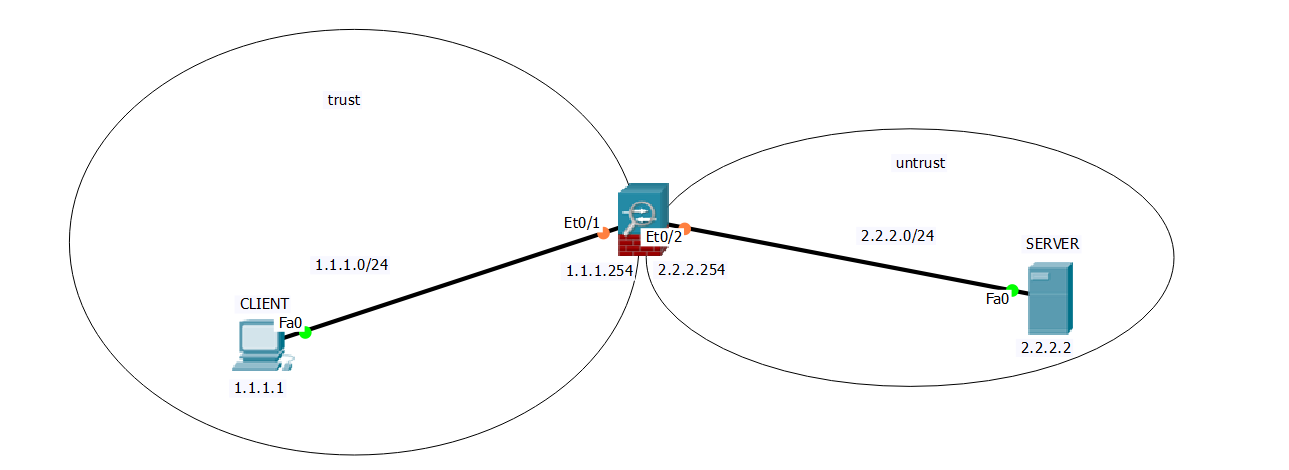
Cisco ASA 5505 firewall creates a security zone by creating VLANs, adding ports to VLANs, setting the security level of VLANs, and controlling the traffic between VLANs through ACL S;
0x01, build the experimental topology as follows:
Experimental requirements and objectives: configure the security zone and security rules to realize that the CLIENT in the trust zone can ping the server in the untrust zone, and the server can also Ping the CLIENT;
0x02 step, command
Firstly, the configuration of asa5505 is cleared to reduce experimental interference: two commands are mainly used: write erase and reload
ciscoasa#write erase Erase configuration in flash memory? [confirm] [OK] ciscoasa#reload Proceed with reload? [confirm] . . . . Then there is the reload process until: INFO: MIGRATION - Saving the startup errors to file 'flash:upgrade_startup_errors_201310031651.log' Pre-configure Firewall now through interactive prompts [yes]:n # Enter N to indicate no interaction Type help or '?' for a list of available commands. ciscoasa>
View vlan and port configuration: show switch vlan or sh sw vl
ciscoasa#show switch vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 inside up Et0/1, Et0/2, Et0/3, Et0/4
Et0/5, Et0/6, Et0/7
2 outside down Et0/0
It can be seen that vlan1 is turned on by default, and the logical name is inside (the name of the security area. In Cisco, generally inside represents the trust area, and outside represents the untrust area). Vlan2 contains most interfaces, while vlan2 is outside, and only e0/0 ports are added;
Next, you need to add e0/1 and e0/2 interfaces to two security zones respectively, that is, create two VLANs, one of which belongs to trust and the other belongs to untrust, and distinguish the security zones by setting the security level:
Configure vlan 1 as inside, that is, the trust area:
ciscoasa#conf t // Enter global configuration mode ciscoasa(config)#int vlan 1 // Configure VLAN 1 ciscoasa(config-if)#ip address 1.1.1.254 255.255.255.0 // Setting the IP address of vlan 1 virtual interface is equivalent to setting the IP address of e0/1 port ciscoasa(config-if)#security-level 100 // Set the security level of the security zone to 100. The higher the security level, the higher the degree of trust, that is, set vlan 1 as the trust zone ciscoasa(config-if)#no shutdown // Activate port ciscoasa(config-if)#
Configure vlan 2 as outside, that is, the untrust area:
ciscoasa#conf t ciscoasa(config)#int vlan 2 ciscoasa(config-if)#ip add 2.2.2.254 255.255.255.0 // Setting the IP address of vlan 1 virtual interface is equivalent to setting the IP address of e0/2 port ciscoasa(config-if)#security-level 0 // Set the security level of the security zone to 0, that is, set vlan 2 to the untrust zone ciscoasa(config-if)#no sh // Activate port ciscoasa(config-if)#
Add the e0/2 interface to vlan 2 (equivalent to adding the port to the security zone):
ciscoasa(config)#int vlan 2 ciscoasa(config-if)#int e0/2 ciscoasa(config-if)#switchport access vlan 2
View vlan and port status and vlan and IP correspondence:
ciscoasa(config-if)#show switch vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 inside up Et0/1, Et0/3, Et0/4, Et0/5
Et0/6, Et0/7
2 outside up Et0/0, Et0/2
#######################################################################################
ciscoasa(config-if)#show int ip brief
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 unassigned YES NVRAM down down
Ethernet0/1 unassigned YES NVRAM up up
Ethernet0/2 unassigned YES NVRAM up up
Ethernet0/3 unassigned YES NVRAM down down
Ethernet0/4 unassigned YES NVRAM down down
Ethernet0/5 unassigned YES NVRAM down down
Ethernet0/6 unassigned YES NVRAM down down
Ethernet0/7 unassigned YES NVRAM down down
Vlan1 1.1.1.254 YES manual up up
Vlan2 2.2.2.254 YES manual up up
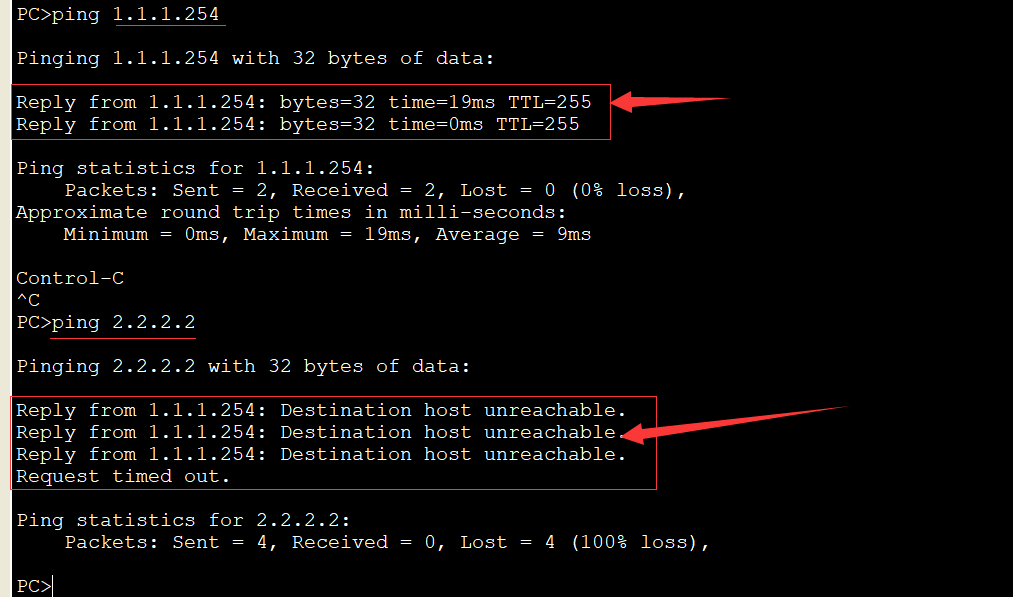
At this time, you can ping 1.1.1.254 on the CLIENT to show that the vlan ip configuration on the firewall is effective. However, ping 2.2.2.2[SERVER] shows that the target host is unreachable because there are no security rules configured on the firewall to release traffic, [the same is true on the SERVER side]:
Understand some concepts:
In Cisco firewall, when accessing interfaces with different security levels, follow: allow outbound connection [i.e., I can access others], prohibit inbound connection [i.e., others cannot access me], and prohibit communication between interfaces with the same security level [if your security level is 100, I am also 100, we cannot access each other]
Configure security policy and release icmp response message from untrust to trust area:
ciscoasa#conf t // Enter global configuration mode ciscoasa(config)#access-list icmp permit icmp host 2.2.2.2 host 1.1.1.1 echo-reply // Access list [create ACL] icmp[ACL entry name] permit [action executed, allow or deny] ICMP [protocol type] host [indicates specified source host ip] 2.2.2.2 host [indicates specified destination host ip1.1.1.1] echo reply [message type: ICMP response message] ciscoasa(config)#Access group icmp in int outside / / access group [apply specified ACL to interface] icmp [name of ACL to be applied] in [traffic direction: inbound] int outside [apply to outside interface] ###################################################################### see ACL ciscoasa(config)#show access-list access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096) alert-interval 300 access-list icmp; 1 elements; name hash: 0xd95cd98d access-list icmp line 1 extended permit icmp host 2.2.2.2 host 1.1.1.1 echo-reply(hitcnt=3) 0xe655907e
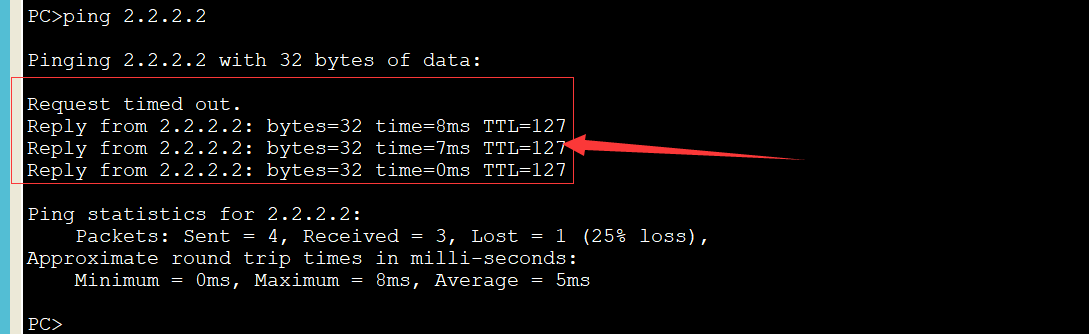
At this time, ping 2.2.2.2 on the CLIENT to ping:
 From setting SERVER ping to CLIENT, the configuration method is the same as above. Pay attention to the application interface, traffic direction, source address, destination address and protocol;
From setting SERVER ping to CLIENT, the configuration method is the same as above. Pay attention to the application interface, traffic direction, source address, destination address and protocol;