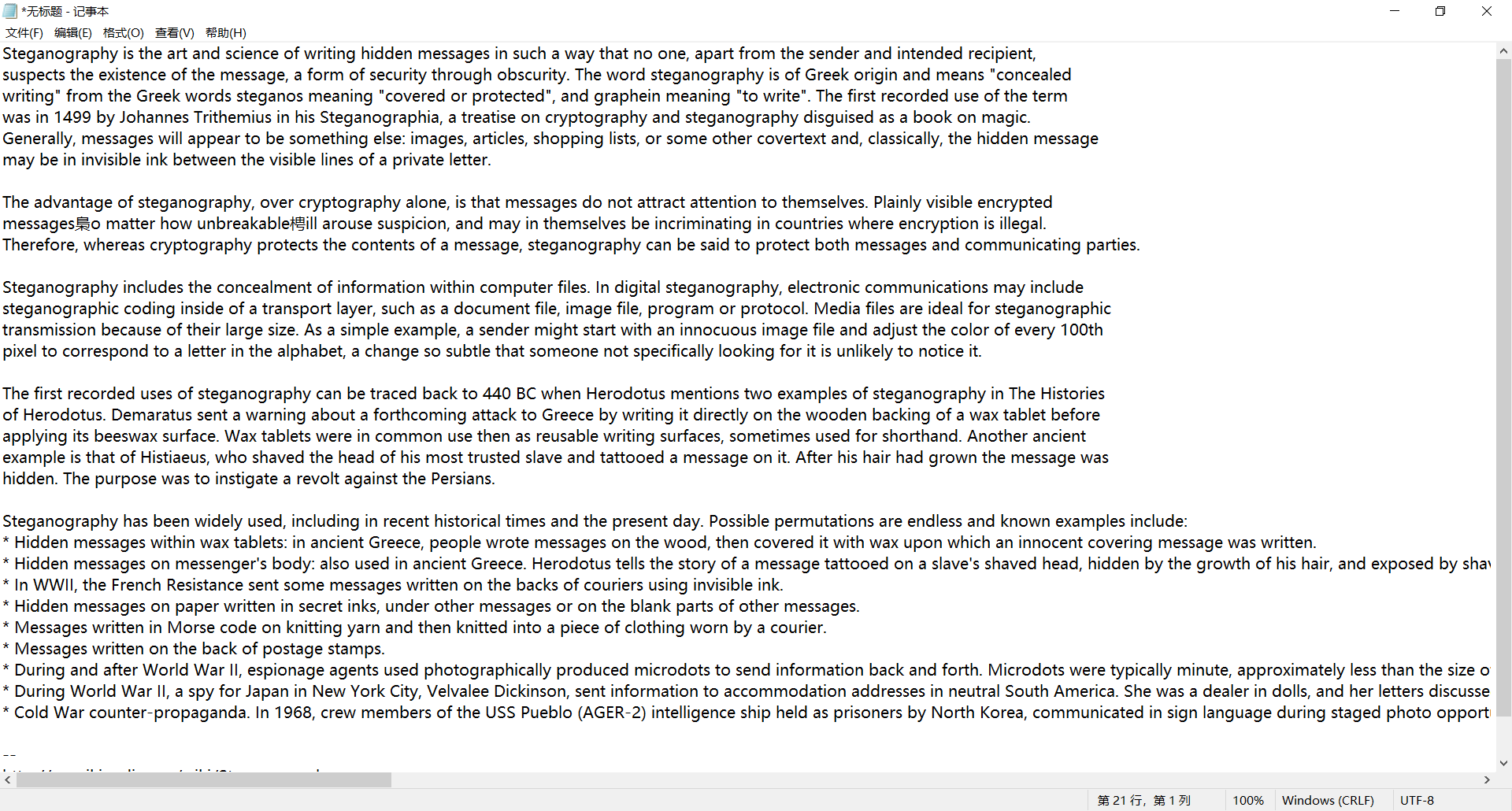
After analysis, it is found that there is no flag in the article, then go back to the original text to find clues.
According to the principle of base64 encryption, when n = occur, the last character of Base64 ciphertext can be steganographed in 2n bits. The specific explanation is as follows.
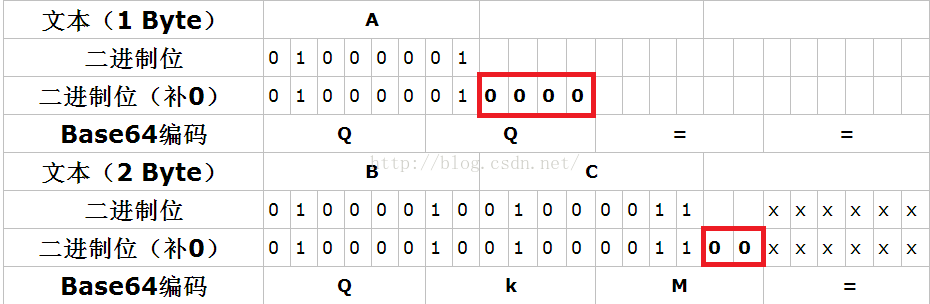
The number in the red box can be changed at will and will not affect the decoded result. Therefore, stego Txt is implicitly written to the last bit of the binary number extracted, and then eight bits into a group of text, you can get the flag.
#include<iostream>
#include <fstream>
using namespace std;
const string base64[64][2]={ //Create base64 encoding
{"000000","A"},
{"000001","B"},
{"000010","C"},
{"000011","D"},
{"000100","E"},
{"000101","F"},
{"000110","G"},
{"000111","H"},
{"001000","I"},
{"001001","J"},
{"001010","K"},
{"001011","L"},
{"001100","M"},
{"001101","N"},
{"001110","O"},
{"001111","P"},
{"010000","Q"},
{"010001","R"},
{"010010","S"},
{"010011","T"},
{"010100","U"},
{"010101","V"},
{"010110","W"},
{"010111","X"},
{"011000","Y"},
{"011001","Z"},
{"011010","a"},
{"011011","b"},
{"011100","c"},
{"011101","d"},
{"011110","e"},
{"011111","f"},
{"100000","g"},
{"100001","h"},
{"100010","i"},
{"100011","j"},
{"100100","k"},
{"100101","l"},
{"100110","m"},
{"100111","n"},
{"101000","o"},
{"101001","p"},
{"101010","q"},
{"101011","r"},
{"101100","s"},
{"101101","t"},
{"101110","u"},
{"101111","v"},
{"110000","w"},
{"110001","x"},
{"110010","y"},
{"110011","z"},
{"110100","0"},
{"110101","1"},
{"110110","2"},
{"110111","3"},
{"111000","4"},
{"111001","5"},
{"111010","6"},
{"111011","7"},
{"111100","8"},
{"111101","9"},
{"111110","+"},
{"111111","/"}
};
int main()
{//
ifstream infile("D:\\stego.txt");//input file
ofstream outfile("D:\\flag.txt");//output file
string line,line_end,base64_flag,binary_flag;
char end[3];
int length,i,count;
if(!infile.is_open())
{
cout<<"The file was not opened successfully"<<endl;
}
while(getline(infile,line)) //From stego Txt to read the string line by line
{
//cout<<line<<endl;
length=line.size(); //Take string length
//cout<<length<<endl;
//cout<<line[length-1]; // Judge the last bit of string
for(i=0;i<3;i++) //Take the last three digits
{
end[i]=line[length-1-i];
}
count=0;
for(i=0;i<3;i++) //Judgment last = quantity
{
if(end[i]=='=')
count++;
}
if(count==1)
{
line_end=line[length-count-1]; //Turn the last bit into a string
for(i=0;i<64;i++)
{
if(base64[i][1]==line_end) //Find the base64 binary corresponding to the last character
{
base64_flag=base64[i][0];
break;
}
}
for(i=0;i<2;i++)
{
outfile<<base64_flag[4+i];
cout<<base64_flag[4+i];
}
}
else if(count==2)
{
line_end=line[length-count-1]; //Turn the last bit into a string
for(i=0;i<64;i++)
{
if(base64[i][1]==line_end) //Find the base64 binary corresponding to the last character
{
base64_flag=base64[i][0];
break;
}
}
for(i=0;i<4;i++)
{
outfile<<base64_flag[2+i];
cout<<base64_flag[2+i];
}
}
}
infile.close();
outfile.close();
cout<<endl<<"finished!";
return 0;
}
12. No matter how high your Kung Fu is, you are afraid of a kitchen knife
Attachment: link: https://pan.baidu.com/s/1g0jmil38aozsrM4bbzNLXA
Extraction code: of2k
Idea: check the data package in wireshark and find the compressed package and flag txt
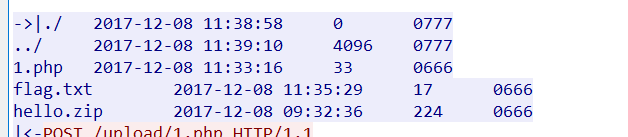
Open it with winhex, find the flag file, find the zip file header, and reorganize the block into a new file
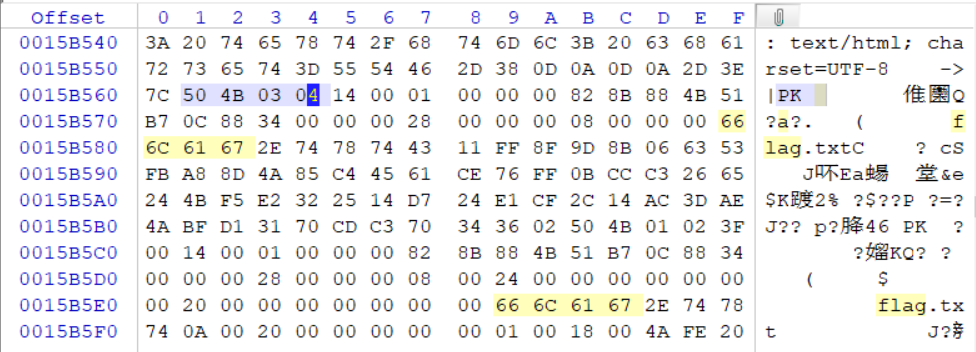
The compressed packet is encrypted. Guess the password hidden in the packet and continue to go back to wireshark to find clues
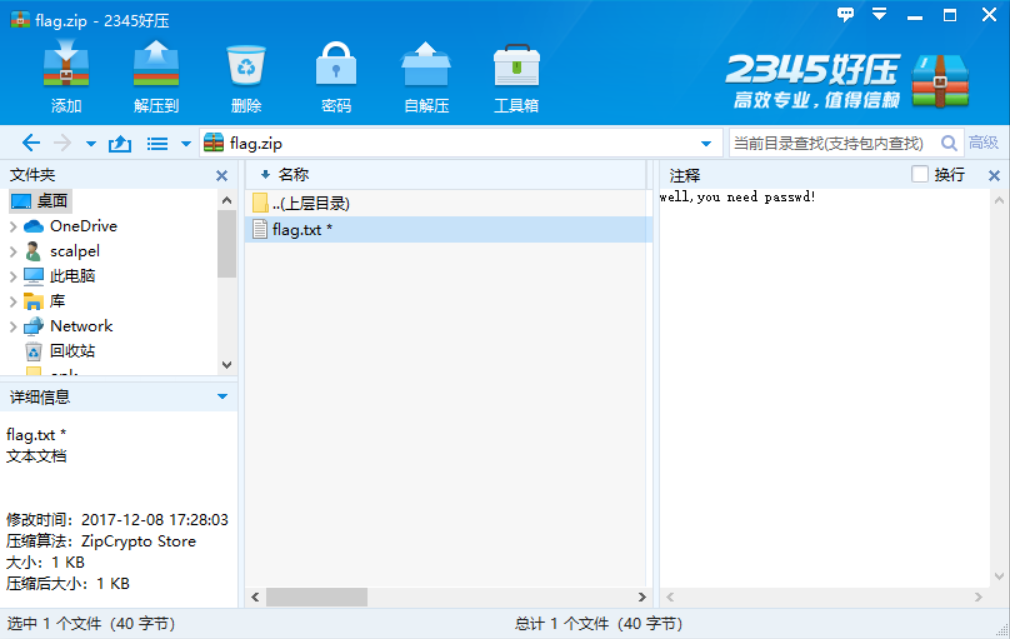
Search the data package with the flag and check it one by one. In the 1150 data package, the following information is found. Due to the beginning FFD8FFE0, it is judged to be the hexadecimal of the jpg file, which is copied to winhex to form a new file. Check it, get the decompression password and open the flag Txt to get the flag
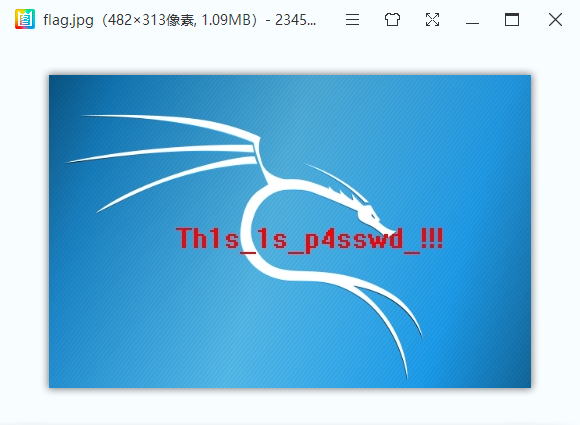
foremost tool can also be used for file separation. Address: foremost/foremost.exe at master · raddyfiy/foremost · GitHub
Drag the file to be separated into foremost Exe, you can get the separated file