Build encrypted web service https httpd+mod_ssl
install
To implement encryption authentication, this security module is called mod_ssl
yum install mod_ssl -y
After installation, an SSL is generated under the sub configuration module Conf file
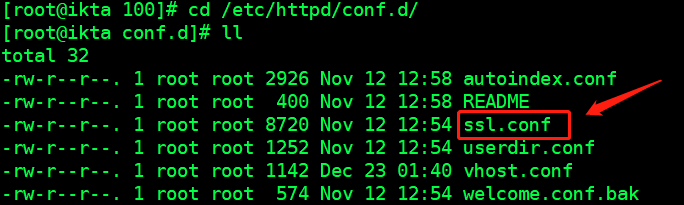
Go to view the configuration items in the file
vim /etc/httpd/conf.d/ssl.conf
Listen 443 https Listening port SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog Set the password information of the certificate SSLSessionCache shmcb:/run/httpd/sslcache(512000) ssl Cache of and its location SSLSessionCacheTimeout 300 Timeout length of cache <VirtualHost _default_:443> Host module definition ErrorLog logs/ssl_error_log Error log TransferLog logs/ssl_access_log Transfer log LogLevel warn Log level (normally warning) SSLEngine on SSL Engine on verification SSLHonorCipherOrder on Negotiation algorithm SSLCertificateFile /etc/pki/tls/certs/localhost.crt Specify our certificate file (internal response transfer) pki Public key infrastructure tls Authentication protocol certs certificate .crt Self signed certificate file SSLCertificateKeyFile /etc/pki/tls/private/localhost.key Private key file path The public key is sent to the client host through the certificate, and the private key must be in our server host
Modify configuration
###Website information of company B
<VirtualHost 192.168.17.200:80>
ServerName 192.168.17.200 ip
DocumentRoot /200 root directory
SSLEngine on SSL Engine on
SSLCertificateFile /etc/pki/tls/certs/openlab.crt Self signed certificate
SSLCertificateKeyFile /etc/pki/tls/private/openlab.key Secret key
</VirtualHost>
<Directory /200> directory right
AllowOverride none
Require all granted
</Directory>
<VirtualHost 192.168.17.200:80>
ServerName www.haha.com Domain name resolution
DocumentRoot /200/haha
</VirtualHost>
SSLCertificateFile must indicate the path of the certificate before sending the certificate (if it is. crt, it is marked as a self signed certificate file)
SSLCertificateKeyFile after we send the certificate, let it verify the public key and private key, so we must also indicate the path of the private key on the server (if it is. Key, it is marked as the private key file)
x.509 general certificate format includes three files: key, CSR and CRT.
Key is the private key file.
csr is a certificate signing request file that is submitted to a certification authority (CA) to sign a certificate.
crt is a certificate signed by a certification authority (CA), or a developer's self signed certificate, including the information of the certificate holder, the holder's public key, and the signer's signature.
---------------------------------------------------------------------RHEL7-------------------------------------------------------------------
(first)[ root@localhost certs]# make jiami. crt
The first method generates a certificate (password authentication is not required)
------------------After version 8 -------------------!!! Attention--------------------------------------------------
(the second) #openssl req - newkey RSA: 4096 - nodes - sha256 - keyout / etc / PKI / TLS / private / iktalab key -x509 -days 365 -out /etc/pki/tls/certs/iktalab. crt
Analysis: the openssl certificate generation command req requests to generate a secret key through - newkey. The secret key algorithm used is the asymmetric secret key RSA algorithm. The encryption length generated through the secret key is 2048 or 4096. The encoding format of the certificate file is marked through - nodes. The sha256 is used. The secret key file generated by us is specified through - keyout / etc / PKI / TLS / private / iktalab Key, specify our certificate format through - x509, specify the certificate validity period of 365 in - x509 standard format, and - out to output our certificate file / etc / PKI / TLS / certs / iktalab crt
openssl req -newkey rsa:4096 -nodes -sha256 -keyout /etc/pki/tls/private/iktalab.key -x509 -days 365 -out /etc/pki/tls/certs/iktalab.crt #According to our requirements, we use RSA algorithm to generate the private key, and after generating the private key, we need to register our public key in the certificate Generating a RSA private key ..........++++ .......................................................................................................................++++ writing new private key to '/etc/pki/tls/private/iktalab.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Information contained (easy test) Country Name (2 letter code) [XX]:86 Country code State or Province Name (full name) []:shannxi province Locality Name (eg, city) [Default City]:xi'an city Organization Name (eg, company) [Default Company Ltd]:iktalab Company name/Organization name Organizational Unit Name (eg, section) []:ce department/Organizational unit Common Name (eg, your name or your server's hostname) []:localhost Your Name/Name of the server Email Address []:admin@ikta.com mailing address
Restart service (test)
systemctl restart httpd
Browser input https://192.168.17.200/
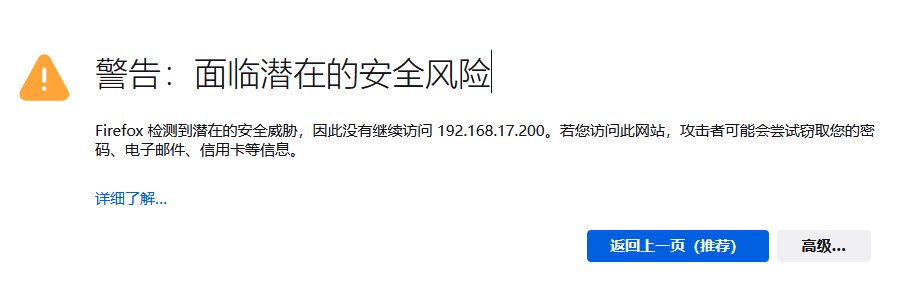
Advanced options accept risk and are accessible
The second method generates a certificate (password authentication is required)
--------------------------------------------------------------------x509 key csr crt------------------------------------------------------
[root@ikta certs]# openssl genrsa -aes128 2048 > /etc/pki/tls/private/iktalab.key
(third) #openssl req - utf8 - New - key / etc / PKI / TLS / private / iktalab key -x509 -days 365 -out /etc/pki/tls/certs/iktalab. crt
Let's try another way
First, delete the public key and private key just configured
rm -rf /etc/pki/tls/private/iktalab.key rm -rf /etc/pki/tls/certs/iktalab.key
The same way
[root@ikta certs]# openssl genrsa -aes128 2048 > /etc/pki/tls/private/iktalab.key Generating RSA private key, 2048 bit long modulus (2 primes) ...............................................+++++ ......+++++ e is 65537 (0x010001) Enter pass phrase: Do a password verification on the private key Verifying - Enter pass phrase: Private key password verification (password verification is required to load the private key later)
Now that you have the private key, you can export the public key file through the private key
[root@ikta certs]# openssl req -utf8 -new -key /etc/pki/tls/private/iktalab.key -x509 \ -days 365 -out /etc/pki/tls/certs/iktalab.crt Enter pass phrase for /etc/pki/tls/private/iktalab.key: Password required to load private key You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:86 Or just the information you need State or Province Name (full name) []:shannxi Locality Name (eg, city) [Default City]:xi'an Organization Name (eg, company) [Default Company Ltd]:iktalab Organizational Unit Name (eg, section) []:ce Common Name (eg, your name or your server's hostname) []:localhost Email Address []:admin@iktalab.com
[root@ikta certs]# systemctl restart httpd The startup service starts to an encrypted virtual host. To realize encryption authentication, you must load the private key file of the current host Therefore, you must enter a password before starting the service Enter TLS private key passphrase for 192.168.17.200:443 (RSA) : ******
interview:
What basic information do we usually enter when applying for a certificate