The introductory questions on the second page of BUU-CRYPTO are finished. wp is integrated here, and all the questions about RSA are put in another column BUUCTF RSA column_ Xiaohan's blog - CSDN blog , then The problem of sensors is put in (BUU-CRYPTO1 cryptography Xiaobai 25 introductory questions detailed problem solving ideas Xiaohan's blog - CSDN blog
[AFCTF2018]Morse
subject
-.../.----/-.../-.../-.../...–/--.../...-/-.../-.../–.../-.../...–/.----/–.../...–/...—/–.../–.../...-/.../...-./–.../...–/...–/-----/.../...-./...–/...–/...–/...-/...–/.../–.../----./–.../-...
Problem solving ideas
This problem gives a moss code. Just decode it
Attach Code:
import binascii
MorseList = {
".-": "A", "-...": "B", "-.-.": "C", "-..": "D", ".": "E", "..-.": "F", "--.": "G",
"....": "H", "..": "I", ".---": "J", "-.-": "K", ".-..": "L", "--": "M", "-.": "N",
"---": "O", ".--.": "P", "--.-": "Q", ".-.": "R", "...": "S", "-": "T",
"..-": "U", "...-": "V", ".--": "W", "-..-": "X", "-.--": "Y", "--..": "Z",
"-----": "0", ".----": "1", "..---": "2", "...--": "3", "....-": "4",
".....": "5", "-....": "6", "--...": "7", "---..": "8", "----.": "9",
".-.-.-": ".", "---...": ":", "--..--": ",", "-.-.-.": ";", "..--..": "?",
"-...-": "=", ".----.": "'", "-..-.": "/", "-.-.--": "!", "-....-": "-",
"..--.-": "_", ".-..-.": '"', "-.--.": "(", "-.--.-": ")", "...-..-": "$",
".-...": "&", ".--.-.": "@", ".-.-.": "+", "": "",
}
c = "-..../.----/-..../-..../-..../...--/--.../....-/-..../-..../--.../-.../...--/.----/--.../...--/..---/--.../--.../....-/...../..-./--.../...--/...--/-----/...../..-./...--/...--/...--/....-/...--/...../--.../----./--.../-.."
flag = ''
L = c.split('/')
for i in L:
flag += MorseList[i]
flag = binascii.unhexlify(flag)
print(flag) #afctf{1s't_s0_345y}
Operation results
afctf{1s't_s0_345y}
Of course, it should be changed to the format specified by BUUCTF
flag
flag{1s't_s0_345y}
Cipher(playfair encryption)
subject
What else can you suggest? Play fair (find the key yourself) Dncnoqqfliqrpgeklwmppu note: please pack the flag {} submitted, flag {lowercase}
Problem solving ideas
Seeing the ciphertext, the first reaction was Caesar encryption, and then tried Caesar enumeration
However, the results under all offsets did not show the correct answer
Put it again https://quipqiup.com/ I tried blasting, but it was still wrong
I didn't find any ideas from the topic, so I learned a wave online
It is found that there is an encryption method called playfair encryption, which is a multi table substitution encryption. Here is the decryption website:
http://rumkin.com/tools/cipher/playfair.php
This encryption requires a key. The title says to find the key yourself. The key is in "play fair", which is also playfair
Decrypt to get it is not a problem havefun
Of course, according to the requirements of the topic, it must be converted into lowercase letters
flag
flag(itisnotaproblemhavefun)
Knowledge points
Playfair algorithm
Playfair algorithm is one of the most famous multi table substitution encryption methods. It belongs to the classical symmetric encryption method. It was invented by British scientist Charles W in 1854. For a long time, Playfair algorithm was considered as an unbreakable encryption method. Its encryption idea is widely used in network security, data encryption and so on. Playfair cipher is an encryption algorithm that takes the two letter syllable in plaintext as a unit and converts it into ciphertext. The available letter pairs of the original algorithm are 26 × 26, although it has a slightly flat frequency distribution curve than the plaintext, the ciphertext still reveals a lot of information to the cryptanalysis.
Playfair algorithm takes the double letters in plaintext as a unit and converts them into the double letters of ciphertext. The conversion is based on 5 × 5 letter matrix.
1. Prepare password table
Compile a 55 password table with 5 lines and 5 columns of letters. The first column (or row) is the key, and the rest are in alphabetical order. If the key is too long, it can occupy the second column or row. The key is a word or phrase. If there are repeated letters, the repeated letters can be removed. Of course, the least frequently used letters should also be removed (it is written according to a cipher table composed of 55 squares. There are 25 letters in the cipher table. If there are more than 25 letters in a language, the one with the least frequency of use can be removed. For example, w or k is generally removed in French, i and j are regarded as one parent in German, and z is the least used in English, so it can be removed.).
Key: shiyanb programmable
[the external chain image transfer fails. The source station may have an anti-theft chain mechanism. It is recommended to save the image and upload it directly (img-uqd2zplc-1626311445535) (C: \ users \ xiao_han \ appdata \ roaming \ typora \ user images \ image-202107085831130. PNG)]
2. Sort out plaintext / ciphertext, and form a pair of plaintext / ciphertext every two letters. If there are two identical letters next to each other after pairing or the last letter is single, insert a letter X (or Q).
Ciphertext: KQSAMFPAOPMFPA
KQ SA MF PA OP MF PA
3. Decryption rules
(1) If C1 and C2 are on the same line, the corresponding plaintext P1 and P2 are the letters close to the left end of C1 and C2 respectively. The last column is regarded as the left of the first column.
(2) If C1 and C2 are in the same column, the corresponding plaintext P1 and P2 are the letters immediately above C1 and C2 respectively. The last line is seen as the top of the first line.
(3) If C1 and C2 are not in the same row and column, P1 and P2 are the letters in the other two corners of the rectangle determined by C1 and C2.
Ciphertext: KQ SA MF PA OP MF PA
Plaintext: dk ay fn ir mo fn ir


4. Encryption rules
(1) If P1 and P2 are on the same line, the corresponding ciphertext C1 and C2 are the letters close to the right end of P1 and P2 respectively. The first column is regarded as the right side of the last column. For example, according to the previous table, fg corresponds to gj and mr corresponds to om
(2) If P1 and P2 are in the same column, the corresponding ciphertext C1 and C2 are the letters immediately below P1 and P2. The first line is considered below the last line. For example, according to the previous table, dk corresponds to kq and ou corresponds to uh
(3) If P1 and P2 are not in the same row and column, C1 and C2 are the letters in the other two corners of the rectangle determined by P1 and P2 (for horizontal replacement or vertical replacement, we should make an appointment in advance, or try by ourselves). For example, according to the previous table, ir corresponds to pa or ap.
from Cryptography notes - playfair password - ILK - blog Park (cnblogs.com)
Da Vinci Code (Fibonacci sequence)
subject
Leonardo da Vinci has always been a controversial painter, scientist... In order to study him, Xiao Ming found the famous Mona Lisa on the Internet. One night, Xiao Ming suddenly saw a string of mysterious numbers from the sky behind the Mona Lisa. By the way, tell Xiao Ming that there is a string of numbers on the windowsill of Da Vinci's house. Xiao Ming found this string of numbers all the way. Please work out this sub question, pro and post (the answer is a string of 32-bit decimal numbers)
Da Vinci's number column hidden in the Mona Lisa: 1 233 3 2584 1346269 144 5 196418 21 1597 610 377 10946 89 514229 987 8 55 6765 2178309 121393 317811 46368 4181 1 832040 2 28657 75025 34 13 17711
Mysterious number string recorded at the window sill of Da Vinci: 36968853882116725547342176952286
Problem solving ideas
This question tests your eyesight
First of all, we should note that there are 32 numbers in the number column. The mysterious string and the answer are 32-bit decimal numbers. There must be a certain relationship between the three
At the same time, comrades who are familiar with the Fibonacci series will find that the numbers in the number series come from the Fibonacci series (I didn't see it anyway, I didn't know it until I learned it online)
1,1,2,3,5,8,13,21,34,...
The number in each number sequence will have a corresponding subscript of the Fibonacci number sequence item. For example, 2 corresponds to the third item and 8 corresponds to the sixth item
According to this, we can sort the number column and transform the corresponding position of the number string to get the flag
Attach Code:
def gen_fibo(n): #Generate a Fibonacci sequence, return a list that included n elements
L = [1]
dp = [0, 1]
for i in range(n - 1):
new = dp[0] + dp[1]
L.append(new)
dp[0] = dp[1]
dp[1] = new
return L
if __name__ == "__main__":
key = "36968853882116725547342176952286"
num_list = "1 233 3 2584 1346269 144 5 196418 21 1597 610 377 10946 89 514229 987 8 55 6765 2178309 121393 317811 46368 4181 1 832040 2 28657 75025 34 13 17711"
L1 = num_list.split(' ')
print(L1)
L2 = gen_fibo(32)
print(L2)
flag = ''
for i in range(32):
flag += key[L1.index(str(L2[i]))]
#The index function will only find the leftmost subscript, and there are two 1s in the sequence, so manually adjust the number corresponding to the second 1
flag = flag[:1] + '7' + flag[2:]
print("flag{" + flag + "}")
There is a small pit. The first two numbers in the Fibonacci series are 1. Therefore, considering the number 7 corresponding to the second 1, it needs to be adjusted manually
flag
flag{37995588256861228614165223347687}
[GXYCTF2019]CheckIn(base64+rot47)
subject
dikqTCpfRjA8fUBIMD5GNDkwMjNARkUwI0BFTg==
Problem solving ideas
The characteristics of this string of characters are like base64. Try it
v)L_F0< }@H0>F49023@FE0#@EN
Note that in the above resu lt s, because < > will match the markdown label and cannot be displayed normally, a space is specially added between < and}, but there is actually no space
The answer is wrong. I tried rabbit coding again, but it didn't work
Learn a wave on the Internet. This channel is encoded twice, and the result of base64 will be decoded again with rot47
Tools website: ROT5, ROT13, ROT18, ROT47 displacement code (qqxiuzi.cn)
GXY{Y0u_kNow_much_about_Rot}
flag
flag{Y0u_kNow_much_about_Rot}
Knowledge points
ROT5, ROT13, ROT18 and ROT47 coding is a simple symbol position sequential replacement code. This kind of coding is reversible and can be self decrypted. It is mainly used to deal with fast browsing or machine reading without understanding its meaning.
ROT5 is the abbreviation of rotate by 5 places, which means to rotate 5 positions, and the others are the same. Here are their coding methods:
ROT5: encode only the number, and replace the current number with the fifth number from the previous number of the current number. For example, the current number is 0, which becomes 5 after coding, 1 after coding, and 6 after coding, and so on.
ROT13: encode only letters. Replace the current letter with the 13th letter from the front of the current letter. For example, if it is currently A, it will become N after coding, if it is currently B, it will become O after coding, and so on.
ROT18: This is a different class. It doesn't exist originally. It combines ROT5 and ROT13. For good name, it is named ROT18.
ROT47: encode numbers, letters and common symbols, and replace their positions according to their ASCII values. Replace the current character with the 47th corresponding character from the previous ASCII value of the current character. For example, the current is lowercase letter z, which becomes uppercase letter K after encoding, and the current is number 0, which becomes symbol. The ASCII value range of characters used for ROT47 coding is 33-126. For details, please refer to ASCII encoding.
Voice of cryptography (binary conversion)
subject
During World War II, an officer of a certain country befriended a musician's mistress. However, since then, he has been defeated repeatedly, and the enemy seems to expect things like God. He also doubted his mistress, but after 24 hours of observation, he found that she only composed music every day, and then played it to the field radio station to cheer up the soldiers. So, who is the spy? Is this score fishy?
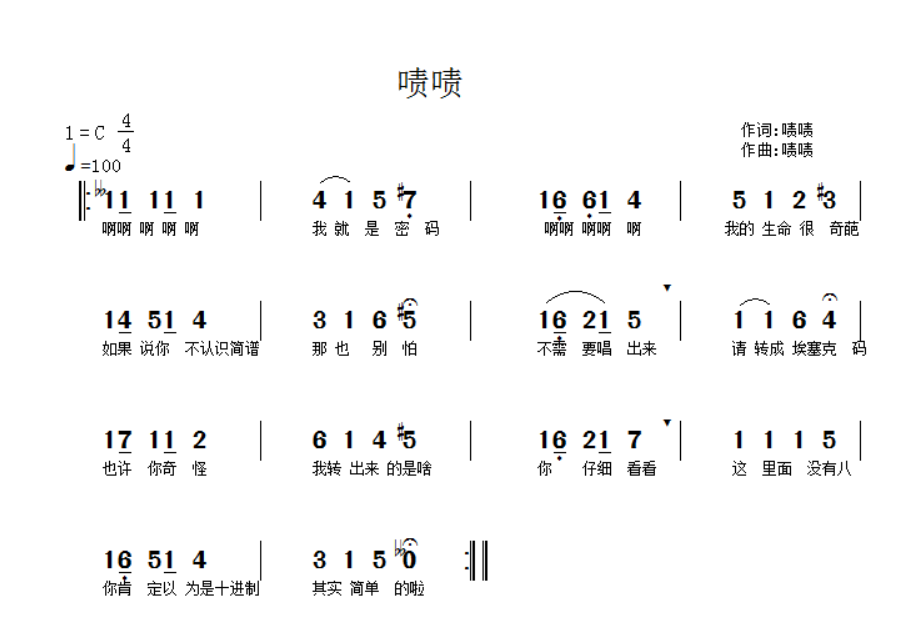
I thought I would give a Morse audio without looking at the score, but I gave a picture of the score
The lyrics are obvious:
Please change to essek code
There are no eight in it
The previous point explained that the number should be converted into Ascll code text, and told that it is octal
Attach Code:
Decryption with one line of code
ctext = '111114157166145123145143165162151164171126145162171115165143150'
print('falg{'+''.join(chr(int(ctext[i*3:(i+1)*3], 8)) for i in range(len(ctext)//3))+'}')
The following code helps you understand, and the function is the same as above
ctext = '111114157166145123145143165162151164171126145162171115165143150'
flag = ''
for i in range(len(ctext)//3):
c = ctext[i*3:(i+1)*3] #Every three digits corresponds to one ascll character
flag += chr(int(c, 8))
print('flag{' + flag + '}')
Note that the conversion is done in groups of three
flag
flag{ILoveSecurityVeryMuch}
What is this?? (64)
subject
dic = {0: 'J', 1: 'K', 2: 'L', 3: 'M', 4: 'N', 5: 'O', 6: 'x', 7: 'y', 8: 'U', 9: 'V', 10: 'z', 11: 'A', 12: 'B', 13: 'C', 14: 'D', 15: 'E', 16: 'F', 17: 'G', 18: 'H', 19: '7', 20: '8', 21: '9', 22: 'P', 23: 'Q', 24: 'I', 25: 'a', 26: 'b', 27: 'c', 28: 'd', 29: 'e', 30: 'f', 31: 'g', 32: 'h', 33: 'i', 34: 'j', 35: 'k', 36: 'l', 37: 'm', 38: 'W', 39: 'X', 40: 'Y', 41: 'Z', 42: '0', 43: '1', 44: '2', 45: '3', 46: '4', 47: '5', 48: '6', 49: 'R', 50: 'S', 51: 'T', 52: 'n', 53: 'o', 54: 'p', 55: 'q', 56: 'r', 57: 's', 58: 't', 59: 'u', 60: 'v', 61: 'w', 62: '+', 63: '/', 64: '='}
ciphertext= "FlZNfnF6Qol6e9w17WwQQoGYBQCgIkGTa9w3IQKw"
Problem solving ideas
The title gives a 64 bit mapping table, which is obviously a deformation of base64
It can be decrypted by imitating base64 encryption
Attach Code:
import binascii
#The encryption method is base64, but the mapping relationship is changed
dic = {0: 'J', 1: 'K', 2: 'L', 3: 'M', 4: 'N', 5: 'O', 6: 'x', 7: 'y', 8: 'U', 9: 'V', 10: 'z', 11: 'A', 12: 'B', 13: 'C', 14: 'D', 15: 'E', 16: 'F', 17: 'G', 18: 'H', 19: '7', 20: '8', 21: '9', 22: 'P', 23: 'Q', 24: 'I', 25: 'a', 26: 'b', 27: 'c', 28: 'd', 29: 'e', 30: 'f', 31: 'g', 32: 'h', 33: 'i', 34: 'j', 35: 'k', 36: 'l', 37: 'm', 38: 'W', 39: 'X', 40: 'Y', 41: 'Z', 42: '0', 43: '1', 44: '2', 45: '3', 46: '4', 47: '5', 48: '6', 49: 'R', 50: 'S', 51: 'T', 52: 'n', 53: 'o', 54: 'p', 55: 'q', 56: 'r', 57: 's', 58: 't', 59: 'u', 60: 'v', 61: 'w', 62: '+', 63: '/', 64: '='}
ciphertext= "FlZNfnF6Qol6e9w17WwQQoGYBQCgIkGTa9w3IQKw"
mtext = ''
for i in ciphertext:
key = list(dic.values()).index(i) #Dictionary keys are sorted the same as index values
mtext += bin(key)[2:].zfill(6) #Fill the six digit length with 0
mtext = (int(mtext, 2))
flag = binascii.unhexlify(hex(mtext)[2:])
print(flag)
Operation results:
b'BJD{D0_Y0u_kNoW_Th1s_b4se_map}'
flag
flag{D0_Y0u_kNoW_Th1s_b4se_map}
rot(rot13+MD5 blasting)
subject
83 89 78 84 45 86 96 45 115 121 110 116 136 132 132 132 108 128 117 118 134 110 123 111 110 127 108 112 124 122 108 118 128 108 131 114 127 134 108 116 124 124 113 108 76 76 76 76 138 23 90 81 66 71 64 69 114 65 112 64 66 63 69 61 70 114 62 66 61 62 69 67 70 63 61 110 110 112 64 68 62 70 61 112 111 112
Problem solving ideas
The rot code is rot13 by comparing "83 89 78 84" and "70 76 65 71"(FLAG)
After offset 13, turn to Ascll code
Attach Code:
ctext = "83 89 78 84 45 86 96 45 115 121 110 116 136 132 132 132 108 128 117 118 134 110 123 111 110 127 108 112 124 122 108 118 128 108 131 114 127 134 108 116 124 124 113 108 76 76 76 76 138 23 90 81 66 71 64 69 114 65 112 64 66 63 69 61 70 114 62 66 61 62 69 67 70 63 61 110 110 112 64 68 62 70 61 112 111 112"
ctext = ctext.split(' ')
flag = ''
for i in ctext:
flag += chr(int(i)-13)
print(flag)
Operation results
FLAG IS flag{www_shiyanbar_com_is_very_good_???}
MD5:38e4c352809e150186920aac37190cbc
I thought the answer was flag{www_shiyanbar_com_is_very_good}, However, it was found that there was something wrong after submission
After seeing the flag, there are four?, MD5 values are given below
It is speculated that MD5 blasting may be performed on the last four characters
Attach Code:
import hashlib
def md5(key):
input_name = hashlib.md5()
input_name.update(key.encode("utf-8"))
return(input_name.hexdigest())
def solve(MD5):
for a in range(32,127):
print(chr(a))
for b in range(32,127):
for c in range(32,127):
for d in range(32,127):
flag = "flag{www_shiyanbar_com_is_very_good_" + chr(a)+chr(b)+chr(c)+chr(d) + "}"
if md5(flag) == MD5:
return flag
flag = "flag{www_shiyanbar_com_is_very_good_????}"
MD5 = "38e4c352809e150186920aac37190cbc"
print(solve(MD5))
Because it runs in one minute, there is no need for parallel optimization
flag
flag{www_shiyanbar_com_is_very_good_@8Mu}
[nctf2019] keyboard (keyboard sequence)
subject
ooo yyy ii w uuu ee uuuu yyy uuuu y w uuu i i rr w i i rr rrr uuuu rrr uuuu t ii uuuu i w u rrr ee www ee yyy eee www w tt ee
Problem solving ideas
The clue to this question is the keyboard keyboard, and then it is found that the ciphertext is the letter on the first line of the keyboard, with its corresponding number on it
Then go to the nine key keyboard. Several letters represent the first few letters in the nine key Pinyin
Spit a slot, the brain hole is very big, very people can solve the problem
Attach Code:
ctext = "ooo yyy ii w uuu ee uuuu yyy uuuu y w uuu i i rr w i i rr rrr uuuu rrr uuuu t ii uuuu i w u rrr ee www ee yyy eee www w tt ee"
ctext = ctext.split(' ')
key_26 = 'qwertyuiop'
key_9 = {2:'abc',3:'def',4:'ghi',5:'jkl',6:'mno',7:'pqrs',8:'tuv',9:'wxyz'}
flag = ''
for i in ctext:
key = key_26.index(i[0])+1
num = len(i)
flag += key_9[key][num-1]
print(flag)
Operation results
youaresosmartthatthisisjustapieceofcake
flag
flag{youaresosmartthatthisisjustapieceofcake}
What is this (jsluck code)
subject
Xiao Ming is a top student majoring in software, but the homework assigned by the teacher doesn't seem to be very reliable, because their teacher used to study physics! I like messy named files and strange coding. Please help Xiao Ming look at this question. Xiao Ming has prepared a box of spicy strips
Give an APK file: 94f5b952-3710-4609-ab6f-bc11609fdc67 apk
Problem solving ideas
Open the file (Notepad or change the suffix to txt) and you can see that there is a section in it, which is obviously jsluck coding
[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+(![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+!+[]]]+(![]+[])[+!+[]]+[+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]]+([][[]]+[])[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+[+[]]+(+(+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+[]])+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[+[]]+[!+[]+!+[]]+[+[]]+[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(![]+[])[+!+[]]+[!+[]+!+[]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]])+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]])()
You can decode it on the jsluck tool website: Jsluck - Online encryption and decryption (bugku.com)
Click Run This and a pop-up window will display flag
In fact, many browsers support jsluck coding. Open the browser, press F12, paste the jsluck code in the console, and press enter. The browser will automatically parse and execute, and the pop-up window will get the flag
flag
flag{a0448fd730b62c13ca80200c4529daa2}
Knowledge points
Jsluck encoding method
- false => ![]
- true => !![]
- undefined => [][[]]
- NaN => +[![]]
- 0 => +[]
- 1 => +!+[]
- 2 => !+[]+!+[]
- 10 => [+!+[]]+[+[]]
- Array => []
- Number => +[]
- String => []+[]
- Boolean => ![]
- Function => []["filter"]
- eval => []["filter"]["constructor"]( CODE )()
- window => []["filter"]["constructor"]("return this")()
Note: in order not to be parsed into markdown syntax, an escape character is added here\
[MRCTF2020] what do you know about classical passwords
subject
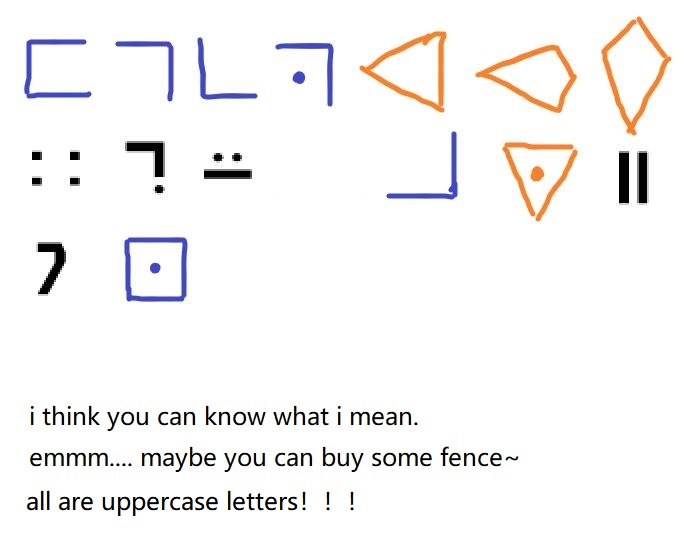
Problem solving ideas
This question tests whether you master enough classical passwords. It is obvious that the front is the pigsty password, and the latter should be similar graphic passwords.
Here's a reference CTF essential password code_ Yanlian Hanlin blog - CSDN blog , the coding method inside is very complete
Then it can be seen that the pigsty code, standard Galaxy letter, Templar Code and pigsty code variants are used in the picture
Pigpen cipher
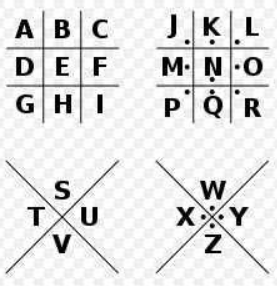
Standard Galaxy letter
Templar Code

Check the password table to get:
fgcpflirtuasyon
Then there are hints under the title
- Fence: fence password
- uppercase: flag should be capitalized
It is obtained by encrypting the number of fence password columns to 5
flagiscryptofun
flag
flag{CRYPTOFUN}
[WUSTCTF2020] Buddha said: only four days
subject
Ciphertext:
A person's mind is silent. I've had to deal with the situation. The way to fix a situation. A woman's body is a great way to be strict. There's a lot of money. There's a lot of people. There's a way to have a good idea. It's a great way to be a monk. It's a way to be quiet. It's a great way to be a monk. It's a great way to be a monk. It's a great way to be a monk. It's a great way to be a monk. The way to fix a situation. The way to be a great way to deal. A person's a great way to deal. Being strict. It's a good idea. There's a lot of people. There's a good way to have a good idea. What's going to be. What's the way to be. What's the way to be. The way to make a person. It's going to be a vowvow to be a vow to fix a vow. A mantmantmantbowl It's a great idea to get a dhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhadhato beat It's a big problem. It's a big problem. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's a big one. It's long life Na Yi also heart also Nan, if curse life also life order
Title Description:
The Bible is divided into the Old Testament and the New Testament
Tips:
- Although it's not environmentally friendly, hint seems to be one-off and has no use value after getting it.
- Caesar is not the last step, by the way, why is Caesar called Caesar?
Problem solving ideas
First thought Buddhism and Zen code , but decryption failed
According to the tips, the Bible is divided into the Old Testament and the faith Testament. Find one New Testament Buddhism on Zen / Buddhism on encryption - PcMoe!
Just as "Buddha said:" should be added in front of Buddhism and Zen, here "new Buddha said:" should be added in front of it. Then decrypt it and get the solution
Equality, civilization, freedom, friendliness, justice, freedom, integrity, prosperity, freedom, equality, democracy, equality, freedom, friendliness, professionalism, equality, justice, equality, prosperity, equality, freedom, equality, democracy, harmony, justice, equality, justice, freedom, justice, equality, rule of law, rule of law, harmony, harmony, equality, freedom, freedom, harmony, justice Harmonious civilization freedom harmony freedom harmony equality harmony rule of law justice integrity equality justice integrity democracy freedom harmony justice democracy equality equality equality freedom harmony harmony equality harmony freedom integrity equality harmony freedom friendship dedication equality harmony freedom friendship friendship respect industry equality rule of law freedom rule of law harmony freedom friendship justice dedication justice friendship patriotism justice Democracy, rule of law, civilization, freedom, democracy, equality, justice, freedom, rule of law, equality, civilization, equality, friendliness, freedom, equality, civilization, freedom, democracy, equality, respect, freedom, harmony, friendliness, freedom, equality, friendliness, respect, justice, integrity, prosperity, friendliness, respect, justice, integrity, equality, integrity, equality, freedom, justice, integrity, equality, rule of law, respect, integrity, equality, rule of law, equality Justice, friendliness, equality, justice, integrity, freedom, justice, friendliness, professionalism, rule of law, justice, justice, equality, integrity, freedom, justice, harmony, justice, equality
Obviously, it is the code of socialist core values: Code of core values - Bugku CTF , solution
RLJDQTOVPTQ6O6duws5CD6IB5B52CC57okCaUUC3SO4OSOWG3LynarAVGRZSJRAEYEZ_ooe_doyouknowfence
Fence is the fence password. The following prompt should be removed here
RLJDQTOVPTQ6O6duws5CD6IB5B52CC57okCaUUC3SO4OSOWG3LynarAVGRZSJRAEYEZ_ooe
The fence password is obtained by enumeration and decryption
R5UALCUVJDCGD63RQISZTBOSO54JVBORP5SAT2OEQCWY6CGEO53Z67L_doyouknowCaesar
Then go to Caesar encryption, but try Caesar shift. The results are also garbled. It also suggests that Caesar is not the last step
It is observed that there are only capital letters A-Z and numbers 2-7 in the previous results, so the guess is base32
Then try Caesar enumeration + base32. The following prompt is also removed here
R5UALCUVJDCGD63RQISZTBOSO54JVBORP5SAT2OEQCWY6CGEO53Z67L
However, there is a pit, which may not meet the requirements of base32 alignment and needs to be filled '='
Attach Code:
import string
import base64
def kaisa(s, k): #The definition function accepts a string s and an offset k
lower = string.ascii_lowercase #Lowercase letters
upper = string.ascii_uppercase #capital
before = string.ascii_letters #Alphabetical order without offset lowercase + uppercase
after = lower[k:] + lower[:k] + upper[k:] + upper[:k]#Is the offset alphabetical order lowercase + uppercase
#Offset the lower case and upper case letters respectively and add them together
table = ''.maketrans(before, after) #Create mapping table
return s.translate(table) #Offset s, i.e. encrypt
def solve(cipher):
for i in range(26): #Enumerate Caesar
caesar = kaisa(c, i)
for j in range(5): #Fill '='
try:
caesar = caesar + "="*j
flag = str(base64.b32decode(bytes(caesar, encoding = "utf8")))
if "{" in flag and "}" in flag:
print(flag)
except:
continue
if __name__ == "__main__":
c = "R5UALCUVJDCGD63RQISZTBOSO54JVBORP5SAT2OEQCWY6CGEO53Z67L"
solve(c)
Operation results
b'\x97j\x16\x0e\xb6Q\x06r{r\x8af\n\t\xf3\x7fx\xab\t\xf2\x87f\x1ai\xe5\x88\xef\x9f\x0c\xe5\x7fv\x0f}'
b"\xa7n7\x16\xf8a\x8a\x93{t\x9a\xea+\x125\x8fx\xcc\x124\x97j;j'\x99r\x1f\x15'\x8fv/}"
b'wctf2020{ni_hao_xiang_xiang_da_wo}'
b'\x87g\x95\x06t@\x82Q{py\xe3\x89\x01\xb1ox\x8a\x01\xb0wc\x99i\xa3xk\x7f\x04\xa3ow\x8f}'
flag
flag{ni_hao_xiang_xiang_da_wo}
[MRCTF2020] tiangan dizhi + Jiazi
subject
The obtained string is wrapped in MRCTF {}
One day Eki received a letter from Sndav, but he was a little confused. I hope you can solve it
Jiaxu, Jiayin, Jiayin, guimao, Jiyou, Jiayin, Xin Chou
Problem solving ideas
And the previous question Traditional knowledge + classical password It's the same, or even simpler. First check the tiangan and dizhi table:
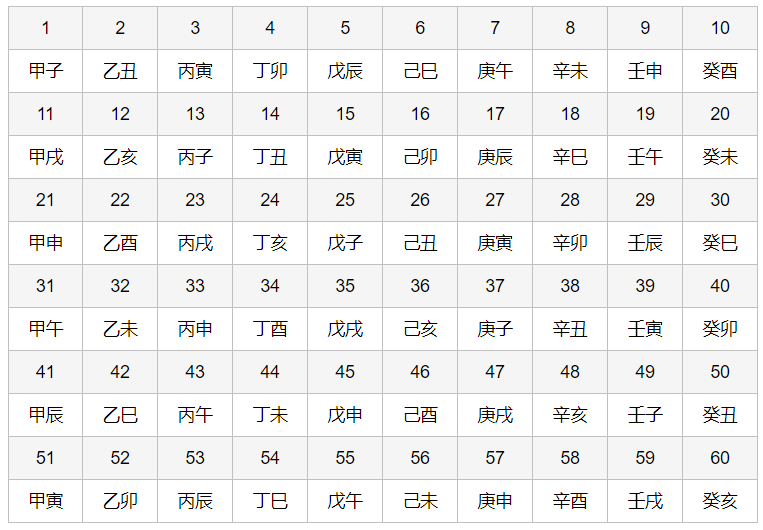
convert to
11 51 51 40 46 51 38
Then the same + a (60)
71 111 111 100 106 111 98
Then convert it to Ascll code
Goodjob
flag
flag{Goodjob}
[MRCTF2020]vigenere
subject
Ciphertext: an article composed of disorderly English characters is given
vigenere.py:
#!/bin/python3
from ctf import source_text, key_string
getdiff = lambda char: ord(char)-ord('a')
getchar = lambda num: chr(ord('a')+num)
def vigenere(src: chr, key: chr) -> chr:
assert(src.isalpha() and key.isalpha())
return(getchar((getdiff(src) + getdiff(key) + 1) % 26))
src = source_text.lower()
count = 0
assert(len(key_string) > 5 and len(key_string) < 10)
for i in src:
if(i.isalpha()):
print(vigenere(i, key_string[count % len(key_string)]), end='')
count+=1
else:
print(i, end='')
Problem solving ideas
According to the meaning of the code, it can be seen that it is the Virginia password, which corresponds to the title
Don't know the key, blow it up directly on the website Vigenere Solver - www.guballa.de
Select a key with a length of 6-9 and burst the get flag!
The last sentence in the result is as follows, indicating that underline and curly braces should be added:
flag is mrctf vigenere crypto crack man, please add underscore and curly braces.
flag
flag{vigenere_crypto_crack_man}
[mrctf2020] keyboard
subject
6
666
22
444
555
33
7
44
666
66
3
Problem solving ideas
From the title, it should be similar to the previous [nctf019] keyboard and simpler
Solve the problem with the keyboard sequence. The number represents the number corresponding to the nine key keyboard. Repeated several times is the first letter on the key
Attach Code:
ctext = ['6','666','22','444','555','33','7','44','666','66','3']
key_9 = {2:'abc',3:'def',4:'ghi',5:'jkl',6:'mno',7:'pqrs',8:'tuv',9:'wxyz'}
flag = ''
for i in ctext:
key = int(i[0])
num = len(i)
flag += key_9[key][num-1]
print(flag)
Operation results
mobilephond
However, if you submit the flag, you will find that the answer is wrong
There is a big hole here. The title should be wrong. The flag is not mobile phone, but mobile phone
Try to correct its spelling mistakes and get the correct answer, but
Lu Xun said, "this is outrageous."
flag
flag{mobilephone}
[bjdctf2020] sign in
subject
welcome to crypto world!!
Ciphertext: 424a447b57653163306d655f743454467d
Problem solving ideas
Looking at the title, I thought it was a digital signature. I thought it was some kind of hash value. The attempt to decrypt online failed
Once again, it's Ascll printable characters. Turn it directly and get flag!
Attach Code:
import binascii
m = int("424a447b57653163306d655f74345f424a444354467d", 16)
flag = binascii.unhexlify(hex(m)[2:])
print(flag)
flag
flag{We1c0me_t4_BJDCTF}
A spy report (single table replacement)
subject
After sending undercover agents to spy for a long time, the national energy headquarters finally found a long-standing foreign Insider: Lao Wang, manager of the energy building on the third floor. Due to the hasty arrest, Lao Wang took poison and killed himself. The investigation department found that the newspaper Lao Wang read every day turned out to be special intelligence. Smart, can you find information from the attached newspaper? flag is the code that Lao Wang said. (because Lao Wang's informant used to be a bandit, he used jargon)
Look at the last paragraph of the espionage
Meow, woo, moo, Ji, double wow top, sleeping bird fart, eight wow report, all Ji, sleeping bird enters the grass in the North brain, eight branches meet Sun Ji, Sun Ji pair boil and weave leaves: it's time to put birds on clothes and catch monkey top. Bird pair: North Wang Luohan Fu boils chaotic Tianmen. Joint editing release, card editing pull call. People leave to burn grass and report to the cave. Sun Ji looks for Grandpa.
Here is jargon, so how to convert it into plaintext
The two paragraphs are almost the same, but some words have been replaced. These words happen to be the jargon in the ciphertext
Therefore, we can find out the corresponding relationship between plaintext and jargon and write a script to solve it
Attach Code:
# -*- coding: utf-8 -*
src = "This morning, the Bangzi company of Chaoge district decided to set up cards at the gates of all districts at night every day for free to provide the whole city with two deafening reminders, calling on everyone to go to bed and get up early. Don't ruin a good life because of sleepiness. The symbol of the times is progress. To this end, the old people in the whole area squatted in the trees in the east of the company and resisted with joint efforts. They didn't let the company's personnel go. The scene was chaotic. Li Luoying has lived in Chaoge district for 50 years. He is called the eagle head. A few years ago, his grandson Li Hunan just came back from the northeast as a hunter and sent back several pieces of dried moles every month. The wife Li Luoying met was a flower of Chaoge, so Li Nanhu was a very delicate man. Li Luoying said: no matter what Bangzi company did right or wrong, we can't disturb his grandson's sleep anyway. Confucius said:'Sleeping is human nature'. Bangzi company doesn't even let Bodhisattva sleep. Li Nanhu said: Bangzi company's IQ is urgent, be careful of residents jumping off the wall! I don't sleep in dog days. Isn't that bullshit! By noon, the crowd had not dispersed, and some people proposed to burn down the company. The top management of the company seemed eager to find a hole to drill in. It was not until the security personnel appeared that they evacuated the crowd home, but Li Nanhu still said that grandpa was old and it was bad for his health if he couldn't sleep well."
dst = "In the morning of meow day, mooji company in Wangge district decided to set up cards in the door and brain of all districts for free in eight wow days every day, provide deafening knock reminder for the whole city, and call on everyone to go to bed and get up early. Don't ruin a good life because of sleepiness. The number of the times is forward. To this end, all the sleepers in the region joined forces in the grass at the edge of the company to resist and did not release the company's personnel. The scene was chaotic. Li luoniao has lived in Wangge district for 50 years. He is known as sleeping bird top. In recent years, Sun Ji and Li Nao have just returned from Liubei as fart households. They also send back several pieces of news every month. The sleeping woman Li luoniao met was a flower of Wang Ge, so Li guanao was a very delicate Han Ji. Li luoniao said: no matter what mooji company did right or wrong, we can't disturb his Sun Ji's sleep anyway. Jiye:'Sleeping is human nature'. Moo Ji company doesn't even let go of clothes and sleep. Li guanao said: moo Ji company IQ catch urgent, be careful of residents jumping off the wall! I don't sleep in dog days. Isn't that bullshit! By noon, the crowd had not dispersed. Wow, someone proposed to burn down the company. The top management of the company seemed eager to find a hole to drill in. It was not until the security personnel appeared that they evacuated the crowd home, but Li guanao still said that grandpa was old and it was bad for his health if he couldn't sleep well."
c = "Meow, woo, moo, Ji, double wow top, sleeping bird fart, eight wow report, all Ji, sleeping bird enters the grass in the North brain, eight branches meet Sun Ji, Sun Ji pair boil and weave leaves: it's time to put birds on clothes and catch monkey top. Bird pair: North Wang Luohan Fu boils chaotic Tianmen. Joint editing release, card editing pull call. People leave to burn grass and report to the cave. Sun Ji looks for Grandpa."
m = ''
for i in c:
index = dst.index(i)
print(src[index], end = '')
Operation results
At present, the Bangzi's second watch, the eagle squats and hunts at the east entrance, the mole breaks the Liangzi at the east entrance at the third watch, the eagle enters the north entrance and goes up the tree, and the third branch meets his grandson. The grandson says to the tiger talisman: the South sky Bodhisattva releases the eagle to catch the monkey head. Eagle pair: the northern arhat subdued the tiger and disordered the Tianmen gate. Compliance release, card symbol pull call. People leave the burning tree, the mole returns to the cave, and the grandson looks for Grandpa.
There are two passwords in the ciphertext. After trying, I found that the sentence "Nantian Bodhisattva puts an eagle to catch a monkey head" is a flag
flag
flag {Nantian Bodhisattva set eagle to catch monkey head}
Yxx (exclusive or processing)
subject
Gave plaintext txt and ciphertext txt, including ciphertext txt is a random code composed of non printable characters, plaintext txt is "lovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelovelove
Problem solving ideas
First convert the data into hexadecimal to have a look
m1 = 0a031702560115110a140e0a1e300e0a1e300e0a1e30140c190d1f100e060318
m2 = 6c6f76656c6f76656c6f76656c6f76656c6f76656c6f76656c6f76656c6f7665
Note that the bytes in m1 are relatively small. After arithmetic operation with m2, they should still be within the range of ascll printable characters
After trying common operations, get flag after XOR is found!
Attach Code:
with open("ciphertext.txt", 'rb') as f1:
m1 = f1.read().hex()
with open("Plaintext.txt", 'rb') as f2:
m2 = f2.read().hex()
length = len(m1)
mtext = ''
for i in range(length//2):
c1 = int(m1[i*2:(i+1)*2], 16)
c2 = int(m2[i*2:(i+1)*2], 16)
mtext += chr(c2^c1) #Byte by byte XOR
print(mtext)
Operation results
flag:nctf{xor_xor_xor_biubiubiu}
flag
flag{xor_xor_xor_biubiubiu}