How to build an enterprise CA certificate server?
Define system environment: CentOS 7.4
ca.com 192.168.80.181 openssl*
mail.com 192.168.80.182 dovecot*
client.com 192.168.80.183 mutt*
Modify three host names:
①hostnamectl set-hostname xx.com
exit logout
Reconnect
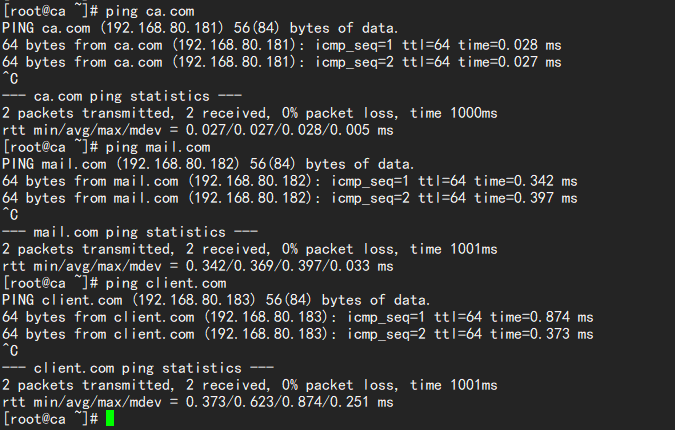
② vi /etc/hosts
192.168.80.181 ca.com
192.168.80.182 mail.com
192.168.80.183 client.com
----The following is configured on the CA server side -- IP: 192.168.80.181
systemctl stop firewalld && setenforce 0 //Turn off firewall and selinux
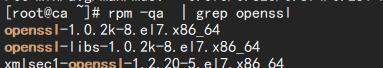
Confirm that openssl software is installed
rpm -qa | grep openssl
vi /etc/pki/tls/openssl.cnf openssl Profile of the service
[ CA_default ] Values issued for other serversdir = /etc/pki/CA working directory # Where everything is kept(Preservation)
certs = $dir/certs Issued certificate # Where the issued(Issuer) certs are kept
crl_dir = $dir/crl Revoked certificate # Where the issued crl are kept
database = $dir/index.txt Index file # database index file.
new_certs_dir = $dir/newcerts New certificate # default place for new certs.certificate = $dir/cacert.pem Root certificate # The CA certificate
serial = $dir/serial serial number # The current serial number
crlnumber = $dir/crlnumber # the current crl number
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
RANDFILE = $dir/private/.rand # private random number filex509_extensions = usr_cert # The extentions to add to the cert
---Modify the following configuration----
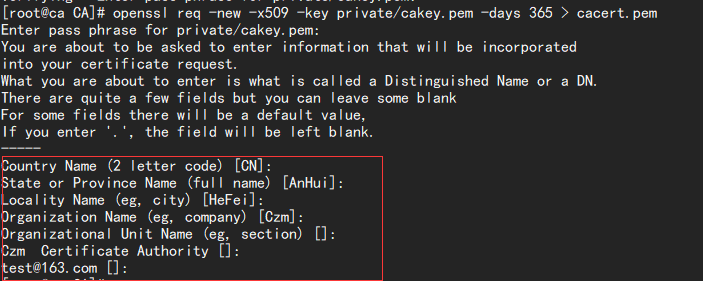
[ req_distinguished_name ] //L128countryName //Country name = Country Name (2 letter code)
countryName_default //Default country = CNstateOrProvinceName //Detailed address = State or Province Name (full name)
stateOrProvinceName_default = AnHuilocalityName = Locality Name (eg, city)
localityName_default = HeFeicommonName = Czm Certificate Authority
commonName_max = 64emailAddress = test@126.com
emailAddress_max = 64
(Save exit)
cd /etc/pki/CA/
(Define certificate version)
echo 01 > serial //Certificate file
touch index.txt //Create a new index file and put it on the Internet for others to download
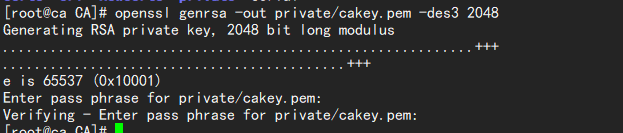
openssl genrsa -out private/cakey.pem -des3 2048 //Password is required to generate private key
openssl req -new -x509 -key private/cakey.pem -days 365 > cacert.pem //The above password confirmation information is required to generate the root certificate
yum install httpd //Share through WWW server
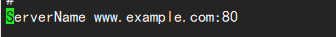
vi /etc/httpd/conf/httpd.conf
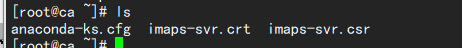
cp /etc/pki/CA/cacert.pem /var/www/html/ //Publish the root certificate
cd /var/www/html/
mv cacert.pem ROOTCA.pem
systemctl start httpd
------The following is configured on the mail server: IP:192.168.80.182
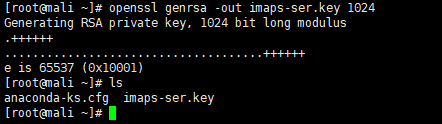
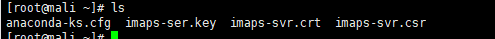
openssl genrsa -out imaps-ser.key 1024 //Generate private key file
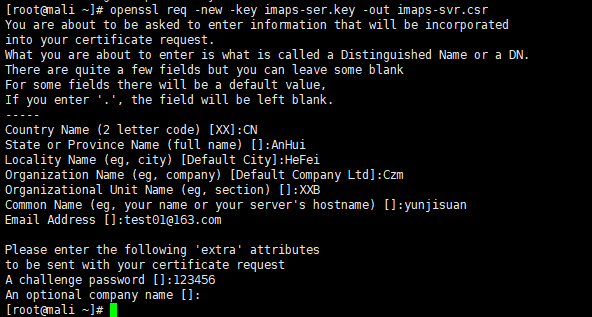
openssl req -new -key imaps-ser.key -out imaps-svr.csr //Generate signature request file to be the same as CA
scp imaps-svr.csr root@192.168.80.181:/root/ //Send signature request file to CA server
--------Do the following on CA---------
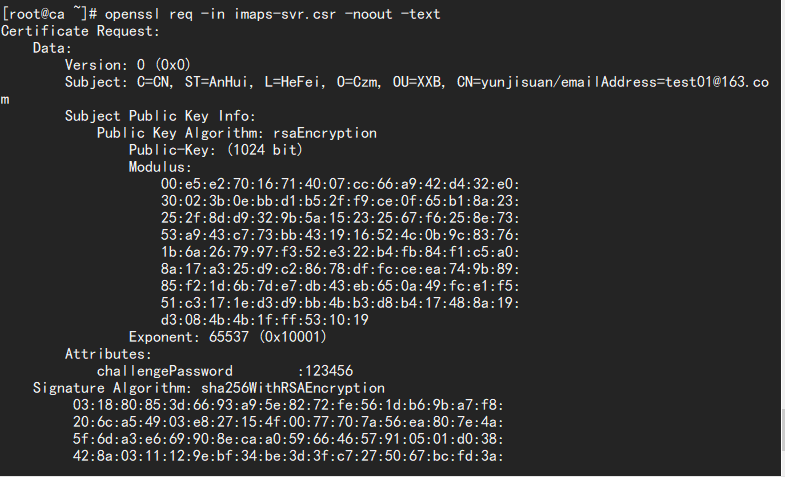
openssl req -in imaps-svr.csr -noout -text //View the contents of an imaps-svr.csr as text
openssl ca -in imaps-svr.csr -out imaps-svr.crt //Generate certificate for client, answer Y for all
scp imaps-svr.crt root@192.168.80.182:/root //Deliver certificate to client
-------Do the following on the mail server------
yum install dovecot -y
vi /etc/dovecot/dovecot.conf
//L24
//L30
ssl = yes //Last line, new
cp imaps-svr.crt /etc/ssl/certs/dovecot.pem //Put the digital certificate in the specified location
mkdir /etc/ssl/private
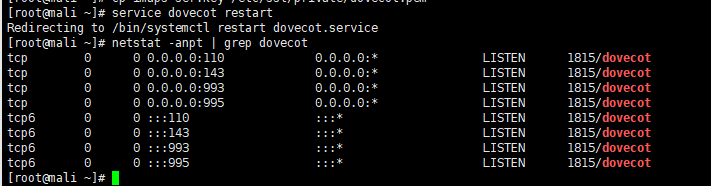
cp imaps-ser.key /etc/ssl/private/dovecot.pem //Place the private key in the specified locationservice dovecot restart
netstat -anpt | grep dovecot //993 and 995 are monitoring
-----------Test on the user side as follows: IP: 192.168.80.183
yum install mutt
mkdir .mutt
cd .mutt
vi muttrc
set folder=imaps://mail.com
set spoolfile=imaps://mail.com
set certificate_file=/root/.mutt/testca.CRT
-------Do the following on the mail server------
yum install httpd -y
yum install mod_ssl -y
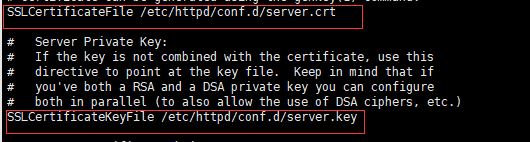
cp /etc/ssl/certs/dovecot.pem /etc/httpd/conf.d/server.key
cp /etc/ssl/private/dovecot.pem /etc/httpd/conf.d/server.crt
vi /etc/httpd/conf.d/ssl.conf
start-up httpd service
Test in browser: https://192.168.80.182

Add exception
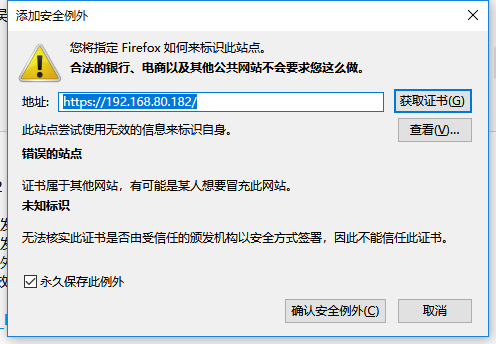
Confirm safety exception
ok