Install audit
The audit package is installed in Centos8 by default. If not installed, use the following command to add:
[root@localhost ~]# yum -y install audit
Audit configuration file / etc/audit/auditd.conf. This file contains default parameters to change the behavior of the auditd daemon.
Management audit services
After configuring auditd, start the service to collect audit information:
# service auditd start
The only reason to use the service command instead of systemctl is to record the user ID (UID) value correctly.
Set startup:
# systemctl enable auditd
Define audit rules
Using the auditctl tool, you can add audit rules to any system call you want. The rules are executed sequentially.
Next, define the monitoring rules. This rule tracks whether a file or directory is triggered by certain types of access, including read, write, execute, and property changes.
The syntax for defining rules is:
auditctl -w path_to_file -p permissions -k key_name
To audit user creation operations, first add monitoring to the / etc/passwd file to track write and attribute change access, and add a custom key to record all messages (this custom key can be used to filter log messages):
[root@localhost ~]# auditctl -w /etc/passwd -p wa -k user-modify
Next, add a new user. Doing so changes the / etc/passwd file:
[root@localhost ~]# useradd user01
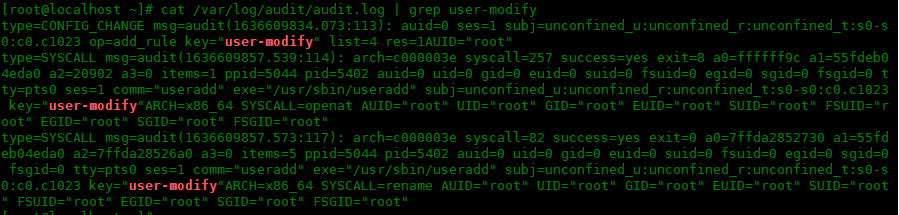
Finally, check that auditd records the changes. By default, auditd stores logs in the / var/log/audit/audit.log file:
[root@localhost ~]# cat /var/log/audit/audit.log | grep user-modify
Define persistent audit rules
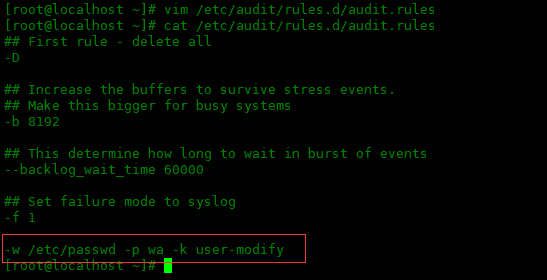
To keep audit rules unchanged after reboot, add them to the / etc/audit/rules.d/audit.rules file.
Next, define persistence rules in the audit.rules file to monitor changes to the / etc/passwd file.
-w /etc/passwd -p wa -k user-modify
Save the file and reload the auditd daemon to make changes to the configuration in the rules file:
[root@localhost ~]# service auditd reload
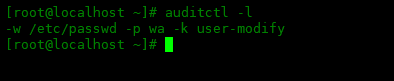
You can run auditctl -l to list rules:
[root@localhost ~]# auditctl -l -w /etc/passwd -p wa -k user-modify
Finally, adding a new user or changing the / etc/passwd file will start the audit. The changes are recorded in / var/log/audit/audit.log, and the rules still exist even if the system is restarted.
Search audit log
Use the ausearch tool to search the audit log. By default, it searches the / var/log/audit/audit.log file.
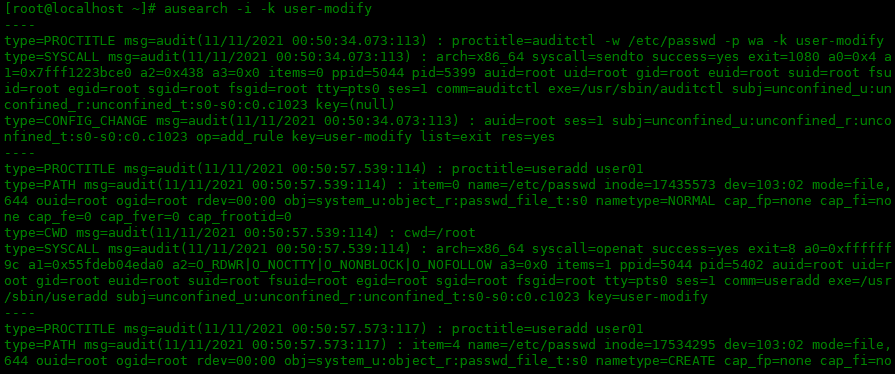
For example, according to the key_name searches log entries and searches for user modify related:
[root@localhost ~]# ausearch -i -k user-modify
Create audit report
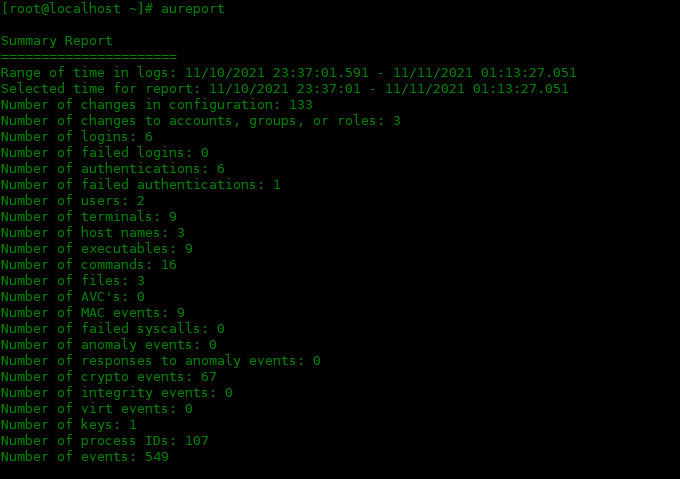
Use the aureport tool to query and create audit reports based on audit logs.
[root@localhost ~]# aureport
To view a report on attempted authentication:
[root@localhost ~]# aureport -au Authentication Report ============================================ # date time acct host term exe success event ============================================ 1. 11/10/2021 23:42:19 root localhost.localdomain tty1 /usr/bin/login yes 81 2. 11/10/2021 23:44:08 root 192.168.43.1 ssh /usr/sbin/sshd yes 111 3. 11/10/2021 23:54:31 root 192.168.43.1 ssh /usr/sbin/sshd yes 76 4. 11/11/2021 00:44:30 root 192.168.43.1 ssh /usr/sbin/sshd yes 81 5. 11/11/2021 00:58:41 root 192.168.43.1 ssh /usr/sbin/sshd yes 131 6. 11/11/2021 01:13:12 root 192.168.43.1 ssh /usr/sbin/sshd no 156
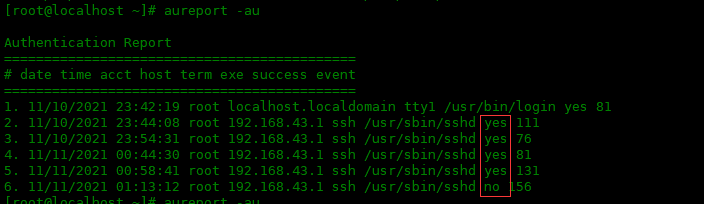
Where no represents authentication failure. yes means the verification is successful.
summary
In this article, you learned how to use auditctl to temporarily define auditd rules and permanently define them in the audit.rules file. Finally, the audit log is searched and the audit report is generated by using ausearch and aureport commands respectively.